In Rule Response, which two (2) options are available for Offense Naming?
New vulnerability scanners are deployed in the company's infrastructure and generate a high number of offenses. Which function in the Use Case Manager app does an analyst use to update the list of vulnerability scanners?

From the Offense Summary window, how is the list of rules that contributed to a chained offense identified?
Which two (2) aggregation types are available for the pie chart in the Pulse app?
When using the Dynamic Search window on the Admin tab, which two (2) data sources are available?
When searching for all events related to "Login Failure", which parameter should a security analyst use to filter the events?
QRadar analysts can download different types of content extensions from the IBM X-Force Exchange portal. Which two (2) types of content extensions are supported by QRadar?
Which statement regarding the Assets tab is true?
Which two (2) columns are valid for searches in the My Offenses and All Offenses tabs in QRadar?
How can an analyst search for all events that include the keyword "access"?
What Is the result of the following AQL statement?
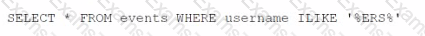
Which two (2) options are used to search offense data on the By Networks page?
What does this example of a YARA rule represent?
rule ibm_forensics : qradar
meta:
description = “Complex Yara rule.“
strings:
Shexl = {4D 2B 68 00 ?? 14 99 F9 B? 00 30 Cl 8D}
Sstrl = "IBM Security!"
condition:
Shexl and (#strl > 3)
How can an analyst improve the speed of searches in QRadar?
An analyst wants to implement an AQL search in QRadar. Which two (2) tabs can be used to accomplish this implementation?
What does this example of a YARA rule represent?
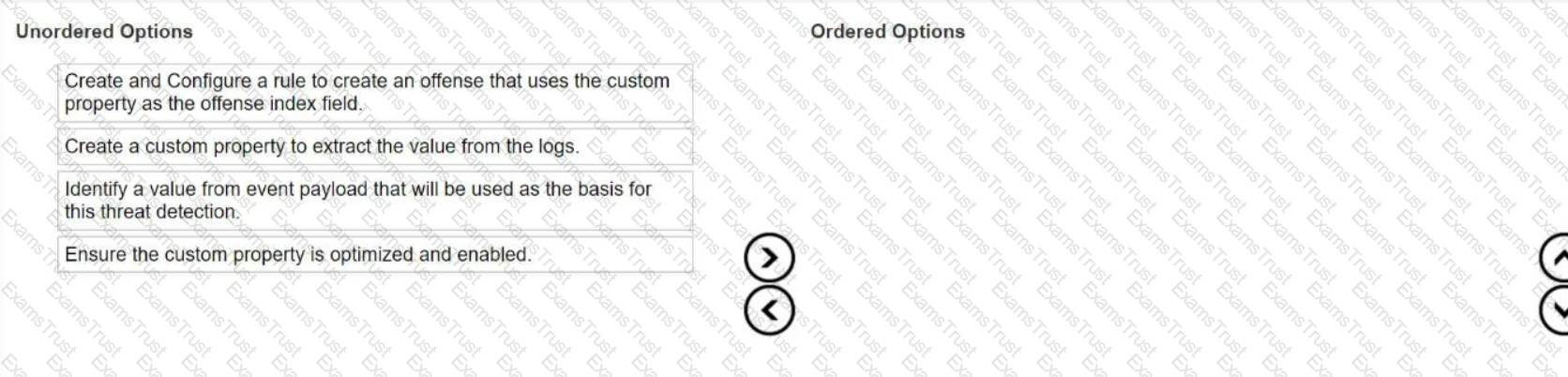
A new log source was configured to send events to QRadar to help detect a malware outbreak. A security analyst has to create an offense based on properties from this payload but not all the information is parsed correctly.
What is the sequence of steps to ensure that the correct information is pulled from the payload to use in a rule?
Which statement regarding the use of the internal structured language of the QRadar database is true?
What is the effect of toggling the Global/Local option to Global in a Custom Rule?
Which log source and protocol combination delivers events to QRadar in real time?
On the Reports tab in QRadar. what does the message "Queued (position in the queue)" indicate when generating a report?
An analyst wishes to review an event which has a rules test against both event and flow data.
What kind of rule is this?
Where can you view a list of events associated with an offense in the Offense Summary window?
Which kind of information do log sources provide?
Which IBM X-Force Exchange feature could be used to query QRadar to see if any of the lOCs were detected for COVID-19 activities?
An analyst runs a search with correct AQL. but no errors or results are shown.
What is one reason this could occur?
Which statement regarding saved event search criteria is true?
What are the behavioral rule test parameter options?
Which two (2) types of data can be displayed by default in the Application Overview dashboard?
For a rule containing the test "and when the source is located in this geographic location" to work properly, what must a QRadar analyst configure?
A Security Analyst has noticed that an offense has been marked inactive.
How long had the offense been open since it had last been updated with new events or flows?
What process is used to perform an IP address X-Force Exchange Lookup in QRadar?
What type of rules will test events or flows for volume changes that occur in regular patterns to detect outliers?
What does the logical operator != in an AQL query do?
On the Offenses tab, which column explains the cause of the offense?
When an analyst is investigating an offense, what is the property that specifies the device that attempts to breach the security of a component on the network?
Which two (2) values are valid for the Offense Type field when a search is performed in the My Offenses or All Offenses tabs?
Which type of rule requires a saved search that must be grouped around a common parameter
When investigating an offense, how does one find the number of flows or events associated with it?
Which two (2) options are at the top level when an analyst right-clicks on the Source IP or Destination IP that is associated with an offense at the Offense Summary?
How long does QRadar store payload indexes by default?