You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
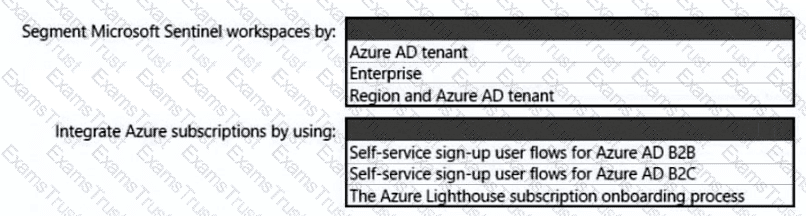
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

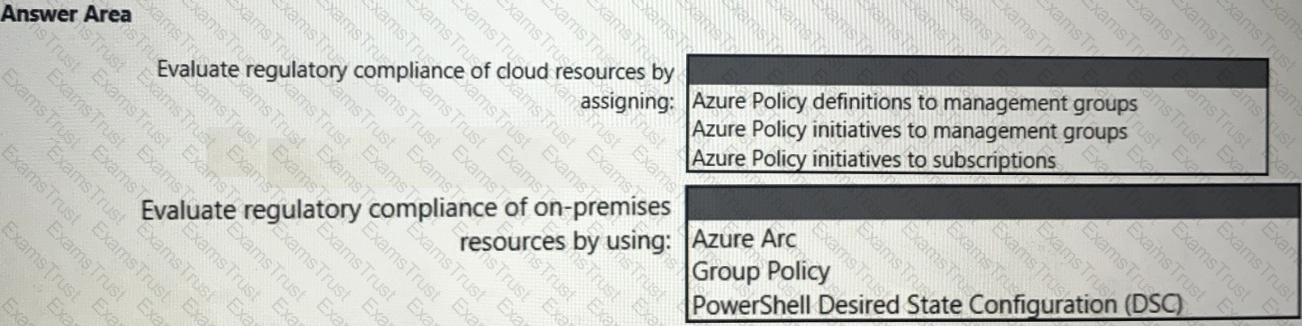
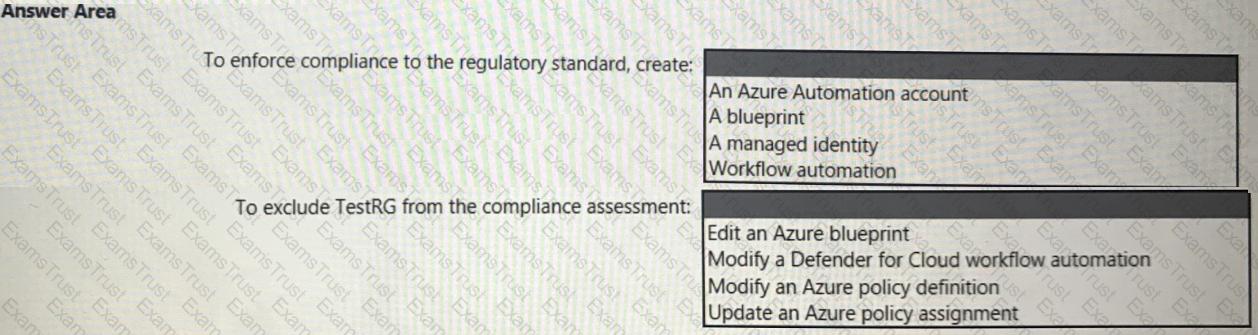
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
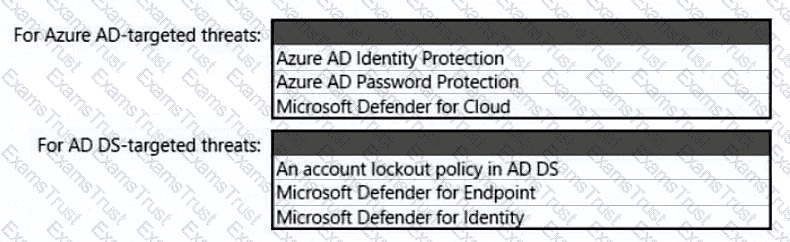
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
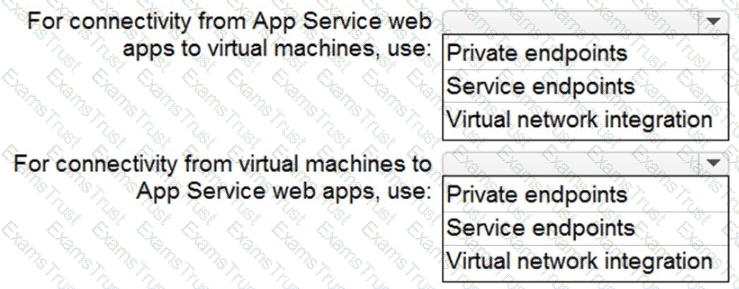
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
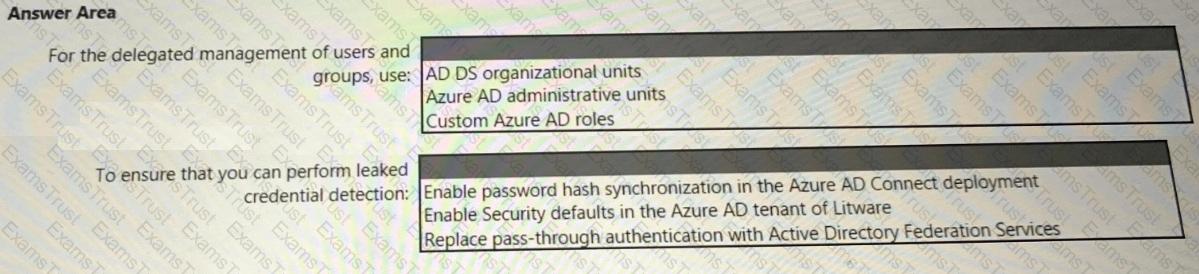
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
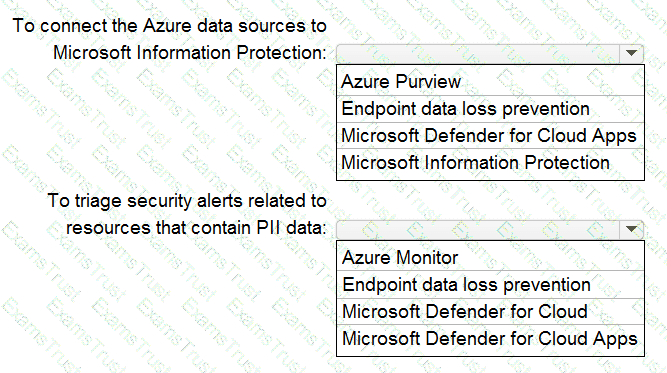
You have an Azure subscription that contains a virtual network named VNet1. VNet1 contains a 10-node virtual machine scale set that hosts a web search app named App1. Customers access App1 from the internet. The nodes establish outbound HTTP and HTTPS connections to the internet.
You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Inbound connections to App1 that contain security threats specified in the Core Rule. Set (CRS) from the Open Web Application Security Project (OWASP) must be blocked.
