You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
You need to meet the identity and access requirements for Group1.
What should you do?
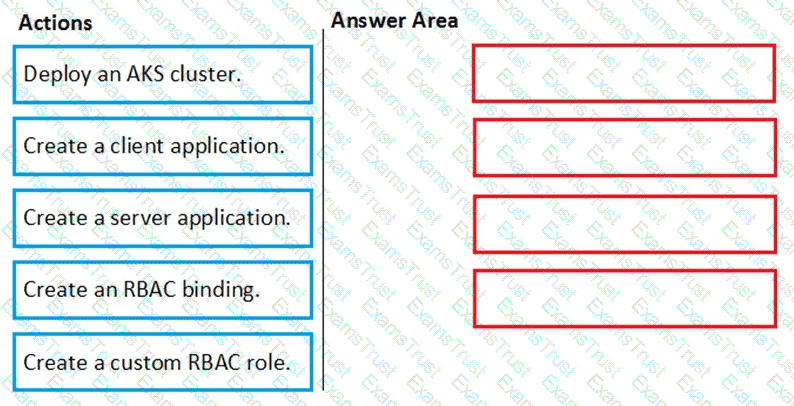
You need to deploy AKS1 to meet the platform protection requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
You need to deploy Microsoft Antimalware to meet the platform protection requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to ensure that you can meet the security operations requirements.
What should you do first?
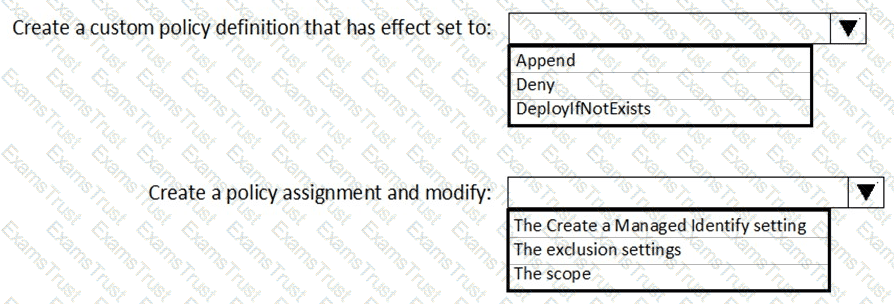
You need to ensure that the Azure AD application registration and consent configurations meet the identity and access requirements.
What should you use in the Azure portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
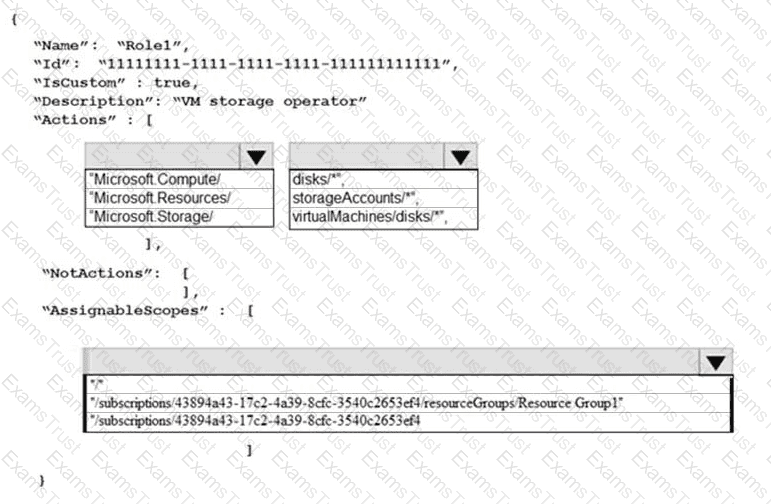
You need to create Role1 to meet the platform protection requirements.
