There are multipleSR-MPLS TE tunnel protection mechanisms.FRR (Fast Reroute)constructs avirtual nodeto convert multiple identical route advertisement nodes into a single route advertisement node, and then computes the backup next hop of the virtual node based on theTI-LFA algorithm. In this way, traffic can be quickly switched when a fault occurs.
What is the name of this protection mechanism?
iMaster NCE-CampusInsightuses SNMP technology to collect metrics and logs of network devices and detects network exceptions based on real service traffic.
The ________ command can be run to completely isolate Layer 2 and Layer 3 of different interfaces in a VLAN. (Use lowercase letters to supplement the command, which cannot be abbreviated.)
Which of the following statements about GRE is incorrect?
NETCONF provides a set of mechanisms for managing network devices. What layers can NETCONF be conceptually partitioned into?
On the network shown in the figure, OSPF-based SR-MPLS TE is enabled on all routers. Which of the following adjacency labels are allocated by P3?
In the firewall hot standby scenario, when VGMP works in load balancing mode, which of the following functions must be enabled on the firewalls to prevent the return traffic from being discarded because it does not match any session entry in the case of inconsistent forward and return paths?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
Which of the following channels are involved in the Huawei SD-WAN Solution?
In SSP packages, Jinja2 templates are used to implement mapping. In the Jinja2 syntax, {% ... %} contains control structures, for example, a 'for' loop.
In an MPLS domain, LSRs can be classified into ingress, transit, and egress LSRs based on how they process data. For the same FEC, an LSR can be both an ingress and a transit LSR of the FEC.
In the Huawei CloudCampus Solution, which of the following deployment modes are supported by Huawei switches?
In the Huawei SD-WAN Solution, which of the following routing protocols is used to advertise VPN routes between CPEs?
HTTP/2 is a UDP-based low-delay Internet transport layer protocol.
A VGMP packet is encapsulated with a UDP header and a VGMP header. By default, a VGMP packet uses UDP port _____.
Flavors can be used to enhance SRv6 instructions to meet more diversified service requirements. Which of the following are flavors? (Select all that apply)
The following figure shows the inter-AS MPLS VPN Option B solution. IfASBR-PE1andASBR-PE2only transmit VPNv4 routes, you can run the following command onASBR-PE1:
[ASBR-PE1-bgp-af-vpnv4] undo peer 10.0.34.4 enable
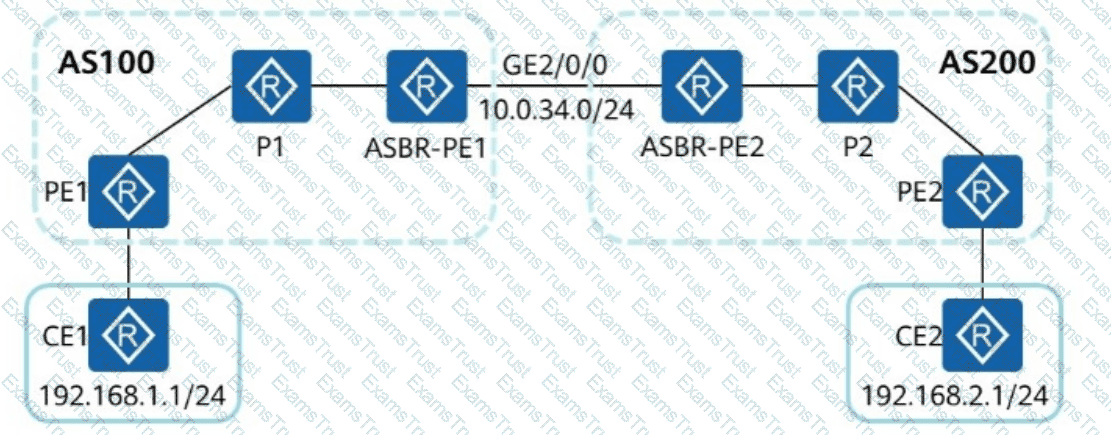
Which of the following statements regarding RT are correct?
To obtain thetoken IDofiMaster NCE, you need to send anHTTP requestusing the followingPython codeto invoke aniMaster NCE RESTful API:
Which of the following statements isincorrect?
In the SD-WAN Solution, which routing protocols can be used by LAN-side devices to connect to a Layer 3 network?
