On a WLAN, MAC address authentication controls network access rights of a user based on the user's access interface and terminal MAC address.
Which of the following statements is false about MAC address authentication?
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
When receiving a packet that does not match any session table entry, the firewall discards the packet to prevent external attacks and ensure internal information security.
If a router ID is configured in both the system via and the BGP view, BGP uses the router ID configured in the BGP view because the BGP view takes precedence over the system view.
A router uses an advanced ACL to filter data. The ACL configuration is shown below. Which of the following statements is false about the configuration?
csharp
CopyEdit
[Huawei] acl 3001
[Huawei-acl-adv-3001] rule permit icmp source 192.168.1.3 0 destination 192.168.2.0 0.0.0.255
Which of the following statements about the forwarding plane of a switch is false?
Which of the following statements about BFD operating modes are true?
As a next-generation wireless technology, Wi-Fi 6 greatly improves bandwidth rate and performance. Which of the following statements isfalseabout the features of Wi-Fi 6?
Which of the following statements regarding the firewall zone security level is false?
Which of the following statements regarding the MED value in BGP are true?
iMaster NCE-Campus can be used as an authentication server on a WLAN to authenticate STAs.
Route summarization can effectively reduce the number of BGP routes. However, many parameters need to be properly set when configuring BGP route summarization. Otherwise, problems such as routing loops may occur.
Which of the following statements is false about BGP route summarization?
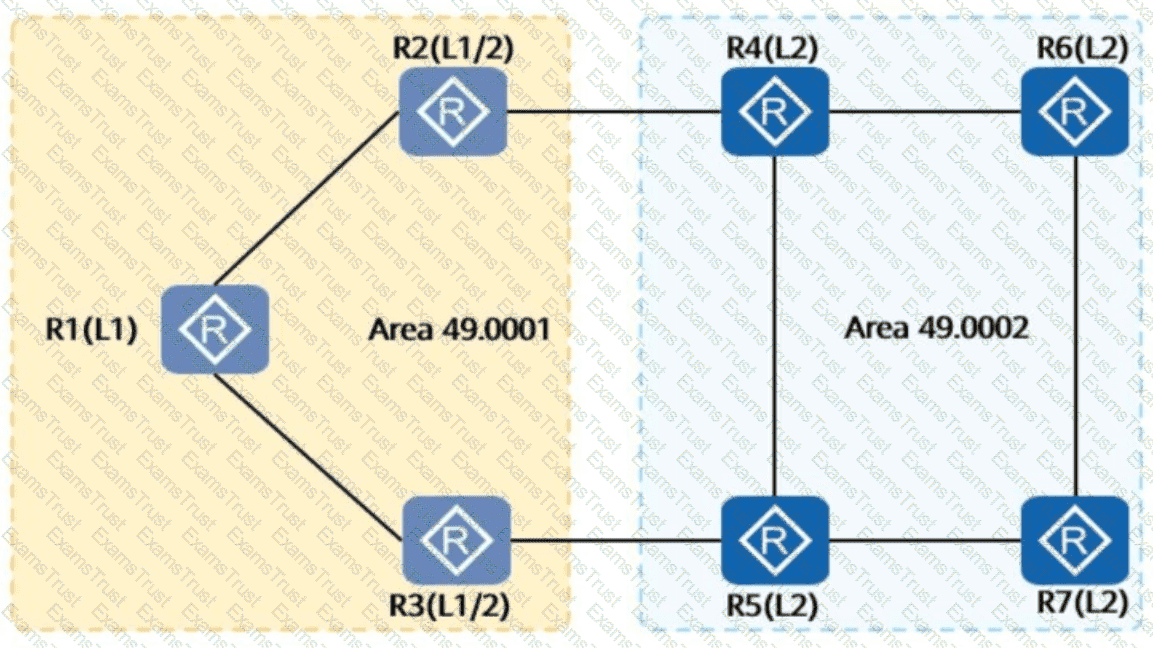
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
BGP is a distance-vector protocol that implements route reachability between ASs and selects optimal routes. Which of the following statements are true about this protocol?
