Which of the following communication characteristics is achieved when the internal audit function avoids redundancies and excludes information that is unnecessary, insignificant, or unrelated to the engagement?
An analytical model determined that on Friday and Saturday nights the luxury brands stores should be open for extended hours and with a doubled number of employees
present; while on Mondays and Tuesdays costs can be minimized by reducing the number of employees to a minimum and opening only for evening hours Which of the
following best categorizes the analytical model applied?
During the second half of the audit year, the chief audit executive (CAE) identified significant negative variances to the approved audit budget required to complete the internal audit plan. Which of the following actions should the CAE take?
The chief audit executive (CAE) and management of the area under review disagree over managing a significant risk item. According to IIA guidance, which of the following actions should the CAE take first?
Internal audit observed an increase in defects of newly installed spare parts. An investigation revealed that vendors delivered spare parts of worse quality than required by contract. Which of the following recommendations would most helpfully mitigate this risk?
Which of the following would most likely serve as a foundation for individual operational goats?
Which of the following security controls would provide the most efficient and effective authentication for customers to access these online shopping account?
Which of the following statements regarding flat and hierarchical internal audit functions is true?
Through meetings with management, an organization's chief audit executive (CAE) learns of a risk that exceeds the established risk tolerance. What would be an appropriate next action for the CAE to take?
Which of the following represents an inventory costing technique that can be manipulated by management to boost net income by selling units purchased at a low cost?
The board and senior management agree to outsource the internal audit function. Which of the following is true regarding the company’s quality assurance and improvement program (QAIP)?
An organization created a formalized plan for a large project. Which of the following should be the first step in the project management plan?
Which of the following should be established by management during implementation of big data systems to enable ongoing production monitoring?
Which of the following actions is likely to reduce the risk of violating transfer pricing regulations?
Which of the following statements regarding the necessary resources to achieve the internal audit plan is true?
At one organization, the specific terms of a contract require both the promisor and promisee to sign the contract in the presence of an independent witness. What is the primary role to the witness to these signatures?
According to 11A guidance on IT, which of the following spreadsheets is most likely to be considered a high-risk user-developed application?
Which of the following documents would provide an internal auditor with information on the length of time to maintain documents after the completion of an engagement?
The chief audit executive (CAE) identified an unacceptable risk and believes that the risk is not being mitigated to an acceptable level. Which of the following is the CAE's next step in this situation?
Employees of an organization noticed that an exterior surface of the office building was deteriorating. Upon investigation, it was found that the deterioration was caused by harsh cleaning chemicals used to remove excessive bird droppings, and that the birds were drawn to the building to feed from a spider infestation. Which of the following best represents a root cause-based recommendation for this situation?
Which of the following controls would be most efficient to protect business data from corruption and errors?
An internal audit function has commenced its annual follow-up activity. An internal auditor has been assigned to verify whether the recommendations from an audit engagement completed three months ago were implemented by the business unit. The auditor had not participated in that audit engagement. What should the auditor do first?
Which of the following situations best illustrates a "false positive" in the performance of a spam filter?
A restaurant decided to expand its business to include delivery services, rather than relying on third-party food delivery services. Which of the following best describes the restaurants strategy?
After identifying and reporting a control deficiency, which of the following actions should an internal auditor perform next?
An internal auditor uses a risk and control questionnaire as part of the preliminary survey for an audit of the organization's anti-bribery and corruption program. What is the primary purpose of using this approach?
Which of the following security controls focuses most on prevention of unauthorized access to the power plant?
An organization decided to outsource its human resources function. As part of its process migration, the organization is implementing controls over sensitive employee data.
What would be the most appropriate directive control in this area?
Management has decided to change the organizational structure from one that was previously decentralized to one that is now highly centralized. As such: which of the
following would be a characteristic of the now highly centralized organization?
Which of the following best describes a transformational leader, as opposed to a transactional leader?
An organization decided to reorganize into a flatter structure. Which of the following changes would be expected with this new structure?
According to IIA guidance on IT, which of the following strategies would provide the most effective access control over an automated point-of-sale system?