How should you complete the role definition of Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
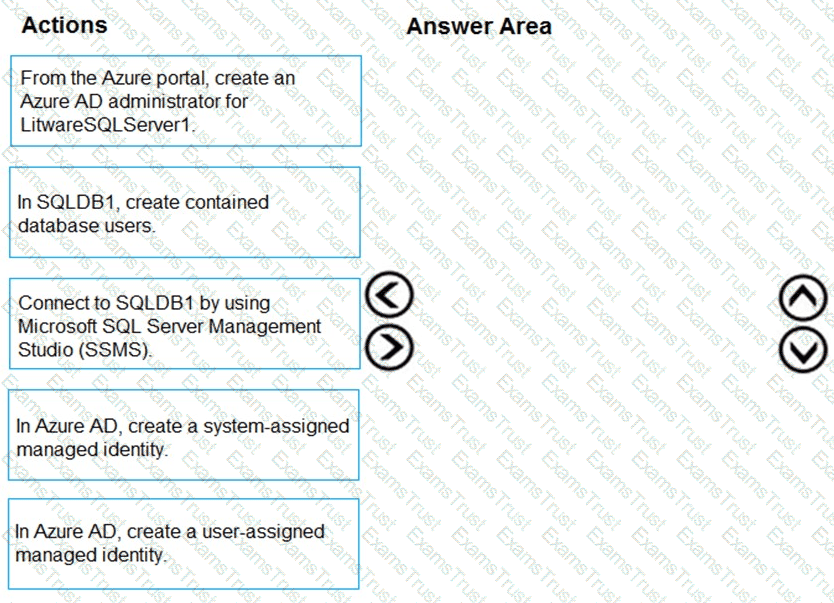
You need to configure SQLDB1 to meet the data and application requirements.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
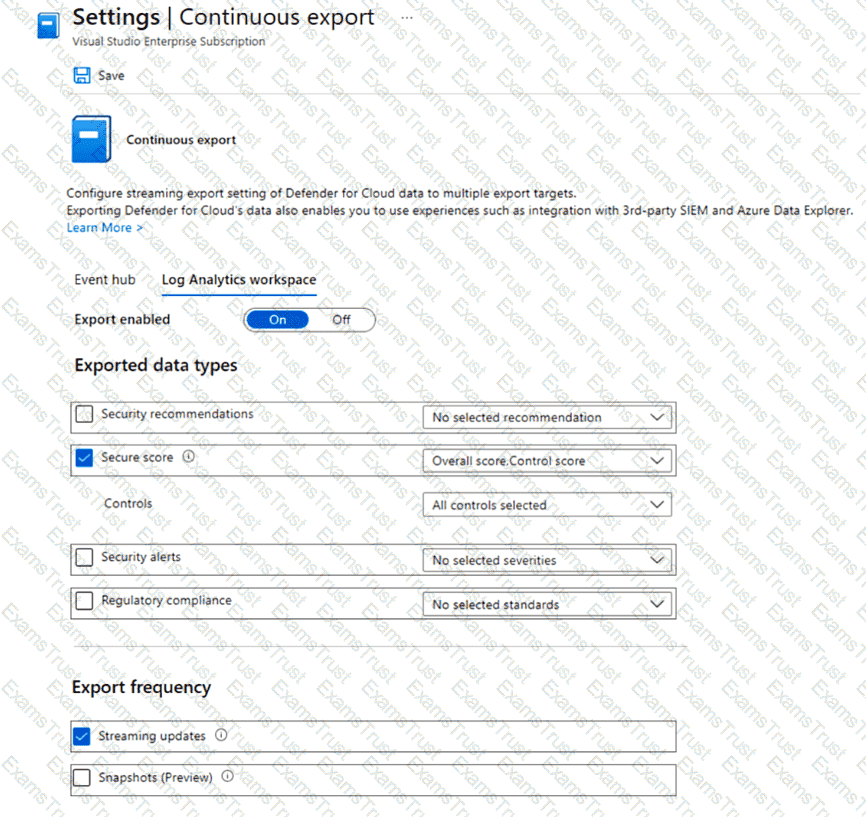
You have an Azure subscription that uses Microsoft Defender for Cloud.
You plan to use the Secure Score Over Time workbook.
You need to configure the Continuous export settings for the Defender for Cloud data.
Which two settings should you configure? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Lab Task
use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password. place your cursor in the Enter password box and click on the password below.
Azure Username: Userl -28681041@ExamUsers.com
Azure Password: GpOAe4@lDg
If the Azure portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 28681041
Task 5
You need to ensure that only devices connected to a 131-107.0.0/16 subnet can access data in the rg1lod28681041 Azure Storage account.
You have an Azure Active Directory (Azure AD) tenant that contains two users named User1 and User2 and a registered app named App1.
You create an app-specific role named Role1.
You need to assign Role1 to User1 and enable User2 to request access to App1.
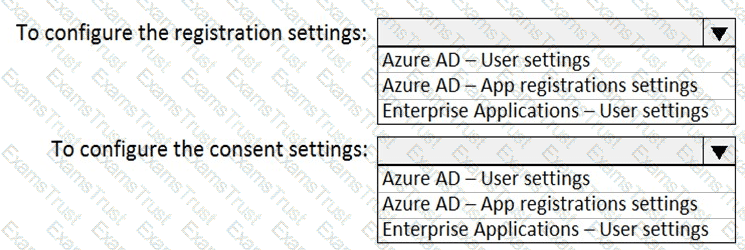
Which two settings should you modify? To answer select the appropriate settings in the answer area
NOTE: Each correct selection is worth one pant.

