Your company policies require you to encrypt logs between network infrastructure devices and Syslog servers. What should you do to meet these requirements on an ArubaOS-CX switch?
Specify the Syslog server with the TLS option and make sure the switch has a valid certificate.
Specify the Syslog server with the UDP option and then add an CPsec tunnel that selects Syslog.
Specify a priv key with the Syslog settings that matches a priv key on the Syslog server.
Set up RadSec and then enable Syslog as a protocol carried by the RadSec tunnel.
To ensure secure transmission of log data over the network, particularly when dealing with sensitive or critical information, using TLS (Transport Layer Security) for encrypted communication between network devices and syslog servers is necessary:
Secure Logging Setup: When configuring an ArubaOS-CX switch to send logs securely to a Syslog server, specifying the server with the TLS option ensures that all transmitted log data is encrypted. Additionally, the switch must have a valid certificate to establish a trusted connection, preventing potential eavesdropping or tampering with the logs in transit.
Other Options:
Option B, Option C, and Option D are less accurate or applicable for directly encrypting log data between the device and Syslog server as specified in the company policies.
Which endpoint classification capabilities do Aruba network infrastructure devices have on their own without ClearPass solutions?
ArubaOS-CX switches can use a combination of active and passive methods to assign roles to clients.
ArubaOS devices (controllers and lAPs) can use DHCP fingerprints to assign roles to clients.
ArubaOS devices can use a combination of DHCP fingerprints, HTTP User-Agent strings, and Nmap to construct endpoint profiles.
ArubaOS-Switches can use DHCP fingerprints to construct detailed endpoint profiles.
Without the integration of Aruba ClearPass or other advanced network access control solutions, ArubaOS devices (controllers and Instant APs) are able to use DHCP fingerprinting to assign roles to clients. This method allows the devices to identify the type of client devices connecting to the network based on the DHCP requests they send. While this is a more basic form of endpoint classification compared to the capabilities provided by ClearPass, it still enables some level of access control based on device type. This functionality and its limitations are described in Aruba's product documentation for ArubaOS devices, highlighting the benefits of integrating a full-featured solution like ClearPass for more granular and powerful endpoint classification capabilities.
Refer to the exhibit.
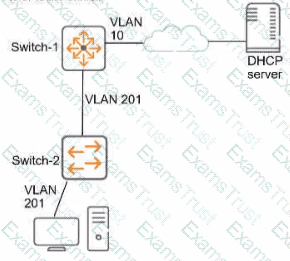
This company has ArubaOS-Switches. The exhibit shows one access layer switch, Swllcn-2. as an example, but the campus actually has more switches. The company wants to slop any internal users from exploiting ARP
What Is the proper way to configure the switches to meet these requirements?
On Switch-1, enable ARP protection globally, and enable ARP protection on ail VLANs.
On Switch-2, make ports connected to employee devices trusted ports for ARP protection
On Swltch-2, enable DHCP snooping globally and on VLAN 201 before enabling ARP protection
On Swltch-2, configure static PP-to-MAC bindings for all end-user devices on the network
To prevent users from exploiting Address Resolution Protocol (ARP) on a network with ArubaOS-Switches, the correct approach would be to enable DHCP snooping globally and on VLAN 201 before enabling ARP protection, as stated in option C. DHCP snooping acts as a foundation by tracking and securing the association of IP addresses to MAC addresses. This allows ARP protection to function effectively by ensuring that only valid ARP requests and responses are processed, thus preventing ARP spoofing attacks. Trusting ports that connect to employee devices directly could lead to bypassing ARP protection if those devices are compromised.
The company’s goal is to prevent internal users from exploiting ARP within their ArubaOS-Switch network. Let’s break down the options:
Option A (Incorrect): Enabling ARP protection globally on Switch-1 and all VLANs is not the best approach. ARP protection should be selectively applied where needed, not globally. It’s also not clear why Switch-1 is mentioned when the exhibit focuses on Switch-2.
Option B (Incorrect): Making ports connected to employee devices trusted for ARP protection is a good practice, but it’s not sufficient by itself. Trusted ports allow ARP traffic, but we need an additional layer of security.
Option C (Correct): This is the recommended approach. Here’s why:
DHCP Snooping: First, enable DHCP snooping globally. DHCP snooping helps validate DHCP messages and builds an IP-MAC binding table. This table is crucial for ARP protection to function effectively.
VLAN 201: Enable DHCP snooping specifically on VLAN 201 (as shown in the exhibit). This ensures that DHCP messages within this VLAN are validated.
ARP Protection: Once DHCP snooping is in place, enable ARP protection. ARP requests/replies from untrusted ports with invalid IP-to-MAC bindings will be dropped. This prevents internal users from exploiting ARP for attacks like man-in-the-middle.
Option D (Incorrect): While static ARP bindings can enhance security, they are cumbersome to manage and don’t dynamically adapt to changes in the network.
A company is deploying ArubaOS-CX switches to support 135 employees, which will tunnel client traffic to an Aruba Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the ArubaOS-CX switches.
What are the licensing requirements for the MC?
one AP license per-switch
one PEF license per-switch
one PEF license per-switch. and one WCC license per-switch
one AP license per-switch. and one PEF license per-switch
When deploying ArubaOS-CX switches that tunnel client traffic to an Aruba Mobility Controller (MC), the licensing requirements typically involve Policy Enforcement Firewall (PEF) licenses. These licenses enable the MC to enforce firewall policies and perform deep packet inspection (DPI). Therefore, for each switch tunneling traffic to the MC, a PEF license would be necessary.
The monitoring admin has asked you to set up an AOS-CX switch to meet these criteria:
Send logs to a SIEM Syslog server at 10.4.13.15 at the standard TCP port (514)
Send a log for all events at the "warning" level or above; do not send logs with a lower level than "warning"The switch did not have any "logging" configuration on it. You then entered this command:AOS-CX(config)# logging 10.4.13.15 tcp vrf defaultWhat should you do to finish configuring to the requirements?
Specify the "warning" severity level for the logging server.
Add logging categories at the global level.
Ask for the Syslog password and configure it on the switch.
Configure logging as a debug destination.
The task is to configure an AOS-CX switch to send logs to a SIEM Syslog server at IP address 10.4.13.15 using TCP port 514, with logs for events at the "warning" severity level or above (i.e., warning, error, critical, alert, emergency). The initial command entered is:
AOS-CX(config)# logging 10.4.13.15 tcp vrf default
This command configures the switch to send logs to the Syslog server at 10.4.13.15 using TCP (port 514 is the default for TCP Syslog unless specified otherwise) and the default VRF. However, this command alone does not specify the severity level of the logs to be sent, which is a requirement of the task.
Severity Level Configuration: AOS-CX switches allow you to specify the severity level for logs sent to a Syslog server. The severity levels, in increasing order of severity, are: debug, informational, notice, warning, error, critical, alert, and emergency. The requirement is to send logs at the "warning" level or above, meaning warning, error, critical, alert, and emergency logs should be sent, but debug, informational, and notice logs should not.
Option A, "Specify the ‘warning’ severity level for the logging server," is correct. To meet the requirement, you need to add the severity level to the logging configuration for the specific Syslog server. The command to do this is:
AOS-CX(config)# logging 10.4.13.15 severity warning
This command ensures that only logs with a severity of warning or higher are sent to the Syslog server at 10.4.13.15. Since the initial command already specified TCP and the default VRF, this additional command completes the configuration.
Option B, "Add logging categories at the global level," is incorrect. Logging categories (e.g., system, security, network) are used to filter logs based on the type of event, not the severity level. The requirement is about severity ("warning" or above), not specific categories, so this step is not necessary to meet the stated criteria.
Option C, "Ask for the Syslog password and configure it on the switch," is incorrect. Syslog servers typically do not require a password for receiving logs, and AOS-CX switches do not have a configuration option to specify a Syslog password. Authentication or encryption for Syslog (e.g., using TLS) is not mentioned in the requirements.
Option D, "Configure logging as a debug destination," is incorrect. Configuring a debug destination (e.g., using the debug command) is used to send debug-level logs to a destination (e.g., console, buffer, or Syslog), but the requirement is to send logs at the "warning" level or above, not debug-level logs. Additionally, the logging command already specifies the Syslog server as the destination.
The HPE Aruba Networking AOS-CX 10.12 System Management Guide states:
"To configure a Syslog server on an AOS-CX switch, use the logging
Additionally, the guide notes:
"Severity levels for logging on AOS-CX switches are, in increasing order: debug, informational, notice, warning, error, critical, alert, emergency. Specifying a severity level of ‘warning’ ensures that only logs at that level or higher are sent to the configured destination." (Page 90, Logging Severity Levels Section)
What is one difference between EAP-Tunneled Layer Security (EAP-TLS) and Protected EAP (PEAP)?
EAP-TLS begins with the establishment of a TLS tunnel, but PEAP does not use a TLS tunnel as part of its process.
EAP-TLS requires the supplicant to authenticate with a certificate, but PEAP allows the supplicant to use a username and password.
EAP-TLS creates a TLS tunnel for transmitting user credentials, while PEAP authenticates the server and supplicant during a TLS handshake.
EAP-TLS creates a TLS tunnel for transmitting user credentials securely, while PEAP protects user credentials with TKIP encryption.
EAP-TLS (Extensible Authentication Protocol - Transport Layer Security) and PEAP (Protected EAP) are two EAP methods used for 802.1X authentication in wireless networks, such as those configured with WPA3-Enterprise on HPE Aruba Networking solutions. Both methods are commonly used with ClearPass Policy Manager (CPPM) for secure authentication.
EAP-TLS:
Requires both the supplicant (client) and the server (e.g., CPPM) to present a valid certificate during authentication.
Establishes a TLS tunnel to secure the authentication process, but the primary authentication mechanism is the mutual certificate exchange. The client’s certificate is used to authenticate the client, and the server’s certificate authenticates the server.
PEAP:
Requires only the server to present a certificate to authenticate itself to the client.
Establishes a TLS tunnel to secure the authentication process, within which the client authenticates using a secondary method, typically a username and password (e.g., via MS-CHAPv2 or EAP-GTC).
Option A, "EAP-TLS begins with the establishment of a TLS tunnel, but PEAP does not use a TLS tunnel as part of its process," is incorrect. Both EAP-TLS and PEAP establish a TLS tunnel. In EAP-TLS, the TLS tunnel is used for the mutual certificate exchange, while in PEAP, the TLS tunnel protects the inner authentication (e.g., username/password).
Option B, "EAP-TLS requires the supplicant to authenticate with a certificate, but PEAP allows the supplicant to use a username and password," is correct. This is a key difference: EAP-TLS mandates certificate-based authentication for the client, while PEAP allows the client to authenticate with a username and password inside the TLS tunnel, making PEAP more flexible for environments where client certificates are not deployed.
Option C, "EAP-TLS creates a TLS tunnel for transmitting user credentials, while PEAP authenticates the server and supplicant during a TLS handshake," is incorrect. Both methods use a TLS tunnel, and both authenticate the server during the TLS handshake (using the server’s certificate). In EAP-TLS, the client’s certificate is also part of the TLS handshake, while in PEAP, the client’s credentials (username/password) are sent inside the tunnel after the handshake.
Option D, "EAP-TLS creates a TLS tunnel for transmitting user credentials securely, while PEAP protects user credentials with TKIP encryption," is incorrect. PEAP does not use TKIP (Temporal Key Integrity Protocol) for protecting credentials; TKIP is a legacy encryption method used in WPA/WPA2 for wireless data encryption, not for EAP authentication. PEAP uses the TLS tunnel to protect the inner authentication credentials.
The HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide states:
"EAP-TLS requires both the supplicant and the server to present a valid certificate for mutual authentication. The supplicant authenticates using its certificate, and the process is secured within a TLS tunnel. In contrast, PEAP requires only the server to present a certificate to establish a TLS tunnel, within which the supplicant can authenticate using a username and password (e.g., via MS-CHAPv2 or EAP-GTC). This makes PEAP more suitable for environments where client certificates are not deployed." (Page 292, EAP Methods Section)
Additionally, the HPE Aruba Networking Wireless Security Guide notes:
"A key difference between EAP-TLS and PEAP is the client authentication method. EAP-TLS mandates that the client authenticate with a certificate, requiring certificate deployment on all clients. PEAP allows the client to authenticate with a username and password inside a TLS tunnel, making it easier to deploy in environments without client certificates." (Page 40, 802.1X Authentication Methods Section)
What is a reason to set up a packet capture on an Aruba Mobility Controller (MC)?
The company wants to use ClearPass Policy Manager (CPPM) to profile devices and needs to receive HTTP User-Agent strings from the MC.
The security team believes that a wireless endpoint connected to the MC is launching an attack and wants to examine the traffic more closely.
You want the MC to analyze wireless clients' traffic at a lower level, so that the ArubaOS firewall can control the traffic I based on application.
You want the MC to analyze wireless clients' traffic at a lower level, so that the ArubaOS firewall can control Web traffic based on the destination URL.
Setting up a packet capture on an Aruba Mobility Controller (MC) is particularly useful in scenarios where detailed analysis of network traffic is necessary to identify and address security concerns. Option B is the correct answer because it directly addresses the need to closely examine the traffic of a potentially malicious wireless endpoint. Packet capture on the MC allows the security team to collect and analyze traffic to/from specific endpoints in real-time, providing valuable insights into the nature of the traffic and potentially identifying harmful activities. This capability is essential for forensics and troubleshooting security incidents, enabling administrators to respond effectively to threats.
What is one benefit of a Trusted Platform Module (TPM) on an Aruba AP?
It enables secure boot, which detects if hackers corrupt the OS with malware.
It deploys the AP with enhanced security, which includes disabling the password recovery mechanism.
It allows the AP to run in secure mode, which automatically enables CPsec and disables the console port.
It enables the AP to encrypt and decrypt 802.11 traffic locally, rather than at the MC.
The TPM (Trusted Platform Module) is a hardware-based security feature that can provide various security functions, one of which includes secure boot. Secure boot is a process where the TPM ensures that the device boots using only software that is trusted by the manufacturer. If the OS has been tampered with or infected with malware, the secure boot process can detect this and prevent the system from loading the compromised OS.
What is a use case for Transport Layer Security (TLS)?
to establish a framework for devices to determine when to trust other devices' certificates
to enable a client and a server to establish secure communications for another protocol
to enable two parties to asymmetrically encrypt and authenticate all data that passes be-tween them
to provide a secure alternative to certificate authentication that is easier to implement
The use case for Transport Layer Security (TLS) is to enable a client and a server to establish secure communications for another protocol. TLS is a cryptographic protocol designed to provide secure communication over a computer network. It is widely used for web browsers and other applications that require data to be securely exchanged over a network, such as file transfers, VPN connections, and voice-over-IP (VoIP). TLS operates between the transport layer and the application layer of the Internet Protocol Suite and is used to secure various other protocols like HTTP (resulting in HTTPS), SMTP, IMAP, and more. This protocol ensures privacy and data integrity between two communicating applications. Detailed information about TLS and its use cases can be found in IETF RFC 5246, which outlines the specifications for TLS 1.2, and in subsequent RFCs that define TLS 1.3.
What is a consideration for using MAC authentication (MAC-Auth) to secure a wired or wireless connection?
As a Layer 2 authentication method, MAC-Auth cannot be used to authenticate devices to an external authentication server.
It is very easy for hackers to spoof their MAC addresses and get around MAC authentication.
MAC-Auth can add a degree of security to an open WLAN by enabling the generation of a PMK to encrypt traffic.
Headless devices, such as Internet of Things (loT) devices, must be configured in advance to support MAC-Auth.
MAC authentication, also known as MAC-Auth, is a method used to authenticate devices based on their Media Access Control (MAC) address. It is often employed in both wired and wireless networks to grant network access based solely on the MAC address of a device. While MAC-Auth is straightforward and doesn’t require complex configuration, it has significant security limitations primarily because MAC addresses can be easily spoofed. Attackers can change the MAC address of their device to match an authorized one, thereby gaining unauthorized access to the network. This susceptibility to MAC address spoofing makes MAC-Auth a weaker security mechanism compared to more robust authentication methods like 802.1X, which involves mutual authentication and encryption protocols.
What is a correct guideline for the management protocols that you should use on AOS-CX switches?
Make sure that SSH is disabled and use HTTPS instead.
Make sure that Telnet is disabled and use SSH instead.
Make sure that Telnet is disabled and use TFTP instead.
Make sure that HTTPS is disabled and use SSH instead.
AOS-CX switches support various management protocols for administrative access, such as SSH, Telnet, HTTPS, and TFTP. Security best practices for managing network devices, including AOS-CX switches, emphasize using secure protocols to protect management traffic from eavesdropping and unauthorized access.
Option B, "Make sure that Telnet is disabled and use SSH instead," is correct. Telnet is an insecure protocol because it sends all data, including credentials, in plaintext, making it vulnerable to eavesdropping. SSH (Secure Shell) provides encrypted communication for remote management, ensuring that credentials and commands are protected. HPE Aruba Networking recommends disabling Telnet and enabling SSH for secure management access on AOS-CX switches.
Option A, "Make sure that SSH is disabled and use HTTPS instead," is incorrect. SSH and HTTPS serve different purposes: SSH is for CLI access, while HTTPS is for web-based management. Disabling SSH would prevent secure CLI access, which is not a recommended practice. Both SSH and HTTPS should be enabled for secure management.
Option C, "Make sure that Telnet is disabled and use TFTP instead," is incorrect. TFTP (Trivial File Transfer Protocol) is used for file transfers (e.g., firmware updates), not for management access like Telnet or SSH. TFTP is also insecure (no encryption), so it’s not a suitable replacement for Telnet.
Option D, "Make sure that HTTPS is disabled and use SSH instead," is incorrect. HTTPS is used for secure web-based management and should not be disabled. Both HTTPS and SSH are secure protocols and should be used together for different management interfaces (web and CLI, respectively).
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"For secure management of AOS-CX switches, disable insecure protocols like Telnet, which sends data in plaintext, and use SSH instead. SSH provides encrypted communication for CLI access, protecting credentials and commands from eavesdropping. Use the command no telnet-server to disable Telnet and ssh-server to enable SSH. Additionally, enable HTTPS for web-based management with https-server to ensure all management traffic is encrypted." (Page 195, Secure Management Protocols Section)
Additionally, the HPE Aruba Networking Security Best Practices Guide notes:
"A key guideline for managing AOS-CX switches is to disable Telnet and enable SSH for CLI access. Telnet is insecure and should not be used in production environments, as it transmits credentials in plaintext. SSH ensures secure remote management, and HTTPS should also be enabled for web access." (Page 25, Management Security Section)
Refer to the exhibits.
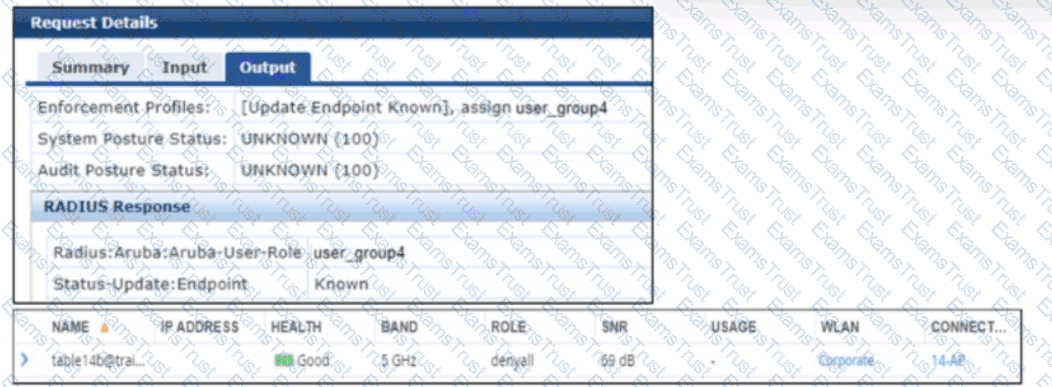
A company has added a new user group. Users in the group try to connect to the WLAN and receive errors that the connection has no Internet access. The users cannot reach any resources. The first exhibit shows the record for one of the users who cannot connect. The second exhibit shows the role to which the AOS device assigned the user’s client.
What is a likely problem?
The AOS device does not have the correct RADIUS dictionaries installed on it to understand the Aruba-User-Role VSA.
The AOS device has a server derivation rule configured on it that has overridden the role sent by CPPM.
The clients rejected the server authentication on their side because they do not have the root CA for CPPM’s RADIUS/EAP certificate.
The role name that CPPM is sending does not match the role name configured on the AOS device.
The scenario involves an AOS-8 Mobility Controller (MC) with a WLAN where a new user group has been added. Users in this group cannot connect to the WLAN, receiving errors indicating no Internet access and inability to reach resources. Exhibit 1 shows the ClearPass Policy Manager (CPPM) Access Tracker record for one user:
CPPM sends an Access-Accept with the VSA Radius:Aruba:Aruba-User-Role user_group4.
The endpoint is classified as "Known," but the user cannot access resources. Exhibit 2 (not provided but described) shows that the AOS device (MC) assigned the user’s client to the "denyall" role, which likely denies all access, explaining the lack of Internet and resource access.
Analysis:
CPPM sends the Aruba-User-Role VSA with the value "user_group4," indicating that the user should be assigned to the "user_group4" role on the MC.
However, the MC assigns the client to the "denyall" role, which typically denies all traffic, resulting in no Internet or resource access.
The issue lies in why the MC did not apply the "user_group4" role sent by CPPM.
Option A, "The AOS device does not have the correct RADIUS dictionaries installed on it to understand the Aruba-User-Role VSA," is incorrect. If the MC did not have the correct RADIUS dictionaries to understand the Aruba-User-Role VSA, it would not process the VSA at all, and the issue would likely affect all users, not just the new user group. Additionally, Aruba-User-Role is a standard VSA in AOS-8, and the dictionaries are built into the system.
Option B, "The AOS device has a server derivation rule configured on it that has overridden the role sent by CPPM," is incorrect. Server derivation rules on the MC can override roles sent by the RADIUS server (e.g., based on attributes like username or NAS-IP), but there is no indication in the scenario that such a rule is configured. If a derivation rule were overriding the role, it would likely affect more users, and the issue would not be specific to the new user group.
Option C, "The clients rejected the server authentication on their side because they do not have the root CA for CPPM’s RADIUS/EAP certificate," is incorrect. If the clients rejected the server authentication (e.g., due to a missing root CA for CPPM’s certificate), the authentication would fail entirely, and CPPM would not send an Access-Accept with the Aruba-User-Role VSA. The scenario confirms that authentication succeeded (Access-Accept was sent), so this is not the issue.
Option D, "The role name that CPPM is sending does not match the role name configured on the AOS device," is correct. CPPM sends the role "user_group4" in the Aruba-User-Role VSA, but the MC assigns the client to the "denyall" role. This suggests that the role "user_group4" does not exist on the MC, or there is a mismatch in the role name (e.g., due to case sensitivity, typos, or underscores vs. hyphens). In AOS-8, if the role specified in the Aruba-User-Role VSA does not exist on the MC, the MC falls back to a default role, which in this case appears to be "denyall," denying all access. The likely problem is that the role name "user_group4" sent by CPPM does not match the role name configured on the MC (e.g., it might be "user-group4" or a different name).