Which of the following is a benefit from the concept of Internet of Things?
Which of the following should software auditors do when reporting internal audit findings related to enterprisewide resource planning?
Which of the following is the most appropriate beginning step of a work program for an assurance engagement involving smart devices?
An attacker, posing as a bank representative, convinced an employee to release certain, financial information that ultimately resulted in fraud. Which of the following best describes this cybersecurity risk?
An internal auditor identified a database administrator with an incompatible dual role. Which of the following duties should not be performed by the identified administrator?
Which of the following inventory costing methods requires the organization to account for the actual cost paid for the unit being sold?
A chief audit executive (CAE) is developing a strategic plan for the internal audit function. In the last two years, the organization has faced significant IT risks, but the internal audit function has not been able to audit those areas due to a lack of knowledge. How could the CAE address this in the strategic plan?
Which of the following describes the most appropriate set of tests for auditing a workstation’s logical access controls?
Capital budgeting involves choosing among various capital projects to find the one(s) that will maximize a company's return on its financial investment. Which of the following parties approves the capital budget?
Which of the following is improved by the use of smart devices?
A motivational technique generally used to overcome monotony and job-related boredom is:
According to IIA guidance, which of the following best describes an adequate management (audit) trail application control for the general ledger?
According to Maslow’s hierarchy of needs theory, which of the following best describes a strategy where a manager offers an assignment to a subordinate specifically to support his professional growth and future advancement?
An organization uses the management-by-objectives method, whereby employee performance is based on defined goals. Which of the following statements is true regarding this approach?
Which of the following is a result of implementing an e-commerce system that relies heavily on electronic data interchange (EDI) and electronic funds transfer (EFT) for purchasing and billing?
Which of the following authentication device credentials is the most difficult to revoke when an employee's access rights need to be removed?
A rapidly expanding retail organization continues to be tightly controlled by its original small management team. Which of the following is a potential risk in this vertically centralized organization?
When using data analytics during a review of the procurement process, what is the first step in the analysis process?
What kind of strategy would be most effective for an organization to adopt in order to implement a unique advertising campaign for selling identical products across all of its markets?
Which type of bond sells at a discount from face value, then increases in value annually until it reaches maturity and provides the owner with the total payoff?
An organization requires an average of 58 days to convert raw materials into finished products to sell. An additional 42 days is required to collect receivables. If the organization takes an average of 10 days to pay for raw materials, how long is its total cash conversion cycle?
For employees, the primary value of implementing job enrichment is which of the following?
What is the primary purpose of an integrity control?
Which of the following is an example of a key systems development control typically found in the in-house development of an application system?
According to IIA guidance on IT, which of the following best describes a situation where data backup plans exist to ensure that critical data can be restored at some point in the future, but recovery and restore processes have not been defined?
Which of the following principles is shared by both hierarchical and open organizational structures?
A superior can delegate the authority to make decisions but cannot delegate the ultimate responsibility for the results of those decisions.
A supervisor's span of control should not exceed seven subordinates.
Responsibility should be accompanied by adequate authority.
Employees at all levels should be empowered to make decisions.
During which phase of the contracting process are contracts drafted for a proposed business activity?
An organization has 1,000 units of a defective item in stock. Per unit, market price is $10; production cost is $4; and the defect selling price is $5. What is the carrying amount (inventory value) of defects at year-end?
A newly appointed chief audit executive (CAE) reviews current reporting practices. The CAE notices that exit meetings tend to be unproductive. When internal auditors present summaries of observations, engagement clients consistently complain that they do not understand where the observations come from. Which of the following could improve this situation?
Which of the following statements is most accurate concerning the management and audit of a web server?
Based on test results, an IT auditor concluded that the organization would suffer unacceptable loss of data if there was a disaster at its data center. Which of the following test results would likely lead the auditor to this conclusion?
A large retail customer made an offer to buy 10,000 units at a special price of $7 per unit. The manufacturer usually sells each unit for $10. Variable manufacturing costs are $5 per unit and fixed manufacturing costs are $3 per unit. For the manufacturer to accept the offer, which of the following assumptions needs to be true?