You have an Azure subscription that contains a Microsoft Defender External Attack Surface Management (Defender EASM) resource named EASM1. You review the Attack Surface Summary dashboard. You need to identify the following insights:
• Deprecated technologies that are no longer supported
• Infrastructure that will soon expire
Which section of the dashboard should you review?
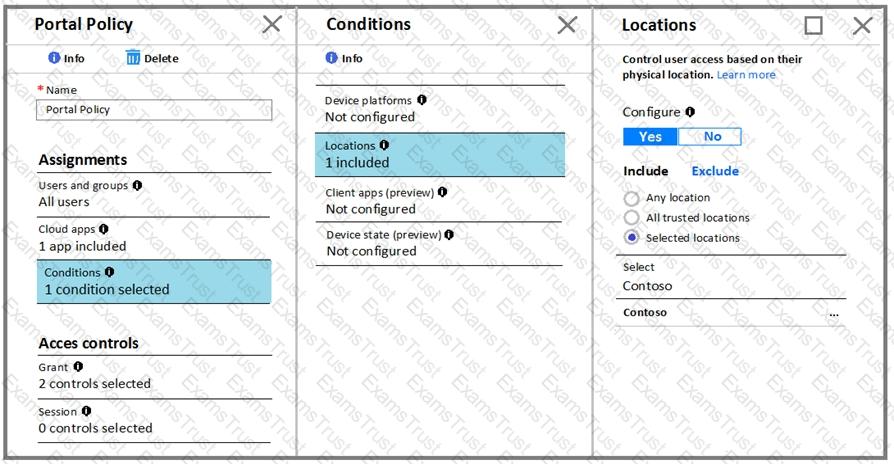
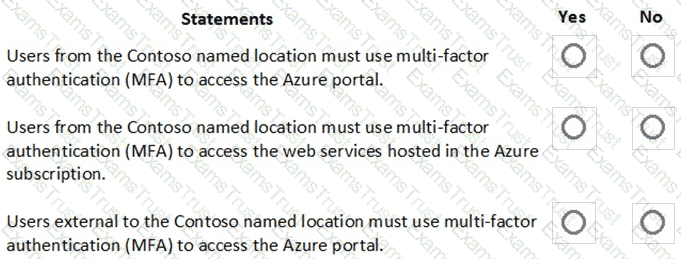
You create a new Azure subscription that is associated to a new Azure Active Directory (Azure AD) tenant.
You create one active conditional access policy named Portal Policy. Portal Policy is used to provide access to the Microsoft Azure Management cloud app.
The Conditions settings for Portal Policy are configured as shown in the Conditions exhibit. (Click the Conditions tab.)
The Grant settings for Portal Policy are configured as shown in the Grant exhibit. (Click the Grant tab.)
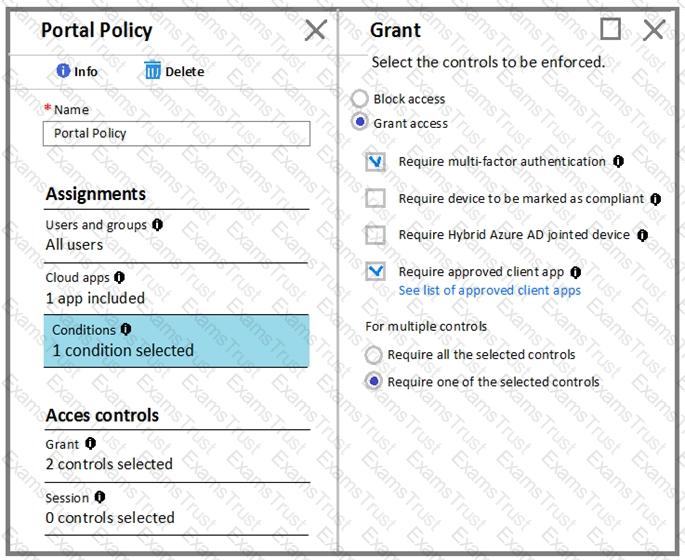
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
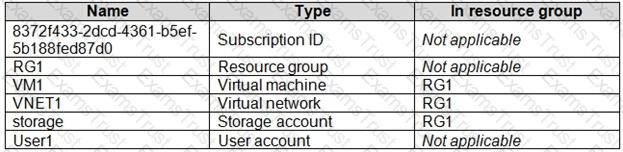
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
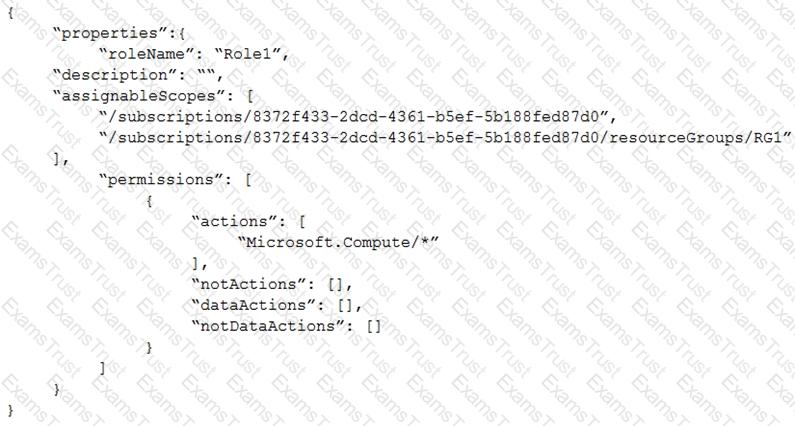
You create an Azure role by using the following JSON file.
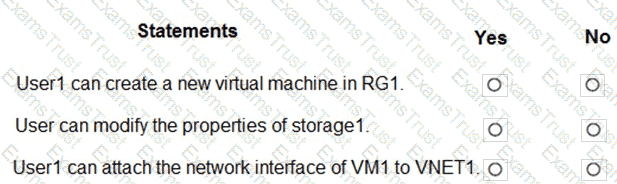
You assign Role1 to User1 for RG1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry.
What should you create?
Lab Task
Task 6
You need to configure a Microsoft SQL server named Web3l 330471 only to accept connections from the Subnet0 subnet on the VNET01 virtual network.
You have an Azure subscription that contains the resources shown in the following Table.
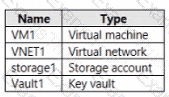
You plan to enable Microsoft Defender for Cloud for the subscription. Which resources can be protected by using Microsoft Defender for Cloud?
