Exhibit:
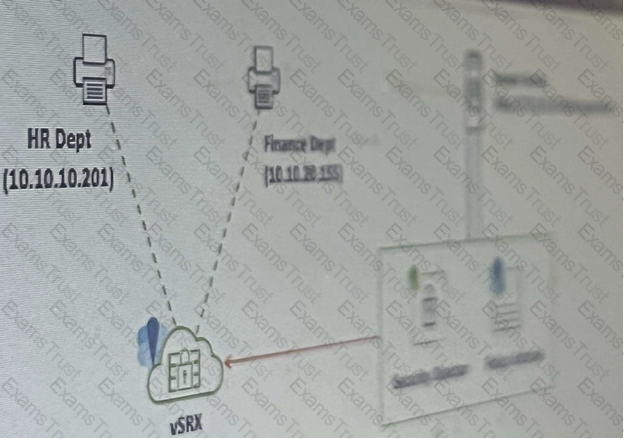
Referring to the exhibit, your company’s infrastructure team implemented new printers
To make sure that the policy enforcer pushes the updated Ip address list to the SRX.
Which three actions are required to complete the requirement? (Choose three )
You want to enable inter-tenant communica?on with tenant system.
In this Scenario, Which two solutions will accomplish this task?
Click the Exhibit button.
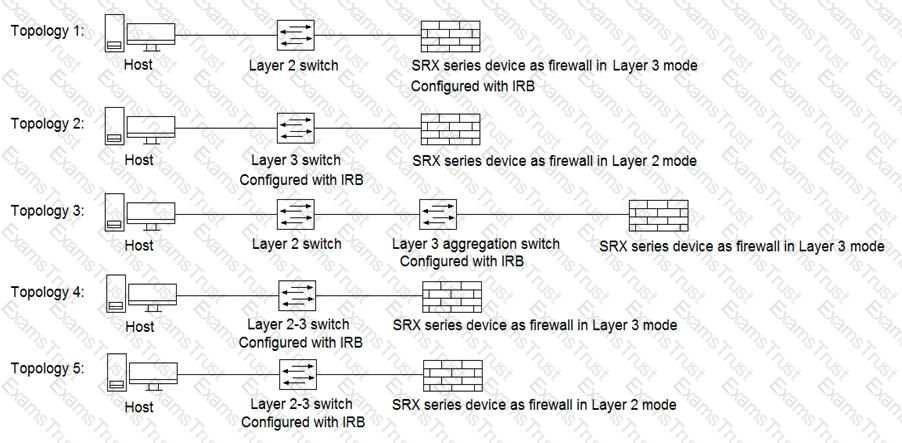
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
Exhibit.
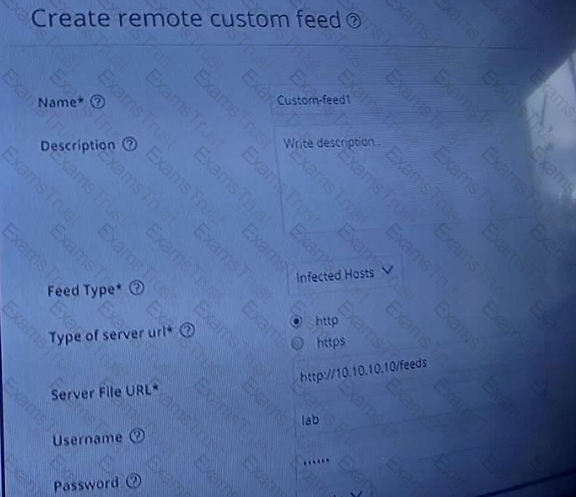
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit.
