Using a web-based common vulnerability scoring system (CVSS) calculator, a security response team member performed an assessment on a reported vulnerability in the company's claims intake component. The base score of the vulnerability was 3.5 and changed to 5.9 after adjusting temporal and environmental metrics.
Which rating would CVSS assign this vulnerability?
Which architecture deliverable identifies the organization's tolerance to security issues and how the organization plans to react if a security issue occurs?
What is a countermeasure to the web application security frame (ASF) authentication threat category?
Which DKEAD category has a risk rating based on the threat exploit's potential level of harm?
The software security group is conducting a maturity assessment using the Building Security in Maturity Model (BSIMM). They are currently focused on reviewing attack models created during recently completed initiatives.
Which BSIMM domain is being assessed?
What is a best practice of secure coding?
The software security team prepared a detailed schedule napping security development lifecycle phases to the type of analysis they will execute.
Which design and development deliverable aid the team prepare?
What refers to the review of software source code by developers other than the original coders to try to identify oversights, mistakes, assumptions, a lack of knowledge, or even experience?
A potential threat was discovered during vulnerability testing when an environment configuration file was found that contained the database username and password stored in plain text.
How should existing security controls be adjusted to prevent this in the future?
Which privacy impact statement requirement type defines how personal information will be protected when authorized or independent external entities are involved?
A recent vulnerability scan uncovered an XML external entity (XXE) Haw that could allow attackers to return the contents of a system file by including a specific payload in an XML request.
How should the organization remediate this vulnerability?
The security team is reviewing all noncommercial software libraries used in the new product to ensure they are being used according to the legal specifications defined by the authors.
What activity of the Ship SDL phase is being performed?
Which security assessment deliverable identifies possible security vulnerabilities in the product?
A software security team recently completed an internal assessment of the company's security assurance program. The team delivered a set of scorecards to leadership along with proposed changes designed to improve low-scoring governance, development, and deployment functions.
Which software security maturity model did the team use?
Which type of security analysis is performed by injecting malformed data into open interfaces of an executable or running application and is most commonly executed during the testing or deployment phases of the SDLC?
What are the three primary goals of the secure software development process?
Senior IT staff has determined that a new product will be hosted in the cloud and will support web and mobile users. Developers will need to deliver secure REST services. Android and IOS mobile apps. and a web application. Developers are currently determining how to deliver each part of the overall product.
Which phase of the software development lifecycle (SDLC) is being described?
Which software control test examines an application from a user perspective by providing a wide variety of input scenarios and inspecting the output?
A new product does not display personally identifiable information, will not let private documents be printed, and requires elevation of privilege to retrieve archive documents. Which secure coding practice is this describing?
Which secure software design principle assumes attackers have the source code and specifications of the product?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
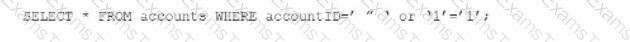
Which technique should be used to detect this vulnerability without running the source codes?
Which threat modeling step collects exploitable weaknesses within the product?
Which DREAD category is based on how easily a threat exploit can be found?
Which software control test examines the internal logical structures of a program and steps through the code line by line to analyze the program for potential errors?
Which software-testing technique can be automated or semi-automated and provides invalid, unexpected, or random data to the inputs of a computer software program?
Which secure coding practice requires users to log in to their accounts using an email address and a password they choose?
Which design and development deliverable contains the types of evaluations that were performed, how many times they were performed, and how many times they were re-evaluated?
What are the eight phases of the software development lifecycle (SDLC)?
During fuzz testing of the new product, an exception was thrown on the order entry view, which caused a full stack dump to be displayed in the browser window that included function names from the source code.
How should existing security controls be adjusted to prevent this in the future?
Which security assessment deliverable defines measures that can be periodically reported to management?
The software security team is performing security testing on a new software product using a testing tool that scans the running application for known exploit signatures.
Which security testing technique is being used?
Which software development model starts by specifying and implementing just a part of the software, which is then reviewed and identifies further requirements that are implemented by repeating the cycle?
Which secure coding best practice says to use a single application-level authorization component that will lock down the application if it cannot access its configuration information?
The software security team is using an automation tool that generates random data to input into every field in the new product and track results.
Which security testing technique is being used?
A public library needs to implement security control on publicly used computers to prevent illegal downloads.
Which security control would prevent this threat?