You have an Azure subscription that contains a resource group named RG1 and a security group named ServerAdmins. RG1 contains 10 virtual machines, a virtual network named VNET1, and a network security group JNSG) named NSG1. ServerAdmins can access the virtual machines by using RDP.
You need to ensure that NSG1 only allows RDP connections to the virtual machines for a maximum of 60 minutes when a member of ServerAdmins requests access.
What should you configure?
You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure SQL Database
instance that is configured to support Azure AD authentication.
Database developers must connect to the database instance and authenticate by using their on-premises
Active Directory account.
You need to ensure that developers can connect to the instance by using Microsoft SQL Server Management
Studio. The solution must minimize authentication prompts.
Which authentication method should you recommend?
You have an Azure subscription named Sub1. Sub1 contains a virtual network named VNet1 that contains one subnet named Subnet1.
Subnet1 contains an Azure virtual machine named VM1 that runs Ubuntu Server 20.04.
You create a service endpoint for Microsoft. Storage in Subnet1.
You need to ensure that when you deploy Docker containers to VM1, the containers can access Azure Storage resources by using the service endpoint.
What should you do on VM1 before you deploy the container?
You have an Azure subscription that uses Microsoft Sentinel.
You need to create a Microsoft Sentinel notebook that will use the Guided Investigation - Anomaly Lookup template.
What should you create first?
You have a file named File1.yaml that contains the following contents.
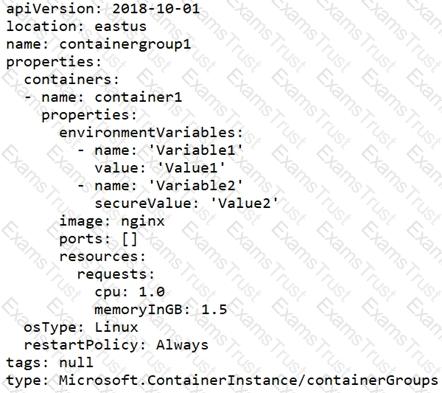
You create an Azure container instance named container1 by using File1.yaml.
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have an Azure subscription that contains the resources shown in the following table.