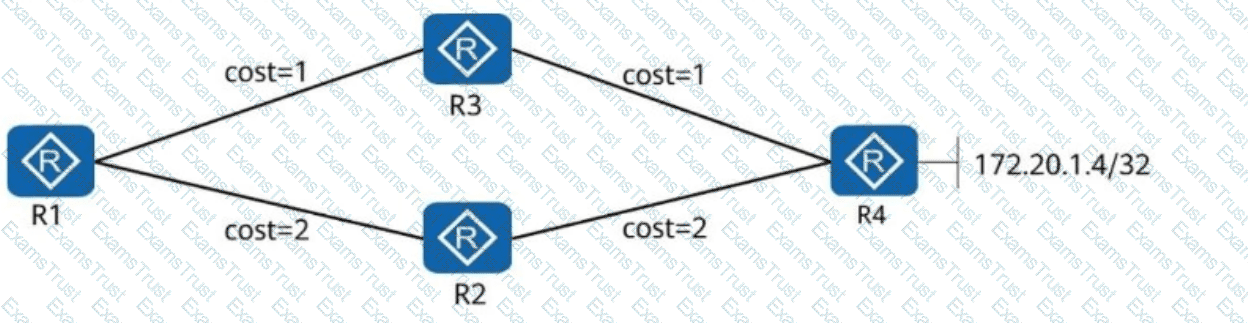
Based on the figure, which of the following statements are correct?
1 10.1.12.2 40 ms 10 ms 10 ms
2 10.1.24.2 30 ms 20 ms 20 ms
3 10.1.34.1 20 ms 20 ms 20 ms
4 10.1.13.1 20 ms 20 ms 10 ms
5 10.1.12.2 20 ms 30 ms 20 ms
6 10.1.24.2 30 ms 30 ms 30 ms
7 10.1.34.1 50 ms 40 ms 40 ms
8 10.1.13.1 20 ms 30 ms 30 ms
Based on the configuration in the following figure, how many interfaces on R4 are advertised into IS-IS?
plaintext
CopyEdit
Interface information for ISIS(1)
Interface Id IPV4.State IPV6.State MTU Type DIS
GE0/0/0 001 Up Down 1497 L1/L2 No/No
GE0/0/1 002 Up Down 1497 L1/L2 No/No
Loop0 001 Up Down 1500 L1/L2 -
NETCONF uses an XML-based encoding format. NETCONF uses text files to represent complex hierarchical data. Which of the following statements are correct about the following XML file?
When MPLS/BGP IP VPN is deployed, which of the following statements is incorrect about BGP route exchange between PEs and CEs?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows. Which of the following routes will be selected according to the conflict handling principle?
MACsec can provide secure services during MAC-layer data transmitting and receiving. Which of the following services isnotprovided by MACsec?
Which of the following items are included in static information collection and analysis?
Which of the following intelligent traffic steering policies can be used to fully utilize link bandwidth and implement link bandwidth-based load balancing on an enterprise network with multiple links?
Prefix segments and adjacency segments are globally visible and unique.
During WLAN planning and design, channels 1, 6, and 11 are recommended on the 2.4 GHz frequency band, and channels 1, 5, 9, and 13 are recommended in high-density scenarios. On the 5 GHz frequency band, it is recommended thathigh-frequency and low-frequency channels of adjacent APs be staggered to prevent overlapping.
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
When an NVE encapsulates a data frame into a VXLAN packet, information of which of the following protocols is encapsulated between the outer IP header and the VXLAN header?
An LSR supports various label retention modes. Which of the following statements regarding the liberal mode are correct?
On the network shown in the following figure, a remote LDP session needs to be established between SWA and SWC. Which of the following statements is correct?
[SWA] mpls lsr-id 1.1.1.1
[SWA] mpls
[SWA-mpls] mpls ldp
[SWC] mpls lsr-id 33.3.3.3
[SWC] mpls
[SWC-mpls] mpls ldp
SWA ---- SWB ---- SWC
<------ Remote LDP Session ------>
Theon-premise modeis recommended for controller deployment onsmall and midsize campus networks.
How long is an IPv6 prefix assigned to a host when an IPv6 address is configured for the host in SLAAC mode?
OSPFv3 link LSAs are advertised in the entire area.
Which of the following number sequences can be matched by the regular expression 100.s?
Which of the following are advantages of GRE tunnels? (Select All that Apply)
The figure shows a packet that contains three label headers. Select the values (in decimal notation) of the X, Y, and Z fields, respectively.