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When the Mobility Controller receives an Aruba-User-Role VSA in a RADIUS Access-Accept message, it attempts to assign the specified role to the client. If the role name sent by the RADIUS server (e.g., ‘user_group4’) does not match a role configured on the controller, the controller will fall back to a default role, such as ‘denyall,’ which may deny all access. To resolve this, ensure that the role name sent by the RADIUS server matches the role name configured on the controller, accounting for case sensitivity and naming conventions (e.g., underscores vs. hyphens)." (Page 306, Role Assignment Troubleshooting Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"A common issue when assigning roles via the Aruba-User-Role VSA is a mismatch between the role name sent by ClearPass and the role name configured on the Aruba device. If the role name does not match (e.g., ‘user_group4’ vs. ‘user-group4’), the device will not apply the intended role, and the client may be assigned a default role like ‘denyall,’ resulting in access issues. Verify that the role names match exactly in both ClearPass and the device configuration." (Page 290, RADIUS Role Assignment Issues Section)
What is a Key feature of me ArubaOS firewall?
The firewall is stateful which means that n can track client sessions and automatically allow return traffic for permitted sessions
The firewall Includes application layer gateways (ALGs). which it uses to filter Web traffic based on the reputation of the destination web site.
The firewall examines all traffic at Layer 2 through Layer 4 and uses source IP addresses as the primary way to determine how to control traffic.
The firewall is designed to fitter traffic primarily based on wireless 802.11 headers, making it ideal for mobility environments
The ArubaOS firewall is a stateful firewall, meaning that it can track the state of active sessions and can make decisions based on the context of the traffic. This stateful inspection capability allows it to automatically allow return traffic for sessions that it has permitted, thereby enabling seamless two-way communication for authorized users while maintaining the security posture of the network.
Refer to the exhibit.
How can you use the thumbprint?
Install this thumbprint on management stations to use as two-factor authentication along with manager usernames and passwords, this will ensure managers connect from valid stations
Copy the thumbprint to other Aruba switches to establish a consistent SSH Key for all switches this will enable managers to connect to the switches securely with less effort
When you first connect to the switch with SSH from a management station, make sure that the thumbprint matches to ensure that a man-in-t he-mid die (MITM) attack is not occurring
install this thumbprint on management stations the stations can then authenticate with the thumbprint instead of admins having to enter usernames and passwords.
The thumbprint (also known as a fingerprint) of a certificate or SSH key is a hash that uniquely represents the public key contained within. When you first connect to the switch with SSH from a management station, you should ensure that the thumbprint matches what you expect. This is a security measure to confirm the identity of the device you are connecting to and to ensure that a man-in-the-middle (MITM) attack is not occurring. If the thumbprint matches the known good thumbprint of the switch, it is safe to proceed with the connection.
You are setting up an Aruba mobility solution which includes a Mobility Master (MM), Mobility Controllers (MCs), and campus APs (CAPs) for a university. The university plans to enforce WPA2-Enterprise for all users' connections. The university wants to apply one set of access control rules to faculty users' traffic and a different set of rules to students' traffic.
What is the best approach for applying the correct rules to each group?
Create two VLANs, one for faculty and one for students. Create one set of firewall access control rules that specify faculty IP addresses for the source and a second set of rules that specify the student IP addresses for the source. Apply the rules to the WLAN.
Create two roles, a "faculty" role and a "student" role. Apply firewall policies with the correct rules for each group to each role.
Create two WLANs, one for faculty and one for students. Apply firewall policies with the correct rules for each group to each WLAN.
Create two VLANs, one for faculty and one for students. Apply firewall policies with the correct rules for each group to each VLAN.
To differentiate access control for faculty and students, the best approach is to use roles. By creating two roles - "faculty" and "student" - and applying the appropriate firewall policies to each, the university can enforce different access rules for each group. This is more efficient than managing multiple VLANs or WLANs because it allows for role-based access control, which is directly tied to user identity rather than just IP addresses or the network they are connected to.QUESTION NO: 105
The monitoring admin has asked you to set up an ArubaOS-Switch to meet these criteria:
• Send logs to a SIEM Syslog server at 10.4.13.15 at the standard UDP port (514)
• Send a log for all events at the "warning" level or above
The switch did not have any "logging" configuration on it. You then entered this command:
ArubaOS-Switch(config)# logging 10.4.13.15 udp
What should you do to finish configuring to the requirements?
A. Add categories (system-modules) at the global level.
B. Specify "warning" as the global level.
C. Ask for the Syslog password and configure it on the switch.
D. Configure logging as a debug destination.
Answer: B
To set up an ArubaOS-Switch to send logs to a SIEM syslog server at the specified criteria, you would need to specify the level of events that should be logged. Since the requirement is to log all events at the "warning" level or above, you should specify the syslog level after the logging server IP and port. The command should look like this:
ArubaOS-Switch(config)# logging 10.4.13.15 ArubaOS-Switch(config)# logging trap warning
This would set up the switch to send logs to the syslog server at the IP address 10.4.13.15 using the default UDP port (514), for all events at the "warning" level or above.
Refer to the exhibit.

A diem is connected to an ArubaOS Mobility Controller. The exhibit snows all Tour firewall rules that apply to this diem
What correctly describes how the controller treats HTTPS packets to these two IP addresses, both of which are on the other side of the firewall
10.1 10.10
203.0.13.5
It drops both of the packets
It permits the packet to 10.1.10.10 and drops the packet to 203 0.13.5
it permits both of the packets
It drops the packet to 10.1.10.10 and permits the packet to 203.0.13.5.
Referring to the exhibit, the ArubaOS Mobility Controller treats HTTPS packets based on the firewall rules applied to the client. The rule that allows svc-https service for destination IP range 10.1.0.0 255.255.0.0 would permit an HTTPS packet to 10.1.10.10 since this IP address falls within the specified range. There are no rules shown that would allow traffic to the IP address 203.0.13.5; hence, the packet to this address would be dropped.
The first exhibit shows roles on the MC, listed in alphabetic order. The second and third exhibits show the configuration for a WLAN to which a client connects. Which description of the role assigned to a user under various circumstances is correct?
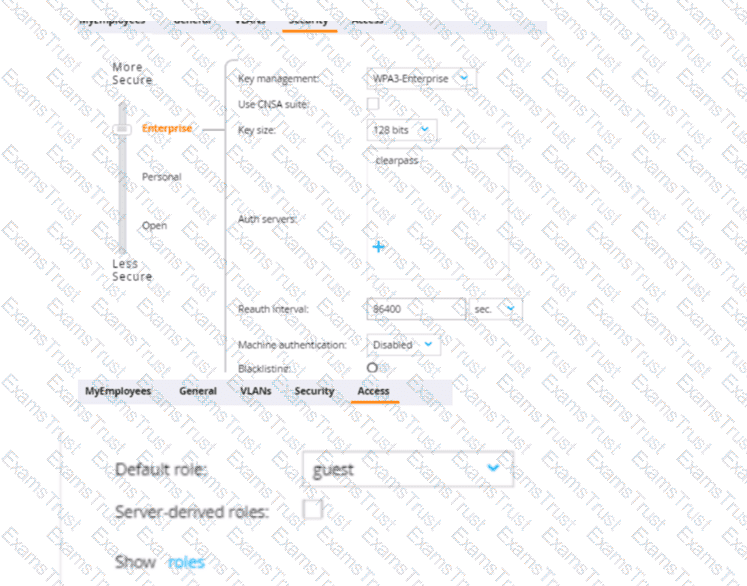
A user fails 802.1X authentication. The client remains connected, but is assigned the "guest" role.
A user authenticates successfully with 802.1 X. and the RADIUS Access-Accept includes an Aruba-User-Role VSA set to "employeel.” The client’s role is "guest."
A user authenticates successfully with 802.1X. and the RADIUS Access-Accept includes an Aruba-User-Role VSA set to "employee." The client’s role is "guest."
A user authenticates successfully with 802.1X, and the RADIUS Access-Accept includes an Aruba-User-RoleVSA set to "employeel." The client's role is "employeel."
In a WLAN setup that uses 802.1X for authentication, the role assigned to a user is determined by the result of the authentication process. When a user successfully authenticates via 802.1X, the RADIUS server may include a Vendor-Specific Attribute (VSA), such as the Aruba-User-Role, in the Access-Accept message. This attribute specifies the role that should be assigned to the user. If the RADIUS Access-Accept message includes an Aruba-User-Role VSA set to "employee1", the client should be assigned the "employee1" role, as per the VSA, and not the default "guest" role. The "guest" role would typically be a fallback if no other role is specified or if the authentication fails.
What is a guideline for managing local certificates on AOS-CX switches?
Understand that the switch must use the same certificate for all usages, such as its HTTPS server and RadSec client.
Create a self-signed certificate online on the switch because AOS-CX switches do not support CA-signed certificates.
Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install.
Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificates.
AOS-CX switches use certificates for various purposes, such as securing HTTPS access to the switch’s web interface, authenticating the switch as a RadSec client, or securing other communications. Managing local certificates on AOS-CX switches involves ensuring that the switch trusts the certificate authority (CA) that issued the certificate, which is critical for proper operation.
Option C, "Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install," is correct. A trust anchor (TA) profile on AOS-CX switches contains the root CA certificate (or intermediate CA certificate) that issued the local certificate. This TA profile allows the switch to validate the certificate chain when the local certificate is installed. For example, if you install a CA-signed certificate for the HTTPS server, the switch needs the root CA certificate in a TA profile to trust the certificate. This is a standard guideline for certificate management on AOS-CX switches to ensure secure and proper operation.
Option A, "Understand that the switch must use the same certificate for all usages, such as its HTTPS server and RadSec client," is incorrect. AOS-CX switches support using different certificates for different purposes. For example, you can have one certificate for the HTTPS server and another for RadSec client authentication, as long as each certificate is associated with the appropriate service and trusted by the switch.
Option B, "Create a self-signed certificate online on the switch because AOS-CX switches do not support CA-signed certificates," is incorrect. AOS-CX switches fully support CA-signed certificates, and using CA-signed certificates is recommended for production environments to ensure trust and security. Self-signed certificates can be used for testing but are not a guideline for general certificate management.
Option D, "Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificates," is incorrect. OCSP is a protocol used to check the revocation status of certificates, not to simplify certificate enrollment. AOS-CX switches support OCSP for certificate validation, but installing an "OCSP certificate" is not a concept in certificate management, and it’s not a guideline for managing local certificates.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"Before installing a CA-signed local certificate on the switch, you must create a trust anchor (TA) profile that includes the root CA certificate (or intermediate CA certificate) that issued the local certificate. This ensures that the switch can validate the certificate chain. For example, to install a CA-signed certificate for the HTTPS server, use the command crypto pki ta-profile
Additionally, the guide notes:
"AOS-CX switches support both self-signed and CA-signed certificates. For production environments, it is recommended to use CA-signed certificates and ensure that the appropriate trust anchor profiles are configured to validate the certificate chain." (Page 202, Best Practices Section)
Which attack is an example or social engineering?
An email Is used to impersonate a Dank and trick users into entering their bank login information on a fake website page.
A hacker eavesdrops on insecure communications, such as Remote Desktop Program (RDP). and discovers login credentials.
A user visits a website and downloads a file that contains a worm, which sell-replicates throughout the network.
An attack exploits an operating system vulnerability and locks out users until they pay the ransom.
An example of a social engineering attack is described in option A, where an email is used to impersonate a bank and deceive users into entering their bank login information on a counterfeit website. Social engineering attacks exploit human psychology rather than technical hacking techniques to gain access to systems, data, or personal information. These attacks often involve tricking people into breaking normal security procedures. The other options describe different types of technical attacks that do not primarily rely on manipulating individuals through deceptive personal interactions.
What is a use case for implementing RadSec instead of RADIUS?
A university wants to protect communications between the students' devices and the network access server.