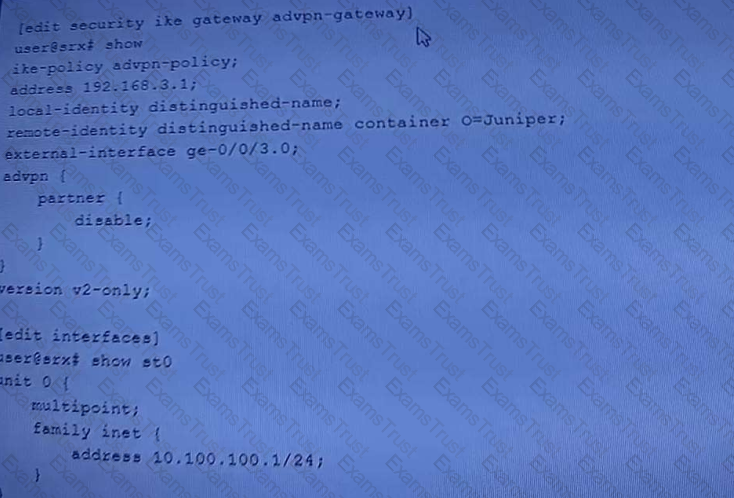
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
Exhibit
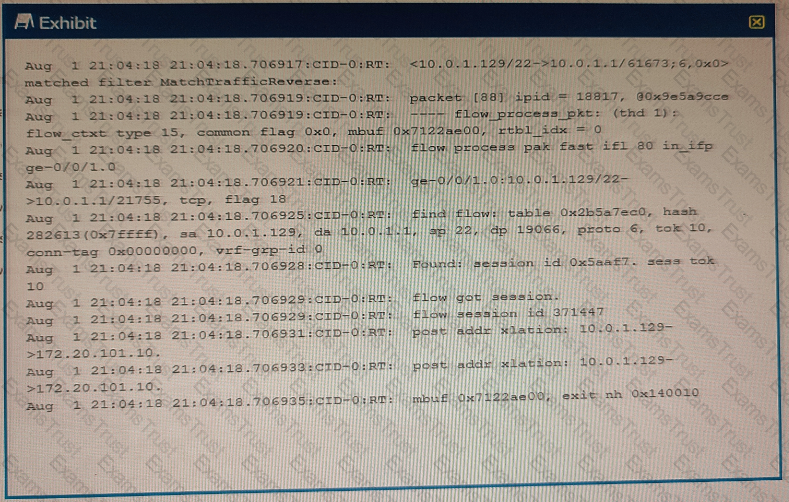
You are using trace options to verity NAT session information on your SRX Series device
Referring to the exhibit, which two statements are correct? (Choose two.)
You are asked to control access to network resources based on the identity of an authenticated device
Which three steps will accomplish this goal on the SRX Series firewalls? (Choose three )
Exhibit
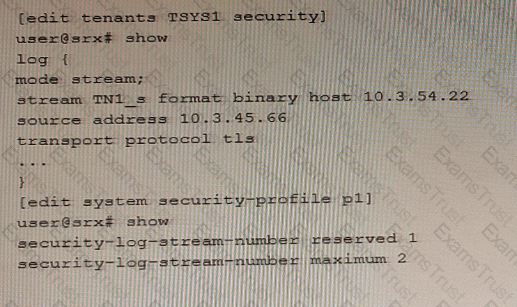
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
Exhibit
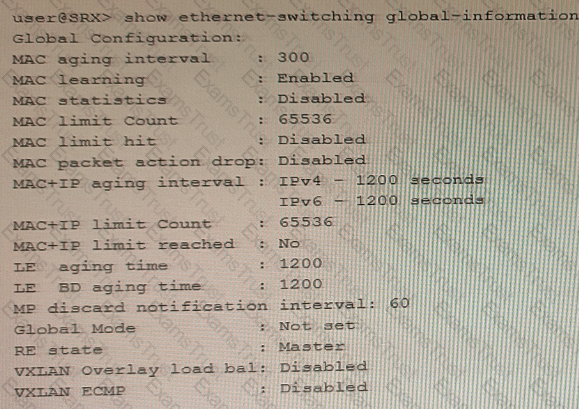
You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?
Which two features would be used for DNS doctoring on an SRX Series firewall? (Choose two.)
Which two log format types are supported by the JATP appliance? (Choose two.)
