For how many hours are Prisma SD-WAN VPN shared secrets valid?
Return traffic for an application from the branch is being dropped on the branch ION. Application traffic arrives via SD-WAN internet overlay at the branch, and path policy for the application at the branch has the following settings:
Active = MPLS Overlay
Backup = Prisma Access on internet
Which branch configuration is the probable cause of this behavior?
A remote branch site is reporting intermittent connectivity to the Data Center. The administrator checks the System > Alarms page and sees a "VPN_DOWN" alarm for the tunnel to the DC. However, the internet circuit status is "Up".
Which specific log file or diagnostic tool in the Prisma SD-WAN portal would provide the IKE (Internet Key Exchange) error codes (e.g., "NO_PROPOSAL_CHOSEN" or "AUTH_FAILED") to pinpoint the cause of the tunnel failure?
A network administrator is viewing the Flow Browser to investigate a report that a specific user cannot access an internal web server. The flow entry for this traffic shows the "Flow State" as "INIT" and it remains in that state until it times out.
What does the "INIT" state indicate about the traffic flow?
BGP core peers on data center IONs are learning only a default route from the core router. Which action will protect the SD-WAN network from getting isolated in the event of BGP misconfiguration on the core routers?
In a Data Center deployment, what is the key functional difference between configuring a BGP neighbor as a "Core Peer" versus an "Edge Peer"?
When configuring SASE connectivity with easy onboarding at a branch, which two options must be selected? (Choose two.)
In which modes can a Prisma SD-WAN branch be deployed?
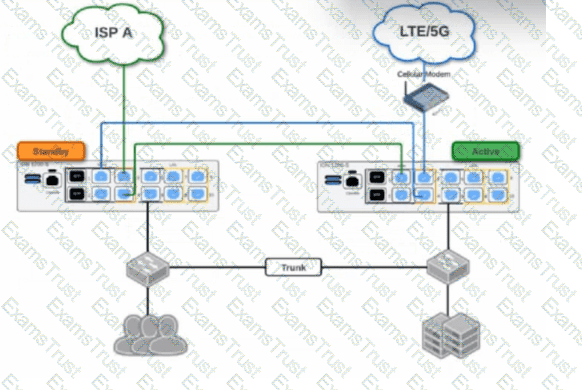
Based on the HA topology image below, which two statements describe the end-state when power is removed from the ION 1200-S labeled “Active”, assuming that the ION labeled “Standby” becomes the active ION? (Choose two.)
A branch manager reports slow network performance, and the network administrator wants to use Prisma SD-WAN Copilot to quickly identify if a specific user, by source IP address, is consuming excessive bandwidth as well as which applications are contributing to this consumption. How can Copilot assist in this investigation?
While designing a greenfield Prisma SD-WAN solution for a retailer, the risk management group requires segmentation of the retail network to avoid one large fault domain.
The following data points are provided:
Two data centers and all sites need to access applications in both data centers
1000 retail branches with stores concentrated in multiple metropolitan areas
Data Center 1 and Data Center 2 have different sets of applications that are not replicated
Maintaining application availability is the primary goal
Which action will segment the retail network and reduce regional outages?
What is the number and structure of Prisma SD-WAN QoS queues supported per WAN interface?
When troubleshooting an issue at a site that is running on two cellular links from two carriers, the operations team shared some evidence shown in the graph below:
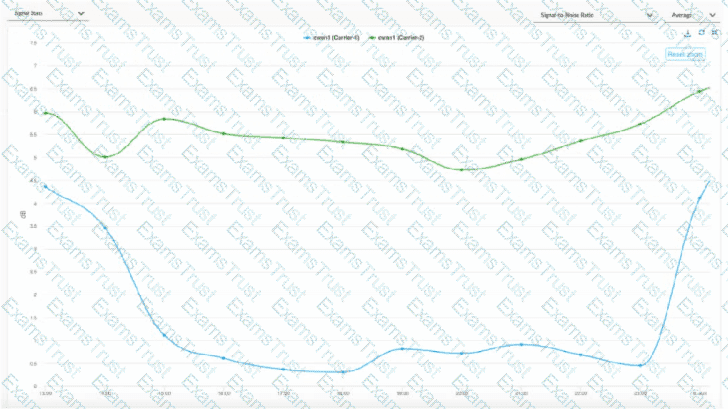
For the time duration shown in the graph, what are two inferences about the site’s traffic that can be made? (Choose two.)