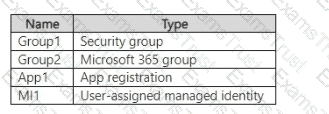
You have The users shown in the following table.
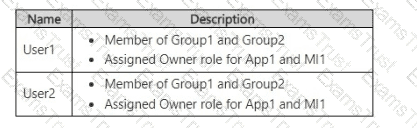
You create an Azure SQL managed instance named SQL1 and enable Microsoft Entra-only authentication. You need to ensure that both User1 and User2 are set as the Microsoft Entra admin for SQL1.
Solution: You set Group1 as the Microsoft Entra admin for SQL1.
Does this meet the goal?
You have an Azure subscription that uses Microsoft Defender.
You enable the CIS Microsoft Azure Foundations Benchmark v2.0.0 built-in to the subscription.
You need to ensure that when users attempt to assign custom role-based access control (RBAC) roles, they receive a custom error message that includes a link to an internal website. The solution must minimize the impact on other policies.
What should you configure?
You have five Azure subscriptions linked to a single Azure Active Directory (Azure AD) tenant.
You create an Azure Policy initiative named SecurityPolicyInitiative1.
You identify which standard role assignments must be configured on all new resource groups.
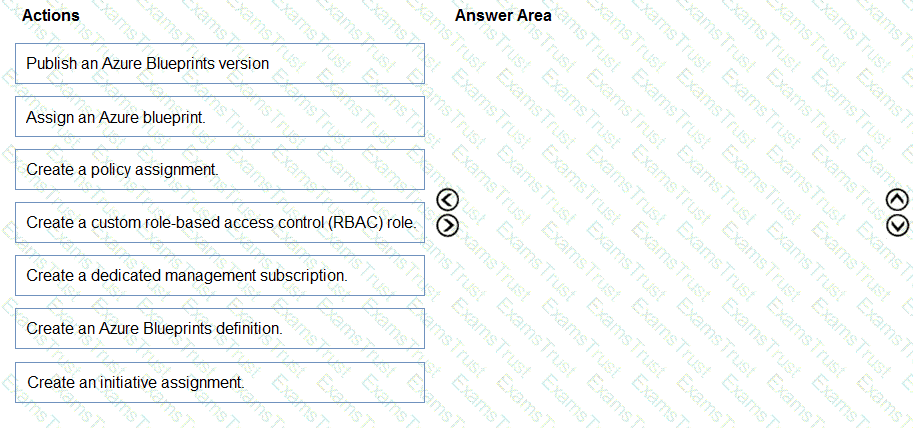
You need to enforce SecurityPolicyInitiative1 and the role assignments when a new resource group is created.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure subscription that contains the resources shown in the following table.
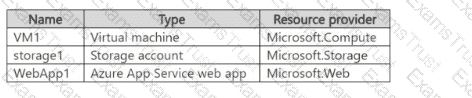
You plan to use service endpoints and service endpoint policies.
Which resources can be accessed by using a service endpoint, and which resources support service endpoint policies? To answer, select the appropriate options in the answer area.
NOTE; Each correct selection is worth one point.

You have an Azure subscription that contains the virtual networks shown in the following table.
The subscription contains the virtual machines shown in the following table.
You have a storage account named contoso2024 that contains the following resources:
• A container named Contained that contains a file named File1
• A file share named Share1 that contains a file named File2
You create a private endpoint for contoso2024 as shown in the following exhibit.