Which of the following is an example of a phishing attack?
Which of the following is true of matrix organizations?
Which of the following statements best describes the current state of data privacy regulation?
Which of the following security controls would be appropriate to protect the exchange of information?
Which of the following data security policies is most likely to be the result of a data privacy law?
The head of the research and development department at a manufacturing organization believes that his team lacks expertise in some areas and decides to hire more experienced researchers to assist in the development of a new product. Which of the following variances are likely to occur as the result of this decision?
Favorable labor efficiency variance
Adverse labor rate variance
Adverse labor efficiency variance
Favorable labor rate variance
Which of the following is a primary driver behind the creation and prioritization of new strategic initiatives established by an organization?
Which of the following is an example of an application control?
How do data analysis technologies affect internal audit testing?
Which of the following differentiates a physical access control from a logical access control?
Which of the following is classified as a product cost using the variable costing method?
Direct labor costs.
Insurance on a factory.
Manufacturing supplies.
Packaging and shipping costs.
Which of the following is a typical activity performed by the help desk?
According to IIA guidance on IT, which of the following would be considered a primary control for a spreadsheet to help ensure accurate financial reporting?
Which of the following statements is true regarding cost-volume-profit analysis?
Which of the following statements is true regarding a project life cycle?
In accounting, which of the following statements is true regarding the terms debit and credit?
An internal auditor considers the financial statement of an organization as part of a financial assurance engagement. The auditor expresses the organization's electricity and depreciation expenses as a percentage of revenue to be 10% and 7% respectively. Which of the following techniques was used by the internal auditor In this calculation?
Following an evaluation of an organization's IT controls, an internal auditor suggested improving the process where results are compared against the input. Which of the following IT controls would the Internal auditor recommend?
Which of the following would be the best method to collect information about employees' job satisfaction?
Which of the following controls would enable management to receive timely feedback and help mitigate unforeseen risks?
A chief audit executive wants to implement an enterprisewide resource planning software. Which of the following internal audit assessments could provide overall assurance on the likelihood of the software implementation's success?
Which of the following Issues would be a major concern for internal auditors when using a free software to analyze a third-party vendor's big data?
Which of the following best describes a man-in-the-middle cyber-attack?
An organization has decided to allow its managers to use their own smart phones at work. With this change, which of the following is most important to Include In the IT department's comprehensive policies and procedures?
The internal audit activity has identified accounting errors that resulted in the organization overstating its net income for the fiscal year. Which of the following is the most likely cause of this overstatement?
An employee was promoted within the organization and relocated to a new office in a different building. A few months later, security personnel discovered that the employee's smart card was being used to access the building where she previously worked. Which of the following security controls could prevent such an incident from occurring?
A clothing company sells shirts for $8 per shirt. In order to break even, the company must sell 25.000 shirts. Actual sales total S300.000. What is margin of safety sales for the company?
Senior management is trying to decide whether to use the direct write-off or allowance method for recording bad debt on accounts receivables. Which of the following would be the best argument for using the direct write-off method?
Which of the following statements is true regarding an investee that received a dividend distribution from an entity and is presumed to have little influence over the entity?
Which of the following can be viewed as a potential benefit of an enterprisewide resource planning system?
Which of the following physical security controls is able to serve as both a detective and preventive control?
Which of the following cost of capital methods identifies the time period required to recover She cost of the capital investment from the annual inflow produced?
An IT auditor is evaluating IT controls of a newly purchased information system. The auditor discovers that logging is not configured al database and application levels. Operational management explains that they do not have enough personnel to manage the logs and they see no benefit in keeping logs. Which of the fallowing responses best explains risks associated with insufficient or absent logging practices?
During a review of the accounts payable process, an internal auditor gathered all of the vendor payment transactions for the past 24 months. The auditor then used an Analytics tool to identify the top five vendors that received the highest sum of payments. Which of the following analytics techniques did the auditor apply?
