You are implementing Netskope Cloud Exchange in your company lo include functionality provided by third-party partners. What would be a reason for using Netskope Cloud Risk Exchange in this scenario?
Your customer is currently using Directory Importer with Active Directory (AD) to provision users to Nelskope. They have recently acquired three new companies (A. B. and C) and want to onboard users from the companies onto the NetsKope platform. Information about the companies is shown below.
- Company A uses Active Directory.
-- Company B uses Azure AD.
-- Company C uses Okta Universal Directory.
Which statement is correct in this scenario?
Review the exhibit.
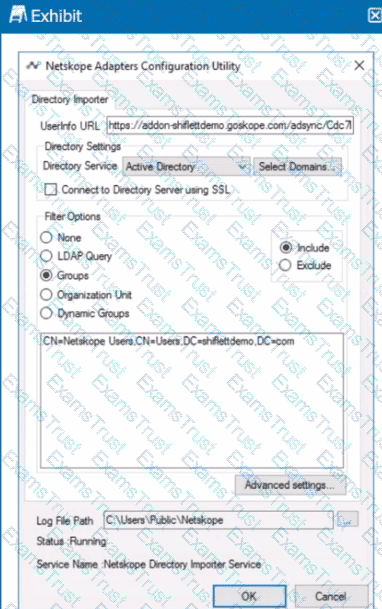
You installed Directory Importer and configured it to import specific groups ot users into your Netskope tenant as shown in the exhibit. One hour after a new user has been added to the domain, the user still has not been provisioned to Netskope.
What are three potential reasons for this failure? (Choose three.)
Review the exhibit.
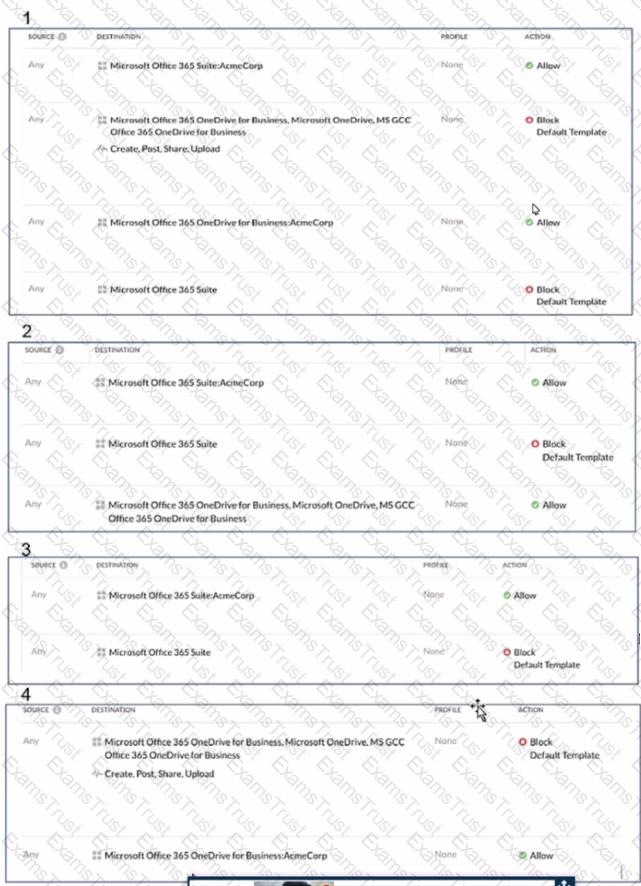
AcmeCorp has recently begun using Microsoft 365. The organization is concerned that employees will start using third-party non-AcmeCorp OneDrive instances to store company data. The CISO asks you to use Netskope to create a policy that ensures that no data is being uploaded to non-AcmeCorp instances of OneDrive.
Referring to the exhibit, which two policies would accomplish this posture? (Choose two.)
Your Netskope Client tunnel has connected to Netskope; however, the user is not receiving any steering or client configuration updates What would cause this issue?
You successfully configured Advanced Analytics to identify policy violation trends Upon further investigation, you notice that the activity is NULL. Why is this happening in this scenario?
Review the exhibit.

A user has attempted to upload a file to Microsoft OneDrive that contains source code with Pll and PCI data.
Referring to the exhibit, which statement Is correct?
You do not want a scheduled Advanced Analytics dashboard to be automatically updated when Netskope makes improvements to that dashboard. In this scenario, what would you do to retain the original dashboard?
Review the exhibit.

You are attempting to block uploads of password-protected files. You have created the file profile shown in the exhibit.
Where should you add this profile to use in a Real-time Protection policy?
You want to verify that Google Drive is being tunneled to Netskope by looking in the nsdebuglog file. You are using Chrome and the Netskope Client to steer traffic. In this scenario, what would you expect to see in the log file?
A)

B)
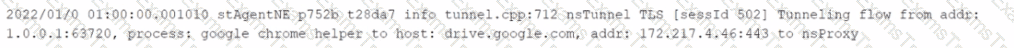
C)
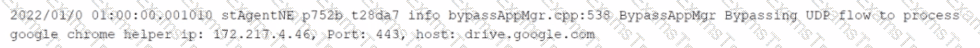
D)

Your CISO asks that you to provide a report with a visual representation of the top 10 applications (by number of objects) and their risk score. As the administrator, you decide to use a Sankey visualization in Advanced Analytics to represent the data in an efficient manner.
In this scenario, which two field types are required to produce a Sankey Tile in your report? {Choose two.)
Your client is an NG-SWG customer. They are going to use the Explicit Proxy over Tunnel (EPoT) steering method. They have a specific list of domains that they do not want to steer to the Netskope Cloud.
What would accomplish this task''
You have deployed Netskope to all users of the organization and you are now ready to begin ingesting all events, alerts, and Web transactions into your SIEM as a part of your requirements.
What are three ways in which you would accomplish this task? (Choose three.)
You are using Netskope CSPM for security and compliance audits across your multi-cloud environments. To decrease the load on the security operations team, you are researching how to auto-re mediate some of the security violations found in low-risk environments.
Which statement is correct in this scenario?
You are deploying the Netskope Client to Windows devices. The following command line would be used to install the client MSI file:

In this scenario, what is
You want to see all instances of malware that were detected by the Netskope Cloud Sandbox.
Which process would you use to achieve this task in the Netskope tenant UI?
You configured a pair of IPsec funnels from the enterprise edge firewall to a Netskope data plane. These tunnels have been implemented to steer traffic for a set of defined HTTPS SaaS applications accessed from end-user devices that do not support the Netskope Client installation. You discover that all applications steered through this tunnel are non-functional.
According to Netskope. how would you solve this problem?
You need to extract events and alerts from the Netskope Security Cloud platform and push it to a SIEM solution. What are two supported methods to accomplish this task? (Choose two.)
You are the network architect for a company using Netskope Private Access. Multiple users are reporting that they are unable to access an application using Netskope Private Access that was working previously. You have verified that the Real-time Protection policy allows access to the application, private applications are steered for the users, and the application is reachable from internal machines. You must verify that the application is reachable through Netskope Publisher
In this scenario, which two tools in the Netskope Ul would you use to accomplish this task? (Choose two.)
You have multiple networking clients running on an endpoint and client connectivity is a concern. You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?