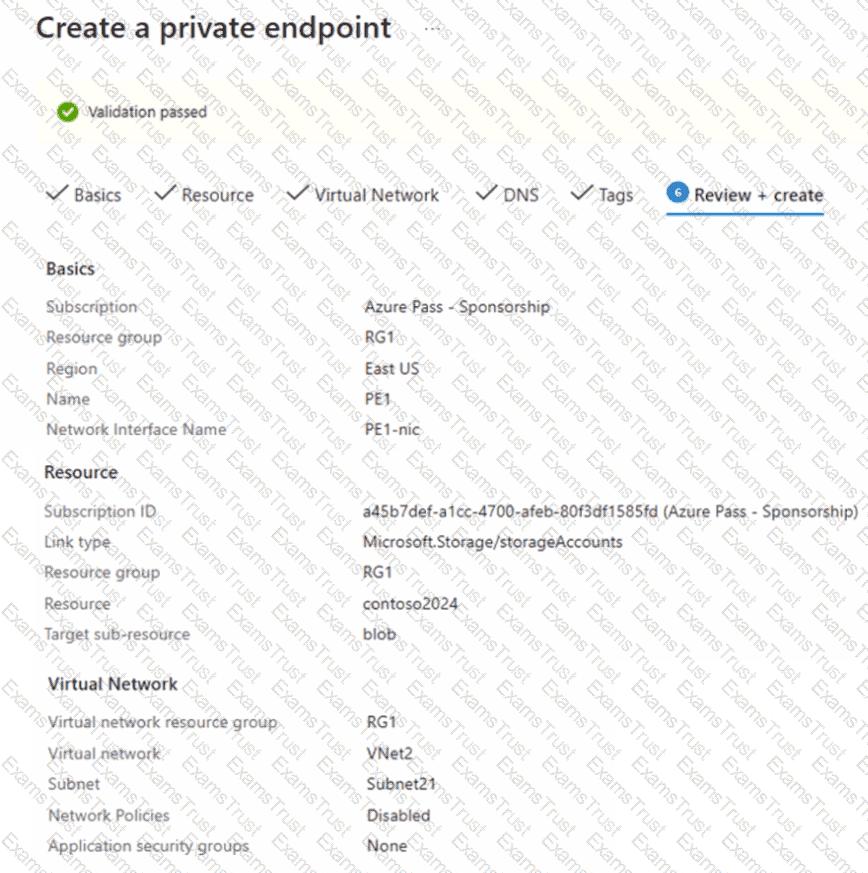
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
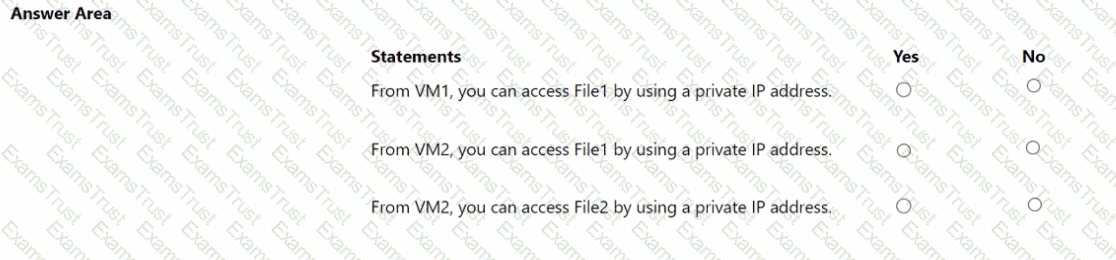
You have an Azure subscription that contains a managed identity named Identity1 and the Azure key vaults shown in the following table.
Key Vault1 contains an access policy that grants Identity1 the following key permissions:
• Get
• List
• Wrap
• Unwrap
You need to provide Identity1 with the same permissions for KeyVault2. The solution must use the principle of least privilege.
Which role should you assign to Identity1?
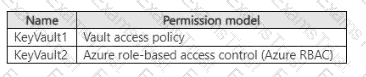
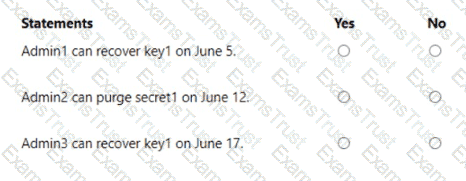
You have an Azure subscription that contains the key vaults shown in the following table.
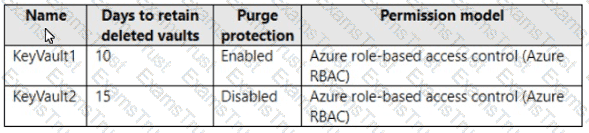
The subscription contains the users shown in the following table.
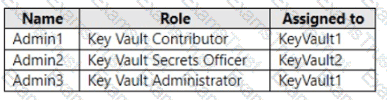
On June 1, you perform the following actions:
• Delete a key named key1 from KeyVault1.
• Delete a secret named secret 1 from KeyVault2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You need to delegate a user to implement the planned change for Defender for Cloud.
The solution must follow the principle of least privilege.
Which user should you choose?
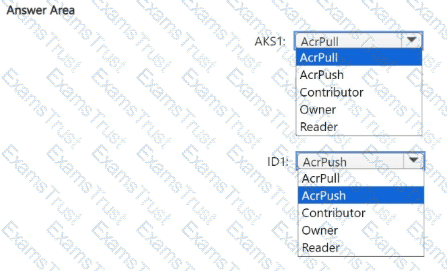
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for WAF1.
The solution must minimize administrative effort
What should you do?
You need to implement the planned change for SQLdb1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You implement the planned changes for the key vaults.