In PIM-DM, which of the following processes are involved in SPT establishment?
Which of the following statements regarding routing policy and policy-based routing are true?
When receiving a packet, a Huawei router matches the packet against ACL rules. The default ACL matching order used by the Huawei router is.
IGMPv2 uses the timeout mechanism for group members leaving a group. Group members can only leave a group silently. Before the timeout period expires, multicast traffic is still forwarded by the multicast router, and this is a defect.
During routine maintenance, an enterprise administrator runs a command to check VRRP group information. Which of the following statements is false about the command output?
yaml
CopyEdit
Vlanif100 | Virtual Router 1 State: Master
Virtual IP: 10.1.1.100
Master IP: 10.1.1.2
PriorityRun: 120 PriorityConfig: 120
DR: None BDR: None MTU: 0
Preempt: YES Delay Time: 20s
Remain: --
Track: YES Priority Reduced: 20
Auth Type: MD5
BFD-session State: UP
After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
The Neighbor Discovery Protocol (NDP) is an important basic protocol in the IPv6 protocol suite and plays an important role. Which of the following functions and features does it support?
On an OSPF network, Type 7 LSAs can be generated only by ASBRs in NSSAs or stub areas and describe AS-external routes.
Which of the following statements regarding IGMPv1 and IGMPv2 are true?
ICMPv6 messages are classified as error or informational messages.
The VRID of the VRRP virtual router is 3 and the virtual IP address is 100.1.1.10. What is the virtual MAC address?
IGMP group entries play an important role in multicast forwarding. An administrator runs a command to view information about a multicast entry. The information is as follows:
sql
Copy
Interface group report information
Vlanif100(10.1.6.2):
Total 1 IGMP Group reported
Group Address Last Reporter Uptime Expires
225.1.1.2 10.1.6.10 00:02:04 00:01:17
Given this, which of the following statements are true?
Which of the following is used as the destination port for single-hop BFD?
An enterprise network runs OSPF to implement network communication. Which of the following types of LSAs may be generated by an ABR?
Which of the following statements regarding the display bgp routing-table command output is true?
Compared with RSTP, which of the following port roles are added to MSTP?
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?
InIP multicast transmission, packets are transmitted from a source to agroup of receivers. Which of the following statements aretrueabout IP multicast technologies?
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
A monitoring plane usually comprises the monitoring units of main control boards and interface boards. This plane can monitor the system environment independently. Which of the following environment monitoring functions can be provided by the monitoring plane?
There are two types of routing entries on a PIM network. (S, G) routing entries are used to set up on a PIM network and are applicable to both PIM-DM and PIM-SM networks.
Which of the following statements regarding the OSPF protocol is false?
As shown in the figure, data traffic is forwarded in tunnel mode along the path of STA -> HAP -> HAC -> upper-layer network before roaming. What is the flow direction of data traffic after Layer 3 roaming?
During BGP route summarization configuration, the keyword can be used to suppress all specific routes so that only the summary route is advertised. The summary route carries the Atomic-aggregate attribute rather than the community attributes of specific routes.
Which of the following statements regarding DR/BDR are false?
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
On an OSPF network, if a router functions as an ABR, the router must also be a BR.
On aBGP network, aroute-policycan be used to modify route attributes. Which of the following statements isfalseaboutroute-policies?
RSTP provides different functions in different scenarios. Which of the following statements Is false?
On an RSTP network, port priorities may be compared during root port or designated port election. Which of the following values is the default priority of a port on a Huawei switch?
Hackers often obtain the login permissions of system administrators through various attacks.
Which of the following measures can be taken to enhance the security of administrator accounts?(Select all that apply)
As shown in the figure, R1 imports the direct route10.1.1.0/24to OSPF. An engineer enablesbidirectional route re-advertisementon R2 and R3.
