An engineer troubleshoots a high availability (HA) link that is unreliable.
Where can the engineer view what time the interface went down?
An engineer is pushing configuration from Panorama to a managed firewall What happens when the pushed Panorama configuration has Address Object names that duplicate the Address Objects already configured on the firewall?
A network administrator notices a false-positive state after enabling Security profiles. When the administrator checks the threat prevention logs, the related signature displays the following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this signature?
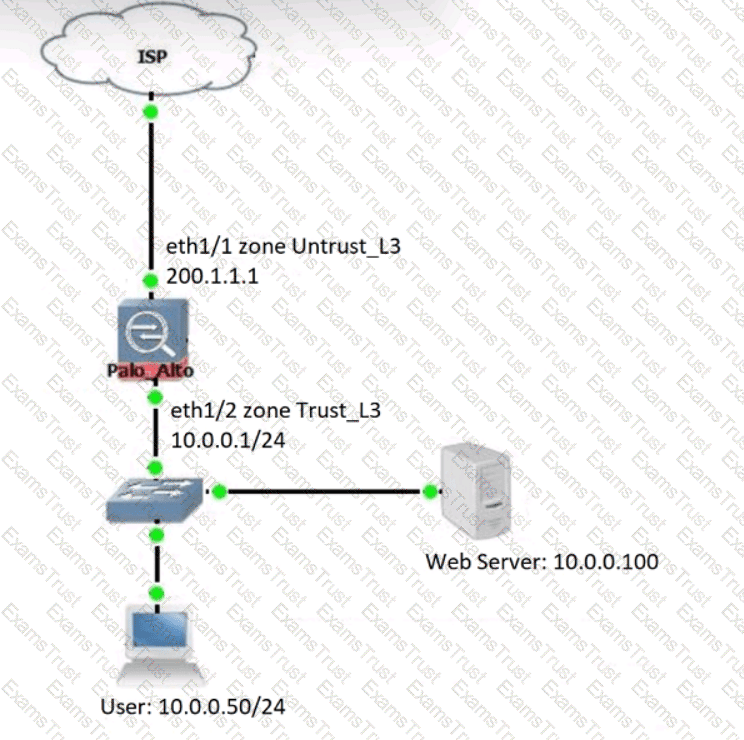
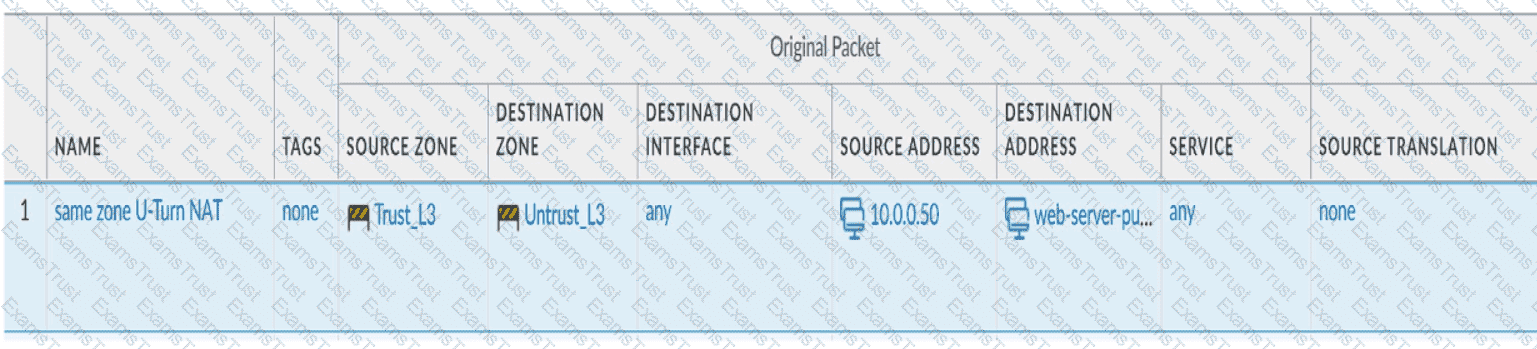
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
What are three prerequisites to enable Credential Phishing Prevention over SSL? (Choose three
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
What must be configured to apply tags automatically based on User-ID logs?