To which key vaults can you restore AKV1 backups?
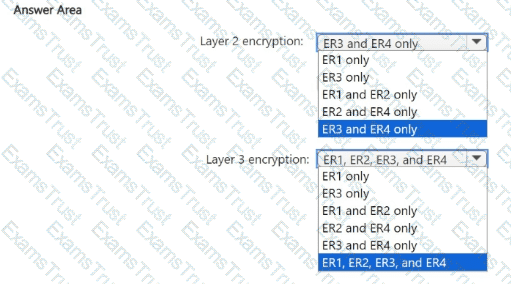
You need to recommend an encryption solution for the planned ExpressRoute implementation. The solution must meet the technical requirements.
Which ExpressRoute circuit should you recommend for each type of encryption? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for VM1 to access storage1.
The solution must meet the technical requirements.
What should you do first?
You need to ensure that User2 can implement PIM.
What should you do first?
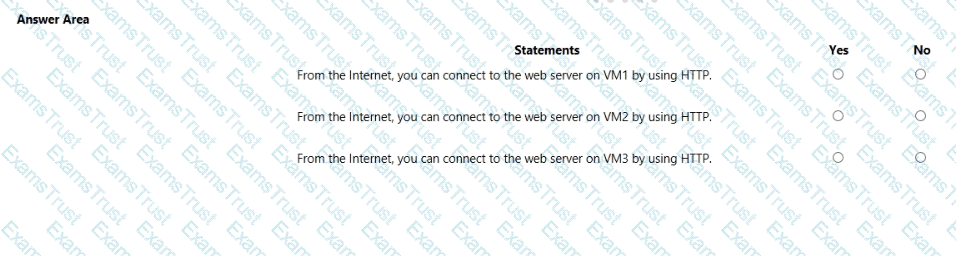
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
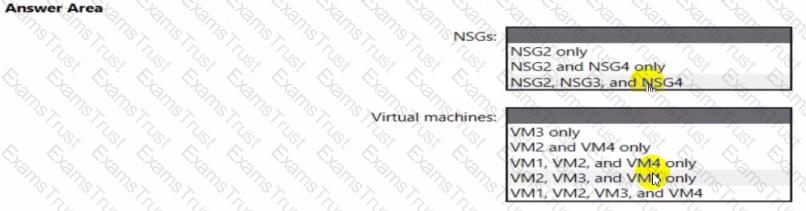
You are evaluating the effect of the application security groups on the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
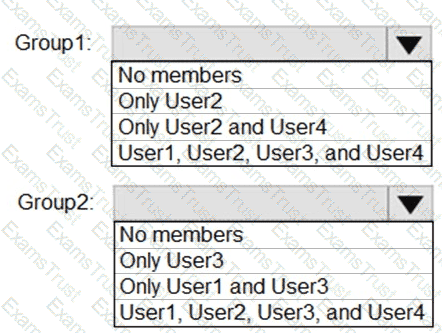
What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
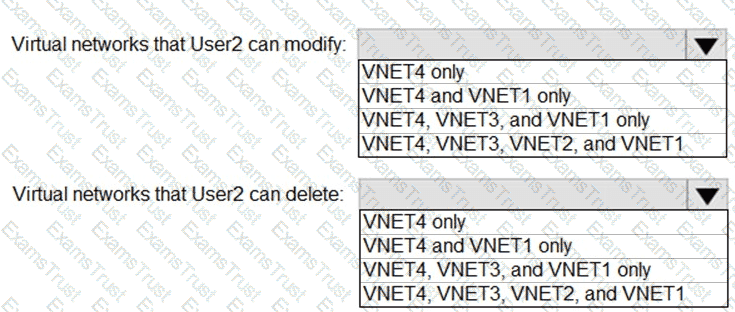
: 2 HOTSPOT
Which virtual networks in Sub1 can User2 modify and delete in their current state? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for VNetwork1.
What should you do first?
