As an Autonomous Transaction Processing (ATP) database administrator, you want to extend the storage capacity In the database.
Examine this command and output from the database:
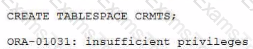
What is the reason for the error?
What does the Application Data Modeling module of the Oracle Data Masking and Subsetting Pack search for?
To avoid hard coding passwords in scripts, you have elected to create an external password store-Examine this list of steps:
1. Set the external password store wallet location.
ALTER SYSTEM SET EXTERNAL_KEYSTORE_CREDENTIAL_LOCATION = "/•tc/ORACLE/WALLETS/orcl/external_Btore" SCOPE c SPFILE;
2. Log in as a user who has syskm privileges.
3. Create an auto-logln keystore that contains the keystore password including the add secret clause.
ADMINISTER KEY MANAGEMENT ADD SECRET 'password'
FOR CLIENT 'TDE_WALLET'
TO LOCAL AUTO_LOGIH KEYSTORE '/etc/0RACLE/WALLETS/orcl/extemal_store';
4. Restart the database instance as sysdba.
SHUTDOWN IMMEDIATE STARTUP
5. Create an auto-logln keystore that contains the keystore password.
ADMINISTER KEY MANAGEMENT
FOR CLIENT 'TDE_WALLET'
TO LOCAL AUTO_L0GIN KEYSTORE ' /etc/ORACLE/WALLETS/orcl/external_store' ;
6. Set an Encryption Key.
ADMINISTER KEY MANAGEMENT SET ENCRYPTION KEY IDENTIFIED BY keystore_password WITH BACKUP
Identify the minimum number of steps in the correct order that must be performed to create the external password store.
Examine this statement and its result:
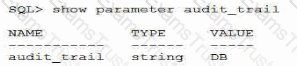
You issue this statement and then restart the database instance:

Which Is true about generated audit records?
Examine these commands and the output used to configure Real Application Security:
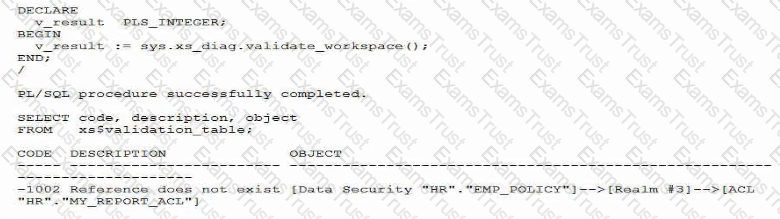
What does this output mean?
Which statement can be used to force password complexity in the password file?
Which two configurations can be used to protect sensitive data In a database?
Which three authentication methods are available with Centrally Managed Users (CMU)?
Examine this command that Is executed:
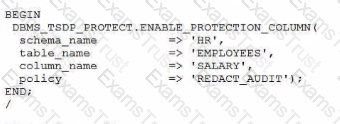
What is the result?
Using Unified Audit, you must determine who performed an pkan backup ot recovery operations on a database.
You are connected as sysdba.
Which statement(s) achieve this?
A)

B)
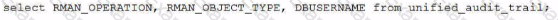
C)

D)

E)

You must rekey encrypted sensitive credential data In your database.
You run the command alter database dictionary rekey credentials.
Which three options ate true about the bkkey process?
You are required to remove embedded passwords from scripts that connect to database instances. Which tool can be used to implement this requirement?
Database Vault realm r protects all tables In the fin schema from DBA access User fin is configured as the owner in realm R.
You must also prevent access to realm r protected tables by user FIN. Which achieves this?