Which of the following is not a direct benefit of control self-assessment (CSA)?
An internal auditor determines that certain information from the engagement results is not appropriate for disclosure to all report recipients because it is privileged. In this situation, which of the following actions would be most appropriate?
The chief audit executive (CAE) of a small internal audit activity (IAA) plans to test conformance with the Standards through a quality assurance review. According to the Standards, which of the following are acceptable practice for this review?
1. Use an external service provider.
2. Conduct a self-assessment with independent validation.
3. Arrange for a review by qualified employees outside of the IAA.
4. Arrange for reciprocal peer review with another CAE.
Which of the following is not an outcome of control self-assessment?
The chief audit executive of a medium-sized financial institution is evaluating the staffing model of the internal audit activity (IAA). According to IIA guidance, which of the following are the most appropriate strategies to maximize the value of the current IAA resources?
• The annual audit plan should include audits that are consistent with the skills of the IAA.
• Audits of high-risk areas of the organization should be conducted by internal audit staff.
• External resources may be hired to provide subject-matter expertise but should be supervised.
• Auditors should develop their skills by being assigned to complex audits for learning opportunities.
Which of the following components should be included in an audit finding?
1. The scope of the audit.
2. The standard(s) used by the auditor to make the evaluation.
3. The engagement's objectives.
4. The factual evidence that the internal auditor found in the course of the examination.
According to IIA guidance, which of the following are appropriate actions for the chief audit executive regarding management's response to audit recommendations?
A code of business conduct should include which of the following to increase its deterrent effect?
1. Appropriate descriptions of penalties for misconduct.
2. A notification that code of conduct violations may lead to criminal prosecution.
3. A description of violations that injure the interests of the employer.
4. A list of employees covered by the code of conduct.
An employee in the sales department completes a purchase requisition and forwards it to the purchaser. The purchaser places competitive bids and orders the requested items using approved purchase orders. When the employee receives the ordered items, she forwards the packing slips to the accounts payable department. The invoice for the ordered items is sent directly to the sales department, and an administrative assistant in the sales department forwards the invoices to the accounts payable department for payment. Which of the following audit steps best addresses the risk of fraud in the cash receipts process?
According to IIA guidance, which of the following accurately describes the responsibilities of the chief audit executive with respect to the final audit report?
1. Coordinate post-engagement conferences to discuss the final audit report with management.
2. Include management's responses in the final audit report.
3. Review and approve the final audit report.
4. Determine who will receive the final audit report.
A manufacturer is under contract to produce and deliver a number of aircraft to a major airline. As part of the contract, the manufacturer is also providing training to the airline's pilots. At the time of the audit, the delivery of the aircraft had fallen substantially behind schedule while the training had already been completed. If half of the aircraft under contract have been delivered, which of the following should the internal auditor expect to be accounted for in the general ledger?
An internal auditor wants to determine whether employees are complying with the information security policy, which prohibits leaving sensitive information on employee desks overnight. The auditor checked a sample of 90 desks and found eight that contained sensitive information. How should this observation be reported, if the organization tolerates 4 percent noncompliance?
After the team member who specialized in fraud investigations left the internal audit team, the chief audit executive decided to outsource fraud investigations to a third party service provider on an as needed basis. Which of the following is most likely to be a disadvantage of this outsourcing decision?
During an assurance engagement, an internal auditor discovered that a sales manager approved numerous sales contracts for values exceeding his authorization limit. The auditor reported the finding to the audit supervisor, noting that the sales manager had additional new contracts under negotiation. According to IIA guidance, which of the following would be the most appropriate next step?
Which of the following statements describes an engagement planning best practice?
The board has asked the internal audit activity (IAA) to be involved in the organization's enterprise risk management process. Which of the following activities is appropriate for IAA to perform without safeguards?
Due to a recent system upgrade, an audit is planned to test the payroll process. Which of the following audit objectives would be most important to prevent fraud?
Which of the following statements is true pertaining to interviewing a fraud suspect?
1. Information gathered can be subjective as well as objective to be useful.
2. The primary objective is to obtain a voluntary written confession.
3. The interviewer is likely to begin the interview with open-ended questions.
4. Video recordings always should be used to provide the highest quality evidence.
According to IIA guidance, which of the following is true regarding the exit conference for an internal audit engagement?
During an assurance engagement, an internal auditor noted that the time staff spent accessing customer information in large Excel spreadsheets could be reduced significantly through the use of macros. The auditor would like to train staff on how to use the macros. Which of the following is the most appropriate course of action for the internal auditor to take?
An audit identified a number of weaknesses in the configuration of a critical client/server system. Although some of the weaknesses were corrected prior to the issuance of the audit report, correction of the rest will require between 6 and 18 months for completion. Consequently, management has developed a detailed action plan, with anticipated completion dates, for addressing the weaknesses. What is the most appropriate course of action for the chief audit executive to take?