A corporation wants to implement EAP-TLS to authenticate wireless users at their main office.
A school district wants to protect messages sent between RADIUS clients and servers over an untrusted network.
A organization wants to strengthen the encryption used to protect RADIUS communications without increasing complexity.
RadSec (RADIUS over TLS) is a protocol for transporting RADIUS messages over TLS-encrypted TCP/IP networks. The primary use case for implementing RadSec instead of traditional RADIUS is to protect RADIUS communications, particularly when those messages must travel across an untrusted network, such as the internet. RadSec provides confidentiality, integrity, and authentication for RADIUS traffic between clients and servers which may not be within a single secure network. In the case of a school district that wants to ensure the security of messages sent between RADIUS clients and servers over potentially insecure networks, RadSec would be the appropriate choice.
You are deploying a new wireless solution with an HPE Aruba Networking Mobility Master (MM), Mobility Controllers (MCs), and campus APs (CAPs). The solution will include a WLAN that uses Tunnel for the forwarding mode and WPA3-Enterprise for the security option.
You have decided to assign the WLAN to VLAN 301, a new VLAN. A pair of core routing switches will act as the default router for wireless user traffic.
Which links need to carry VLAN 301?
Only links on the path between APs and the core routing switches
Only links on the path between APs and the MC
All links in the campus LAN to ensure seamless roaming
Only links between MC ports and the core routing switches
In an HPE Aruba Networking AOS-8 architecture with a Mobility Master (MM), Mobility Controllers (MCs), and campus APs (CAPs), the WLAN is configured to use Tunnel forwarding mode and WPA3-Enterprise security. In Tunnel mode, all user traffic from the APs is encapsulated in a GRE tunnel and sent to the MC, which then forwards the traffic to the appropriate VLAN. The WLAN is assigned to VLAN 301, and the core routing switches act as the default router for wireless user traffic.
Tunnel Forwarding Mode: In this mode, the AP does not directly place user traffic onto the wired network. Instead, the AP tunnels all user traffic to the MC over a GRE tunnel. The MC then decapsulates the traffic and places it onto the wired network in the specified VLAN (VLAN 301 in this case). This means the VLAN tagging for user traffic occurs at the MC, not at the AP.
VLAN 301 Assignment: Since the WLAN is assigned to VLAN 301, the MC will tag user traffic with VLAN 301 when forwarding it to the wired network. The core routing switches, acting as the default router, need to receive this traffic on VLAN 301 to route it appropriately.
Therefore, VLAN 301 needs to be carried on the links between the MC ports and the core routing switches, as this is where the MC forwards the user traffic after decapsulating it from the GRE tunnel.
Option A, "Only links on the path between APs and the core routing switches," is incorrect because, in Tunnel mode, the APs do not directly forward user traffic to the wired network. The traffic is tunneled to the MC, so the links between the APs and the core switches do not need to carry VLAN 301 for user traffic (though they may carry other VLANs for AP management).
Option B, "Only links on the path between APs and the MC," is incorrect for the same reason. The GRE tunnel between the AP and MC carries encapsulated user traffic, and VLAN 301 tagging occurs at the MC, not on the AP-to-MC link.
Option C, "All links in the campus LAN to ensure seamless roaming," is incorrect because VLAN 301 only needs to be present where the MC forwards user traffic to the wired network (i.e., between the MC and the core switches). Extending VLAN 301 to all links is unnecessary and could introduce security or scalability issues.
Option D, "Only links between MC ports and the core routing switches," is correct because the MC places user traffic onto VLAN 301 and forwards it to the core switches, which act as the default router.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"In Tunnel forwarding mode, the AP encapsulates all user traffic in a GRE tunnel and sends it to the Mobility Controller (MC). The MC decapsulates the traffic and forwards it to the wired network on the VLAN assigned to the WLAN. For example, if the WLAN is assigned to VLAN 301, the MC tags the user traffic with VLAN 301 and sends it out of its wired interface to the upstream switch. Therefore, the VLAN must be configured on the links between the MC and the upstream switch or router that acts as the default gateway for the VLAN." (Page 275, Tunnel Forwarding Mode Section)
Additionally, the HPE Aruba Networking Wireless LAN Design Guide notes:
"When using Tunnel mode, the VLAN assigned to the WLAN must be carried on the wired links between the Mobility Controller and the default router for the VLAN. The links between the APs and the MC do not need to carry the user VLAN, as all traffic is tunneled to the MC, which handles VLAN tagging." (Page 52, VLAN Configuration Section)
You have an AOS-8 architecture, consisting of a Mobility Conductor (MC) and Mobility Controllers (MCs). You want to monitor wireless clients’ application usage in the Traffic Analysis dashboard. What is a requirement?
Configuring packet capturing on the MCs’ data plane
Enabling logging on the users category on the MCs
Discovering the mobility devices in HPE Aruba Networking Central
Enabling firewall visibility and deep packet inspection (DPI) on the MCs
In an AOS-8 architecture with a Mobility Conductor (MC) and Mobility Controllers (MCs), the Traffic Analysis dashboard (available in the MC UI) allows administrators to monitor wireless clients’ application usage (e.g., identifying traffic from applications like Zoom, YouTube, or Skype). To enable this functionality, the MCs must be able to inspect and classify client traffic at the application level.
Firewall Visibility and DPI: The AOS-8 platform includes a stateful firewall that can perform deep packet inspection (DPI) to classify traffic based on application signatures. Enabling "firewall visibility" on the MCs activates DPI, allowing the firewall to inspect packet payloads and identify applications. This data is then used by the Traffic Analysis dashboard to display application usage statistics for wireless clients.
Option D, "Enabling firewall visibility and deep packet inspection (DPI) on the MCs," is correct. Firewall visibility must be enabled on the MCs to perform DPI and classify client traffic by application. This is typically done with the command firewall visibility in the MC configuration, which activates DPI and allows the Traffic Analysis dashboard to display application usage data.
Option A, "Configuring packet capturing on the MCs’ data plane," is incorrect. Packet capturing (e.g., using the packet-capture command) is used for manual troubleshooting or analysis, not for enabling the Traffic Analysis dashboard. Packet captures generate raw packet data, which is not processed for application usage statistics.
Option B, "Enabling logging on the users category on the MCs," is incorrect. Enabling logging for the "users" category (e.g., using the logging command) generates logs for user events (e.g., authentication, role assignment), but it does not provide application usage data for the Traffic Analysis dashboard.
Option C, "Discovering the mobility devices in HPE Aruba Networking Central," is incorrect. While discovering devices in Aruba Central can provide centralized monitoring, the Traffic Analysis dashboard in AOS-8 is a local feature on the MC and does not require Aruba Central. Additionally, application usage monitoring requires DPI on the MCs, not just device discovery.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"The Traffic Analysis dashboard on the Mobility Controller provides visibility into wireless clients’ application usage, such as identifying traffic from applications like Zoom or YouTube. To enable this feature, you must enable firewall visibility and deep packet inspection (DPI) on the MCs. Use the command firewall visibility to activate DPI, which allows the firewall to classify traffic by application. The classified data is then displayed in the Traffic Analysis dashboard under Monitoring > Traffic Analysis." (Page 360, Traffic Analysis Dashboard Section)
Additionally, the HPE Aruba Networking Security Guide notes:
"Firewall visibility on AOS-8 Mobility Controllers enables deep packet inspection (DPI) to classify client traffic by application. This is required for features like the Traffic Analysis dashboard, which displays application usage statistics for wireless clients, helping administrators monitor network activity." (Page 55, Firewall Visibility Section)
Refer to the exhibit, which shows the current network topology.
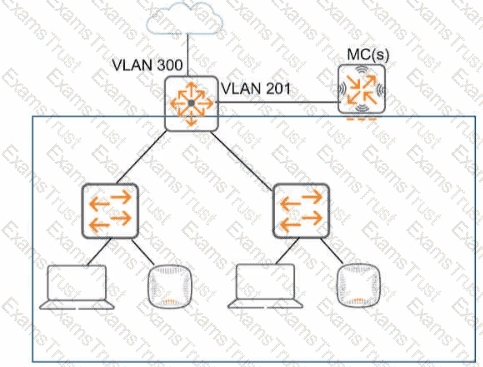
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
Assign the WLAN to a single new VLAN which is dedicated to wireless users
Use wireless user roles to assign the devices to different VLANs in the 100-150 range
Assign the WLAN to a named VLAN which specified 100-150 as the range of IDs.
Use wireless user roles to assign the devices to a range of new vlan IDs.
When setting up VLANs for a wireless solution with an Aruba Mobility Master (MM), Aruba Mobility Controllers (MCs), and campus APs (CAPs), it is recommended to use wireless user roles to assign devices to different VLANs. This allows for greater flexibility and control over network resources and policies applied to different user groups. Wireless user roles can dynamically assign devices to the appropriate VLAN based on a variety of criteria such as user identity, device type, location, and the resources they need to access. This approach aligns with the ArubaOS features that leverage user roles for network access control, as detailed in Aruba's configuration and administration guides.
Refer to the exhibit.
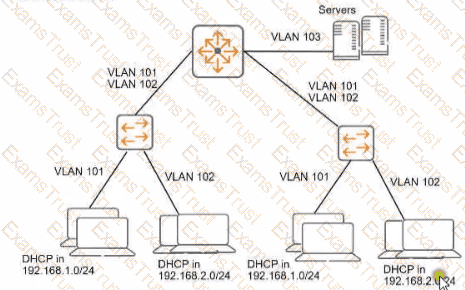
You need to ensure that only management stations in subnet 192.168.1.0/24 can access the ArubaOS-Switches' CLI. Web Ul. and REST interfaces The company also wants to let managers use these stations to access other parts of the network What should you do?
Establish a Control Plane Policing class that selects traffic from 192.168 1.0/24.
Specify 192.168.1.0.255.255.255.0 as authorized IP manager address
Configure the switch to listen for these protocols on OOBM only.
Specify vlan 100 as the management vlan for the switches.
To ensure that only management stations in the subnet 192.168.1.0/24 can access the ArubaOS-Switches' Command Line Interface (CLI), Web UI, and REST interfaces, while also allowing managers to access other parts of the network, you should specify 192.168.1.0 255.255.255.0 as the authorized manager IP address on the switches. This configuration will restrict access to the switch management interfaces to devices within the specified IP address range, effectively creating a management access list.
Refer to the exhibit, which shows the settings on the company’s MCs.
— Mobility Controller
Dashboard General Admin AirWave CPSec Certificates
Configuration
WLANsv Control Plane Security
Roles & PoliciesEnable CP Sec
Access PointsEnable auto cert provisioning:
You have deployed about 100 new Aruba 335-APs. What is required for the APs to become managed?
installing CA-signed certificates on the APs
installing self-signed certificates on the APs
approving the APs as authorized APs on the AP whitelist
configuring a PAPI key that matches on the APs and MCs
Based on the exhibit, which shows the settings on the company's Mobility Controllers (MCs), with 'Control Plane Security' enabled and 'Enable auto cert provisioning' available, new Aruba 335-APs require approval on the MC to become managed. This is commonly done by adding the APs to an authorized AP whitelist, after which they can be automatically provisioned with certificates generated by the MC.
A company has Aruba Mobility Controllers (MCs), Aruba campus APs, and ArubaOS-Switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type. This company is using only CPPM and no other ClearPass solutions.
The ClearPass admins tell you that they want to use HTTP User-Agent strings to help classify endpoints.
What should you do as a part of configuring the ArubaOS-Switches to support this requirement?
Create a device fingerprinting policy that includes HTTP, and apply the policy to edge ports.
Create remote mirrors that collect traffic on edge ports, and mirror it to CPPM's IP address.
Configure CPPM as the sFlow collector, and make sure that sFlow is enabled on edge ports.
