You have a Microsoft 365 subscription.
You identify the following data loss prevention (DLP) requirements:
• Send notifications to users if they attempt to send attachments that contain an EU Social Security Number (SSN) or Equivalent ID.
• Prevent any email messages that contain credit card numbers from being sent outside your organization.
• Block the external sharing of Microsoft OneDrive content that contains EU passport numbers.
• Send administrators email alerts if any rule matches occur.
What is the minimum number of DLP policies and rules you must create to meet the requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that contains three DOCX files named File1, File2, and File3.
You create the sensitivity labels shown in the following table.
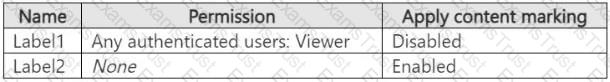
You apply the labels to the files as shown in the following table.
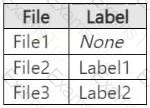
You ask Microsoft 365 Copilot to summarize the files, and you receive the results shown in the following table.
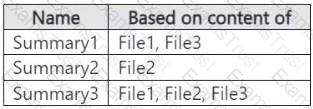
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 tenant.
You have a database that stores customer details. Each customer has a unique 13-digit identifier that consists of a fixed pattern of numbers and letters.
You need to implement a data loss prevention (DLP) solution that meets the following requirements:
● Email messages that contain a single customer identifier can be sent outside your company.
● Email messages that contain two or more customer identifiers must be approved by the company's data privacy team.
Which two components should you include in the solution? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft J65 subscription linked to a Microsoft Entra tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which role should you assign to User1?
You have a Microsoft 365 tenant.
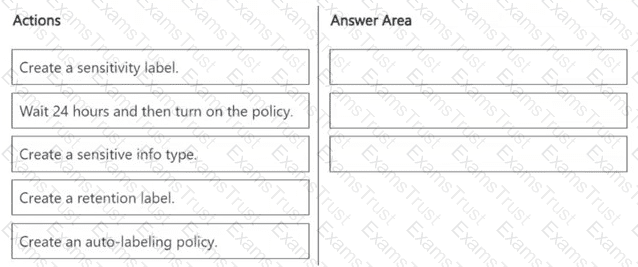
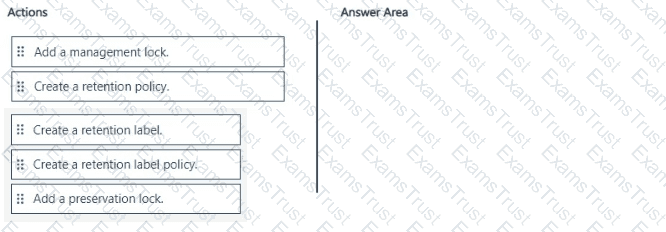
A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone.
You need to implement the regulatory requirement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
HOTSPOT
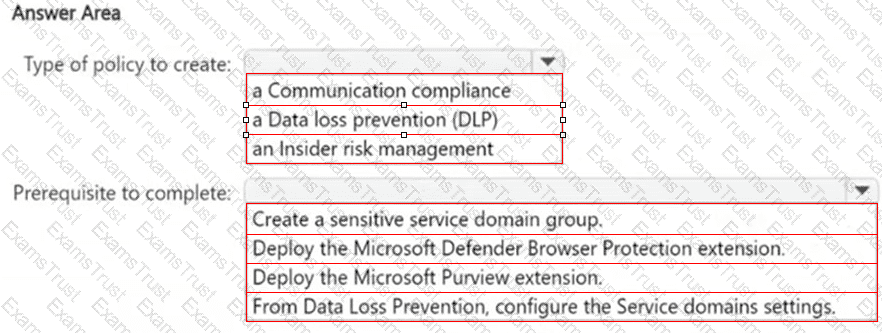
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You need ensure that an incident will be generated when a user visits a phishing website.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You create and run a content search from the Microsoft Purview portal.
You need to download the results of the content search.
What should you obtain first?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-MailboxFolderPermission -Identity "User1" -User User1@contoso.com -AccessRights Owner command.
Does that meet the goal?
You have a Microsoft 365 E5 subscription that contains two users named User! and User2.
You need to implement insider risk management. The solution must meet the following requirements:
• Ensure that User1 can create insider risk management policies.
• Ensure that User2 can use content captured by using insider risk management policies
• Follow the principle of least privilege.
To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each role group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to provide a user with the ability to view data loss prevention (DIP) alerts in the Microsoft Purview portal. The solution must use the principle of least privilege.
Which role should you assign to the user?
You have a Microsoft 365 E5 subscription that contains a user named User1. You deploy Microsoft Purview Data Security Posture Management for AD (DSPM for AD). You need to ensure that User1 can verify the auditing status of the subscription. The solution must follow the principle of least privilege. To which role group should you add User1?
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3 and a file named Filetdocx.
You create a sensitivity label named Label1 as shown in the following exhibit.