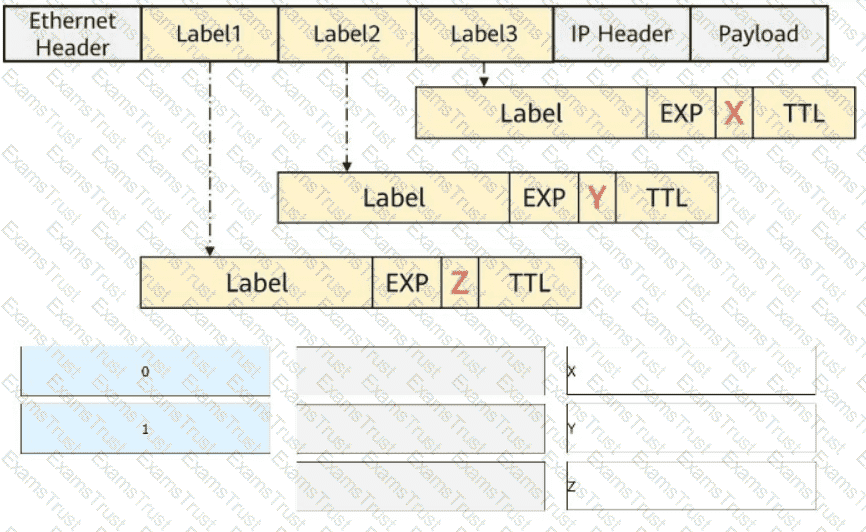
With telemetry, certain data can be sampled based on specific sampling paths. Which of the following sampling paths are supported by telemetry?
Exhibit:
A loop occurs because Spanning Tree Protocol (STP) is not enabled on the network. Which of the following symptoms may occur?
Huawei CloudCampus Solution has multiple application scenarios, and iMaster NCE-Campus provides different APIs for each application scenario. Match the following application scenarios with the open APIs provided by iMaster NCE-Campus.
In the following figure, R1, R2, R3, and R4 all belong to OSPF area 0. The link costs are marked in the figure. The Loopback0 addresses of R1, R2, R3, and R4 are advertised to OSPF. R1, R2, and R3, which are R4 clients, use Loopback0 to establish an iBGP peer relationship with R4. The directly connected network segment 172.20.1.4/32 of R4 is advertised to BGP. Which of the following statements are correct about the direction of traffic from R1 to 172.20.1.4/32?
An SRv6 Policy can be either statically configured on a device or dynamically generated by the controller and then delivered to the device.
As shown in the following figure, OSPF is deployed on a campus network to implement network interconnection, and Area 1 is deployed as an NSSA. To enable R1 to access R4’s loopback interface address, an engineer imports a direct route to R4’s OSPF process. Which of the following statements about this scenario are correct?
[R4-ospf-1] import-route direct
Loopback0: 10.1.4.4/32
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is ______ IRB forwarding. (Capitalize the first letter.)
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
A network administrator runs the display telemetry destination command on a device to check information about a destination group that sampled data is sent to. The command output is as follows. Which of the following statements is incorrect?
[~CE-telemetry-sensor-group-Sensor1]display telemetry destination
Dest-name Dest-addr Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
The path of an SR-MPLS TE tunnel can be calculated by the controller or tunnel ingress.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following statements about symmetric IRB forwarding are correct?
Which of the following statements about BGP EVPN principles are correct in a scenario where a VXLAN tunnel is dynamically established through BGP EVPN?
The BGP ORF function can be used to control the maximum number of routes that can be sent by a BGP peer. To achieve this, which of the following tools is used to send such a route list to BGP peers?
BGP EVPN can be used as the VXLAN control plane protocol to completely prevent traffic flooding, such as broadcast ARP packets, on the VXLAN network.
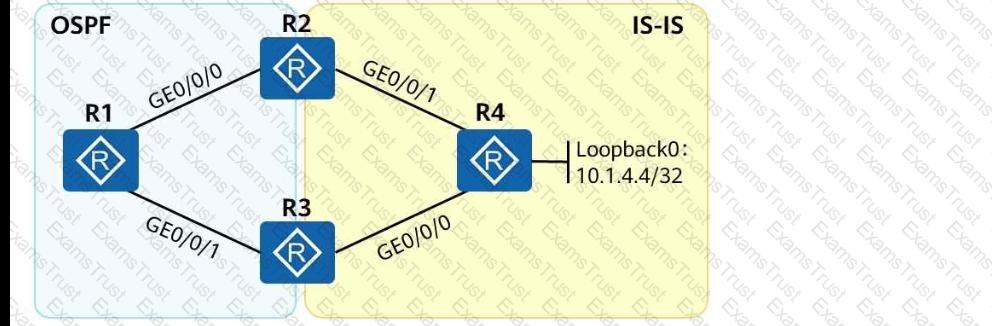
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
In thesmall and midsize campus network designbased on theHuawei CloudCampus Solution, when over100 branchesneed to communicate with each other, which of the following interconnection networking models is recommended?