• Outbound HTTP and HTTPS connections from the virtual machine scale set that contain security threats identified by the Microsoft Defender Threat Intelligence (Defender Tl) feed must be blocked.
What should you include in the recommendation? To answer, select the options in the answer area,
NOTE: Each correct answer is worth one point.
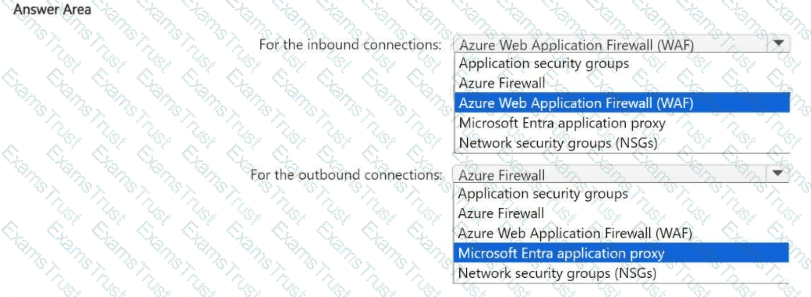
You have an Azure subscription.
You need to use a federated model in Azure API Management to control access to your organization's APIs. The solution must meet the following requirements:
• Support the use of role-based access control (RBAC) to manage the APIs.
• Support the use of keys to control the consumption of the APIs.
To which scope should you associate each control method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

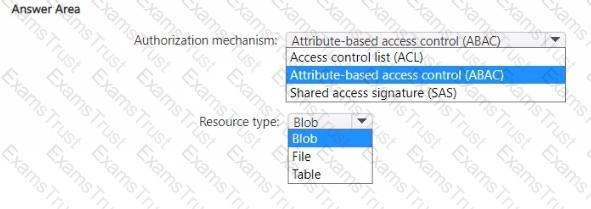
You have an Azure subscription.
You plan to deploy a storage account named storage1 that will store confidential data. You will assign tags to the confidential data.
