A defined relationship between two Configuration Items (CIs), such as Runs on, Depends On, or Contains is called a what?
How many ServiceNow instances can one MID Server connect to?
When using Service Mapping Pattern Designer, which one of the following is the result when using the Parse command output operation with the following command?
cat /etc/haproxy/haproxy.cfg
In Service Mapping, which one of the following is used to discover the applications and outbound connections to other applications that appear on a Service map?
In Event Management, if a Message key is not passed from an Event, which of the following Alert fields combine to populate the Message key on an Alert?
Within the CMDB, all application CI Types/Classes are children of which parent class?
What is the recommended approach to map a heavily containerized service in a production environment?
From the Service Mapping service map, which one of the following best describes the difference between the options Resume discovery and Run discovery?
Which of the following are methods used to initiate discovery on a service? (Choose three.)
In Service Mapping, which one of the following best describes the process of discovery after an Entry Point is configured?
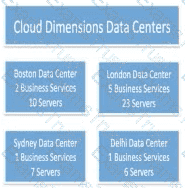
Cloud Dimensions has data centers, services, and servers represented in the image.
Assuming each data center contains minimum one subnet, which one of the following is the best number of MID Servers Tur Cloud Dimensions to start with?
In order for Service Mapping to successfully discover UNIX targets, which SSH credential can be granted with limited privileges to a user?
In Service Mapping, when discovery is started, what is the execution strategy used to run Connection Sections?
Service Mapping provides visibility to the Operator in Agent Workspace without leaving the Workspace UI. This visibility includes what items associated with the CI? (Choose two.)
When running Service Mapping discovery, which of the following represents the root cause of the error?
“Failed to access target system. Access is denied”
Which one of the following is the baseline Identification Rule (CI Identifier) used to determine inserts or updates to all servers discovered by ServiceNow Discovery or Service Mapping?
During Service Mapping discovery, which one of the following is used to uniquely identify a configuration item to determine updates or inserts into the CMDB?
To begin the configuration of tag-based services, tag values must be defined where?
After discovering load balancers in a customer environment, service candidates may appear on the Service Mapping Home page under which one of the following tiles?
Which address is required for Service Mapping to discover a Load Balancer that does not previously exist in the CMDB?
In Pattern Designer, which one of the following best describes the Create Connection step?
Reconciliation Rules for the Application [cmdb_ci_appl] table are configured exactly the same for both ServiceNow and SCCM data sources and the following priorities are configured:
ServiceNow Priority: 100
SCCM Priority: 200
Which of the following is true?
Choose 3 answers:
Which one of the following best describes the definition of an Entry Point?
Which one of the following Regular Expressions could be used to parse "San Diego" from the string "Location San Diego"?
Which one of the following Identification Rule (CI Identifier) fields, when selected, determines CMDB update/inserts based on the configuration item's (CI) own attributes, without taking other CIs or relationships into consideration?
Which one of the following represents what the MID stands for in MID Server?
Which of the following commands does Service Mapping run on Linux-based targets that requires elevated privileges (i.e. sudo)?
During ServiceNow Discovery, which one of the following is the approximate number of host IPs that are port scanned with a Discovery Schedule configured with an IP network as shown?
180.181.0.0/16
During ServiceNow Discovery, which one of the following protocols is used to extract data from printers?
In Service Mapping, which one of the following best describes the process of discovery after an Entry Point is configured?
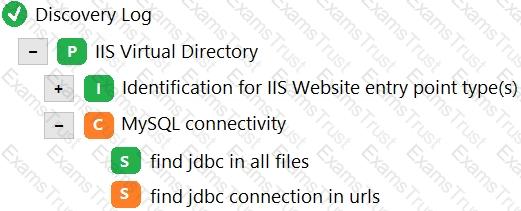
In the following image of the Discovery Log, the green S represents which one of the following?