For telemetry data push, data can be transferred between devices and collectors using the TLS protocol. TLS must be configured for data encryption if data is pushed based on gRPC.
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
Which of the following statements aboutprefix segments and adjacency segmentsare correct?
Whenstatic IPsec VPNis used for WAN interconnection in theHuawei CloudCampus Solution, theAP, Router, and ____can be used as egress devices.
Which of the following issues do DiffServ model-based QoS have?
When aclient invokes the iMaster NCE-Campus RESTful API, it sends anHTTP request. The server then returns thestatus code 401.
Which of the following errors has occurred?
NAFTIR policing can only be applied to the inbound direction. Its purpose is to monitor the traffic entering the device and ensure that the upstream device does not unnecessarily consume network resources.
Among NETCONF operations, the
R1 receives a common IPv6 packet from the CE and generates a packet carrying the SRH (Segment Routing Header), as shown in the figure. The packet is forwarded along the path R1 → R2 → R3 → R4. Identify the node type of each device based on their role in SRv6 processing.
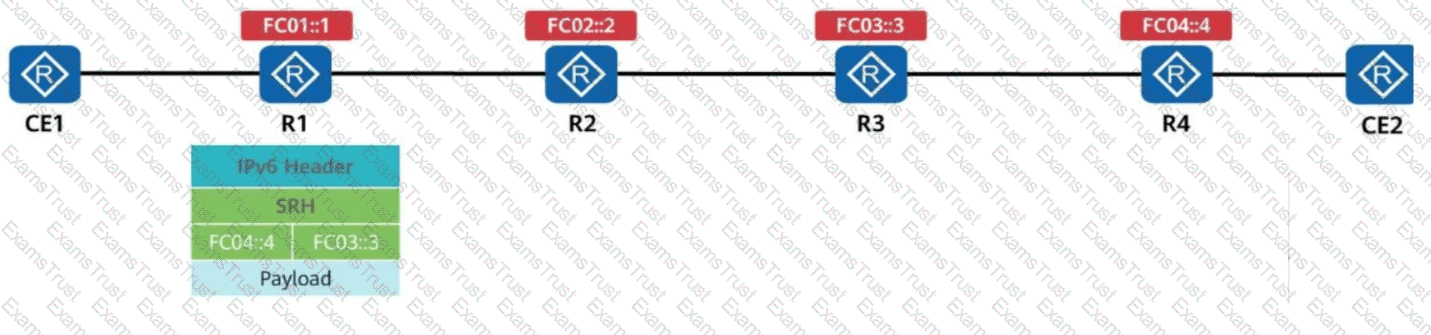

In the firewall hot standby scenario, which of the following status information can be backed up between the active and standby firewalls?
Network administrator A wants to view the BGP peer status of R2. The BGP peer status of R2 is shown in this figure. Obtain the following information: R2 resides in AS _____ (Enter only digits. Do not add punctuations or spaces.)
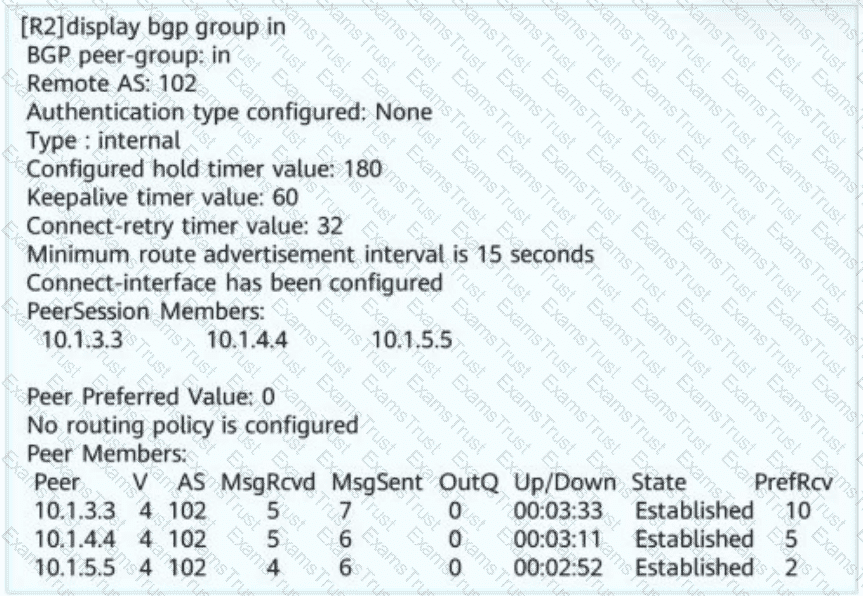
The naming of SRv6 instructions complies with certain rules. You can quickly determine the function of an instruction based on the instruction name. Which of the following statements about the keywords in SRv6 instruction names are correct? (Select all that apply)
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
A network administrator runs the display telemetry subscription command on a device to check telemetry subscription information. The command output is as follows. Which of the following statements is incorrect?