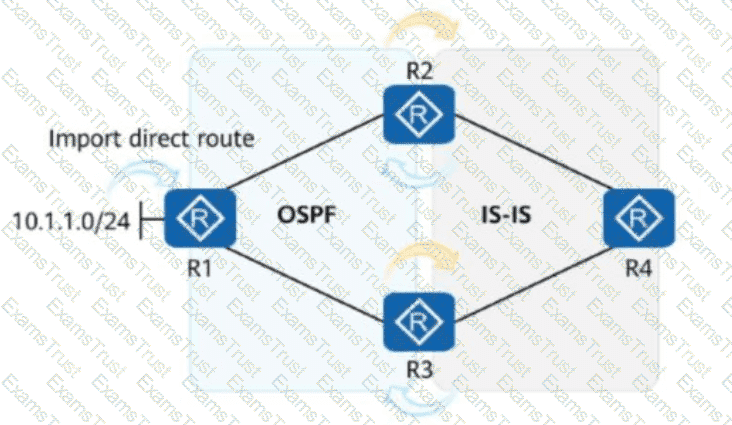
After the network becomes stable, which of the following is thePre (preference) valueof the route10.1.1.0/24in therouting table of R3?
An IP prefix list is a common matching tool used in routing policies. Which of the following cannot be configured as matching conditions in an IP prefix list on a Huawei router?
InIPv6,NDP (Neighbor Discovery Protocol)uses multiple types ofICMPv6 packets. Which of the following functions areRS (Router Solicitation) packetsused for?
On an OSPF or IS-IS network, the filter-policy import command can be run on a router to filter out the LSAs forwarded by its neighbors.
In BGP, Notification messages are used to request peers to resend routing information after routing policies are changed.
ACLs are a common tool for matching routes. ACLs are classified into multiple types based on ACL rule functions. An ACL can be identified by a number, and the number range for each type of ACLs is different. Which of the following type of ACLs are numbered from 4000 to 4999?
Roaming technologyis typically used on alarge WLANto ensure thatSTA (station) servicesare not interrupted when STAs move between coverage areas of different APs.
To prevent inter-area routing loops, OSPF does not allow advertising routing information between two non-backbone areas and allows sing routing information only within an area or between the backbone area and a non-backbone area. Therefore, each ABR must be connected to the backbone area.
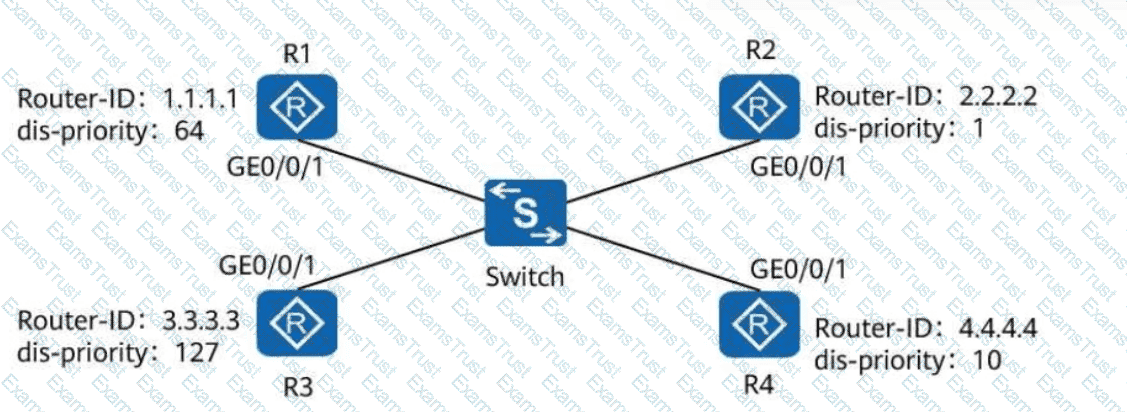
On a broadcast IS-IS network shown in the following figure, a DIS needs to be elected to create and update pseudonodes. Which of the following routers is elected as the DIS?
In the OSPF protocol, inter-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
Which of the following methods is usually used by a network administrator to configure a newly purchased device for the first time?
