An engineer has configured a Web Security rule that restricts access to certain web applications for a specific user group. During testing, the rule does not take effect as expected, and the users can still access blocked web applications.
What is a reason for this issue?
What must be configured to accurately report an application's availability when onboarding a discovered application for ZTNA Connector?
When a review of devices discovered by IoT Security reveals network routers appearing multiple times with different IP addresses, which configuration will address the issue by showing only unique devices?
What is the impact of selecting the “Disable Server Response Inspection” checkbox after confirming that a Security policy rule has a threat protection profile configured?
Which feature within Strata Cloud Manager (SCM) allows an operations team to view applications, threats, and user insights for branch locations for both NGFW and Prisma Access simultaneously?
Strata Logging Service is configured to forward logs to an external syslog server; however, a month later, there is a disruption on the syslog server.
Which action will send the missing logs to the external syslog server?
A malicious user is attempting to connect to a blocked website by crafting a packet using a fake SNI and the correct website in the HTTP host header.
Which option will prevent this form of attack?
A company has four branch offices between Canada Central and Canada East which use the same IPSec termination node and have QoS configured with customized bandwidth per site. An engineer wants to onboard a new branch office on the same IPSec termination node.
What is the QoS behavior for the new branch office?
Which two statements apply when a customer has a large branch office with employees who all arrive and log in within a five-minute time period? (Choose two.)
How can an engineer use risk score customization in SaaS Security Inline to limit the use of unsanctioned SaaS applications by employees within a Security policy?
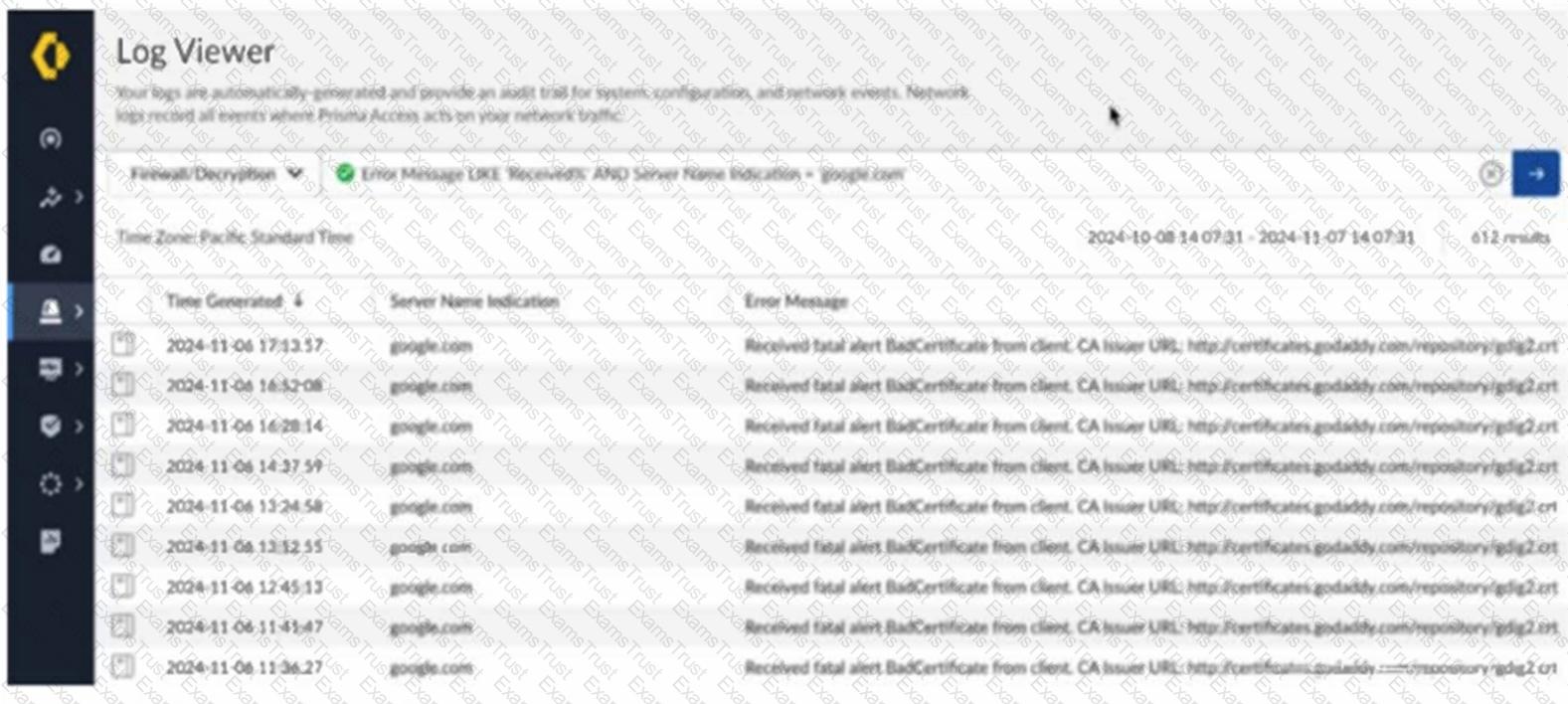
Based on the image below, which two statements describe the reason and action required to resolve the errors? (Choose two.)