You apply Label1 to File1.
For which users can Microsoft 365 Copilot summarize File1?
You have a Microsoft 365 E5 tenant.
You have sensitivity labels as shown in the Sensitivity Labels exhibit. (Click the Sensitivity Labels tab.)

The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content.
The sensitivity labels ate published as shown in the Published exhibit. (Click the Published tab.)
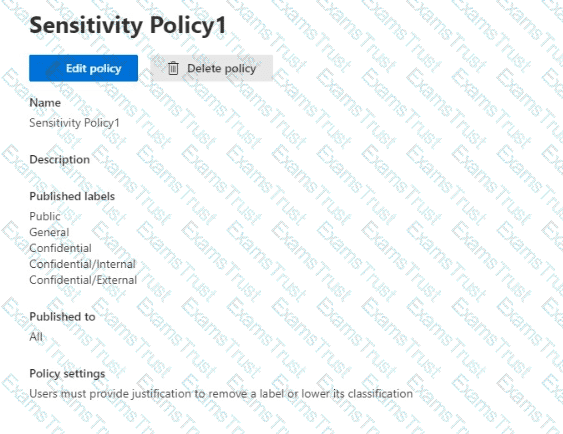
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that contains three users named U$er1, User2, and User3. The subscription contains the groups shown in the following table.
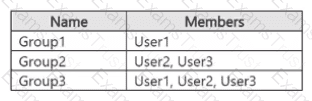
The subscription contains the devices shown in the following table.
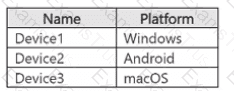
All the devices are onboarded to Microsoft Purview.
You have the data loss prevention (DLP) policies shown in the following table.
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes.
You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible.
What should you do?
You have a Microsoft 365 E5 tenant that contains a user named User1. User1 is assigned the Compliance Administrator role. User1 cannot view the regular expression in the IP Address sensitive info type. You need to ensure that User! can view the regular expression. What should you do?
You are implementing Microsoft Purview Advanced Message Encryption for a Microsoft 365 tenant named contoso.com You need to meet the following requirements:
• All email to a domain named (abrikam.com must be encrypted automatically.
• Encrypted emails must expire seven days after they are sent
What should you configure for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that contains a device named Device1.
You need to enable Endpoint data loss prevention (Endpoint DLP) for Device1.
What should you do first in the Microsoft Purview portal?
You have a Microsoft 36S subscription that contains the sensitive information types (SITs) shown in the following exhibit.
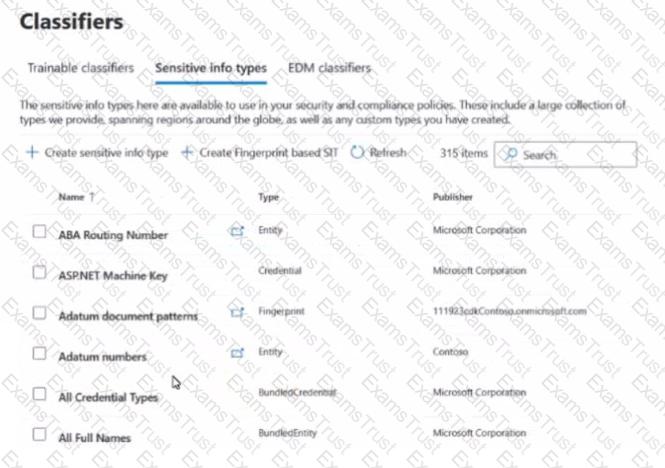
Use the drop-down menus To select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct flection is worth one point.

