What is a key characteristic of a parsing rule in Cortex XSIAM?
Which action is required to enable use of a custom script in an alert layout?
While using the remote repository on a Development XSIAM tenant, which two objects can be pushed or pulled to the remote repository? (Choose two.)
Cortex XSIAM has not received any logs for 30 minutes from a Palo Alto Networks NGFW named "MainFW.” An engineer wants to create an alert for this scenario.
Correlation rule settings include:
 Time Schedule: Every 30 minutes
Time Schedule: Every 30 minutes
 Query Timeframe: 30 minutes
Query Timeframe: 30 minutes
 Action: Generate alert
Action: Generate alert
 Alert Name: No logs received from MainFW in the past 30 minutes
Alert Name: No logs received from MainFW in the past 30 minutes
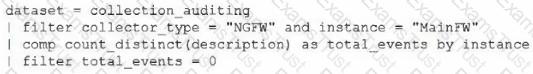
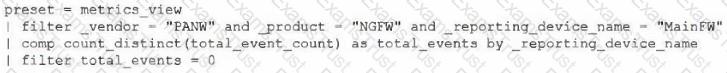
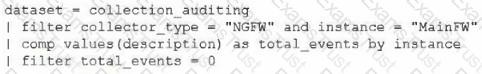
Which query should be used in the correlation rule?
A)
B)
C)
D)

A CISO has asked an engineer to create a custom dashboard in Cortex XSIAM that can be filtered to show incidents assigned to a specific user.
Which feature should be used to filter the incident data in the dashboard?
Which installer type should be used when upgrading a non-Linux Kubernetes cluster?
In the Incident War Room, which command is used to update incident fields identified in the incident layout?
A Cortex XSIAM engineer adds a disable injection and prevention rule for a specific running process. After an hour, the engineer disables the rule to reinstate the security capabilities, but the capabilities are not applied.
What is the explanation for this behavior?
What is the purpose of using rolling tokens to manage Cortex XDR agents?
What is the function of the "MODEL" section when creating a data model rule?
Which cytool command will look up the policy being applied to a Cortex XDR agent?
How does Cortex XSIAM manage licensing for Kubernetes environments?
A vulnerability analyst asks a Cortex XSIAM engineer to identify assets vulnerable to newly reported zero-day CVE affecting the "ai_app" application and versions 12.1, 12.2, 12.4, and 12.5.
Which XQL query will provide the required result?
A)

B)

C)
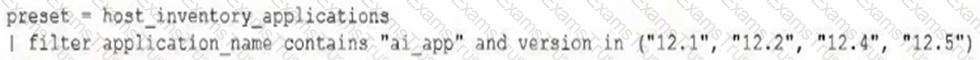
D)

Which common issue can result in sudden data ingestion loss for a data source that was previously successful?
A Behavioral Threat Protection (BTP) alert is triggered with an action of "Prevented (Blocked)" on one of several application servers running Windows Server 2022. The investigation determines the involved processes to be legitimate core OS binaries, and the description from the triggered BTP rule is an acceptable risk for the company to allow the same activity in the future.
This type of activity is only expected on the endpoints that are members of the endpoint group "AppServers," which already has a separate prevention policy rule with an exceptions profile named "Exceptions-AppServers" and a malware profile named "Malware-AppServers."
The CGO that was terminated has the following properties:
SHA256: eb71ea69dd19f728ab9240565e8c7efb59821e19e3788e289301e1e74940c208
File path: C:\Windows\System32\cmd.exe
Digital Signer: Microsoft Corporation
How should the exception be created so that it is scoped as narrowly as possible to minimize the security gap?
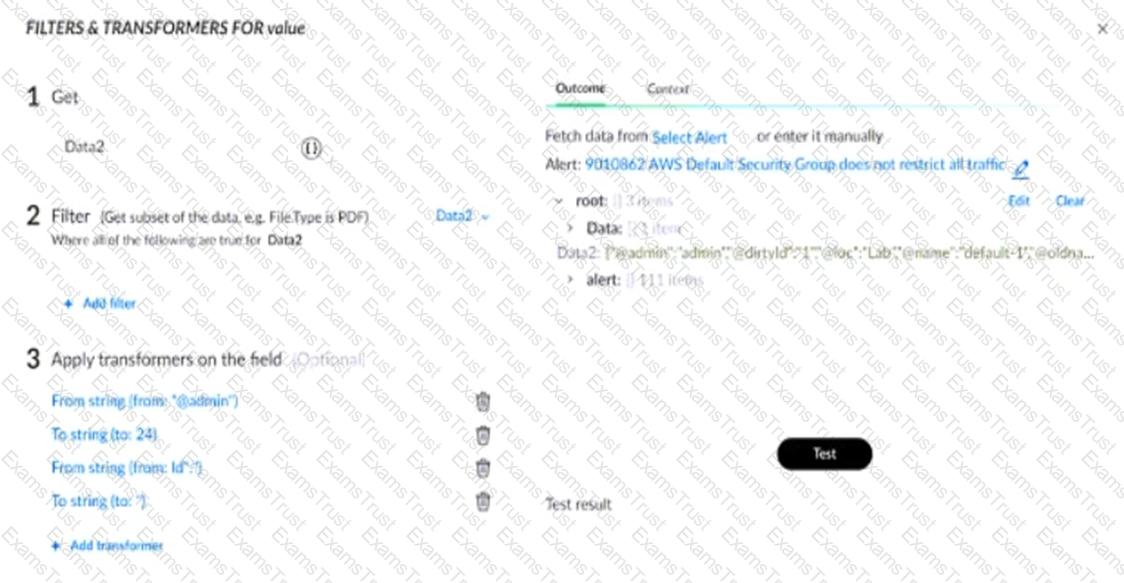
The following string is a value of a key named "Data2" in the context:
{"@admin":"admin","@dirtyld":"1","@loc":"Lab","@name":"default‑1","@oldname":"Test","@time":"2024/08/28 07:45:15","alert":{"@admin":"admin","@dirtyld":"2","@time":"2024/08/28 07:45:15","member":{"#text":"
Based on the image below, what will be displayed in the "Test result" field when the "Test" button is pressed?
How will Cortex XSIAM help with raw log ingestion from third-party sources in an existing infrastructure?