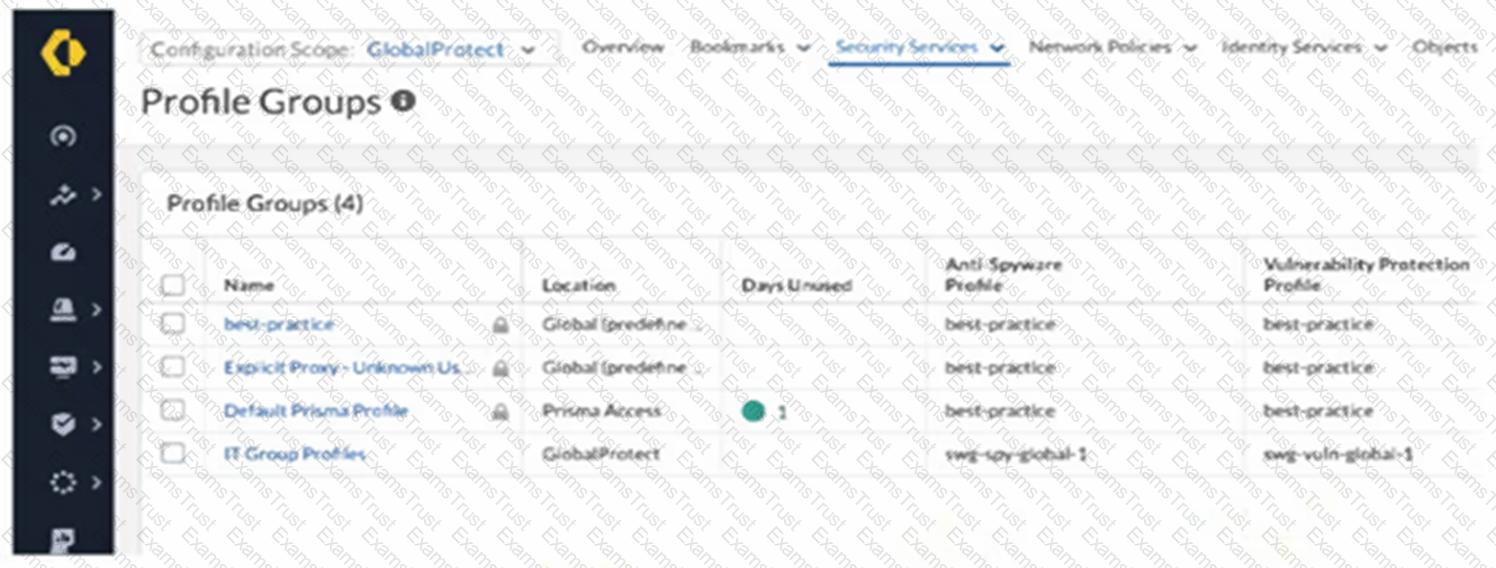
An intern is tasked with changing the Anti-Spyware Profile used for security rules defined in the GlobalProtect folder. All security rules are using the Default Prisma Profile. The intern reports that the options are greyed out and cannot be modified when selecting the Default Prisma Profile.
Based on the image below, which action will allow the intern to make the required modifications?
All mobile users are unable to authenticate to Prisma Access (Managed by Strata Cloud Manager) using SAML authentication through the Cloud Identity Engine. Users report that after entering their credentials on the Identity Provider (IdP) login page, they are redirected to the Prisma Access portal without successful authentication, and they receive this error message:
Error: Prisma Access Portal Authentication Failed using CIE-SAML with message “400 Bad Request”
Which action will identify the root cause of this error?
When configuring Remote Browser Isolation (RBI) with Prisma Access (Managed by Strata Cloud Manager), which element is required to define the protected URLs for mobile users?
Which two configurations must be enabled to allow App Acceleration for SaaS applications? (Choose two.)