While conducting an audit of the accounts payable department, an internal auditor found that 3% of payments made during the period under review did not agree with the submitted invoices. Which of the following key performance indicators (KPIs) for the department would best assist the auditor in determining the significance of the test results?
According to Maslow's hierarchy of needs theory, which of the following would likely have the most impact on retaining staff, if their lower-level needs are already met?
The board of directors wants to implement an incentive program for senior management that is specifically tied to the long-term health of the organization. Which of the following methods of compensation would be best to achieve this goal?
An organization's board of directors is particularly focused on positioning, the organization as a leader in the industry and beating the competition. Which of the following strategies offers the greatest alignment with the board's focus?
Which of the following is an example of internal auditors applying data mining techniques for exploratory purposes?
A financial institution receives frequent and varied email requests from customers for funds to be wired out of their accounts. Which verification activity would best help the institution avoid falling victim to phishing?
An organization contracted a third-party service provider to plan, design, and build a new facility. Senior management would like to transfer all of the risk to the builder. Which type of procurement contract would the organization use?
Which of the following performance measures includes both profits and investment base?
An organization buys equity securities for trading purposes and sells them within a short time period. Which of the following is the correct way to value and report those securities at a financial statement date?
Which of following best demonstrates the application of the cost principle?
According to IIA guidance, which of the following is an IT project success factor?
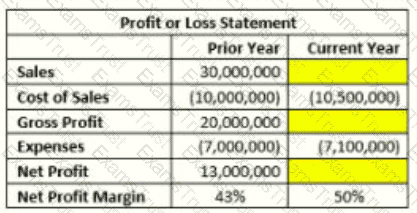
The manager of the sales department wants to Increase the organization's net profit margin by 7% (from 43% in the prior year to 50% in the current year). Given the information provided in the table below, what would be the targeted sales amount for the current year?
When auditing databases, which of the following risks would an Internal auditor keep In mind In relation to database administrators?
The chief audit executive (CAE) has embraced a total quality management approach to improving the internal audit activity's (lAArs) processes. He would like to reduce the time to complete audits and improve client ratings of the IAA. Which of the following staffing approaches is the CAE most likely lo select?
According to IIA guidance, which of the following statements is true regarding penetration testing?
A manager at a publishing company received an email that appeared to be from one of her vendors with an attachment that contained malware embedded in an Excel spreadsheet . When the spreadsheet was opened, the cybercriminal was able to attack the company's network and gain access to an unpublished and highly anticipated book. Which of the following controls would be most effective to prevent such an attack?
With increased cybersecurity threats, which of the following should management consider to ensure that there is strong security governance in place?
Which of the following characteristics applies to an organization that adopts a flat structure?
Which of the following common quantitative techniques used in capital budgeting is best associated with the use of a table that describes the present value of an annuity?
According to IIA guidance, which of the following would be the best first stop to manage risk when a third party is overseeing the organization's network and data?
An organization's account for office supplies on hand had a balance of $9,000 at the end of year one. During year two. The organization recorded an expense of $45,000 for purchasing office supplies. At the end of year two. a physical count determined that the organization has $11 ,500 in office supplies on hand. Based on this Information, what would he recorded in the adjusting entry an the end of year two?
Management is designing its disaster recovery plan. In the event that there is significant damage to the organization's IT systems this plan should enable the organization to resume operations at a recovery site after some configuration and data restoration. Which of the following is the ideal solution for management in this scenario?
Which of the following is classified as a product cost using the variable costing method?
1. Direct labor costs.
2. Insurance on a factory.
3. Manufacturing supplies.
4. Packaging and shipping costa.
Which of the following should be included in a data privacy poky?
1. Stipulations for deleting certain data after a specified period of time.
2. Guidance on acceptable methods for collecting personal data.
3. A requirement to retain personal data indefinitely to ensure a complete audit trail,
4. A description of what constitutes appropriate use of personal data.
An Internal auditor is using data analytics to focus on high-risk areas during an engagement. The auditor has obtained data and is working to eliminate redundancies in the data. Which of the following statements is true regarding this scenario?
