What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 8.1 version?
An administrator accidentally closed the commit window/screen before the commit was finished. Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
A)

B)
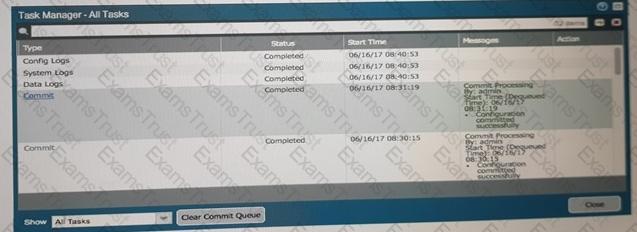
C)
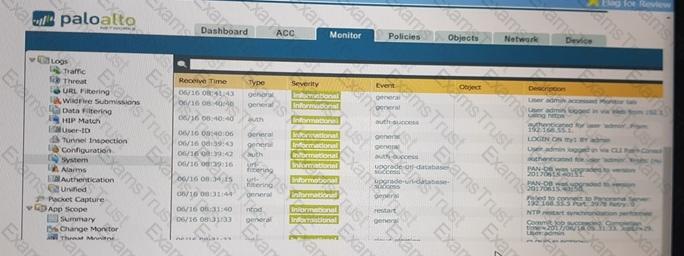
D)
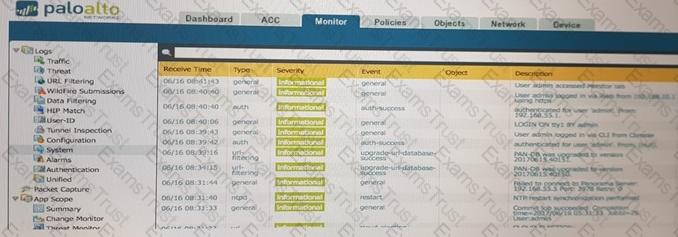
If the firewall is configured for credential phishing prevention using the "Domain Credential Filter" method, which login will be detected as credential theft?
An administrator pushes a new configuration from panorama to a pair of firewalls that are configured as active/passive HA pair.
Which NGFW receives the configuration from panorama?
Which option would an administration choose to define the certificate and protect that Panorama and its managed devices uses for SSL/ITS services?
A Palo Alto Networks NGFW just submitted a file lo WildFire tor analysis Assume a 5-minute window for analysis. The firewall is configured to check for verdicts every 5 minutes.
How quickly will the firewall receive back a verdict?
An administrator is using Panorama and multiple Palo Alto NetworksNGFWs. After upgrading all devices to the latest PAN-OS® software, the administrator enables logs forwarding from the firewalls to panorama Pre-existing logs from the firewall are not appearing in Panorama.
Which action would enables the firewalls to sendtheir preexisting logs to Panorama?
An administrator using an enterprise PKI needs to establish a unique chain of trust to ensure mutual authentication between panorama and the managed firewall and Log Collectors. How would the administrator establish the chain of trust?
Which virtual router feature determines if a specific destination IP address is reachable'?
When is the content inspection performed in the packet flowprocess?
An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on any port. Which log entry can the administrator use to verify that sessions are being decrypted?