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
Which of the following statements regarding multicast MAC addresses are false?
Security policy is the core feature of firewalls. Only valid traffic that complies with security policies can be forwarded by firewalls. Which of the following statements are true about security policy matching rules?
In BGP, the AS_Path attribute records the numbers of all ASs that a route passes through from the local end to the destination in the vector order.
Which of the following statements is false about the attribute change during route transmission?
See the network shown in the following figure.
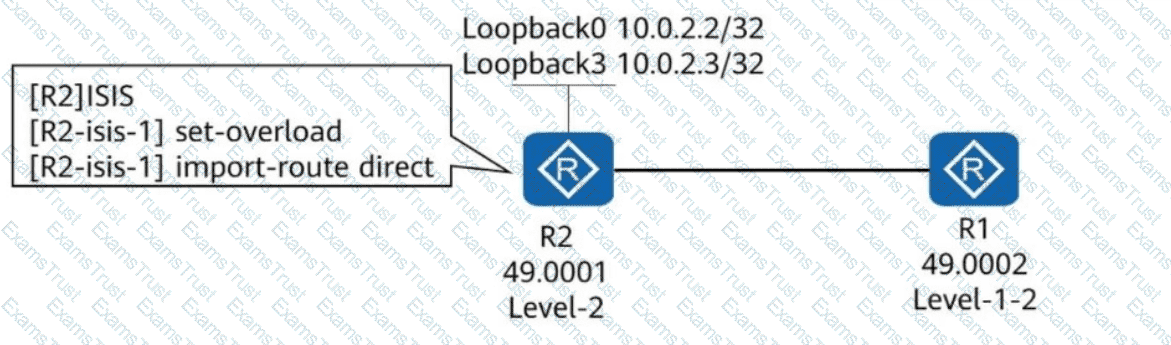
R1 and R2 run IS-IS and establish an adjacency. IS-IS is enabled on Loopback0 of R2 but disabled on Loopback3 of R2. The configurations shown in the figure are performed in the IS-IS process of R2. Which of the following statements are true?
The typical characteristics of the AI era are that it focuses on data, explores data value, and improves AI efficiency. Therefore, the core requirement of AI for data center networks is speed, meaning low latency.
On an IS-IS network, the length and components of aNETare the same as those of anNSAP. Which of the followingNETfields is used to uniquely identify a host or router in an area?
AnIP prefix listis a common matching tool in routing policies. When anIP prefix listis configured on a Huawei router, which of the following parameters areoptional?
When a routing policy is used to filter routes, which of the following route prefixes will be denied by the IP prefix below?
L2TP does not provide security encryption. Therefore, other security measures, such as IPsec, are required to ensure the security of the entire tunnel for data transmission.
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
On an enterprise WLAN where Portal authentication is deployed, an AC functions as an access device and communicates with a Portal server using the Portal protocol. Which of the following statements are true about the Portal protocol?
When creating a single-hop BFD session for the first time, bind the single-hop BFD session to the peer IP address and the local address. To modify a configured BFD session, delete it and create a new one.
PBR is a mechanism for selecting routes based on user-defined policies. There are two types of PBR: interface-based PBR and local PBR. Which of the following statements is false about these two types of PBR?
Which of the following statements is false?
Which of the following statements is false about the default processing of the next hop address when a BGP device advertises a route?
OSPF has several types of special areas, which are used to reduce the LSDB size and improve device performance.
Which of the following LSAs cannot be in a totally stub area?
A forwarding information database (FIB) can directly guide packet forwarding on a router.
The administrator of an enterprise configuresSNMPv3on a device for communicating with theNMS (Network Management System). After the configuration is complete, thedisplay trapbuffercommand output shows that there are traps in the trap buffer of theinformation center, but theNMS does not receive any of them. Which of the following may cause this problem?
The Next_Hop attribute in BGP records the next hop of a route. Similar to the next hop in an IGP, the Next_Hop attribute in BGP must be the IP address of a peer interface.