Which of the following is a primary driver behind the creation and prloritteation of new strategic Initiatives established by an organization?
An organization and its trading partner rely on a computer-to-computer exchange of digital business documents. Which of the following best describes this scenario?
Which of the following IT-related activities is most commonly performed by the second line of defense?
Which of the following is an example of a physical control?
According to IIA guidance, which of the following links computers and enables them to -communicate with each other?
An organization has a declining inventory turnover but an Increasing gross margin rate, Which of the following statements can best explain this situation?
Which of the following statements is true regarding the management-by-objectives method?
An internal auditor observed that the organization's disaster recovery solution will make use of a cold site in a town several miles away. Which of the following is likely to be a characteristic of this disaster recover/ solution?
Based on lest results, an IT auditor concluded that the organization would suffer unacceptable loss of data if there was a disaster at its data center. Which of the following test results would likely lead the auditor to this conclusion?
According to lIA guidance on IT, which of the following plans would pair the identification of critical business processes with recovery time objectives?
Which of the following is the most appropriate way lo record each partner's initial Investment in a partnership?
Which of the following practices impacts copyright issues related to the manufacturer of a smart device?
According to Herzberg's Two-Factor Theory of Motivation, which of the following factors arc mentioned most often by satisfied employees?
Which of the following is on advantage of a decentralized organizational structure, as opposed to a centralized structure?
What kind of strategy would be most effective for an organization to adopt in order to Implement a unique advertising campaign for selling identical product lines across all of its markets?
An internal auditor is assessing the risks related to an organization's mobile device policy. She notes that the organization allows third parties (vendors and visitors) to use outside smart devices to access its proprietary networks and systems. Which of the following types of smart device risks should the internal
Auditor be most concerned about?
An organization requires an average of 5S days to convert raw materials into finished products to sell. An average of 42 additional days is required to collect receivables. If the organization takes an average of 10 days to pay for the raw materials, how long is its total cash conversion cycle?
According to IIA guidance, which of the following is a broad collection of integrated policies, standards, and procedures used to guide the planning and execution of a project?
An organization with global headquarters in the United States has subsidiaries in eight other nations. If the organization operates with an ethnocentric attitude, which of the following statements is true?
Which of the following statements is true regarding data backup?
While auditing an organization's customer call center, an internal auditor notices that Key performance indicators show a positive trend, despite the fact that there have been increasing customer complaints over the same period. Which of the following audit recommendations would most likely correct the cause of this inconsistency?
An internal auditor found the following information while reviewing the monthly financial siatements for a wholesaler of safety

The cost of goods sold was reported at $8,500. Which of the following inventory methods was used to derive this value?
Which of the following network types should an organization choose if it wants to allow access only to its own personnel?
An organization discovered fraudulent activity involving the employee time-tracking system. One employee regularly docked in and clocked out her co-worker friends on their days off, inflating their reported work hours and increasing their wages. Which of the following physical authentication devices would be most effective at disabling this fraudulent scheme?
Which of the following is a result of Implementing on e-commerce system, which relies heavily on electronic data interchange and electronic funds transfer, for purchasing and biting?
Which of the following purchasing scenarios would gain the greatest benefit from implementing electronic cate interchange?
An organization has 10,000 units of a defect item in stock, per unit, market price is $10$; production cost is $4; and defect selling price is $5. What is the carrying amount (inventory value) of defects at your end?
Which of the following items represents the first thing that should be done with obtained dote in the data analytics process?
Which of the following types of date analytics would be used by a hospital to determine which patients are likely to require remittance for additional treatment?
A new manager received computations of the internal fate of return regarding the project proposal. What should the manager compare the computation results to in order to determine whether the project is potentially acceptable?
The head of the research arid development department at a manufacturing organization believes that his team lacks expertise in some areas, and he decides to hire more experienced researchers to assist in the development of a new product. Which of the following variances are likely to occur as the result of this decision?
1. Favorable labor efficiency variance.
2. Adverse labor rate variance.
3. Adverse labor efficiency variance.
4. Favorable labor rate variance.