In the following options, which of the two attacks use similar attack methods, they will generate a large number of useless response packets, occupying network bandwidth,
Consume equipment resources?
Due to differences in network environment and system security strategies, intrusion detection systems are also different in specific implementation. From the perspective of system composition, the main
Which four major components are included?
Which of the following threats cannot be detected by IPS?
Which of the following options belong to the upgrade method of the anti-virus signature database of Huawei USG6000 products? (multiple choice)
If the processing strategy for SMTP virus files is set to alert, which of the following options is correct?
Which of the following options is correct for the description of the Anti DDoS system configuration?
Which of the following options are the possible reasons why a certain signature is not included after the IPS policy configuration is completed? (multiple choice)
In the anti-virus policy configuration of Huawei USG6000 product, what are the response methods of HTTP protocol? (multiple choice)
The user needs of a university are as follows:
1. The environment is large, and the total number of two-way traffic can reach 800M. Huawei USG6000 series firewall is deployed at its network node.
2. The intranet is divided into student area, server area, etc., users are most concerned about the security of the server area to avoid attacks from various threats.
3. At the same time, some pornographic websites in the student area are prohibited.
The external network has been configured as an untrust zone and the internal network has been configured as a trust zone on the firewall. How to configure the firewall to meet the above requirements?
155955cc-666171a2-20fac832-0c042c0415
Regarding the mail content filtering configuration of Huawei USG6000 products, which of the following statements is wrong?.
Which of the following options describes the IntelliSense engine IAE incorrectly?
The anti-tampering technology of Huawei WAF products is based on the cache module. Suppose that when user A visits website B, website B has page tampering.
Signs: The workflow for the WAF tamper-proof module has the following steps:.
① WAF uses the pages in the cache to return to the client;
②WAF compares the watermark of the server page content with the page content in the cache
③Store the content of the page in the cache after learning
④ When the user accesses the Web page, the WAF obtains the page content of the server
⑤WAF starts the learning mode to learn the page content of the user's visit to the website;
For the ordering of these steps, which of the following options is correct?
Regarding Huawei's anti-virus technology, which of the following statements is wrong?
Cloud sandbox refers to deploying the sandbox in the cloud and providing remote detection services for tenants. The process includes:
1. Report suspicious files
2. Retrospective attack
3. Firewall linkage defense
4. Prosecution in the cloud sandbox
For the ordering of the process, which of the following options is correct?
Since the sandbox can provide a virtual execution environment to detect files in the network, the sandbox can be substituted when deploying security equipment
Anti-Virus, IPS, spam detection and other equipment.
For the description of the Anti DDOS system, which of the following options is correct? C
The application behavior control configuration file takes effect immediately after being referenced, without configuration submission.
Intrusion detection is a network security technology used to detect any damage or attempt to damage the confidentiality, integrity or availability of the system. Which of the following
What is the content of the intrusion detection knowledge base?
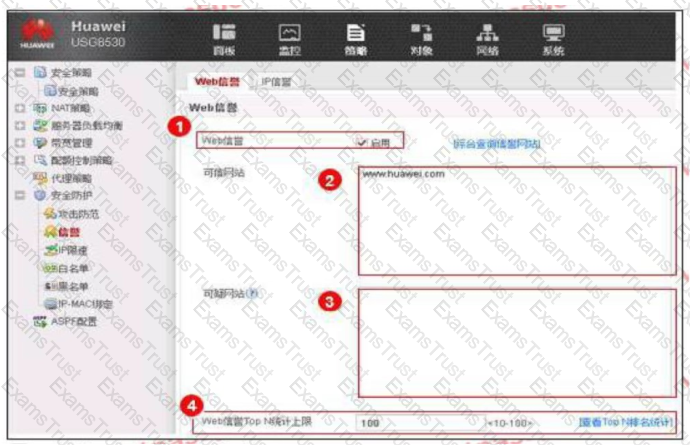
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
Which of the following options is not a special message attack?
Which of the following options is correct for the sequence of the flow-by-stream detection of AntiDDoS?
1. The Netflow analysis device samples the current network flow;
2. Send a drainage command to the cleaning center;
3. Discover the DDoS attack stream;
4.Netior: analysis equipment sends alarms to ATIC management center
5. The abnormal flow is diverted to the cleaning center for further inspection and cleaning;
6. The cleaning center sends the host route of the attacked target IF address server to the router to achieve drainage
7. The cleaning log is sent to the management center to generate a report;
8. The cleaned traffic is sent to the original destination server.
The whitelist rule of the firewall anti-virus module is configured as ("*example*, which of the following matching methods is used in this configuration?
Regarding the enhanced mode in HTTP Flood source authentication, which of the following descriptions are correct? Multiple choices
Which of the following statements about IPS is wrong?
The processing flow of IPS has the following steps;
1. Reorganize application data
2. Match the signature
3. Message processing
4. Protocol identification
Which of the following is the correct order of the processing flow?
Regarding intrusion detection I defense equipment, which of the following statements are correct? (multiple choice)