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of reconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
An engineer must configure a new SSL decryption deployment.
Which profile or certificate is required before any traffic that matches an SSL decryption rule is decrypted?
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
Which three external authentication services can the firewall use to authenticate admins into the Palo Alto Networks NGFW without creating administrator account on the firewall? (Choose three.)
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
Why would a traffic log list an application as "not-applicable”?
An engineer is configuring a firewall with three interfaces:
• MGT connects to a switch with internet access.
• Ethernet1/1 connects to an edge router.
• Ethernet1/2 connects to a visualization network.
The engineer needs to configure dynamic updates to use a dataplane interface for internet traffic. What should be configured in Setup > Services > Service Route Configuration to allow this traffic?
Which three firewall multi-factor authentication factors are supported by PAN-OS? (Choose three.)
What can be used as an Action when creating a Policy-Based Forwarding (PBF) policy?
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
A company wants to deploy IPv6 on its network which requires that all company Palo Alto Networks firewalls process IPv6 traffic and to be configured with IPv6 addresses. Which consideration should the engineers take into account when planning to enable IPv6?
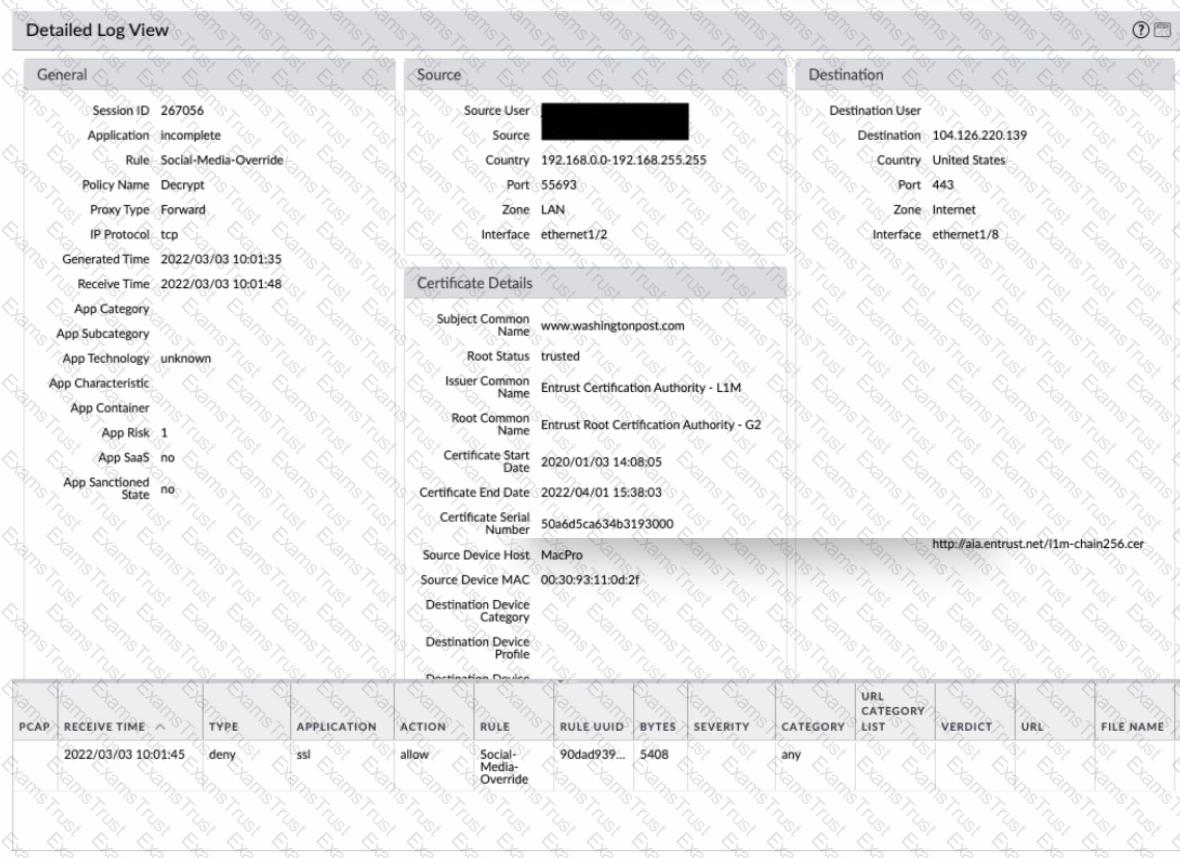
When a new firewall joins a high availability (HA) cluster, the cluster members will synchronize all existing sessions over which HA port?
