What are three benefits of SD-WAN infrastructure? (Choose three.)
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
Which Palo Alto Networks solution has replaced legacy IPS solutions?
The seventy of an attack needs to be escalated.
What needs to be in place in order for the security operations team to properly inform various units within the enterprise of the issue?
Which IoT connectivity technology is provided by satellites?
What is a function of SSL/TLS decryption?
Which technology grants enhanced visibility and threat prevention locally on a device?
Which of the following is a Routed Protocol?
Which tool's analysis data gives security operations teams insight into their environment's risks from exposed services?
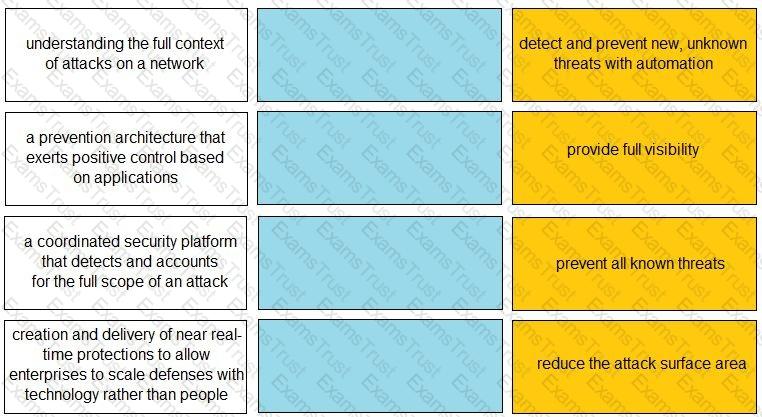
Match each description to a Security Operating Platform key capability.
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
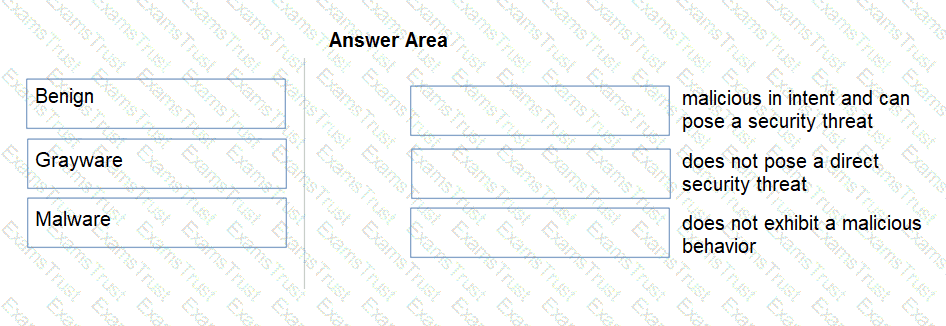
Match the Palo Alto Networks WildFire analysis verdict with its definition.
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
Which type of portable architecture can package software with dependencies in an isolated unit?
When does a TLS handshake occur?
What differentiates Docker from a bare metal hypervisor?
Which of the Cloud-Delivered Security Services (CDSS) will detect zero-day malware by using inline cloud machine learning (ML) and sandboxing?
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
Which component of the AAA framework regulates user access and permissions to resources?
Which technique uses file sharing or an instant messenger client such as Meebo running over Hypertext Transfer Protocol (HTTP)?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
Which two descriptions apply to an XDR solution? (Choose two.)
Which next-generation firewall (NGFW) deployment option provides full application visibility into Kubernetes environments?
Which type of attack includes exfiltration of data as a primary objective?
Which architecture model uses virtual machines (VMs) in a public cloud environment?
What type of area network connects end-user devices?
Which two processes are critical to a security information and event management (SIEM) platform? (Choose two.)
Which option is an example of a North-South traffic flow?
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
Which attacker profile acts independently or as part of an unlawful organization?
Which capability does Cloud Security Posture Management (CSPM) provide for threat detection within Prisma Cloud?
Which action is unique to the security orchestration, automation, and response (SOAR) platforms?
Which type of malware replicates itself to spread rapidly through a computer network?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
Which two statements apply to SaaS financial botnets? (Choose two.)
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
Which feature is part of an intrusion prevention system (IPS)?
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads.
What deployment options do you have available? (Choose two.)
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
What are two advantages of security orchestration, automation, and response (SOAR)? (Choose two.)
Which statement describes the process of application allow listing?
Which security component can detect command-and-control traffic sent from multiple endpoints within a corporate data center?
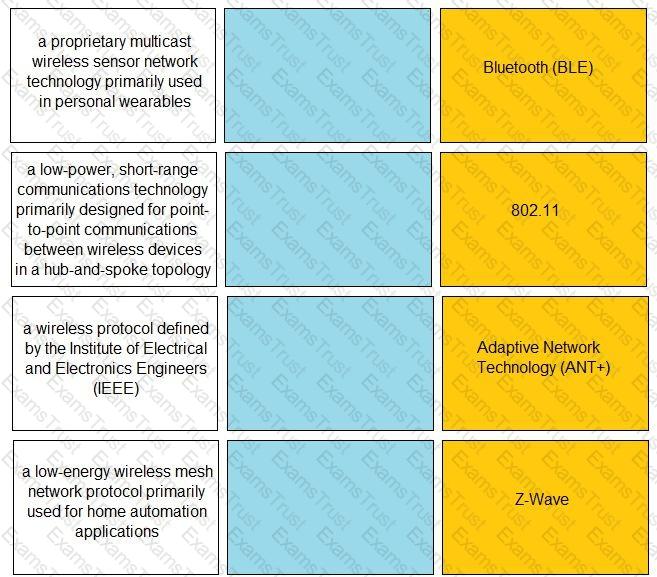
Match the IoT connectivity description with the technology.
What type of DNS record maps an IPV6 address to a domain or subdomain to another hostname?
Which pillar of Prisma Cloud application security does vulnerability management fall under?
If an endpoint does not know how to reach its destination, what path will it take to get there?
How can local systems eliminate vulnerabilities?
What are two functions of User and Entity Behavior Analytics (UEBA) data in Prisma Cloud CSPM? (Choose two.)
What is the definition of a zero-day threat?
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
Which network analysis tool can be used to record packet captures?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
Which of the following is a CI/CD platform?
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
Which characteristic of serverless computing enables developers to quickly deploy application code?
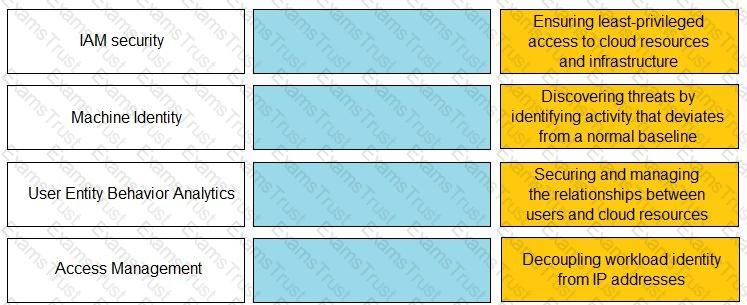
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
Which statement describes a host-based intrusion prevention system (HIPS)?
In SecOps, what are two of the components included in the identify stage? (Choose two.)
Which methodology does Identity Threat Detection and Response (ITDR) use?
Which network device breaks networks into separate broadcast domains?
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
Which two services does a managed detection and response (MDR) solution provide? (Choose two.)
What does SOAR technology use to automate and coordinate workflows?
Which statement describes DevOps?
Which two workflows are improved by integrating SIEMs with other security solutions? (Choose two.)
What differentiates knowledge-based systems from behavior-based systems?