Click the Exhibit button.
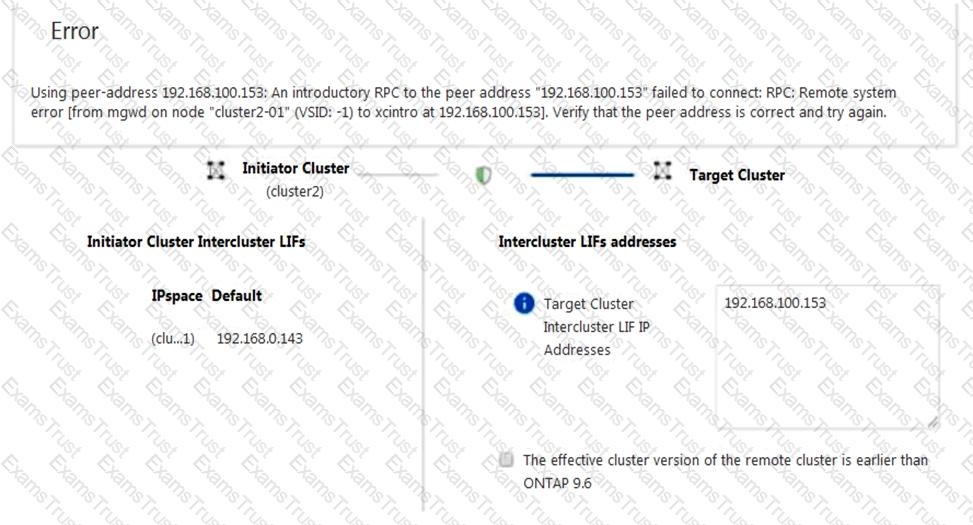
You are configuring cluster peering from cluster2 to cluster1 on your ONTAP 9.7 clusters using ONTAP System Manager. You are given the details shown below to set up the cluster peer relationship. You want to determine why the peering has failed.
Cluster2 intercluster LIFIP: 192.168.0.143 Subnet: 255.255.255.0 Port: e0e passphrase: netapp1234
Cluster1 intercluster LIF IP: 192.168.0.153 Subnet: 255.255.255.0 Port: e0e passphrase: netapp1234
Referring to the exhibit, which statement is correct?
You are configuring a SnapMirror replication between a source volume with adaptive compression enabled and a destination volume with secondary compression enabled.
In this scenario; which statement is correct?
Click the Exhibit button.
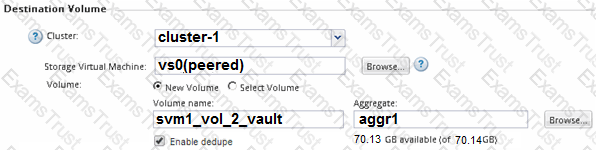
An employee’s computer and mapped home folder has been encrypted with ransomware. You are asked to restore the data from a SnapVault repository.
Referring to the exhibit, what happens when the volume is restored?
What are two ways to determine if yourSnapMirror relationships are up-to-date? (Choose two.)
You want to ensure that you are using compatible hardware and software versions with your MetroCluster installation. Which tool would accomplish this task?
A customer has a 2-node ONTAP Select HA cluster deployed on the same site. The ONTAP Deploy VM has been accidentally deleted. The 2-node ONTAP Select HA cluster is still serving data, but the storage failover capability has been disabled.
In this scenario, what would you do to reestablish the storage failover capability on your cluster?
Your customer wants to implement SVM DR, but the customer is not certain whether theidentity-preserve parameter should be enabled. The customer explains that the source and destination clusters are in different network subnets.
In this scenario, which SVM DR solution should the customer use?
You have a NAS volume containing 100 GB of data and daily change rate of 10%. You want to keep seven daily Snapshot copies. What is the minimum size for the volume?
To assist with capacity planning, your supervisor wants to receive weekly capacity summaryreports using e- mail for all on-premises ONTAP clusters. You are asked to implement a solution that has no additional software licensing costs.
Which action accomplishes this task?
After deploying an ONTAP Select 2 node HA cluster at a remote site, you successfully perform manual takeover and giveback before placing the cluster into production. After the cluster runs in production for a week, you notice that you can no longer perform a manual takeover.
In this scenario, what are two causes of this problem? (Choose two.)
You are working for a customer that has deployed a large FlexGroup with ONTAP 9.5. This FlexGroup has a SnapMirror relationship to a system at a disaster recovery site. The FlexGroup is nearly full and needs to be expanded to accommodate additional data.
In this scenario, what must you do to expand the FlexGroup and ensure that the data remains protected?
You want to modify the existing Snapshot copy schedule to allow for more granularity in your ability to recover data after a corruption or loss.
In this scenario, which two tools allow you to accomplish this task (Choose two.)
A customer has a new cloud strategy. They want to replicate mission-critical SAN volumes to the cloud for DR. Which NetApp technology satisfies the requirement?
Which attribute does Data ONTAP use the identify Snapshot copies between primary and secondary FlexVol volumes in a SnapVault relationship?