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?
In which two scenarios is it necessary to use Proxy IDs when configuring site-to-site VPN tunnels? (Choose two.)
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates.
What must occur to have Antivirus signatures update?
What does the User-ID agent use to find login and logout events in syslog messages?
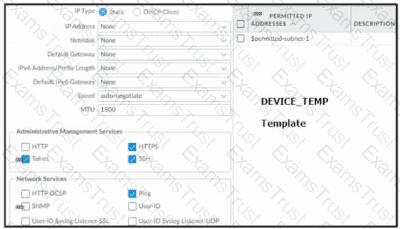
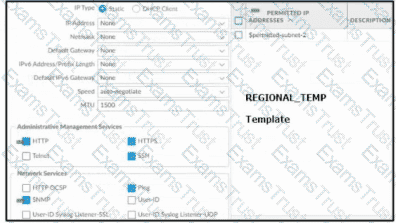
Based on the images below, and with no configuration inside the Template Stack itself, what access will the device permit on its management port?

Where can a service route be configured for a specific destination IP?
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy.
Without changing the existing access to the management interface, how can the engineer fulfill this request?
Which method will dynamically register tags on the Palo Alto Networks NGFW?
The vulnerability protection profile of an on-premises Palo Alto Networks firewall is triggering on a common Threat ID, and it has been determined to be a false positive. The issue causes an outage of a critical service. When the vulnerability protection profile is opened to add the exception, the Threat ID is missing. Which action will most efficiently find and implement the exception?
Which User-ID mapping method should be used in a high-security environment where all IP address-to-user mappings should always be explicitly known?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
Which two are required by IPSec in transport mode? (Choose two.)
During the process of developing a decryption strategy and evaluating which websites are required for corporate users to access, several sites have been identified that cannot be decrypted due to technical reasons. In this case, the technical reason is unsupported ciphers Traffic to these sites will therefore be blocked if decrypted.
How should the engineer proceed?
While troubleshooting an issue, a firewall administrator performs a packet capture with a specific filter. The administrator sees drops for packets with a source IP address of 10.1.1.1.
How can the administrator further investigate these packet drops by looking at the global counters for this packet capture filter?
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile. What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
Which three split tunnel methods are supported by a globalProtect gateway? (Choose three.)
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install.
When performing an upgrade on Panorama to PAN-OS. what is the potential cause of a failed install?
Which configuration change will improve network reliability and ensure minimal disruption during tunnel failures?
Review the screenshots.
What is the most likely reason for this decryption error log?
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known
What can the administrator configure to establish the VPN connection?
What must be taken into consideration when preparing a log forwarding design for all of a customer’s deployed Palo Alto Networks firewalls?
A company uses GlobalProtect for its VPN and wants to allow access to users who have only an endpoint solution installed. Which sequence of configuration steps will allow access only for hosts that have antivirus or anti-spyware enabled?
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
A superuser is tasked with creating administrator accounts for three contractors. For compliance purposes, all three contractors will be working with different device-groups in their hierarchy to deploy policies and objects
Which type of role-based access is most appropriate for this project?
What happens when the log forwarding built-in action with tagging is used?