Connect the switches to CPPM's span ports, and set up mirroring of HTTP traffic on the switches.
ArubaOS-Switches can use sFlow technology to sample network traffic and send the samples to a collector, such as ClearPass Policy Manager (CPPM), for analysis. sFlow can be configured to capture various types of traffic, including HTTP, which typically contains User-Agent strings that can be used for device fingerprinting and classification.
To support the requirement for using HTTP User-Agent strings to classify endpoints, the switches would need to be configured to send sFlow samples containing HTTP traffic to CPPM. CPPM would then analyze these samples and use the User-Agent strings to classify the devices.
Therefore, the correct action to configure ArubaOS-Switches would involve:
Configuring CPPM as the sFlow collector on the switches.
Enabling sFlow on the edge ports that connect to endpoints.
This approach allows the network traffic to be analyzed by CPPM without requiring any additional mirroring or redirection of traffic, which would be resource-intensive and potentially disruptive to network performance.
What is a benefit of Opportunistic Wireless Encryption (OWE)?
It allows both WPA2-capabie and WPA3-capable clients to authenticate to the same WPA-Personal WLAN
It offers more control over who can connect to the wireless network when compared with WPA2-Personal
It allows anyone lo connect, but provides better protection against eavesdropping than a traditional open network
It provides protection for wireless clients against both honeypot APs and man-in-the-middle (MUM) attacks
The benefit of Opportunistic Wireless Encryption (OWE) is that it allows anyone to connect, but it provides better protection against eavesdropping than a traditional open network. OWE is a type of wireless security specified in the WPA3 standard that offers encrypted communication without the complexity of a full authentication process, thereby securing data on networks that would otherwise be open and unencrypted.
You are troubleshooting an authentication issue for HPE Aruba Networking switches that enforce 802.1X to a cluster of HPE Aruba Networking ClearPass Policy Manager (CPPMs). You know that CPPM is receiving and processing the authentication requests because the Aruba switches are showing Access-Rejects in their statistics. However, you cannot find the record for the Access-Rejects in CPPM Access Tracker.
What is something you can do to look for the records?
Go to the CPPM Event Viewer, because this is where RADIUS Access Rejects are stored.
Verify that you are logged in to the CPPM UI with read-write, not read-only, access.
Make sure that CPPM cluster settings are configured to show Access-Rejects.
Click Edit in Access Viewer and make sure that the correct servers are selected.
The scenario involves troubleshooting an 802.1X authentication issue on HPE Aruba Networking switches (likely AOS-CX switches) that use a cluster of HPE Aruba Networking ClearPass Policy Manager (CPPM) servers as the RADIUS server. The switches show Access-Rejects in their statistics, indicating that CPPM is receiving and processing the authentication requests but rejecting them. However, the records for these Access-Rejects are not visible in CPPM Access Tracker.
Access Tracker: Access Tracker (Monitoring > Live Monitoring > Access Tracker) in CPPM logs all authentication attempts, including successful (Access-Accept) and failed (Access-Reject) requests. If an Access-Reject is not visible in Access Tracker, it suggests that the request was processed at a lower level and not logged in Access Tracker, or there is a visibility issue (e.g., filtering, clustering).
Option A, "Go to the CPPM Event Viewer, because this is where RADIUS Access Rejects are stored," is correct. The Event Viewer (Monitoring > Event Viewer) in CPPM logs system-level events, including RADIUS-related events that might not appear in Access Tracker. For example, if the Access-Reject is due to a configuration issue (e.g., the switch’s IP address is not recognized as a Network Access Device, NAD, or the shared secret is incorrect), the request may be rejected before it is logged in Access Tracker, and the Event Viewer will capture this event (e.g., "RADIUS authentication attempt from unknown NAD"). Since the switches confirm that CPPM is sending Access-Rejects, the Event Viewer is a good place to look for more details.
Option B, "Verify that you are logged in to the CPPM UI with read-write, not read-only, access," is incorrect. Access Tracker visibility is not dependent on read-write vs. read-only access. Both types of accounts can view Access Tracker records, though read-only accounts cannot modify configurations. The issue is that the records are not appearing, not that the user lacks permission to see them.
Option C, "Make sure that CPPM cluster settings are configured to show Access-Rejects," is incorrect. In a CPPM cluster, Access Tracker records are synchronized across nodes, and there is no specific cluster setting to "show Access-Rejects." Access Tracker logs all authentication attempts by default, unless filtered out (e.g., by time range or search criteria), but the issue here is that the records are not appearing at all.
Option D, "Click Edit in Access Viewer and make sure that the correct servers are selected," is incorrect. Access Tracker (not "Access Viewer") does not have an "Edit" option to select servers. In a CPPM cluster, Access Tracker shows records from all nodes by default, and the user can filter by time, NAD, or other criteria, but the absence of records suggests a deeper issue (e.g., the request was rejected before logging in Access Tracker).
The HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide states:
"If an Access-Reject is not visible in Access Tracker, it may indicate that the RADIUS request was rejected at a low level before being logged. The Event Viewer (Monitoring > Event Viewer) logs system-level events, including RADIUS Access-Rejects that do not appear in Access Tracker. For example, if the request is rejected due to an unknown NAD or shared secret mismatch, the Event Viewer will log an event like ‘RADIUS authentication attempt from unknown NAD,’ providing insight into the rejection." (Page 301, Troubleshooting RADIUS Issues Section)
Additionally, the HPE Aruba Networking AOS-CX 10.12 Security Guide notes:
"When troubleshooting 802.1X authentication issues, if the switch logs show Access-Rejects from the RADIUS server (e.g., ClearPass) but the records are not visible in Access Tracker, check the RADIUS server’s system logs. In ClearPass, the Event Viewer logs RADIUS Access-Rejects that may not appear in Access Tracker, such as those caused by NAD configuration issues." (Page 150, Troubleshooting 802.1X Authentication Section)
What is a benefit or using network aliases in ArubaOS firewall policies?
You can associate a reputation score with the network alias to create rules that filler traffic based on reputation rather than IP.
You can use the aliases to translate client IP addresses to other IP addresses on the other side of the firewall
You can adjust the IP addresses in the aliases, and the rules using those aliases automatically update
You can use the aliases to conceal the true IP addresses of servers from potentially untrusted clients.
In ArubaOS firewall policies, using network aliases allows administrators to manage groups of IP addresses more efficiently. By associating multiple IPs with a single alias, any changes made to the alias (like adding or removing IP addresses) are automatically reflected in all firewall rules that reference that alias. This significantly simplifies the management of complex rulesets and ensures consistency across security policies, reducing administrative overhead and minimizing the risk of errors.
An MC has a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The WLAN's default role is set to guest. A Mobility Controller (MC) has these roles configured on it:
authenticated
denyall
guest
general-access
guest-logon
logon
stateful-dot1x
switch-logon
voiceA client authenticates. CPPM returns an Access-Accept with an Aruba-User-Role VSA set to general_access. What role does the client receive?
guest
logon
general-access
authenticated
In an AOS-8 Mobility Controller (MC) environment, a WLAN is configured with WPA3-Enterprise security, using HPE Aruba Networking ClearPass Policy Manager (CPPM) for authentication. The WLAN’s default role is set to "guest," which would be applied if no specific role is assigned after authentication. The MC has several roles configured, including "general-access" (note the underscore in the question: "general_access").
The client successfully authenticates, and CPPM sends an Access-Accept message with an Aruba-User-Role Vendor-Specific Attribute (VSA) set to "general_access." In AOS-8, the Aruba-User-Role VSA is used to assign a specific role to the client, overriding the default role configured on the WLAN. The role specified in the VSA must match a role that exists on the MC. Since "general-access" (or "general_access" as written in the question) is listed among the roles configured on the MC, the MC will apply this role to the client.
The underscore in "general_access" in the VSA versus the hyphen in "general-access" in the MC’s role list is likely a typographical inconsistency in the question. In practice, AOS-8 role names are case-insensitive and typically use hyphens, not underscores, but for the purpose of this question, we assume "general_access" matches "general-access" as the intended role.
Option A, "guest," is incorrect because the guest role is the default 802.1X role for the WLAN, but it is overridden by the Aruba-User-Role VSA specifying "general_access."
Option B, "logon," is incorrect because the logon role is typically applied during the authentication process (e.g., to allow access to DNS or RADIUS servers), not after successful authentication when a specific role is assigned.
Option C, "general-access," is correct because the MC applies the role specified in the Aruba-User-Role VSA ("general_access"), which matches the "general-access" role configured on the MC.
Option D, "authenticated," is incorrect because the "authenticated" role is not specified in the VSA, and there is no indication that it is the default role for successful authentication in this scenario.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When a client authenticates successfully via 802.1X, the Mobility Controller checks for an Aruba-User-Role VSA in the RADIUS Access-Accept message. If the VSA is present and the specified role exists on the controller, the controller assigns that role to the client, overriding the default 802.1X role configured for the WLAN. For example, if the VSA specifies ‘general-access’ and this role is configured on the controller, the client will be assigned the ‘general-access’ role." (Page 305, Role Assignment Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"The Aruba-User-Role VSA allows ClearPass to assign a specific role to a client on an Aruba Mobility Controller. The role name sent in the VSA must match a role configured on the controller, and the controller will apply this role to the client session, ignoring the default role for the WLAN." (Page 289, RADIUS Enforcement Section)
You need to implement a WPA3-Enterprise network that can also support WPA2-Enterprise clients. What is a valid configuration for the WPA3-Enterprise WLAN?
CNSA mode disabled with 256-bit keys
CNSA mode disabled with 128-bit keys
CNSA mode enabled with 256-bit keys
CNSA mode enabled with 128-bit keys
In an Aruba network, when setting up a WPA3-Enterprise network that also supports WPA2-Enterprise clients, you would typically configure the network to operate in a transitional mode that supports both protocols. CNSA (Commercial National Security Algorithm) mode is intended for networks that require higher security standards as specified by the US National Security Agency (NSA). However, for compatibility with WPA2 clients, which do not support CNSA requirements, you would disable CNSA mode. WPA3 can use 256-bit encryption keys, which offer a higher level of security than the 128-bit keys used in WPA2.
You are configuring ArubaOS-CX switches to tunnel client traffic to an Aruba Mobility Controller (MC). What should you do to enhance security for control channel communications between the switches and the MC?
Create one UBT zone for control traffic and a second UBT zone for clients.
Configure a long, random PAPI security key that matches on the switches and the MC.
install certificates on the switches, and make sure that CPsec is enabled on the MC
Make sure that the UBT client vlan is assigned to the interface on which the switches reach the MC and only that interface.
When configuring ArubaOS-CX switches to tunnel client traffic to an Aruba Mobility Controller (MC), securing the control channel communications is crucial to prevent unauthorized access and ensure data integrity. Option B is the correct answer as it involves configuring a long, random PAPI security key that matches on both the switches and the MC. The PAPI (Policy Access Point Interface) protocol is used for secure communication between Aruba devices, and employing a robust, randomized security key significantly enhances the security of the control channel. This setup prevents potential interception or manipulation of the control traffic between the devices.
What purpose does an initialization vector (IV) serve for encryption?
It enables programs to convert easily-remembered passphrases to keys of a correct length.
It makes encryption algorithms more secure by ensuring that the same plaintext and key can produce different ciphertext.
It helps parties to negotiate the keys and algorithms used to secure data before data transmission.
It enables the conversion of asymmetric keys into keys that are suitable for symmetric encryption.
An initialization vector (IV) is a random or pseudo-random value used in encryption algorithms to enhance security. It is commonly used in symmetric encryption modes like Cipher Block Chaining (CBC) or Counter (CTR) modes with algorithms such as AES, which is used in WPA3 and other Aruba security features.
