A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
In which two ways can Prisma Cloud images be retrieved in Prisma Cloud Compute Self-Hosted Edition? (Choose two.)
Which statement applies to Adoption Advisor?
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant’s existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which option shows the steps required during the alert rule creation process to achieve this objective?
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
Where can Defender debug logs be viewed? (Choose two.)
On which cloud service providers can new API release information for Prisma Cloud be received?
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
Given the following audit event activity snippet:
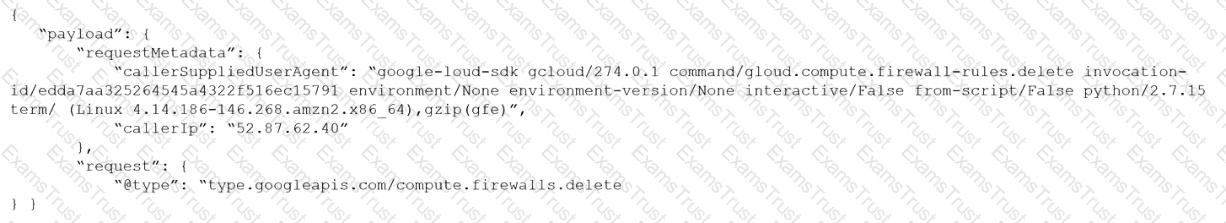
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
Which policy type should be used to detect and alert on cryptominer network activity?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
Which two integrated development environment (IDE) plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
What are the two ways to scope a CI policy for image scanning? (Choose two.)
Which report includes an executive summary and a list of policy violations, including a page with details for each policy?
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
Which step is included when configuring Kubernetes to use Prisma Cloud Compute as an admission controller?
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day.
Which area on the Console will provide input on this issue?
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
Which two integrations enable ingesting host findings to generate alerts? (Choose two.)
How is the scope of each rule determined in the Prisma Cloud Compute host runtime policy?
Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
What is the primary purpose of Prisma Cloud Code Security?
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
Which options show the steps required after upgrade of Console?
Which Prisma Cloud policy type detects port scanning activities in a customer environment?
Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three).
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
What are the subtypes of configuration policies in Prisma Cloud?
Which statement accurately characterizes SSO Integration on Prisma Cloud?
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
Which role does Prisma Cloud play when configuring SSO?
Which policy type in Prisma Cloud can protect against malware?
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
Which two frequency options are available to create a compliance report within the console? (Choose two.)
A customer has multiple violations in the environment including:
User namespace is enabled
An LDAP server is enabled
SSH root is enabled
Which section of Console should the administrator use to review these findings?
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
What is required for Prisma Cloud to successfully execute auto-remediation commands?
Which statement about build and run policies is true?
What are two alarm types that are registered after alarms are enabled? (Choose two.)
Which three elements are part of SSH Events in Host Observations? (Choose three.)
What factor is not used in calculating the net effective permissions for a resource in AWS?
Which IAM RQL query would correctly generate an output to view users who enabled console access with both access keys and passwords?
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
Which three types of runtime rules can be created? (Choose three.)
Which three types of buckets exposure are available in the Data Security module? (Choose three.)
What is an example of an outbound notification within Prisma Cloud?
A customer wants to scan a serverless function as part of a build process. Which twistcli command can be used to scan serverless functions?
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
Given this information:
The Console is located at The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
Which ban for DoS protection will enforce a rate limit for users who are unable to post five (5) “. tar.gz" files within five (5) seconds?
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
Which ROL query is used to detect certain high-risk activities executed by a root user in AWS?
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
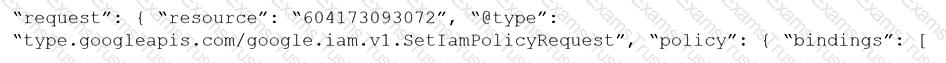
B)
C)
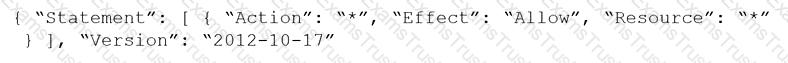
D)

Where can a user submit an external new feature request?
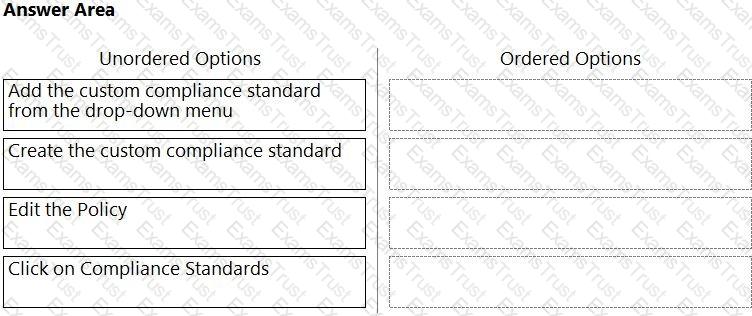
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
An administrator sees that a runtime audit has been generated for a host. The audit message is:
“Service postfix attempted to obtain capability SHELL by executing /bin/sh /usr/libexec/postfix/postfix- script.stop. Low severity audit, event is automatically added to the runtime model”
Which runtime host policy rule is the root cause for this runtime audit?
What happens when a role is deleted in Prisma Cloud?
An administrator needs to detect and alert on any activities performed by a root account.
Which policy type should be used?
Which of the following is a reason for alert dismissal?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
The development team wants to block Cross Site Scripting attacks from pods in its environment. How should the team construct the CNAF policy to protect against this attack?
What is the function of the external ID when onboarding a new Amazon Web Services (AWS) account in Prisma Cloud?
The attempted bytes count displays?
Which RQL query will help create a custom identity and access management (1AM) policy to alert on Lambda functions that have permission to terminate EC2 instances?