On an IS-IS network, areas are divided by router, and a router can belong to only one area. Therefore, an IS-IS router only needs to maintain the LSDB of its area.
In BGP, Keepalive messages are used to maintain BGP peer relationships. When a BGP router receives a Keepalive message from a peer, the BGP router sets the state of the peer to Established and periodically sends Keepalive messages to maintain the connection. By default, the device sends Keepalive messages every seconds.
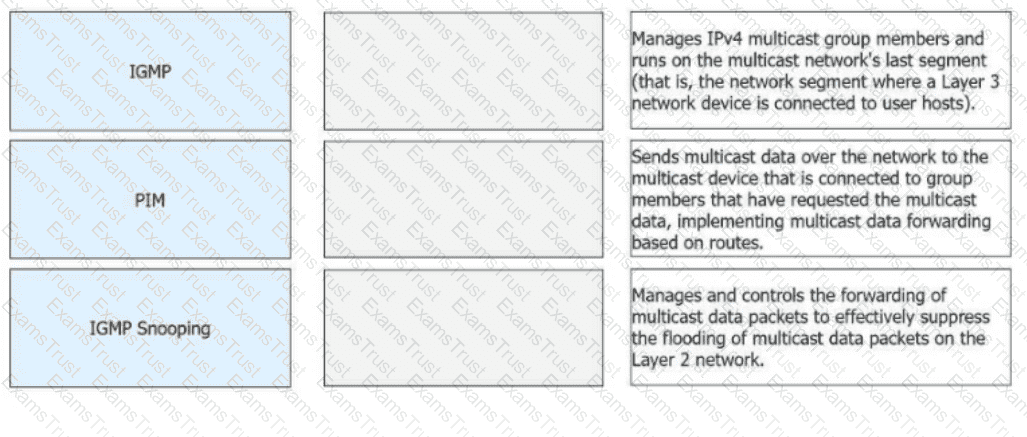
Match the following IPv4 multicast protocols with the corresponding functions.
A non-client is an IBGP peer that functions as neither an RR nor a client. A non-client must establish fully meshed connections with the RR and all the other non-clients.
Which of the following attribute must be carried in an Update message?
The following figure shows acampus network. IS-IS is configured on all routers, and the network runs normally.
By default, which of the following routers havespecific routeson the entire network?
Which of the following statements regarding Local-Preference in BGP is true?
OSPF has five types of packets, which have the same header format. If the Auth Type field in the packet header is 1, which of the following authentication modes is used?
Which of the following statement regarding the display ospf peer command output is true?
A session is an entry used to record the connection status of a protocol and is fundamental for the firewall to forward packets. Which of the following protocol packets will the firewall create sessions for?
Based on IGMP snooping, IGMP snooping proxy enables a switch to act as a substitute for an upstream Layer 3 device to send IGMP Query messages to downstream hosts, and also to act as a substitute for downstream hosts to send IGMP Report/Leave messages to an upstream device. As such, this function conserves bandwidth between the upstream device and the local device.
A Layer 2 switch supports multiple types of Ethernet interfaces. Similar to a trunk interface, a hybrid interface allows data frames from multiple VLANs to pass through. In addition, you can determine whether data frames from a VLAN sent out from a hybrid interface are tagged or untagged.
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
Which of the following statements regarding OSPF multi-instance is false?
An edge port is a new port role added to RSTP to overcome the disadvantages of STP. Which of the following statements is false about this port role?
On an OSPF network, routers learn routing information on the entire network by exchanging LSAs. Which of the following values is the LS Age in the LSA header when an LSA is deleted?
An enterprise administrator wants to configure single-hop BFD to implement fast detection of direct links. Which of the following configurations are mandatory?
In BGP, the Origin attribute is used to identify the origin of a route. Which of the following statements are true about the Origin attribute?
Which of the following statements regarding the LSA age field are true?
OSPF neighbors have multiple states, such as Down, Init, 2-way, Loading, or Full. In which of the following states do OSPF routers negotiate the master and slave roles?