A network engineer is troubleshooting a user complaint regarding "slow application performance" for an internal web application. While viewing the Flow Browser in the Prisma SD-WAN portal, the engineer notices that the Server Response Time (SRT) is consistently high (over 500ms), while the Network Transfer Time (NTT) and Round Trip Time (RTT) are low (under 50ms).
What does this data indicate about the root cause of the issue?
Site templates are to be used for the large-scale deployment of 100 Prisma SD-WAN branch sites across different regions.
Which two statements align with the capabilities and best practices for Prisma SD-WAN site templates? (Choose two.)
A network administrator is troubleshooting a critical SaaS application, “SuperSaaSApp”, that is experiencing connectivity issues. Initially, the configured active and backup paths for the application were reported as completely down at Layer 3. The Prisma SD-WAN system attempted to route traffic for the application over an L3 failure path that was explicitly configured as a Standard VPN to Prisma Access.
However, users are still reporting a complete outage for the application and monitoring tools show application flows being dropped when attempting to use the Standard VPN L3 failure path, even though the tunnel itself appears to be up. The administrator suspects a policy misconfiguration related to how the Standard VPN path interacts with destination groups.
What is the most likely reason for flows being dropped when attempting to use the Standard VPN L3 failure path?
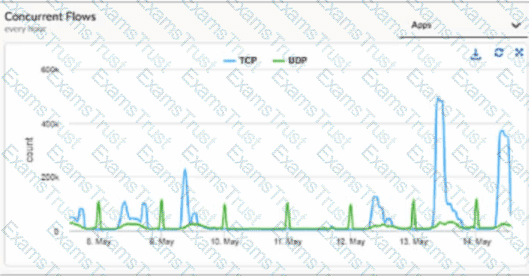
The UI triggers incident DEVICESW_CONCURRENT_FLOWLIMIT_EXCEEDED for a branch site. Based in the image below, which tool can be used to identify the host?
An engineer at a managed services provider is updating an application that allows its customers to request firewall changes to also manage SD-WAN. The application will be able to make any approved changes directly to devices via API.
What is a requirement for the application to create SD-WAN interfaces?
A network installer is attempting to claim a new ION device using the "Claim Code" method. The device is connected to the internet, but the status in the portal remains stuck at "Claimed" and does not transition to "Online". The installer connects a laptop to the LAN port of the ION and can successfully browse the internet, confirming the uplink is active.
What is the most likely cause of the device failing to reach the "Online" state?
A customer wants to deploy Prisma SD-WAN ION devices at small home offices that use consumer-grade broadband routers. These routers typically use Symmetric NAT and do not allow static port forwarding.
Which standard mechanism does Prisma SD-WAN utilize to successfully establish direct Branch-to-Branch (Dynamic) VPN tunnels through these Symmetric NAT devices?
A multinational company is deploying Prisma SD-WAN across North America, Europe, and Asia. The data centers in the North America region have served all regions, but regional policies are now being enforced that mandate each of the regions to build their own data centers and branch sites to only connect to their respective regional data centers.
How can this regionalization be achieved so that new or existing branch sites only build tunnels to the regional DC IONs?
Which statement is valid when integrating Prisma SD-WAN with Prisma Access remote networks?
Which condition, when configured within a performance policy, is a trigger for generating an incident related to application performance or path degradation?
A network administrator notices that a branch ION device is experiencing high CPU utilization due to a suspected TCP SYN Flood attack originating from a compromised host on the local LAN.
Which specific security feature should be configured and applied to the "LAN" zone to mitigate this Denial of Service (DoS) attack?
Where is route leaking configured between VRFs?