An internal auditor is assessing the organization's risk management framework. Which of the following formulas should he use to calculate the residual risk?
A) 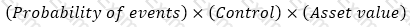
B)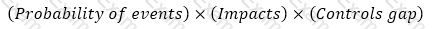
C) 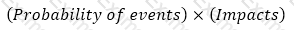
D) 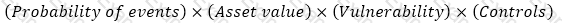
A chief audit executive is preparing interview questions for the upcoming recruitment of a senior internal auditor. According to IIA guidance, which of the following attributes shows a candidate's ability to probe further when reviewing incidents that have the appearance of misbehavior?
A large retail organization, which sells most of its products online, experiences a computer hacking incident. The chief IT officer immediately investigates the incident and concludes that the attempt was not successful. The chief audit executive (CAE) learns of the attack in a casual conversation with an IT auditor. Which of the following actions should the CAE take?
1. Meet with the chief IT officer to discuss the report and control improvements that will be implemented as a result of the security breach, if any.
2. Immediately inform the chair of the audit committee of the security breach, because thus far only the chief IT officer is aware of the incident.
3. Meet with the IT auditor to develop an appropriate audit program to review the organization's Internet-based sales process and key controls.
4. Include the incident in the next quarterly report to the audit committee.
It is close to the fiscal year end for a government agency, and the chief audit executive (CAE) has the following items to submit to either the board or the chief executive officer (CEO) for approval. According to IIA guidance, which of the following items should be submitted only to the CEO?
Which of the followings statements describes a best practice regarding assurance engagement communication activities?
If observed during fieldwork by an internal auditor, which of the following activities is least important to communicate formally to the chief audit executive?
Which of the following is not a primary reason for outsourcing a portion of the internal audit activity?
Which of the following recommendations made by the internal audit activity (IAA) is most likely to help prevent fraud?
The internal audit activity (IAA) wants to measure its performance related to the quality of audit recommendations. Which of the following client survey questions would best help the IAA meet this objective?
Which of the following combinations of conditions is most likely a red flag for fraud?
According to IIA guidance, which of the following must the internal auditor consider to meet the requirements for due professional care?
According to IIA guidance, which of the following must internal auditors consider to conform with the requirements for due professional care during a consulting engagement?
1. The cost of the engagement, as it pertains to audit time and expenses in relation to the potential benefits.
2. The needs and expectation of clients, including the nature, timing, and communication of engagement results.
3. The application of technology-based audit and other data analysis techniques, where appropriate.
4. The relative complexity and extent of work needed to achieve the engagement's objectives.
An organization is beginning to implement an enterprise risk management program. One of the first steps is to develop a common risk language. Which of the following statements about a common risk language is true?
According to COSO, which of the following describes a principle related to the control environment?
An organization has implemented a software system that requires a supervisor to approve transactions that would cause treasury dealers to exceed their authorized limit. This is an example of which of the following types of controls?
An internal auditor uses a predefined macro provided in a popular spreadsheet application to verify the present value of the organization's investments. Which of the following is the most appropriate course of action regarding the auditor's use of this functionality?
According to IIA guidance, which of the following statements describes one of the similarities between assurance and consulting services?
While auditing an organization's credit approval process, an internal auditor learns that the organization has made a large loan to another auditor's relative. Which course of action should the auditor take?
Which of the following actions should the audit committee take to promote organizational independence for the internal audit activity?
Which of the following is a weakness of observation as audit evidence?
Which of the following is a requirement for an assurance engagement that may not be for a consulting engagement?
A chief audit executive (CAE) is reviewing the internal audit activity's performance and is concerned that the average number of revisions to findings is steadily rising, making it increasingly difficult to trace the finding to the supporting evidence and workpapers. According to MA guidance, which of the following elements of the internal audit activity's quality assurance and improvement program would provide the CAE with the most helpful insight into the cause of this problem?
Which of the following is not an objective of internal control?
According to IIA guidance, which of the following is an area in which the internal auditor should be proficient?
According to COSO, which of the following is not considered one of the components of an organization's internal environment?
According to IIA guidance, which of the following external groups is most likely to represent a liability risk, based on activities associated with the organization's corporate social responsibility program?
The manager for an organization's accounts payable department resigned her post in that capacity. Three months later, she was recruited to the internal audit activity and has been working with the audit team for the last eight months. Which of the following assignments would the newly hired internal auditor be able to execute without any impairments to independence or objectivity?
According to The IIA's Code of Ethics, which of the following statements is true?
Faced with a complex, highly technical construction audit engagement, the chief audit executive (CAE) considered complementing the current internal audit resources by engaging the services of a civil engineer.
Which of the following should the CAE consider in determining whether the engineer possesses the necessary skills to perform the engagement?