After configuring an IPSec tunnel, how should a firewall administrator initiate the IKE phase 1 to see if it will come up?
An administrator configures HA on a customer's Palo Alto Networks firewalls with path monitoring by using the default configuration values.
What are the default values for ping interval and ping count before a failover is triggered?
How is Perfect Forward Secrecy (PFS) enabled when troubleshooting a VPN Phase 2 mismatch?
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
Which is not a valid reason for receiving a decrypt-cert-validation error?
How can a firewall engineer bypass App-ID and content inspection features on a Palo Alto Networks firewall when troubleshooting?
Which three sessions are created by a NGFW for web proxy? (Choose three.)
A firewall engineer is managing a Palo Alto Networks NGFW that does not have the DHCP server on DHCP agent configuration. Which interface mode can the broadcast DHCP traffic?
Which three statements accurately describe Decryption Mirror? (Choose three.)
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
What are three tasks that cannot be configured from Panorama by using a template stack? (Choose three.)
A firewall administrator to have visibility on one segment of the company network. The traffic on the segment is routed on the Backbone switch. The administrator is planning to apply security rules on segment X after getting the visibility. There is already a PAN-OS firewall used in L3 mode as an internet gateway, and there are enough system resources to get extra traffic on the firewall. The administrator needs to complete this operation with minimum service interruptions and without making any IP changes. What is the best option for the administrator to take?
After importing a pre-configured firewall configuration to Panorama, what step is required to ensure a commit/push is successful without duplicating local configurations?
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two.)
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
What action does a firewall take when a Decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an interal syslog server. Where can the firewall engineer define the data to be added into each forwarded log?
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
When you troubleshoot an SSL Decryption issue, which PAN-OS CL1 command do you use to check the details of the Forward Trust certificate. Forward Untrust certificate, and SSL Inbound Inspection certificate?
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
A firewall administrator manages sets of firewalls which have two unique idle timeout values. Datacenter firewalls needs to be set to 20 minutes and BranchOffice firewalls need to be set to 30 minutes. How can the administrator assign these settings through the use of template stacks?
Which log type is supported in the Log Forwarding profile?
An engineer is configuring Packet Buffer Protection on ingress zones to protect from single-session DoS attacks.
Which sessions does Packet Buffer Protection apply to?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
An administrator is creating a new Dynamic User Group to quarantine users for suspicious activity.
Which two objects can Dynamic User Groups use as match conditions for group membership? (Choose two.)
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
ln a security-first network, what is the recommended threshold value for apps and threats to be dynamically updated?
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
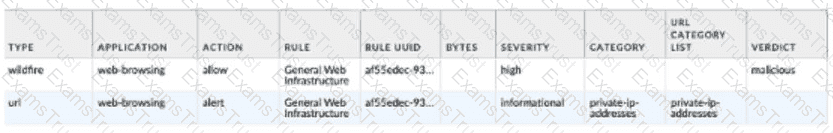
Given the following snippet of a WildFire submission log did the end-user get access to the requested information and why or why not?
A standalone firewall with local objects and policies needs to be migrated into Panorama. What procedure should you use so Panorama is fully managing the firewall?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all."
Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?'
A firewall administrator has confirm reports of a website is not displaying as expected, and wants to ensure that decryption is not causing the issue. Which three methods can the administrator use to determine if decryption is causing the website to fail? (Choose three.)
An administrator is building Security rules within a device group to block traffic to and from malicious locations.
How should those rules be configured to ensure that they are evaluated with a high priority?
Which protocol is supported by GlobalProtect Clientless VPN?
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an internal syslog server.
Where can the firewall engineer define the data to be added into each forwarded log?