A client has a primary data center that is located in a coastal area where the forecast is calling for a Category 5 hurricane to make landfall in three days. The client’s data is protected using NetApp SVM SnapMirror replication technology with identity-preserve that is enabled. The data is mirrored to a destination cluster outside of the affected area. The client has scheduled a controlled maintenance window for tomorrow to ensure that dependable operations are maintained.
Which three steps must be taken to accomplish this task? (Choose three.)
A customer has a MetroCluster solution and wants to automate the disaster-recovery process. The customer wants to control the switchcover between the sites.
Which NetApp tool would satisfy these requirements?
You want to create an application-consistent Snapshot copy by using SnapCenter software. What is required to accomplishthis task?
An administrator notices that a NAS volume has been filled completely by active data and Snapshot copies that have expanded over the Snap reserve. The volume is no longerwritable.
In this scenario, which two actions must you take to make the volume writable again? (Choose two.)
What are two NetApp data protection solutions? (Choose two.)
Which two NetApp features would help you to recover from a file share that was encrypted by a ransomware event? (Choose two.)
You decide to enable SnapMirror network compression on your NetApp clustered Data ONTAP environment. Which two statements are correct about enabling this feature?
(Choose two.)
Your customer needs to activate a destination SVM DRfollowing a disaster.
In this situation, which two actions should be performed? (Choose two.)
Click the Exhibit button.
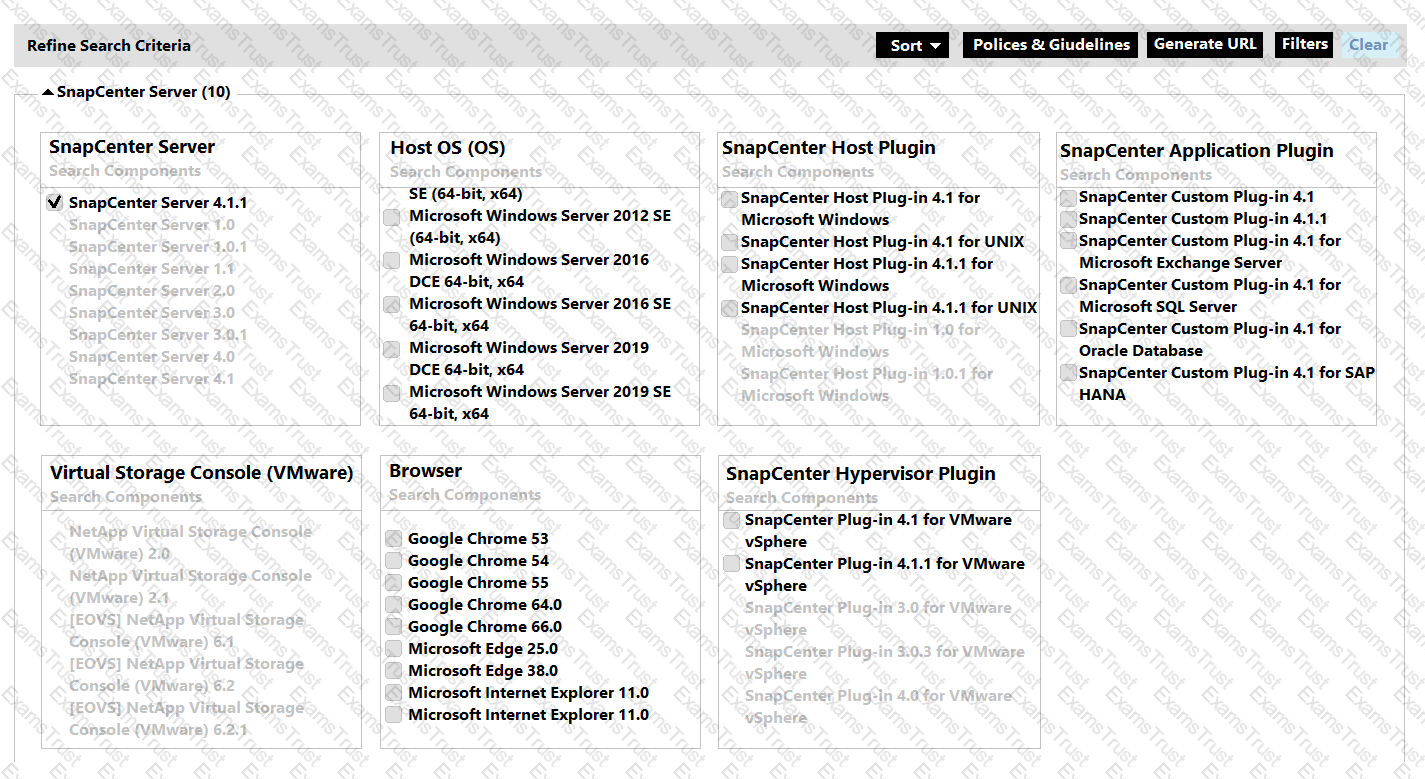
Referring to the exhibit, what two Search Criteria check boxes need to be used to provide a supported solution for protecting Windows Server 2019 DCE 64-bit, x64 host using local NetApp LUNs with SnapCenter Server 4.1.1? (Choose two.)