1. Professional certification, license, or other recognition of the engineer's competence in the relevant discipline.
2. Experience of the engineer in the type of work being considered.
3. Compensation or other incentives that the engineer may receive.
4. The extent of other ongoing services that the engineer may be performing for the organization.
The chief audit executive (CAE) of a small internal audit activity (IAA) performs all high-risk engagements on the annual audit plan to make use of his knowledge and experience and to maximize the efficient use of audit resources. Which of the following statements is most relevant regarding this practice?
Which of the following statements is true with regard to conducting an effective quality assurance and improvement program?
According to IIA guidance, which of the following statements is true regarding periodic internal assessments of the internal audit activity?
Which of the following options is the most cost-effective and efficient way for internal auditors to keep current with the latest developments in the internal audit profession?
Which of the following is an example of a management control technique?
Which of the following responsibilities would fall under the role of the chief audit executive, rather than internal audit staff or the audit manager?
Which of the following techniques would provide the most compelling evidence that a safety hazard exists within a manufacturing facility?
A former line supervisor from the Financial Services Department has completed six months of a two-year development opportunity with the internal audit activity (IAA). She is assigned to a team that will audit the organization's payroll function, which is managed by the Human Resources Department. Which of the following statements is most relevant regarding her independence and objectivity with respect to the payroll audit?
Management would like to self-assess the overall effectiveness of the controls in place for its 200-person manufacturing department. Which of the following client-facilitated approaches is likely to be the most efficient way to accomplish this objective?
Which of the following is an example of collusion?
The process of scenario planning begins with which of the following steps?
An organization produces two products, X and Y. The materials used for the production of both products are limited to 500 kilograms (kg) per month. All other resources are unlimited and their costs are fixed. Individual product details are as follows:
Product X
Product Y
Selling price per unit
$10
$13
Materials per unit (at $1/kg)
2 kg
6 kg
Monthly demand
100 units
120 units
In order to maximize profit, how much of product Y should the organization produce each month?
Which of the following application software features is the least effective control to protect passwords?
Which of the following statements is true regarding a bring-your-own-device (BYOD) environment?
A holding company set up a centralized group technology department, using a local area network with a mainframe computer to process accounting information for all companies within the group. An internal auditor would expect to find all of the following controls within the technology department except:
When granting third parties temporary access to an entity's computer systems, which of the following is the most effective control?
At what point during the systems development process should an internal auditor verify that the new application's connectivity to the organization's other systems has been established correctly?
Which of the following is the most effective control to prevent unauthorized entrance of a former employee of the organization?
Which of the following statements pertaining to a market skimming pricing strategy is not true?
Which of the following is not a potential area of concern when an internal auditor places reliance on spreadsheets developed by users?
The percentage of sales method, rather than the percentage of receivables method, would be used to estimate uncollectible accounts if an organization seeks to:
Providing knowledge, motivating organizational members, controlling and coordinating individual efforts, and expressing feelings and emotions are all functions of:
In which of the following plans is an employee most likely to find guidance on action and performance standards?
In which type of business environment are price cutting strategies and franchising strategies most appropriate?
Which of the following describes a typical desktop workstation used by most employees in their daily work?
An organization's balance sheet indicates that the total asset amount and the total capital stock amount remained unchanged from one year to the next, and no dividends were declared or paid. However, the organization reported a loss of $200,000. Which of the following describes the most likely year-over-year change to the organization's total liabilities and total stockholder equity?
Which of the following conditions could lead an organization to enter into a new business through internal development rather than through acquisition?
Which of the following standards would be most useful in evaluating the performance of a customer-service group?
How do data analysis technologies affect internal audit testing?
Which of the following is not included in the process of user authentication?
Technological uncertainty, subsidy, and spin-offs are usually characteristics of:
In terms of international business strategy, which of the following is true regarding a multi-domestic strategy?
The market price is the most appropriate transfer price to be charged by one department to another in the same organization for a service provided when:
The greatest advantage of functional departmentalization is that it:
Organizations use matrix management to accomplish which of the following?
Maintenance cost at a hospital was observed to increase as activity level increased. The following data was gathered:
Activity Level -
Maintenance Cost
Month
Patient Days
Incurred
January
5,600
$7,900
February
7,100
$8,500
March
5,000
$7,400
April
6,500
$8,200
May
7,300
$9,100
June
8,000
$9,800
If the cost of maintenance is expressed in an equation, what is the independent variable for this data?
Which of the following are typical audit considerations for a review of authentication?
1. Authentication policies and evaluation of controls transactions.
2. Management of passwords, independent reconciliation, and audit trail.
3. Control self-assessment tools used by management.
4. Independent verification of data integrity and accuracy.
An organization decided to install a motion detection system in its warehouse to protect against after-hours theft. According to the COSO enterprise risk management framework, which of the following best describes this risk management strategy?
The critical path for any project is the path that exhibits which of the following characteristics?
Which of the following IT-related activities is most commonly performed by the second line of defense?