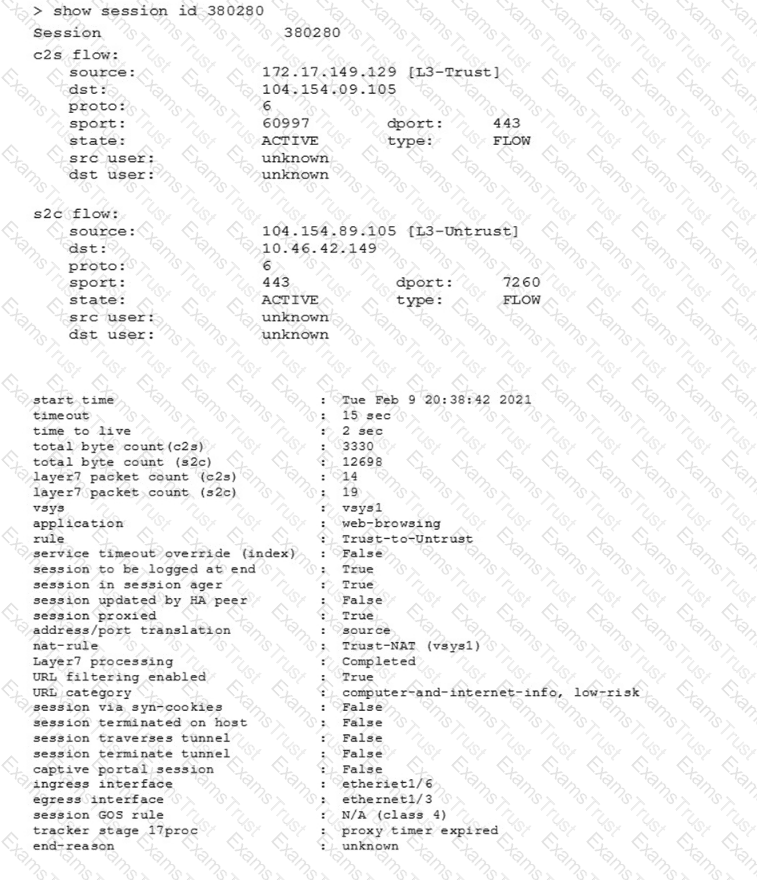
Which two statements correctly describe Session 380280? (Choose two.)
After switching to a different WAN connection, users have reported that various websites will not load, and timeouts are occurring. The web servers work fine from other locations.
The firewall engineer discovers that some return traffic from these web servers is not reaching the users behind the firewall. The engineer later concludes that the maximum transmission unit (MTU) on an upstream router interface is set to 1400 bytes.
The engineer reviews the following CLI output for ethernet1/1.
Which setting should be modified on ethernet1/1 to remedy this problem?
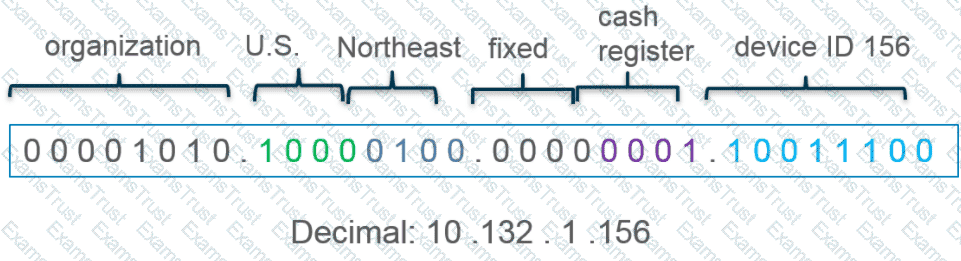
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
Which statement regarding HA timer settings is true?
How can Panorama help with troubleshooting problems such as high CPU or resource exhaustion on a managed firewall?
