Is the correct statement about TCP proxy and TCP reverse source probing?
Which of the following methods is used to switch between active and standby links in the IPSec backup and backup system?
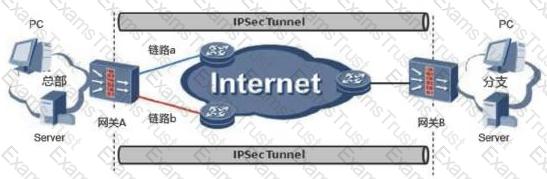
In the IPSec active/standby link backup application scenario, gateway B uses IPSec tunneling technology and gateway A to establish an IPSec VPN.
A user wants to limit the maximum bandwidth of the 192.168.1.0/24 network segment to 500M, and limit all IP addresses in the network segment to maintain a bandwidth of 1M. How should I configure a current limiting policy for this requirement?
Regarding the Radius authentication process, there are the following steps: 1. The Radius client (network access server) in the network device receives the username and password, and sends an authentication request to the Radius server; 2 the user logs in to the USG access server, etc. When the network device sends the username and password to the network access server; 3. After receiving the legitimate request, the Radius server completes the authentication and returns the required user authorization information to the client. What is the correct order?
Which of the following statements is true for virtual service technology?
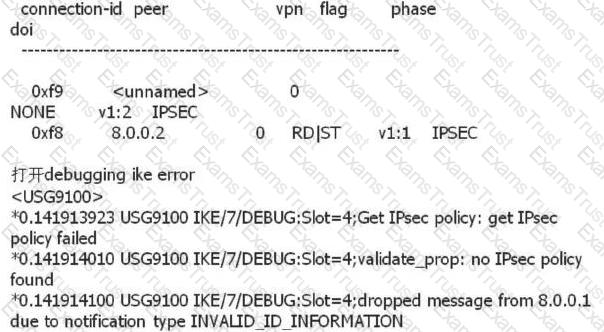
The IPSec establishment of a device is unsuccessful. The debug print information is as follows. What are the possible causes of the fault?
? %%01IKE/4/WARING(1):phase2:proposal mismatch,please check ipsec proposal configuration 0 34476900 %%01IKE/7/DEBUG(d) dropped message from 3.3.3.1 due to notification type NO_PROPOSAL_CHOSEN
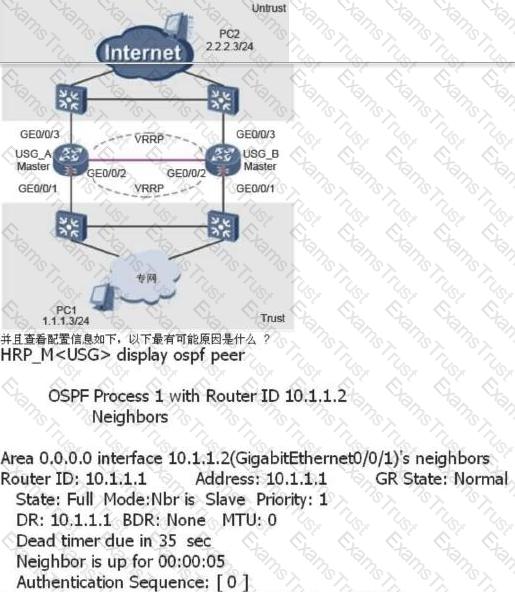
An administrator can view the IPSec status information and Debug information as follows. What is the most likely fault?
The dual-system hot backup load balancing service interface works at Layer 3, and the upstream and downstream routers are connected to each other. The two USG devices are active and standby. Therefore, both the hrp track master and the hrp track slave must be configured on the morning service interface.
In the IPSec VPN, the digital certificate is used for identity authentication. If the IKE main mode is used for negotiation, the certificate verification is completed in message 5 and message 6.
The following scan snoop attacks are:
Which of the following security services can a secure multi-instance provide for a virtual firewall?
The virtual firewall forwards multiple instances. The firewall has multiple routing tables and forwarding tables. The addresses are overlapped and are implemented on the same configuration interface. Users with configuration rights can configure and view all data.
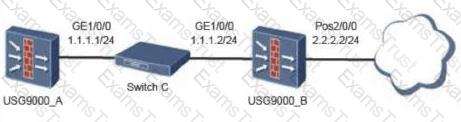
The topology of the BFD-bound static route is as follows: The administrator has configured the following on firewall A: [USG9000_A] bfd [USG9000_A-bfd] quit [USG9000_A] bfd aa bind peer-ip 1.1.1.2 [USG9000_A- Bfd session-aa] discriminator local 10 [USG9000_A-bfd session-aa] discriminator remote 20 Which of the following configurations can be added to the firewall to implement BFD-bound static routes?
A user dials to the LNS of the company through L2TP over IPSec using the VPN client, and the final dialup fails. However, the debug ike all and debug l2tp all did not see any information on the LNS. The two stages of establishing ike failed. What are the reasons for the failure?
Which of the following does the virtual firewall technical feature not include?
SSL VPN authentication is successful. Using the file sharing function, you can view directories and files, but you cannot upload, delete, and rename files. What are the possible reasons?
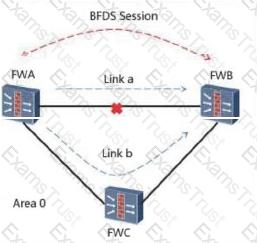
As shown in the following figure, the BFD for OSPF network is as follows: 1. OSPF is running between the three devices: FW_A, FW_B, and FW_C. The neighbors are in the FULL state. The association between BFD and OSPF is complete. BFD is complete. To establish a BFD session, the following instructions are correct?
A data flow has established a session in the firewall. If the packet filtering policy corresponding to the data is modified, how should the firewall execute?
What are the scenarios in which the USG series firewall service port sends gratuitous ARPs when the following configurations are performed?
What type of message is the VRRP hello message?
The administrator can create vfw1 and vfw2 on the root firewall to provide secure multi-instance services for enterprise A and enterprise B, and configure secure forwarding policies between security zones of vfw1 and vfw2.
In IPSec VPN, which one is incorrect about the difference between the barbaric mode and the main mode?
IP address scanning attack defense not only prevents ICMP packet detection target addresses, but also prevents TCP/UDP scanning detection target addresses.
When using manual IPSec negotiation, NAT traversal is also required if there is a NAT device on the network.
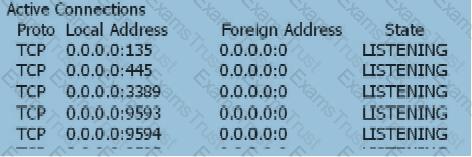
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
Avoid DHCP server spoofing attacks. DHCP snooping is usually enabled. What is the correct statement?
In the active/standby mode of the USG dual-system hot standby, the service interface works at Layer 3, and the upstream and downstream routers are connected to the router. The administrator can view: USG_A status is HRP_M[USG_A], USG_B status is HRP_S[USG_B], current 15000+ session Table, every time a switchover occurs, all traffic is interrupted for a period of time, and seamless switching is impossible.
Static fingerprint filtering function, different processing methods for different messages, the following statement is correct?
The preemption function of the VGMP management group is enabled by default, and the delay time is 60s.
In the case of IPSec VPN NAT traversal, you must use IKE's aggressive mode.
On the USG, you need to delete sslconfig.cfg in the hda1:/ directory. Which of the following commands can complete the operation?