Which of the following attacks can be mitigated by providing proper training to the employees in an organization?
Which of the following statements is related with the second law of OPSEC?
Rick is the project manager for TTM project. He is in the process of procuring services from vendors. He makes a contract with a vendor in which he precisely specify the services to be procured, and any changes to the procurement specification will increase the costs to the buyer. Which type of contract is this?
Your project team has identified a project risk that must be responded to. The risk has been recorded in the risk register and the project team has been discussing potential risk responses for the risk event. The event is not likely to happen for several months but the probability of the event is high. Which one of the following is a valid response to the identified risk event?
In which of the following SDLC phases is the system's security features configured and enabled, the system is tested and installed or fielded, and the system is authorized for processing?
Which of the following sites are similar to the hot site facilities, with the exception that they are completely dedicated, self-developed recovery facilities?
Which of the following 'Code of Ethics Canons' of the '(ISC)2 Code of Ethics' states to act honorably, honestly, justly, responsibly and legally?
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
Which of the following are the process steps of OPSEC? Each correct answer represents a part of the solution. Choose all that apply.
Fill in the blank with an appropriate phrase.___________ is the process of using a strategy and plan of what patches should be applied to which systems at a specified time. Correct
Which of the following is a process of monitoring data packets that travel across a network?
Ned is the program manager for his organization and he's considering some new materials for his program. He and his team have never worked with these materials before and he wants to ask the vendor for some additional information, a demon, and even some samples. What type of a document should Ned send to the vendor?
You are the project manager of the HJK project for your organization. You and the project team have created risk responses for many of the risk events in the project. A teaming agreement is an example of what risk response?
Fill in the blank with an appropriate word. _________ are used in information security to formalize security policies.
Which of the following Acts enacted in United States allows the FBI to issue National Security Letters (NSLs) to Internet service providers (ISPs) ordering them to disclose records about their customers?
Which of the following can be done over telephone lines, e-mail, instant messaging, and any other method of communication considered private.
You are the project manager of the GHE Project. You have identified the following risks with the characteristics as shown in the following figure:
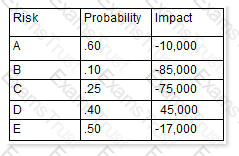
How much capital should the project set aside for the risk contingency reserve?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet? Each correct answer represents a part of the solution. Choose two.
Which of the following plans provides procedures for recovering business operations immediately following a disaster?
Which of the following test methods has the objective to test the IT system from the viewpoint of a threat-source and to identify potential failures in the IT system protection schemes?
Which of the following ports is the default port for Layer 2 Tunneling Protocol (L2TP) ?
You work as a Forensic Investigator. Which of the following rules will you follow while working on a case? Each correct answer represents a part of the solution. Choose all that apply.
Which of the following documents is described in the statement below? "It is developed along with all processes of the risk management. It contains the results of the qualitative risk analysis, quantitative risk analysis, and risk response planning."
Which of the following recovery plans includes specific strategies and actions to deal with specific variances to assumptions resulting in a particular security problem, emergency, or state of affairs?
What are the purposes of audit records on an information system? Each correct answer represents a complete solution. Choose two.
You are responsible for network and information security at a metropolitan police station. The most important concern is that unauthorized parties are not able to access data. What is this called?
Which of the following access control models uses a predefined set of access privileges for an object of a system?
What course of action can be taken by a party if the current negotiations fail and an agreement cannot be reached?
Which of the following involves changing data prior to or during input to a computer in an effort to commit fraud?
Which of the following is a name, symbol, or slogan with which a product is identified?
You work as the Network Administrator for a defense contractor. Your company works with sensitive materials and all IT personnel have at least a secret level clearance. You are still concerned that one individual could perhaps compromise the network (intentionally or unintentionally) by setting up improper or unauthorized remote access. What is the best way to avoid this problem?
Which of the following types of activities can be audited for security? Each correct answer represents a complete solution. Choose three.