You need to ensure that access to storage1 can be defined by using the assigned tags.
Which authorization mechanism should you enable, and which type of resource should you use to store the data? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure AD tenant that contains 10 Windows 11 devices and two groups named Group1 and Group2. The Windows 11 devices are joined to the Azure AD tenant and are managed by using Microsoft Intune.
You are designing a privileged access strategy based on the rapid modernization plan (RaMP). The strategy will include the following configurations:
• Each user in Group1 will be assigned a Windows 11 device that will be configured as a privileged access device.
• The Security Administrator role will be mapped to the privileged access security level.
• The users in Group1 will be assigned the Security Administrator role.
• The users in Group2 will manage the privileged access devices.
You need to configure the local Administrators group for each privileged access device. The solution must follow the principle of least privilege.
What should you include in the solution?
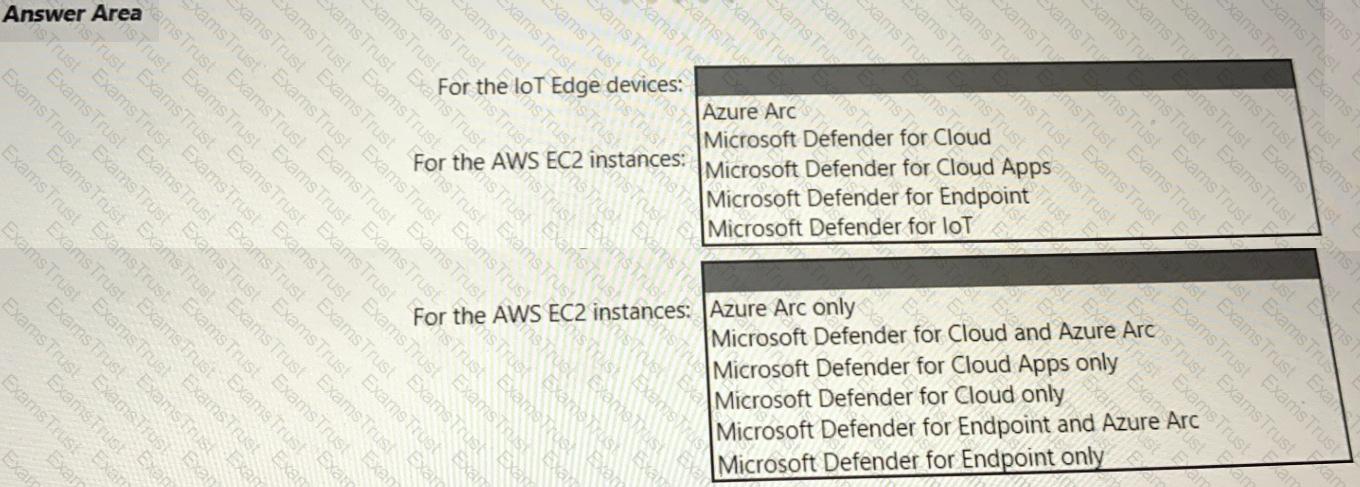
Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation. You need to recommend a security posture management solution for the following components:
• Azure loT Edge devices
• AWS EC2 instances
Which services should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company plans to follow DevSecOps best practices of the Microsoft Cloud Adoption Framework for Azure to integrate DevSecOps processes into continuous integration and continuous deployment (Cl/CD) DevOps pipelines
You need to recommend which security-related tasks to integrate into each stage of the DevOps pipelines.
What should recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

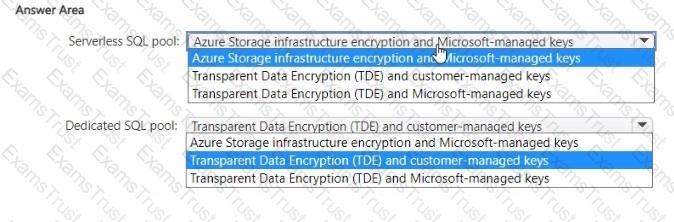
You have an Azure subscription.
You plan to implement Azure Synapse Analytics SQL dedicated pools and SQL serverless pools.
You need to recommend a solution to provide additional encryption-at-rest security for each type of pool. The solution must use customer-managed keys, whenever possible.
What should you recommend for each pool type? To answer, drag the appropriate recommendations to the correct pool types. Each recommendation may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites. What should you include in the recommendation?
You have an on-premises app named App1. Remote users access App1 by using VPN connections. You have a third-party software as a service (SaaS) app named App2. You need to deploy Global Secure Access to manage access to App1 and App2. What should you use for each app?
