Refer to the exhibit.
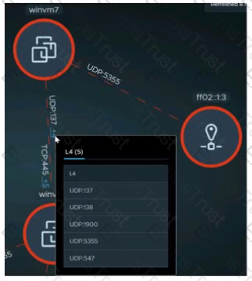
An administrator is reviewing NSX Intelligence information as shown in the exhibit.
What does the red dashed line for the UDP:137 flow represent?
Where is a partner security virtual machine (Partner SVM) deployed to process the redirected North-South traffic in an efficient manner?
At which OSI Layer do Next Generation Firewalls capable of analyzing application traffic operate?
A security administrator recently enabled Guest Introspection on NSX-T Data Center.
Which would be a reason none of the Microsoft Windows based VMs are reporting any information?
Refer to the exhibit.
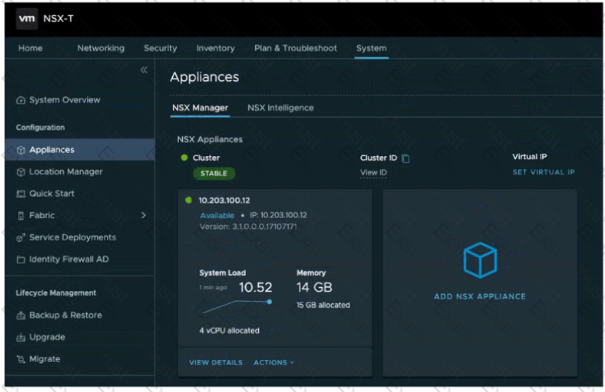
Referencing the exhibit, what is the VMware recommended number of NSX Manager Nodes to additionally deploy to form an NSX-T Manager Cluster?
A customer has deployed NSX Intelligence appliance with an incorrect IP address.
What should the customer do to correct the IP address?
Which two are the insertion points for North-South service insertion? (Choose two.)
An administrator is creating the first distributed firewall rules for a company's salts department. What is the first object that must be created in the distributed firewall'
Information Security Management (ISM) describes a set of controls that organizations employ to protect which properties?
What is one of the main use-cases of NSX-T Endpoint Protection?