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses. Which two steps will fulfill this requirement? (Choose two.)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
Exhibit
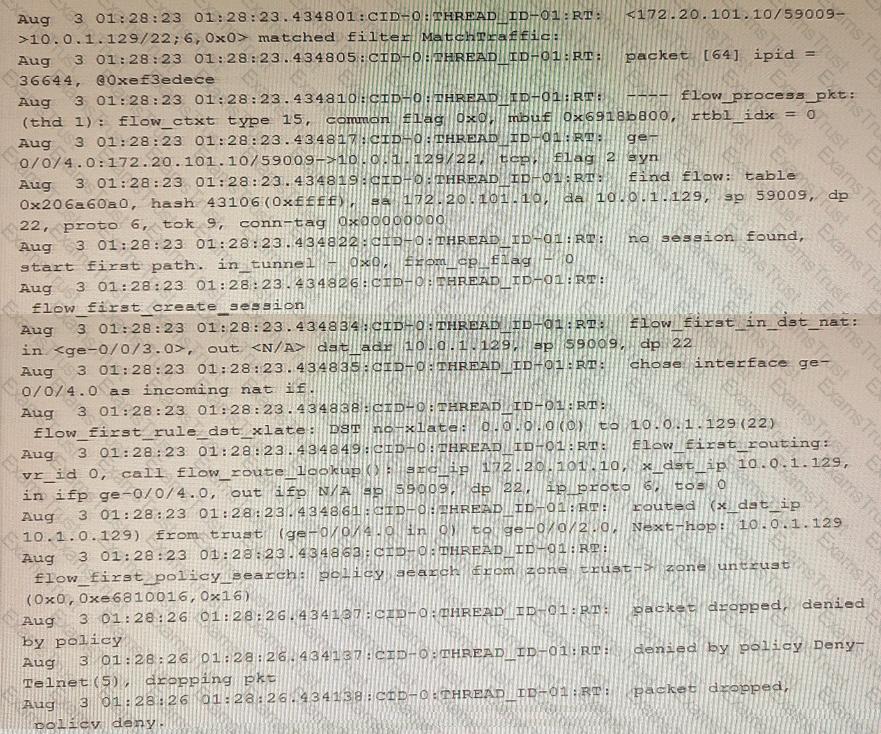
Referring to the exhibit, which statement is true?
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
Exhibit:
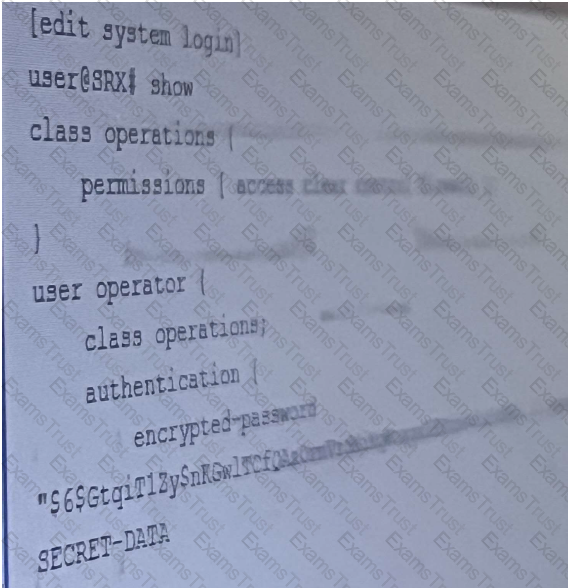
Referring to the exhibit, the operator user is unable to save configuration files to a usb stick the is
plugged into SRX. What should you do to solve this problem?
You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
A company wants to par??on their physical SRX series firewall into multiple logical units and assign
each unit (tenant) to a department within the organization. You are the primary administrator of firewall
and a colleague is the administrator for one of the departments.
Which two statements are correct about your colleague? (Choose two)
Exhibit
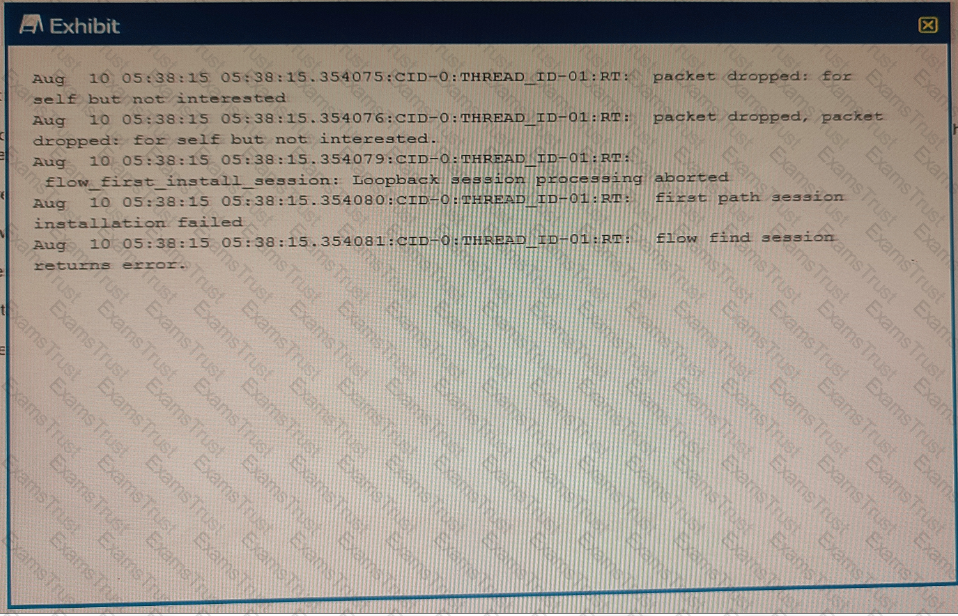
You are asked to establish an IBGP peering between the SRX Series device and the router, but the session is not being established. In the security flow trace on the SRX device, packet drops are observed as shown in the exhibit.