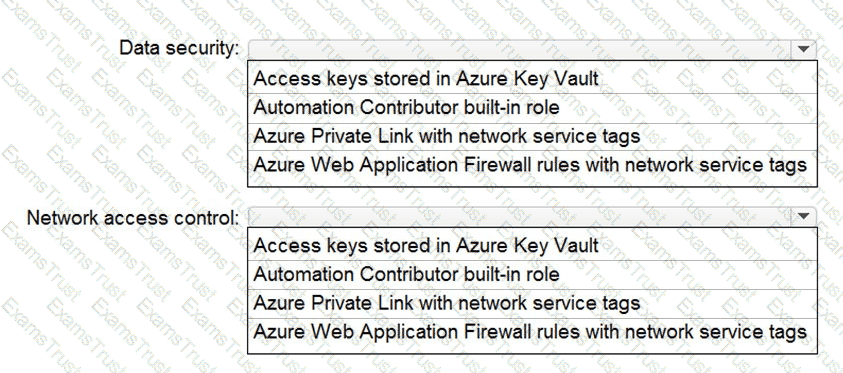
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
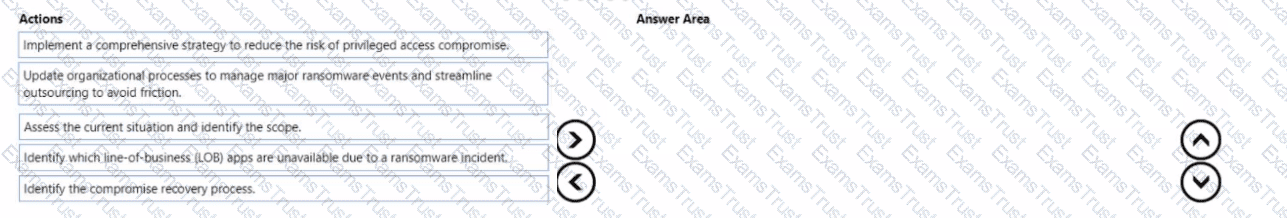
Your company wants to optimize ransomware incident investigations.
You need to recommend a plan to investigate ransomware incidents based on the Microsoft Detection and Response Team (DART) approach.
Which three actions should you recommend performing in sequence in the plan? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have multiple Azure subscriptions that each contains multiple resource groups.
You need to identify the privileged role assignments in each subscription and any associated security risks. The solution must minimize administrative effort.
What should you use?
You have an Azure subscription that contains multiple network security groups (NSGs), multiple virtual machines, and an Azure Bastion host named bastion1.
Several NSGs contain rules that allow direct RDP access to the virtual machines by bypassing bastion!
You need to ensure that the virtual machines can be accessed only by using bastion! The solution must prevent the use of NSG rules to bypass bastion1.
What should you include in the solution?
You have a Microsoft 365 subscription that contains a group named Group1. The subscription contains 1,000 Windows devices that are joined to a Microsoft Entra tenant and managed by using Microsoft Intune. All users sign in to the devices by using standard user accounts.
You plan to deploy a new app named App1 to the members of Group1. The Group1 members must have administrative rights to install new versions of App1.
You need to ensure that the Group1 members can install new versions of App1. The solution must follow the principles of Zero Trust.
What should you implement?
You have an Azure subscription that contains a resources group named RG1. RG1 contains multiple Azure Files shares.
You need to recommend a solution to deploy a backup solution for the shares. The solution must meet the following requirements:
• Prevent the deletion of backups and the vault used to store the backups.
• Prevent privilege escalation attacks against the backup solution.