Option B, "It makes encryption algorithms more secure by ensuring that the same plaintext and key can produce different ciphertext," is correct. The primary purpose of an IV is to introduce randomness into the encryption process. When the same plaintext is encrypted with the same key multiple times, the IV ensures that the resulting ciphertext is different each time. This prevents attackers from identifying patterns in the ciphertext, which could otherwise be used to deduce the plaintext or key. For example, in AES-CBC mode, the IV is XORed with the first block of plaintext before encryption, and each subsequent block is chained with the previous ciphertext, ensuring unique outputs.
Option A, "It enables programs to convert easily-remembered passphrases to keys of a correct length," is incorrect. This describes a key derivation function (KDF), such as PBKDF2, which converts a passphrase into a cryptographic key of the correct length. An IV is not involved in key derivation.
Option C, "It helps parties to negotiate the keys and algorithms used to secure data before data transmission," is incorrect. This describes a key exchange or handshake protocol (e.g., Diffie-Hellman or the 4-way handshake in WPA3), not the role of an IV. The IV is used during the encryption process, not during key negotiation.
Option D, "It enables the conversion of asymmetric keys into keys that are suitable for symmetric encryption," is incorrect. This describes a process like hybrid encryption (e.g., using RSA to encrypt a symmetric key), which is not the purpose of an IV. An IV is used in symmetric encryption to enhance security, not to convert keys.
The HPE Aruba Networking Wireless Security Guide states:
"An initialization vector (IV) is a random value used in symmetric encryption algorithms like AES to enhance security. The IV ensures that the same plaintext encrypted with the same key produces different ciphertext each time, preventing attackers from identifying patterns in the ciphertext. In WPA3, for example, the IV is used in AES-GCMP encryption to ensure that each packet is encrypted uniquely, even if the same data is sent multiple times." (Page 28, Encryption Fundamentals Section)
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"The initialization vector (IV) in encryption algorithms like AES-CBC or AES-GCMP makes encryption more secure by ensuring that identical plaintext encrypted with the same key results in different ciphertext. This randomness prevents pattern analysis attacks, which could otherwise compromise the security of the encryption." (Page 282, Wireless Encryption Section)
What is a benefit of deploying Aruba ClearPass Device insight?
Highly accurate endpoint classification for environments with many devices types, including Internet of Things (loT)
visibility into devices' 802.1X supplicant settings and automated certificate deployment
Agent-based analysts of devices' security settings and health status, with the ability to implement quarantining
Simpler troubleshooting of ClearPass solutions across an environment with multiple ClearPass Policy Managers
Aruba ClearPass Device Insight offers a significant benefit by providing highly accurate endpoint classification. This feature is particularly useful in complex environments with a wide variety of device types, including IoT devices. Accurate device classification allows network administrators to better understand the nature and behavior of devices on their network, which is crucial for implementing appropriate security policies and ensuring network performance and security.
A company has an ArubaOS controller-based solution with a WPA3-Enterprise WLAN. which authenticates wireless clients to Aruba ClearPass Policy Manager (CPPM). The company has decided to use digital certificates for authentication A user's Windows domain computer has had certificates installed on it However, the Networks and Connections window shows that authentication has tailed for the user. The Mobility Controllers (MC's) RADIUS events show that it is receiving Access-Rejects for the authentication attempt.
What is one place that you can you look for deeper insight into why this authentication attempt is failing?
the reports generated by Aruba ClearPass Insight
the RADIUS events within the CPPM Event Viewer
the Alerts tab in the authentication record in CPPM Access Tracker
the packets captured on the MC control plane destined to UDP 1812
When an authentication attempt for a user's Windows domain computer is failing on a WPA3-Enterprise WLAN and the Mobility Controller is receiving Access-Rejects, one place to look for deeper insight is the RADIUS events within the CPPM Event Viewer. ClearPass Policy Manager (CPPM) logs all RADIUS authentication events, and the Event Viewer would show detailed information about why a particular authentication attempt was rejected. This could include reasons such as incorrect credentials, expired certificates, or policy mismatches. The CPPM Event Viewer is an essential troubleshooting tool within ClearPass to diagnose authentication issues, as indicated in the ClearPass Policy Manager documentation.
From which solution can ClearPass Policy Manager (CPPM) receive detailed information about client device type OS and status?
ClearPass Onboard
ClearPass Access Tracker
ClearPass OnGuard
ClearPass Guest
ClearPass Policy Manager (CPPM) can receive detailed information about client device type, OS, and status from ClearPass OnGuard. ClearPass OnGuard is part of the ClearPass suite and provides posture assessment and endpoint health checks. It gathers detailed information on the status and security posture of devices trying to connect to the network, such as whether antivirus software is up to date, which operating system is running, and other details that characterize the device's compliance with the network's security policies.
A user is having trouble connecting to an AP managed by a standalone Mobility Controller (MC). What can you do to get detailed logs and debugs for that user's client?
In the MC CLI, set up a control plane packet capture and filter for the client's IP address.
In the MC CLI, set up a data plane packet capture and filter for the client's MAC address.
In the MC UI’s Traffic Analytics dashboard, look for the client's IP address.
In the MC UI’s Diagnostics > Logs pages, add a "user-debug" log setting for the client's MAC address.
When troubleshooting connectivity issues for a user connecting to an AP managed by a standalone Mobility Controller (MC) in an AOS-8 architecture, detailed logs and debugs specific to the user’s client are essential. The MC provides several tools for capturing logs and debugging information, including packet captures and user-specific debug logs.
Option D, "In the MC UI’s Diagnostics > Logs pages, add a ‘user-debug’ log setting for the client's MAC address," is correct. The "user-debug" feature in the MC allows administrators to enable detailed debugging for a specific client by specifying the client’s MAC address. This generates logs related to the client’s authentication, association, role assignment, and other activities, which are critical for troubleshooting connectivity issues. The Diagnostics > Logs pages in the MC UI provide a user-friendly way to configure this setting and view the resulting logs.
Option A, "In the MC CLI, set up a control plane packet capture and filter for the client's IP address," is incorrect because control plane packet captures are used to capture management traffic (e.g., between the MC and APs or other controllers), not user traffic. Additionally, the client may not yet have an IP address if connectivity is failing, making an IP-based filter less effective.
Option B, "In the MC CLI, set up a data plane packet capture and filter for the client's MAC address," is a valid troubleshooting method but is not the best choice for getting detailed logs. Data plane packet captures are useful for analyzing user traffic (e.g., to see if packets are being dropped), but they do not provide the same level of detailed logging as the "user-debug" feature, which includes authentication and association events.
Option C, "In the MC UI’s Traffic Analytics dashboard, look for the client's IP address," is incorrect because the Traffic Analytics dashboard is used for monitoring application usage and traffic patterns, not for detailed troubleshooting of a specific client’s connectivity issues. Additionally, if the client cannot connect, it may not have an IP address or generate traffic visible in the dashboard.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"To troubleshoot issues for a specific wireless client, you can enable user-specific debugging using the ‘user-debug’ feature. In the Mobility Controller UI, navigate to Diagnostics > Logs, and add a ‘user-debug’ log setting for the client’s MAC address. This will generate detailed logs for the client, including authentication, association, and role assignment events, which can be viewed in the Logs page. For example, to enable user-debug for a client with MAC address 00:11:22:33:44:55, add the setting ‘user-debug 00:11:22:33:44:55’." (Page 512, Troubleshooting Wireless Clients Section)
Additionally, the guide notes:
"While packet captures (control plane or data plane) can be useful for analyzing traffic, the ‘user-debug’ feature provides more detailed logs for troubleshooting client-specific issues, such as failed authentication or association problems." (Page 513, Debugging Tools Section)
You need to deploy an Aruba instant AP where users can physically reach It. What are two recommended options for enhancing security for management access to the AP? (Select two )
Disable Its console ports
Place a Tamper Evident Label (TELS) over its console port
Disable the Web Ul.
Configure WPA3-Enterpnse security on the AP
install a CA-signed certificate
When deploying an Aruba Instant AP in a location where users can physically access it, enhancing security for management access could involve several measures: C. Disabling the Web UI will prevent unauthorized access via the browser-based management interface, which could be a security risk if the AP is within physical reach of untrusted parties. E. Installing a CA-signed certificate helps ensure that any communication with the AP's management interface is encrypted and authenticated, preventing man-in-the-middle attacks and eavesdropping.
How can hackers implement a man-in-the-middle (MITM) attack against a wireless client?
The hacker uses a combination of software and hardware to jam the RF band and prevent the client from connecting to any wireless networks.
The hacker runs an NMap scan on the wireless client to find its MAC and IP address. The hacker then connects to another network and spoofs those addresses.
The hacker uses spear-phishing to probe for the IP addresses that the client is attempting to reach. The hacker device then spoofs those IP addresses.
The hacker connects a device to the same wireless network as the client and responds to the client's ARP requests with the hacker device's MAC address.
A man-in-the-middle (MITM) attack involves an attacker positioning themselves between a wireless client and the legitimate network to intercept or manipulate traffic. HPE Aruba Networking documentation often discusses MITM attacks in the context of wireless security threats and mitigation strategies.
Option D, "The hacker connects a device to the same wireless network as the client and responds to the client's ARP requests with the hacker device's MAC address," is correct. This describes an ARP poisoning (or ARP spoofing) attack, a common MITM technique in wireless networks. The hacker joins the same wireless network as the client (e.g., by authenticating with the same SSID and credentials). Once on the network, the hacker sends fake ARP responses to the client, associating the hacker’s MAC address with the IP address of the default gateway (or another target device). This causes the client to send traffic to the hacker’s device instead of the legitimate gateway, allowing the hacker to intercept, modify, or forward the traffic, thus performing an MITM attack.
Option A, "The hacker uses a combination of software and hardware to jam the RF band and prevent the client from connecting to any wireless networks," is incorrect. Jamming the RF band would disrupt all wireless communication, including the hacker’s ability to intercept traffic. This is a denial-of-service (DoS) attack, not an MITM attack.
Option B, "The hacker runs an NMap scan on the wireless client to find its MAC and IP address. The hacker then connects to another network and spoofs those addresses," is incorrect. NMap scans are used for network discovery and port scanning, not for implementing an MITM attack. Spoofing MAC and IP addresses on another network does not position the hacker to intercept the client’s traffic on the original network.
Option C, "The hacker uses spear-phishing to probe for the IP addresses that the client is attempting to reach. The hacker device then spoofs those IP addresses," is incorrect. Spear-phishing is a delivery method for malware or credentials theft, not a direct method for implementing an MITM attack. Spoofing IP addresses alone does not allow the hacker to intercept traffic unless they are on the same network and can manipulate routing (e.g., via ARP poisoning).
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"A common man-in-the-middle (MITM) attack against wireless clients involves ARP poisoning. The hacker connects a device to the same wireless network as the client and sends fake ARP responses to the client, associating the hacker’s MAC address with the IP address of the default gateway. This causes the client to send traffic to the hacker’s device, allowing the hacker to intercept and manipulate the traffic." (Page 422, Wireless Threats Section)
Additionally, the HPE Aruba Networking Security Guide notes:
"ARP poisoning is a prevalent MITM attack in wireless networks. The attacker joins the same network as the client and responds to the client’s ARP requests with the attacker’s MAC address, redirecting traffic through the attacker’s device. This allows the attacker to intercept sensitive data or modify traffic between the client and the legitimate destination." (Page 72, Wireless MITM Attacks Section)
Refer to the exhibit.
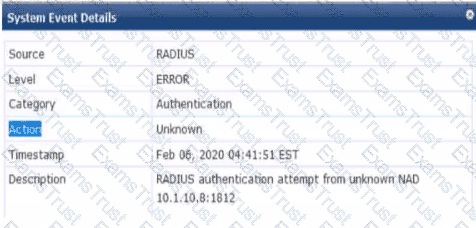
You are deploying a new ArubaOS Mobility Controller (MC), which is enforcing authentication to Aruba ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown In the exhibit in the CPPM Event Viewer.