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories
Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
Refer to Exhibit:
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
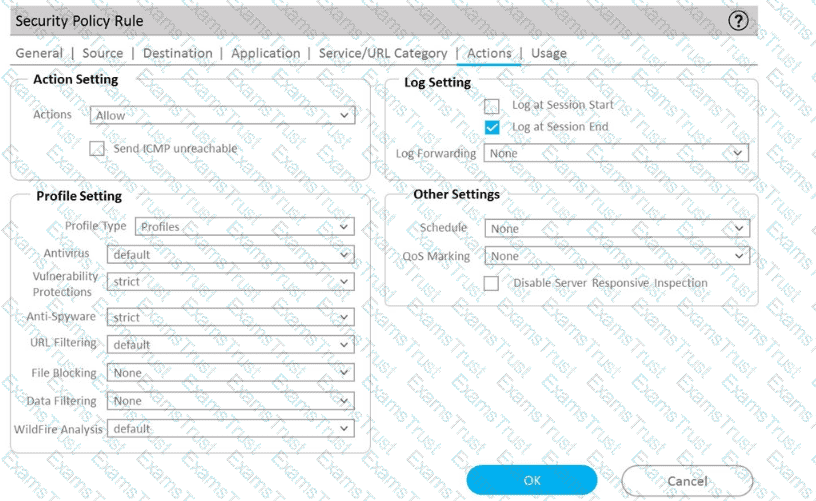
B)
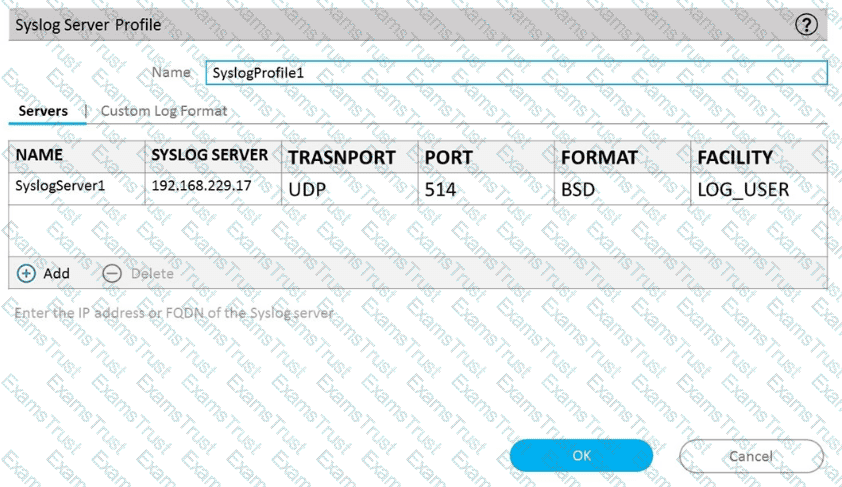
C)
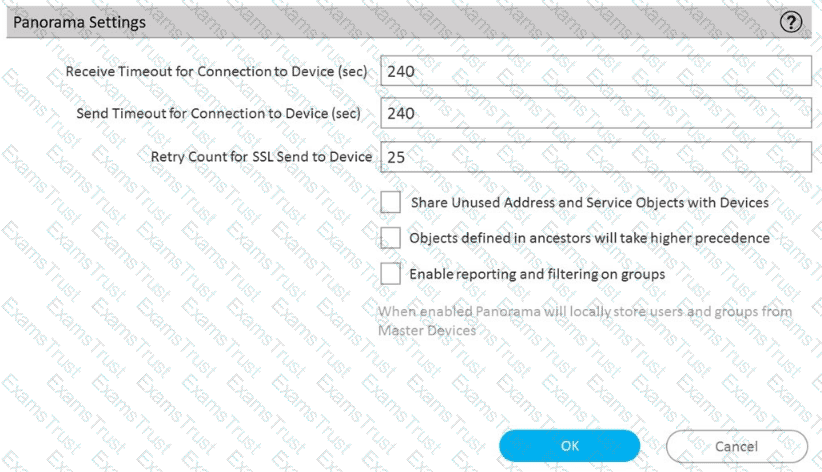
D)
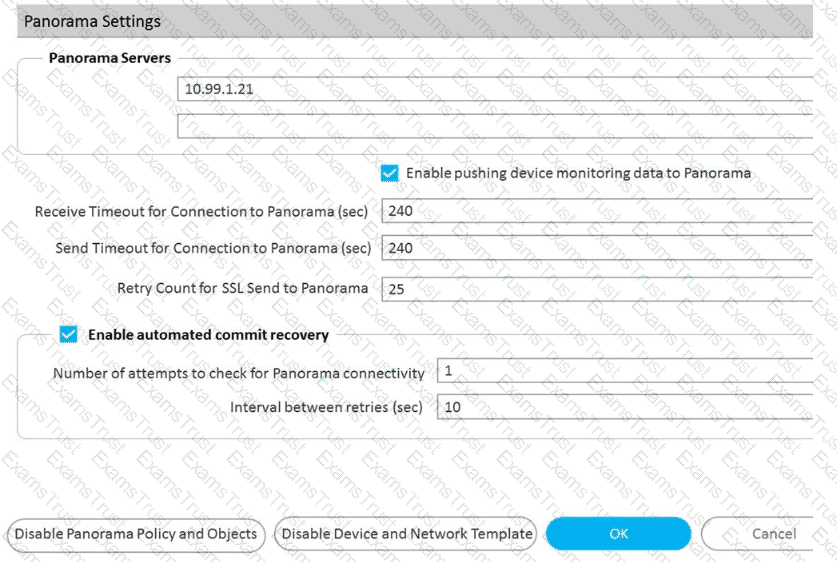
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
What happens when an A/P firewall pair synchronizes IPsec tunnel security associations (SAs)?
Which source is the most reliable for collecting User-ID user mapping?
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow. Upon opening the newly created packet capture, the administrator still sees traffic for the previous filter.