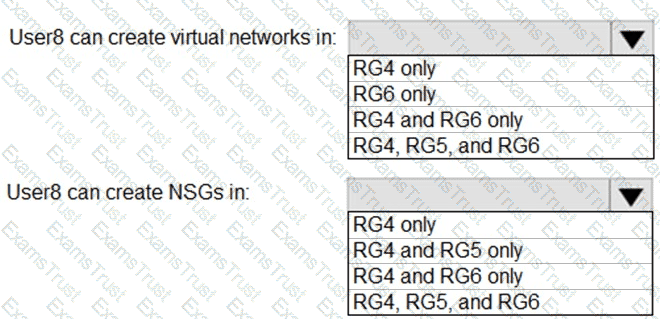
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
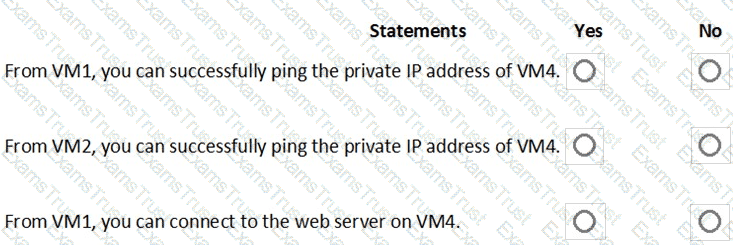
You are evaluating the security of the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
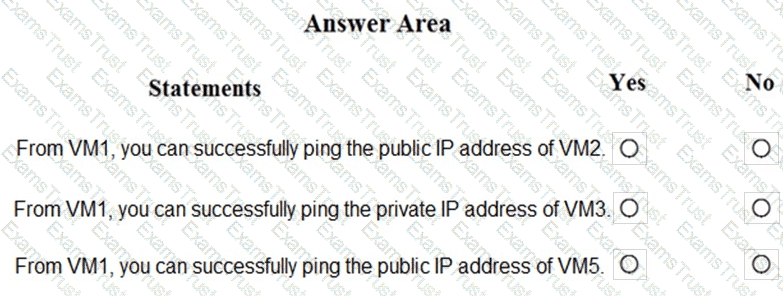
You need to meet the technical requirements for the finance department users.
Which CAPolicy1 settings should you modify?
From Azure Security Center, you need to deploy SecPol1.
What should you do first?
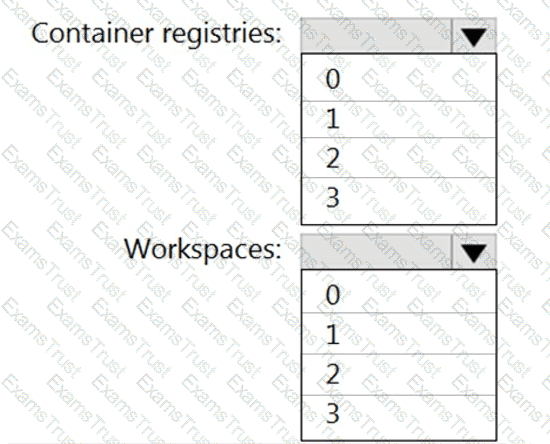
You need to configure support for Azure Sentinel notebooks to meet the technical requirements.
What is the minimum number of Azure container registries and Azure Machine Learning workspaces required?
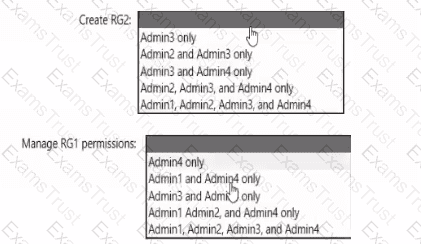
You need to delegate the creation of RG2 and the management of permissions for RG1. Which users can perform each task? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point
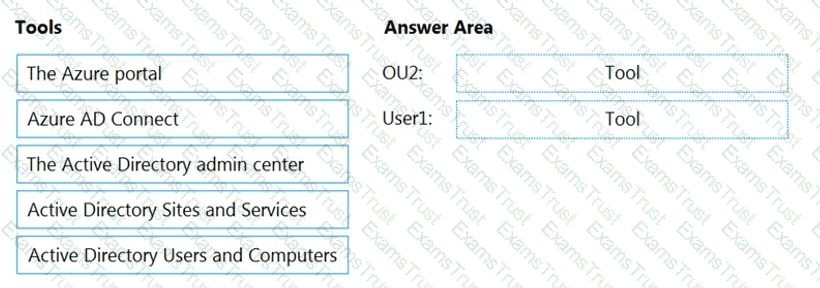
You need to perform the planned changes for OU2 and User1.
Which tools should you use? To answer, drag the appropriate tools to the correct resources. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You plan to implement JIT VM access. Which virtual machines will be supported?
You need to encrypt storage1 to meet the technical requirements. Which key vaults can you use?
You implement the planned changes for ASG1 and ASG2.
In which NSGs can you use ASG1. and the network interfaces of which virtual machines can you assign to ASG2?
You plan to configure Azure Disk Encryption for VM4. Which key vault can you use to store the encryption key?