[~CE] display telemetry subscription
Sub name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20030 RESOLVED - GRPC
Sub state : PASSIVE
Total subscription number is : 1
Drag the IPsec functions on the left to the corresponding function description on the right.
Which of the following factors does not need to be considered during the selection of core devices for the enterprise bearer WAN?
In the CloudCampus public cloud scenario, if deployment through the Huawei registration query center is used, you do not need to configure DHCP Option 148 on the DHCP server of the campus network.
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
Which of the following statements isincorrectaboutintranet security designfor a large or medium-sizedvirtualized campus network?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. HTTP is the most widely used network transmission protocol on the Internet. By default, the TCP port number _____ is used. (Fill in Arabic numerals.)
Which of the following statements about VXLAN principles is incorrect?
Which of the following can be used to transmit traffic to a VXLAN network and implement intra-subnet communication on the same VXLAN network?
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
Which of the following number sequences can be matched by the regular expression100.$?
In the gRPC-based telemetry protocol, the data model layer consists of theRPC layer,telemetry layer, andservice data layer. Drag the.proto fileto the layer where the file should be located.
Which of the following inter-AS MPLS L3VPN solutions does not require MPLS to run between ASBRs?
The following figure shows some configurations of R1. Based on these configurations, which of the following statements about IS-IS on R1 are correct?
isis 1
is-level level-2
cost-style wide
network-entity 49.0022.ee8c.a0c2.baf1.00
isis 2 vpn-instance tt
is-level level-2
cost-style wide
network-entity 47.00ce.390d.efdc.b3e1.00
isis 3 vpn-instance rr
is-level level-2
cost-style wide
network-entity 47.cc0a.3efb.bbdd.aae1.00
In a scenario whereSR Policiesare dynamically established through thecontroller, which of the following statements about theSR Policy solution architectureis incorrect?
If an engineer wants to remotely log in to a Huawei device, the engineer uses the Paramiko library to compile the following code when compiling the SSH Python script:
cli = ssh.invoke_shell()
cli.send("screen-length 0 temporary\n")
What is the function of screen-length 0 temporary?
iMaster NCE-Campus provides the terminal identification function to display the terminal type, operating system, and manufacturer information.
Which of the following are application optimization functions in the Huawei SD-WAN Solution?
Telemetry data must be encoded in GPB binary format. This format reduces the number of bytes in telemetry messages and improves the transmission efficiency compared with messages encoded in JSON format.
HTTP is an application layer protocol for distributed, collaborative, and hypermedia information systems.
You have developed a third-party Portal authentication application and connected it to iMaster NCE-Campus to perform Portal authentication for Wi-Fi users. After connecting to Wi-Fi, a user will be redirected to the login page pushed by the authentication application when visiting any website for the first time.
In addition to indicating priority, the DSCP value can also indicate the drop probability. Which of the following DSCP values is set with the highest drop probability?
After a wireless user passes Portal authentication, which of the following parameterscannotbe used for authorizing the user?
Congestion avoidance technology can prevent congestion on an interface.
OSPFv2 is an IGP running on IPv4 networks, whereas OSPFv3 is an IGP running on IPv6 networks. OSPFv2 and OSPFv3 have similar LSA types, but their LSA functions are slightly different. Which of the following is not an OSPFv3 LSA type?
Network administrator A wants to use an IP prefix list to match specific routes. Which of the following routes can be matched by the IP prefix list shown in this figure?
ip ip-prefix TEST permit 10.0.0.0 24 less-equal 30
Which of the following statements about configuring user access authentication is incorrect?