What is the correct action to solve the problem on the SRX device?
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
Exhibit

You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
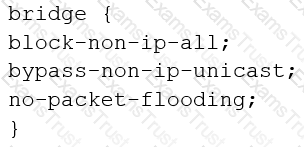
B)
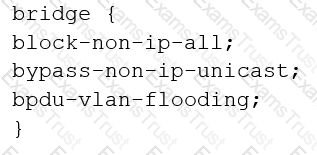
C)
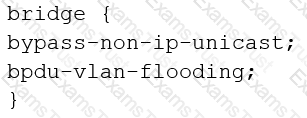
D)

Exhibit
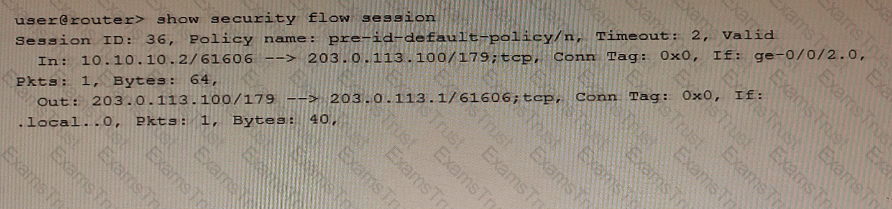
Referring to the exhibit, which type of NAT is being performed?
Exhibit
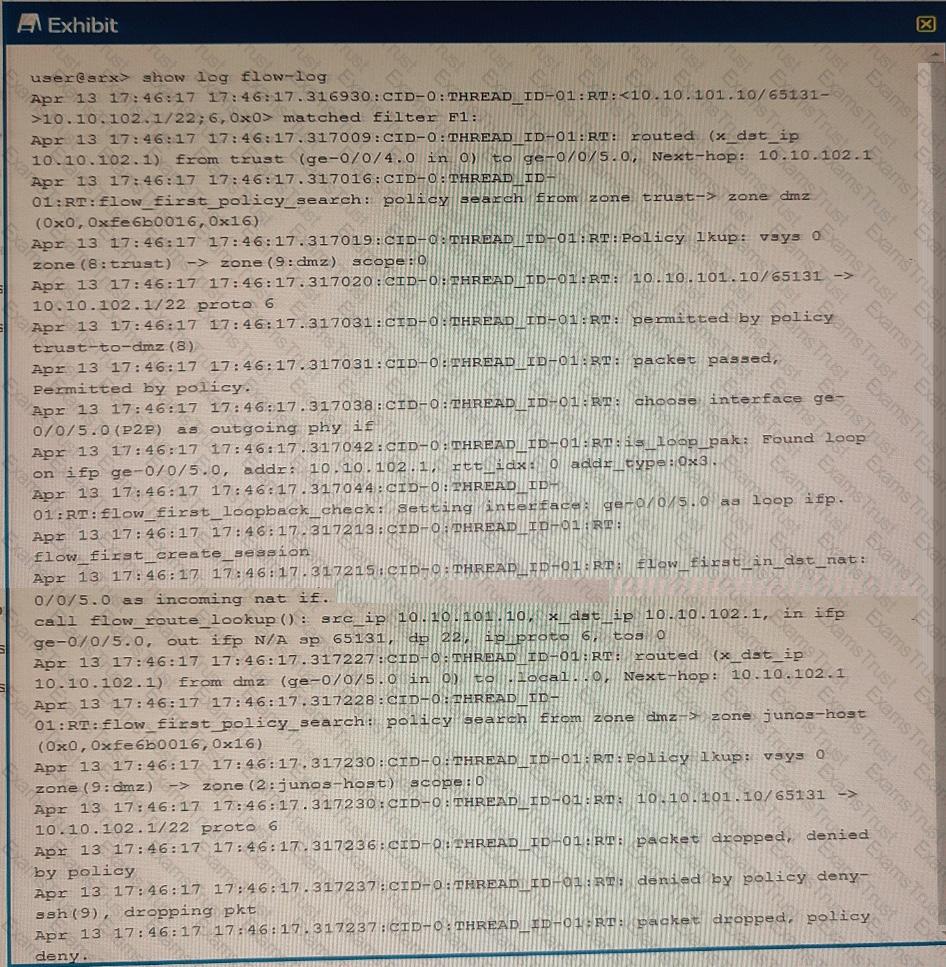
You are using traceoptions to verify NAT session information on your SRX Series device. Referring to the exhibit, which two statements are correct? (Choose two.)