HOTSPOT
You have a Microsoft 365 E5 subscription that contains two Microsoft 365 groups named Group1 and Group2. Both groups use the following resources:
● A group mailbox
● Microsoft Teams channel messages
● A Microsoft SharePoint Online teams site
You create the objects shown in the following table.

To which resources will AutoApply1 and Retention1 be applied? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

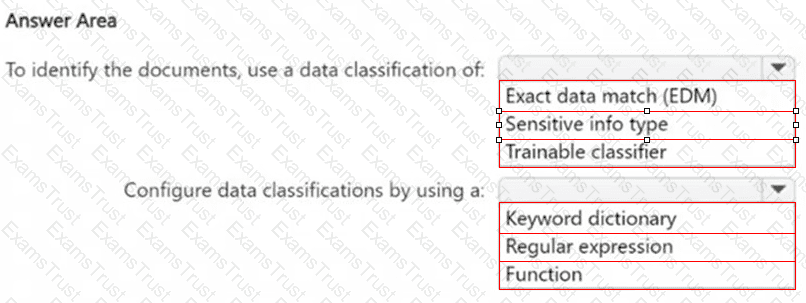
You have a Microsoft 365 E5 subscription.
You need to identify documents that contain patent application numbers containing the letters PA followed by eight digits, for example, PA 12345678. The solution must minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses retention label policies.
You need to identify all the changes made to retention labels during the last 30 days.
What should you use in the Microsoft Purview portal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folder path to the file path exclusions.
Does this meet the goal?
You have a Microsoft 365 tenant that uses Microsoft Teams.
You create a data loss prevention (DLP) policy to prevent Microsoft Teams users from sharing sensitive information. You need to identify which locations must be selected to meet the following requirements:
• Documents that contain sensitive information must not be shared inappropriately in Microsoft Teams.
• If a user attempts to share sensitive information during a Microsoft Teams chat session, the message must be deleted immediately.
Which three locations should you select? To answer, select the appropriate locations in the answer area
NOTE: Each correct selection is worth one point.

You are creating a custom trainable classifier to Identify organizational product codes referenced in Microsoft 36S content. You identify 300 files to use as seed content When? should you store the seed content?
You have a Microsoft 36S ES subscription that contains the devices shown in the following table.

You publish Microsoft Purview Information Protection sensitivity labels.
You plan to deploy the information protection client to the devices. The solution must ensure that the labels can be applied to sensitive images and documents
On which devices can you install the information protection client, and what should users use to apply labels? To answer, select the appropriate options in the answer area.