What can the administrator do to limit the captured traffic to the newly configured filter?
An administrator pushes a new configuration from Panorama to a par of firewalls that are configured as an active/passive HA pair. Which NGFW receives the from Panorama?
An engineer is bootstrapping a VM-Series Firewall Other than the /config folder, which three directories are mandatory as part of the bootstrap package directory structure? (Choose three.)
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
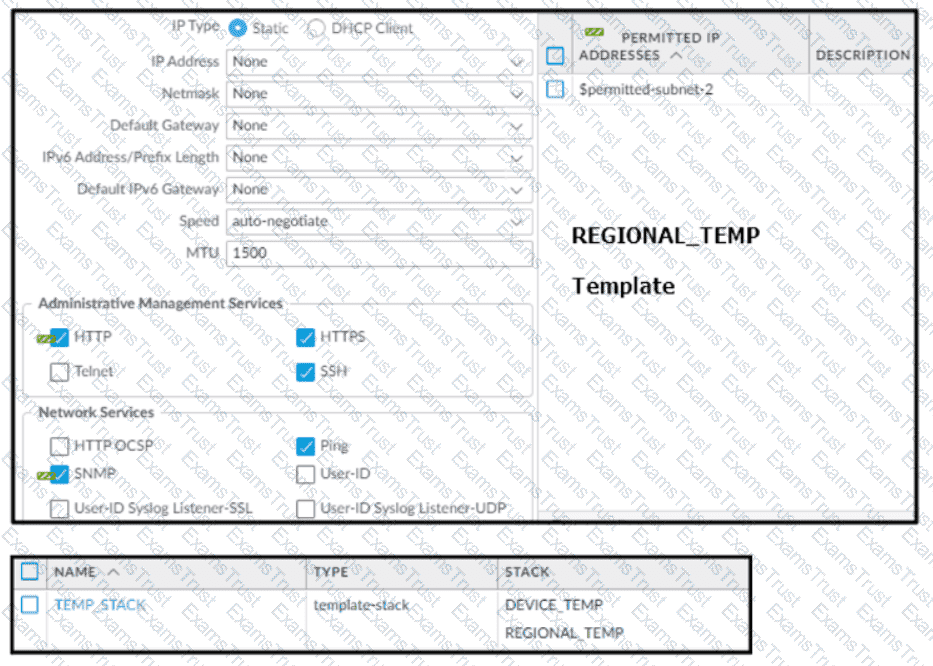
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
Which tool can gather information about the application patterns when defining a signature for a custom application?
When using certificate authentication for firewall administration, which method is used for authorization?