which security feature bypasses routing or switching lookup?
You are asked to provide single sign-on (SSO) to Juniper ATP Cloud. Which two steps accomplish this goal? (Choose two.)
You must setup a Ddos solution for your ISP. The solution must be agile and not block legitimate traffic.
Which two products will accomplish this task? (Choose two.)
Exhibit.
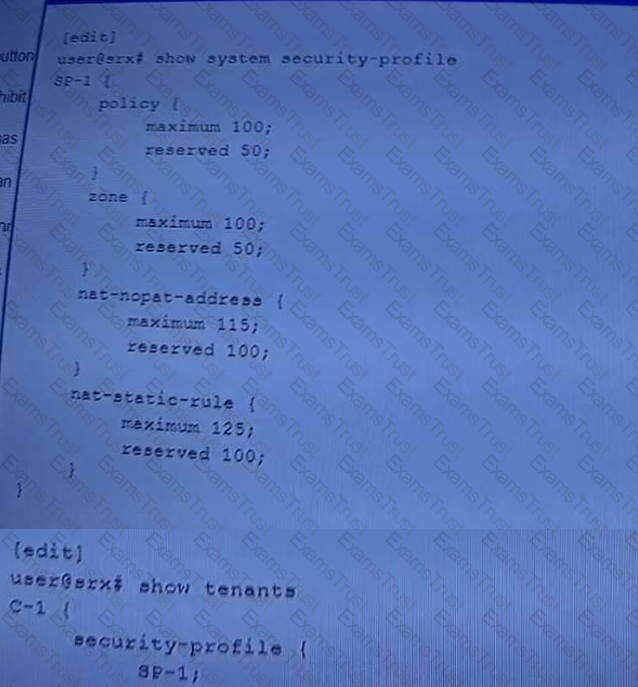
Referring to the exhibit, which two statements are true? (Choose two.)
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
Exhibit
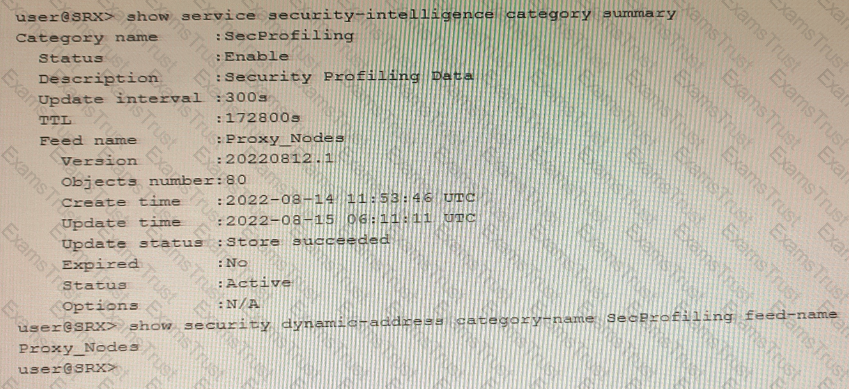
You have recently configured Adaptive Threat Profiling and notice 20 IP address entries in the monitoring section of the Juniper ATP Cloud portal that do not match the number of entries locally on the SRX Series device, as shown in the exhibit.
What is the correct action to solve this problem on the SRX device?