What should you check?
that the MC has been added as a domain machine on the Active Directory domain with which CPPM is synchronized
that the snared secret configured for the CPPM authentication server matches the one defined for the device on CPPM
that the IP address that the MC is using to reach CPPM matches the one defined for the device on CPPM
that the MC has valid admin credentials configured on it for logging into the CPPM
Given the error message from the ClearPass Policy Manager (CPPM) Event Viewer, indicating a RADIUS authentication attempt from an unknown Network Access Device (NAD), you should check that the IP address the Mobility Controller (MC) is using to communicate with CPPM matches the IP address defined for the MC in the CPPM's device inventory. If there is a mismatch in IP addresses, CPPM will not recognize the MC as a known device and will not process the authentication request, leading to the error observed.
Which is a correct description of a Public Key Infrastructure (PKI)?
A device uses Intermediate Certification Authorities (CAs) to enable it to trust root CAs that are different from the root CA that signed its own certificate.
A user must manually choose to trust intermediate and end-entity certificates, or those certificates must be installed on the device as trusted in advance.
Root Certification Authorities (CAs) primarily sign certificates, and Intermediate Certification Authorities (CAs) primarily validate signatures.
A user must manually choose to trust a root Certification Authority (CA) certificate, or the root CA certificate must be installed on the device as trusted.
Public Key Infrastructure (PKI) relies on a trusted root Certification Authority (CA) to issue certificates. Devices and users must trust the root CA for the PKI to be effective. If a root CA certificate is not pre-installed or manually chosen to be trusted on a device, any certificates issued by that CA will not be inherently trusted by the device.
You have an Aruba Mobility Controller (MC) that is locked in a closet. What is another step that Aruba recommends to protect the MC from unauthorized access?
Use local authentication rather than external authentication to authenticate admins.
Change the password recovery password.
Set the local admin password to a long random value that is unknown or locked up securely.
Disable local authentication of administrators entirely.
Protecting an Aruba Mobility Controller from unauthorized access involves several layers of security. One recommendation is to change the password recovery password, which is a special type of password used to recover access to the device in the event the admin password is lost. Changing this to something complex and unique adds an additional layer of security in the event the physical security of the device is compromised.
Refer to the exhibit, which shows the settings on the company's MCs.
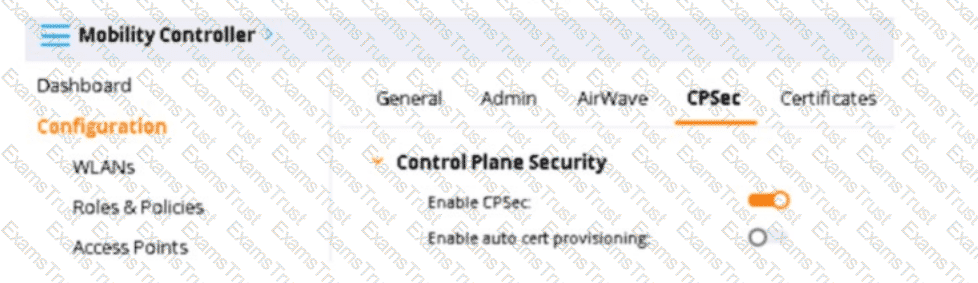
You have deployed about 100 new HPE Aruba Networking 335 APs. What is required for the APs to become managed?
Installing CA-signed certificates on the APs
Approving the APs as authorized APs on the AP whitelist
Installing self-signed certificates on the APs
Configuring a PAPI key that matches on the APs and MCs
The scenario involves an AOS-8 Mobility Controller (MC) with Control Plane Security (CPSec) enabled and auto certificate provisioning disabled. CPSec is a feature that secures the control plane communication between the MC and APs using certificates. When CPSec is enabled, APs must be authorized and trusted by the MC to become managed.
CPSec Enabled, Auto Cert Provisioning Disabled: When CPSec is enabled, APs must have a valid certificate to establish a secure control plane connection with the MC. If auto certificate provisioning is disabled (as shown in the exhibit), the MC does not automatically provision certificates to the APs. Instead, the APs must already have a factory-installed certificate (or a manually installed certificate), and the MC must trust the AP’s certificate by having the issuing CA in its trust list. Additionally, the AP must be on the MC’s AP whitelist to be authorized.
AP Whitelist: The AP whitelist is a list of authorized APs maintained on the MC (or Mobility Master, MM, if present). For an AP to become managed, its MAC address must be in the whitelist, especially when CPSec is enabled and auto provisioning is disabled. This ensures that only authorized APs can connect to the MC.
Option A, "Installing CA-signed certificates on the APs," is incorrect because HPE Aruba Networking APs, such as the 335 series, come with factory-installed certificates signed by Aruba’s CA. These certificates are sufficient for CPSec, provided the MC trusts the Aruba CA (which is typically preconfigured). Manually installing CA-signed certificates is not required unless the factory certificates are not used or trusted.
Option B, "Approving the APs as authorized APs on the AP whitelist," is correct. With CPSec enabled and auto cert provisioning disabled, the APs must be explicitly authorized by adding their MAC addresses to the AP whitelist on the MC. This step ensures that the MC accepts the AP’s certificate and allows it to become managed.
Option C, "Installing self-signed certificates on the APs," is incorrect because self-signed certificates are not typically used for CPSec. APs use factory-installed certificates, and the MC must trust the issuing CA. Self-signed certificates would require manual trust configuration on the MC, which is not a standard practice.
Option D, "Configuring a PAPI key that matches on the APs and MCs," is incorrect. PAPI (Protocol for AP Provisioning and Information) keys are used for securing communication between APs and the MC in non-CPSec environments or for specific configurations (e.g., when CPSec is disabled). When CPSec is enabled, certificate-based authentication replaces the need for a PAPI key.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When Control Plane Security (CPSec) is enabled and auto certificate provisioning is disabled, APs must be authorized by adding their MAC addresses to the AP whitelist on the Mobility Controller (or Mobility Master). The AP uses its factory-installed certificate to establish a secure control plane connection with the MC. The MC must trust the CA that issued the AP’s certificate (e.g., Aruba’s CA), and the AP must be in the whitelist to become managed. To add an AP to the whitelist, navigate to Configuration > Access Points > AP Whitelist in the MC UI and add the AP’s MAC address." (Page 395, CPSec Configuration Section)
Additionally, the HPE Aruba Networking CPSec Deployment Guide notes:
"If auto cert provisioning is disabled, the AP whitelist becomes mandatory for CPSec. Each AP must be explicitly approved by adding its MAC address to the whitelist, ensuring that only authorized APs can connect to the MC. The AP’s factory certificate is used for authentication, and no manual certificate installation is required on the AP." (Page 12, CPSec with Manual Provisioning Section)
Refer to the exhibit:
port-access role role1 vlan access 11
port-access role role2 vlan access 12
port-access role role3 vlan access 13
port-access role role4 vlan access 14
aaa authentication port-access dot1x authenticator
enable
interface 1/1/1
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
interface 1/1/2
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
The exhibit shows the configuration on an AOS-CX switch.
Client1 connects to port 1/1/1 and authenticates to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM sends an Access-Accept with this VSA: Aruba-User-Role: role4.
Client2 connects to port 1/1/2 and does not attempt to authenticate.To which roles are the users assigned?
Client1 = role3; Client2 = role2
Client1 = role4; Client2 = role1
Client1 = role4; Client2 = role2
Client1 = role3; Client2 = role1
The scenario involves an AOS-CX switch configured for 802.1X port-access authentication. The configuration defines several roles and their associated VLANs:
port-access role role1 vlan access 11: Role1 assigns VLAN 11.
port-access role role2 vlan access 12: Role2 assigns VLAN 12.
port-access role role3 vlan access 13: Role3 assigns VLAN 13.
port-access role role4 vlan access 14: Role4 assigns VLAN 14.
The switch has 802.1X authentication enabled globally (aaa authentication port-access dot1x authenticator enable). Two ports are configured:
Interface 1/1/1:
vlan access 1: Default VLAN is 1.
aaa authentication port-access critical-role role1: If the RADIUS server is unavailable, assign role1 (VLAN 11).
aaa authentication port-access preauth-role role2: Before authentication, assign role2 (VLAN 12).
aaa authentication port-access auth-role role3: After successful authentication, assign role3 (VLAN 13) unless overridden by a VSA.
Interface 1/1/2: Same configuration as 1/1/1.
Client1 on port 1/1/1:
Client1 authenticates successfully, and CPPM sends an Access-Accept with the VSA Aruba-User-Role: role4.
In AOS-CX, the auth-role (role3) is applied after successful authentication unless the RADIUS server specifies a different role via the Aruba-User-Role VSA. Since CPPM sends Aruba-User-Role: role4, and role4 exists on the switch, Client1 is assigned role4 (VLAN 14), overriding the default auth-role (role3).
Client2 on port 1/1/2:
Client2 does not attempt to authenticate (i.e., does not send 802.1X credentials).
In AOS-CX, if a client does not attempt authentication and no other authentication method (e.g., MAC authentication) is configured, the client is placed in the preauth-role (role2, VLAN 12). This role is applied before authentication or when authentication is not attempted, allowing the client limited access (e.g., to perform authentication or access a captive portal).
Option A, "Client1 = role3; Client2 = role2," is incorrect because Client1 should be assigned role4 (from the VSA), not role3.
Option B, "Client1 = role4; Client2 = role1," is incorrect because Client2 should be assigned the preauth-role (role2), not the critical-role (role1), since the RADIUS server is reachable (Client1 authenticated successfully).
Option C, "Client1 = role4; Client2 = role2," is correct. Client1 gets role4 from the VSA, and Client2 gets the preauth-role (role2) since it does not attempt authentication.
Option D, "Client1 = role3; Client2 = role1," is incorrect for the same reasons as Option A and Option B.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"After successful 802.1X authentication, the AOS-CX switch assigns the client to the auth-role configured for the port (e.g., aaa authentication port-access auth-role role3). However, if the RADIUS server returns an Aruba-User-Role VSA (e.g., Aruba-User-Role: role4), and the specified role exists on the switch, the client is assigned that role instead of the auth-role. If a client does not attempt authentication and no other authentication method is configured, the client is assigned the preauth-role (e.g., aaa authentication port-access preauth-role role2), which provides limited access before authentication." (Page 132, 802.1X Authentication Section)
Additionally, the guide notes:
"The critical-role (e.g., aaa authentication port-access critical-role role1) is applied only when the RADIUS server is unavailable. The preauth-role is applied when a client connects but does not attempt 802.1X authentication." (Page 134, Port-Access Roles Section)
You have detected a Rogue AP using the Security Dashboard Which two actions should you take in responding to this event? (Select two)
There is no need to locale the AP If you manually contain It.
This is a serious security event, so you should always contain the AP immediately regardless of your company's specific policies.
You should receive permission before containing an AP. as this action could have legal Implications.
For forensic purposes, you should copy out logs with relevant information, such as the time mat the AP was detected and the AP's MAC address.
There is no need to locate the AP If the Aruba solution is properly configured to automatically contain it.
When responding to the detection of a Rogue AP, it's important to consider legal implications and to gather forensic evidence:
You should receive permission before containing an AP (Option C), as containing it could disrupt service and may have legal implications, especially if the AP is on a network that the organization does not own.
For forensic purposes, it is essential to document the event by copying out logs with relevant information, such as the time the AP was detected and the AP's MAC address (Option D). This information could be crucial if legal action is taken or if a detailed analysis of the security breach is required.
Automatically containing an AP without consideration for the context (Options A and E) can be problematic, as it might inadvertently interfere with neighboring networks and cause legal issues. Immediate containment without consideration of company policy (Option B) could also violate established incident response procedures.