• Prevent the modification of the backup retention period.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
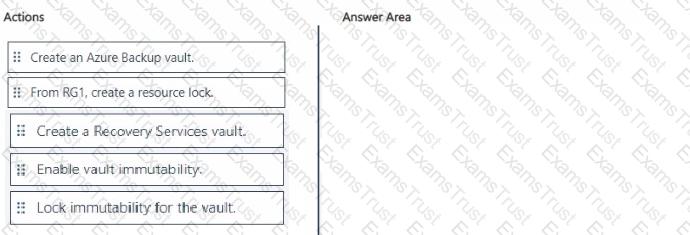
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
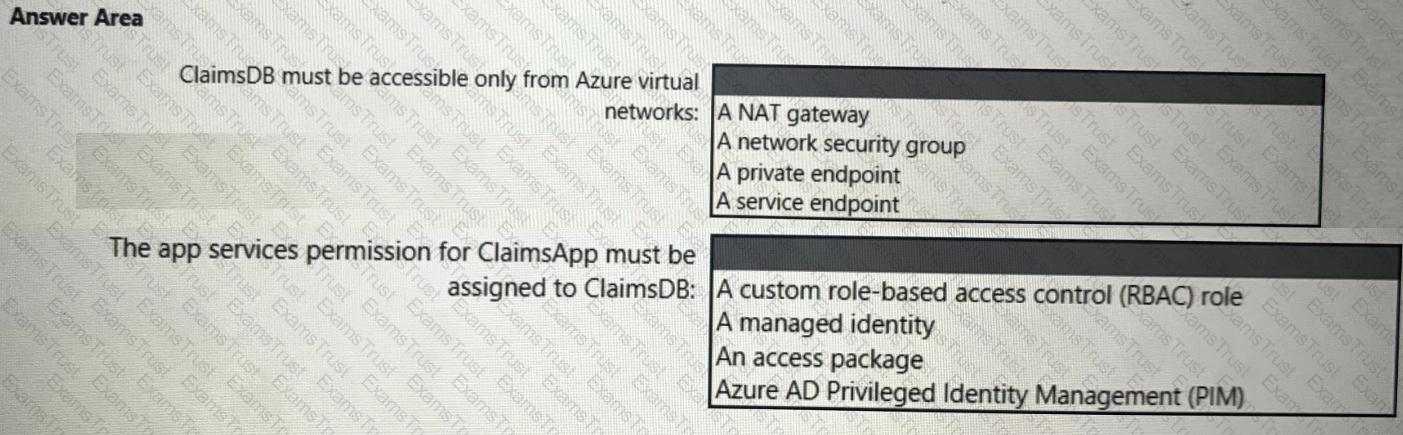
What should you create in Azure AD to meet the Contoso developer requirements?
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
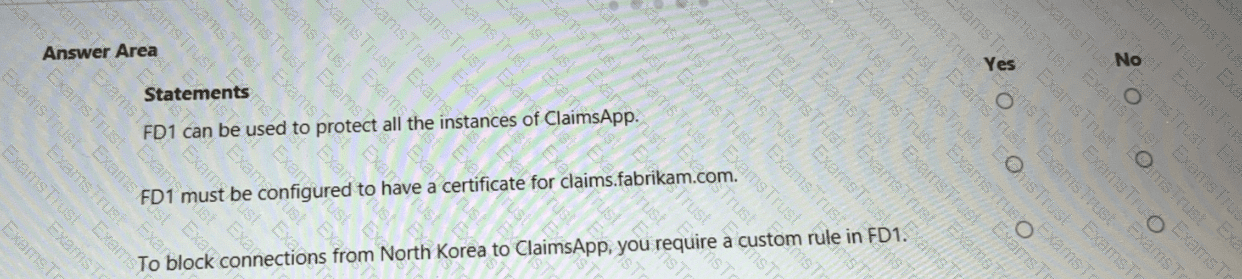
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
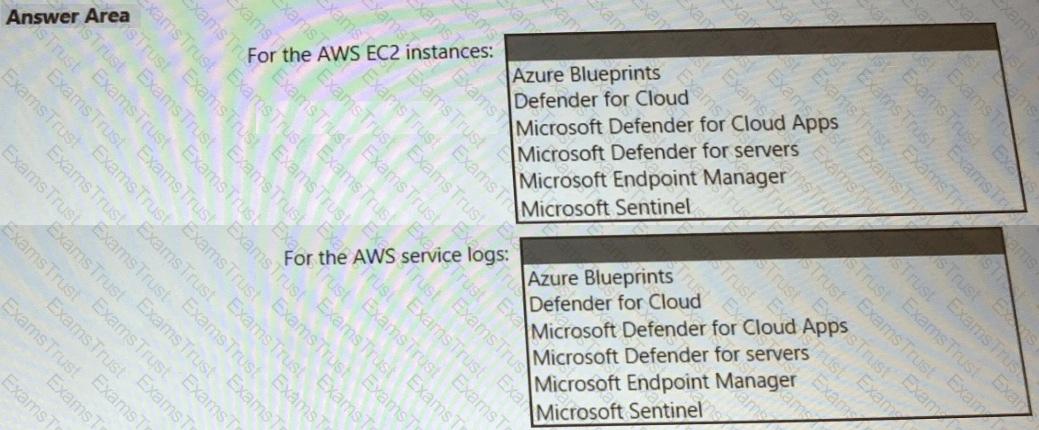
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?