Your company has a Microsoft 365 tenant.
The company performs annual employee assessments. The assessment results are recorded in a document named AssessmentTemplate.docx that is created by using a Microsoft Word template. Copies of the employee assessments are sent to employees and their managers.
The assessment copies are stored in mailboxes, Microsoft SharePoint Online sites, and OneDrive folders. A copy of each assessment is also stored in a SharePoint Online folder named Assessments.
You need to create a data loss prevention (DLP) policy that prevents the employee assessments from being emailed to external users. You will use a document fingerprint to identify the assessment documents. The solution must minimize effort.
What should you include in the solution?
You have a Microsoft 36S ES subscription
You plan to create an met data match (EDM) classifier named EDM1.
You need to grant permissions to hash and upload the sensitive ^formation source table for EDMI. What should you create first?
HOTSPOT
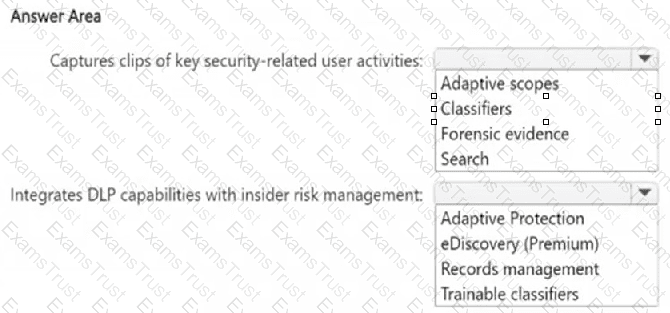
You have a Microsoft 365 E5 subscription.
You need to implement a compliance solution that meets the following requirements:
● Captures clips of key security-related user activities, such as the exfiltration of sensitive company data.
● Integrates data loss prevention (DLP) capabilities with insider risk management.
What should you use for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You plan to deploy a Defender for Cloud Apps file policy that will be triggered when the following conditions are met:
● A file is shared externally.
● A file is labeled as internal only.
Which filter should you use for each condition? To answer, drag the appropriate filters to the correct conditions. Each filter may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
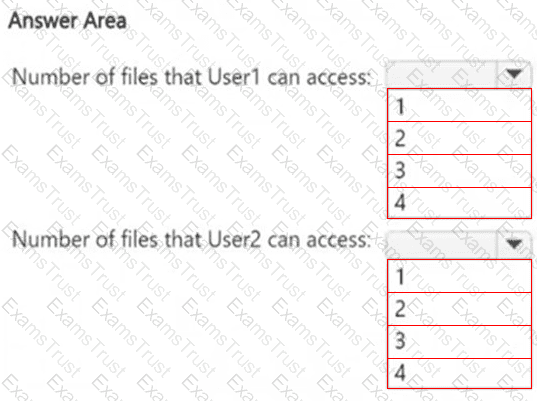
HOTSPOT
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
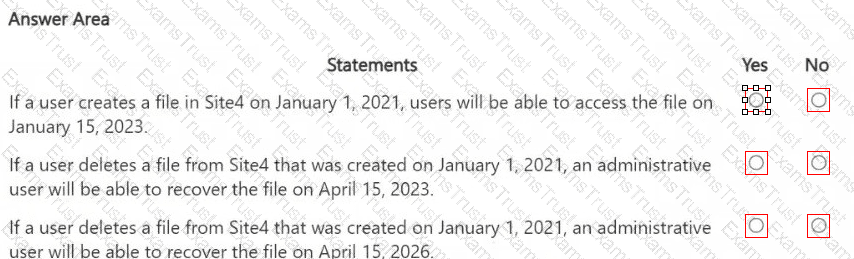
HOTSPOT
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
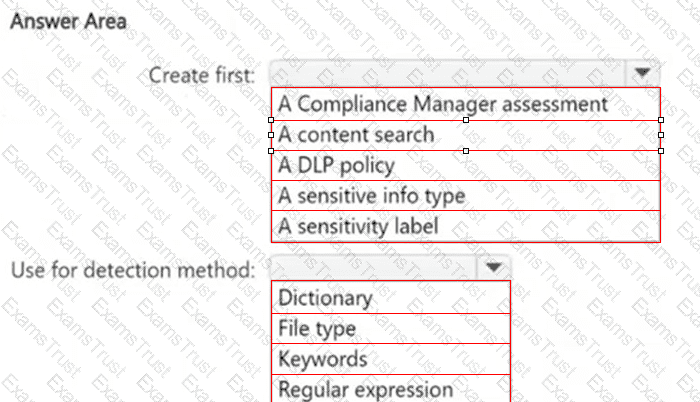
HOTSPOT
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.