You have been instructed to look in the ArubaOS Security Dashboard's client list Your goal is to find clients mat belong to the company and have connected to devices that might belong to hackers
Which client fits this description?
MAC address d8:50:e6:f3;6d;a4; Client Classification Authorized; AP Classification, interfering
MAC address d8:50:e6 f3;6e;c5; Client Classification Interfering. AP Classification Neighbor
MAC address d8:50:e6:f3;6e;60; Client Classification Interfering. AP Classification Interfering
MAC address d8:50:e6:f3;TO;ab; Client Classification Interfering. AP Classification Rogue
In the context of the ArubaOS Security Dashboard, if the goal is to find company clients that have connected to devices potentially operated by hackers, you would look for a client that is classified as 'Interfering' (indicating a security threat) while being connected to an 'AP Classification: Rogue'. A rogue AP is one that is not under the control of network administrators and is considered malicious or a security threat. Therefore, the client fitting this description is:
MAC address: d8:50:e6:f3:70:ab; Client Classification: Interfering; AP Classification: Rogue
You have been instructed to look in the ArubaOS Security Dashboard's client list. Your goal is to find clients that belong to the company and have connected to devices that might belong to hackers.
Which client fits this description?
MAC address: d8:50:e6:f3:70:ab; Client Classification: Interfering; AP Classification: Rogue
MAC address: d8:50:e6:f3:6e:c5; Client Classification: Interfering; AP Classification: Neighbor
MAC address: d8:50:e6:f3:6e:60; Client Classification: Interfering; AP Classification: Authorized
MAC address: d8:50:e6:f3:6d:a4; Client Classification: Authorized; AP Classification: Rogue
The ArubaOS Security Dashboard, part of the AOS-8 architecture (Mobility Controllers or Mobility Master), provides visibility into wireless clients and access points (APs) through its Wireless Intrusion Prevention (WIP) system. The goal is to identify clients that belong to the company (i.e., authorized clients) and have connected to devices that might belong to hackers (i.e., rogue APs).
Client Classification:
Authorized: A client that has successfully authenticated to an authorized AP and is recognized as part of the company’s network (e.g., an employee device).
Interfering: A client that is not authenticated to the company’s network and is considered external or potentially malicious.
AP Classification:
Authorized: An AP that is part of the company’s network and managed by the MC/MM.
Rogue: An AP that is not authorized and is suspected of being malicious (e.g., connected to the company’s wired network without permission).
Neighbor: An AP that is not part of the company’s network but is not connected to the wired network (e.g., a nearby AP from another organization).
The requirement is to find a client that is authorized (belongs to the company) and connected to a rogue AP (might belong to hackers).
Option A: MAC address: d8:50:e6:f3:70:ab; Client Classification: Interfering; AP Classification: RogueThis client is classified as "Interfering," meaning it does not belong to the company. Although it is connected to a rogue AP, it does not meet the requirement of being a company client.
Option B: MAC address: d8:50:e6:f3:6e:c5; Client Classification: Interfering; AP Classification: NeighborThis client is "Interfering" (not a company client) and connected to a "Neighbor" AP, which is not considered a hacker’s device (it’s just a nearby AP).
Option C: MAC address: d8:50:e6:f3:6e:60; Client Classification: Interfering; AP Classification: AuthorizedThis client is "Interfering" (not a company client) and connected to an "Authorized" AP, which is part of the company’s network, not a hacker’s device.
Option D: MAC address: d8:50:e6:f3:6d:a4; Client Classification: Authorized; AP Classification: RogueThis client is "Authorized," meaning it belongs to the company, and it is connected to a "Rogue" AP, which might belong to hackers. This matches the requirement perfectly.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"The Security Dashboard in ArubaOS provides a client list that includes the client classification and the AP classification for each client. A client classified as ‘Authorized’ has successfully authenticated to an authorized AP and is part of the company’s network. A ‘Rogue’ AP is an unauthorized AP that is suspected of being malicious, often because it is connected to the company’s wired network (e.g., detected via Eth-Wired-Mac-Table match). To identify potential security risks, look for authorized clients connected to rogue APs, as this may indicate that a company device has connected to a hacker’s AP." (Page 415, Security Dashboard Section)
Additionally, the HPE Aruba Networking Security Guide notes:
"An ‘Authorized’ client is one that has authenticated to an AP managed by the controller, typically an employee or corporate device. A ‘Rogue’ AP is classified as such if it is not authorized and poses a potential threat, such as being connected to the corporate LAN. Identifying authorized clients connected to rogue APs is critical for detecting potential man-in-the-middle attacks." (Page 78, WIP Classifications Section)
A company is deploying AOS-CX switches to support 114 employees, which will tunnel client traffic to an HPE Aruba Networking Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the AOS-CX switches.
What are the licensing requirements for the MC?
One PEF license per switch
One PEF license per switch, and one WCC license per switch
One AP license per switch
One AP license per switch, and one PEF license per switch
The scenario involves AOS-CX switches tunneling client traffic to an HPE Aruba Networking Mobility Controller (MC) in an AOS-8 architecture. The MC will apply firewall policies and perform deep packet inspection (DPI) on the tunneled traffic. The MC is dedicated to receiving traffic from the AOS-CX switches, and there are 114 employees (implying 114 potential clients). The question asks about the licensing requirements for the MC.
Tunneling from AOS-CX Switches to MC: In this setup, the AOS-CX switches act as Layer 2 devices, tunneling client traffic to the MC using a mechanism like GRE or VXLAN (though GRE is more common in AOS-8). The MC treats the tunneled traffic as if it were coming from wireless clients, applying firewall policies and DPI.
Licensing in AOS-8:
AP License (Access Point License): Required for each AP managed by the MC. Since the scenario involves AOS-CX switches tunneling traffic, not APs, AP licenses are not required.
PEF License (Policy Enforcement Firewall License): Required to enable the stateful firewall and DPI features on the MC. The PEF license is based on the number of devices (e.g., switches, APs) or users that the MC processes traffic for. In this case, the MC is processing traffic from AOS-CX switches, and the license is typically per switch (not per user or employee).
WCC License (Web Content Classification License): An optional license that enhances DPI by enabling URL-based filtering and web content classification. This is not mentioned as a requirement in the scenario.
Option A, "One PEF license per switch," is correct. Since the MC is dedicated to receiving traffic from the AOS-CX switches, and the MC will apply firewall policies and DPI, a PEF license is required. In AOS-8, when switches tunnel traffic to an MC, the PEF license is typically required per switch (not per user). With 114 employees, the number of switches is not specified, but the licensing model is per switch, so one PEF license per switch is needed.
Option B, "One PEF license per switch, and one WCC license per switch," is incorrect. While a PEF license is required, a WCC license is not mentioned as a requirement. WCC is for advanced web filtering, which is not specified in the scenario.
Option C, "One AP license per switch," is incorrect. AP licenses are for managing APs, not switches. Since the scenario involves switches tunneling traffic, not APs, AP licenses are not required.
Option D, "One AP license per switch, and one PEF license per switch," is incorrect for the same reason as Option C. AP licenses are not needed, but the PEF license per switch is correct.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"The Policy Enforcement Firewall (PEF) license is required on the Mobility Controller to enable stateful firewall policies and deep packet inspection (DPI). When AOS-CX switches tunnel client traffic to the MC for firewall processing, a PEF license is required for each switch. The license is based on the number of devices (e.g., switches) sending traffic to the MC, not the number of users. For example, if 10 switches tunnel traffic to the MC, 10 PEF licenses are required." (Page 375, Licensing Requirements Section)
Additionally, the HPE Aruba Networking Licensing Guide notes:
"PEF licenses on the Mobility Controller are required for firewall and DPI features. In deployments where switches tunnel traffic to the MC, the PEF license is typically per switch. AP licenses are not required unless the MC is managing APs. The Web Content Classification (WCC) license is optional and only needed for advanced URL filtering, which is not required for basic DPI." (Page 15, PEF Licensing Section)
An organization has HPE Aruba Networking infrastructure, including AOS-CX switches and an AOS-8 mobility infrastructure with Mobility Controllers (MCs) and APs. Clients receive certificates from ClearPass Onboard. The infrastructure devices authenticate clients to ClearPass Policy Manager (CPPM). The company wants to start profiling clients to take their device type into account in their access rights.
What is a role that CPPM should play in this plan?
Assigning clients to their device categories
Helping to forward profiling information to the component responsible for profiling
Accepting and enforcing CoA messages
Enforcing access control decisions
HPE Aruba Networking ClearPass Policy Manager (CPPM) is a network access control (NAC) solution that provides device profiling, authentication, and policy enforcement. In this scenario, the company wants to profile clients to determine their device type and use that information to define access rights. Device profiling in ClearPass involves identifying and categorizing devices based on various attributes, such as DHCP fingerprints, HTTP User-Agent strings, or TCP fingerprinting, to assign them to specific device categories (e.g., Windows, macOS, IoT devices, etc.). These categories can then be used in policy decisions to grant or restrict access.
Option A, "Assigning clients to their device categories," directly aligns with ClearPass’s role in device profiling. ClearPass collects profiling data from network devices (like APs, MCs, or switches) and uses its profiling engine to categorize devices. This categorization is a core function of ClearPass Device Insight, which is integrated into CPPM, and is used to build policies based on device type.
Option B, "Helping to forward profiling information to the component responsible for profiling," is incorrect because ClearPass itself is the component responsible for profiling. It doesn’t forward data to another system for profiling; instead, it collects data (e.g., via DHCP snooping, HTTP headers, or mirrored traffic) and processes it internally.
Option C, "Accepting and enforcing CoA messages," refers to ClearPass’s ability to send Change of Authorization (CoA) messages to network devices to dynamically change a client’s access rights (e.g., reassign a role or disconnect a session). While CoA is part of ClearPass’s enforcement capabilities, it is not directly related to the profiling process or categorizing devices.
Option D, "Enforcing access control decisions," is a broader function of ClearPass. While ClearPass does enforce access control decisions based on profiling data (e.g., by assigning roles or VLANs), the question specifically asks about its role in the profiling process, not the enforcement step that follows.
The HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide states:
"ClearPass Policy Manager provides a mechanism to profile devices that connect to the network. Device profiling collects information about a device during its authentication or through network monitoring (e.g., DHCP, HTTP, or SNMP). The collected data is used to identify and categorize the device into a device category (e.g., Computer, Smartphone, Printer, etc.) and device family (e.g., Windows, Android, etc.). These categories can then be used in policy conditions to enforce access control." (Page 245, Device Profiling Section)
Additionally, the ClearPass Device Insight Data Sheet notes:
"ClearPass Device Insight uses a combination of passive and active profiling techniques to identify and classify devices. It assigns devices to categories based on their attributes, enabling organizations to create granular access policies." (Page 2)
An ArubaOS-CX switch enforces 802.1X on a port. No fan-through options or port-access roles are configured on the port The 802 1X supplicant on a connected client has not yet completed authentication
Which type of traffic does the authenticator accept from the client?
EAP only
DHCP, DNS and RADIUS only
RADIUS only
DHCP, DNS, and EAP only
For an ArubaOS-CX switch enforcing 802.1X on a port without any fallback options or port-access roles configured, and where the supplicant on the connected client has not completed authentication, the only type of traffic the authenticator accepts from the client is EAP (Extensible Authentication Protocol). EAP is a universal authentication framework used in 802.1X for message exchange during the authentication process. The switch allows EAP packets because they are necessary for the client and the authentication server to perform the authentication process. This is standard behavior for 802.1X authenticators, which is to permit EAP traffic to pass through even before authentication is successful to facilitate the authentication exchange. This information is supported by the IEEE 802.1X standard and ArubaOS-CX security configuration guides.
Copyright © 2014-2025 Examstrust. All Rights Reserved
