Which of the following vault lease operations uses a lease_id as an argument? Choose two correct answers.
An organization would like to use a scheduler to track & revoke access granted to a job (by Vault) at completion. What auth-associated Vault object should be tracked to enable this behavior?
What are orphan tokens?
You can build a high availability Vault cluster with any storage backend.
The key/value v2 secrets engine is enabled at secret/ See the following policy:
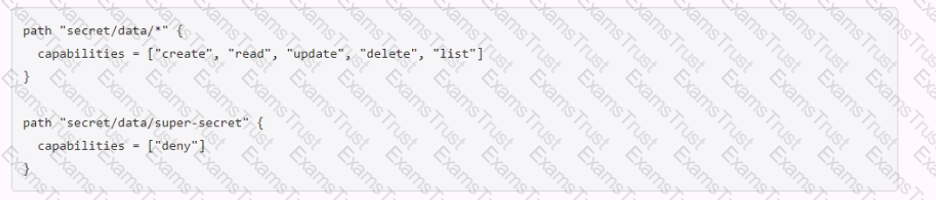
Which of the following operations are permitted by this policy? Choose two correct answers.
An authentication method should be selected for a use case based on:
How would you describe the value of using the Vault transit secrets engine?
Which of these are a benefit of using the Vault Agent?
To make an authenticated request via the Vault HTTP API, which header would you use?
Which of the following cannot define the maximum time-to-live (TTL) for a token?
Your DevOps team would like to provision VMs in GCP via a CICD pipeline. They would like to integrate Vault to protect the credentials used by the tool. Which secrets engine would you recommend?
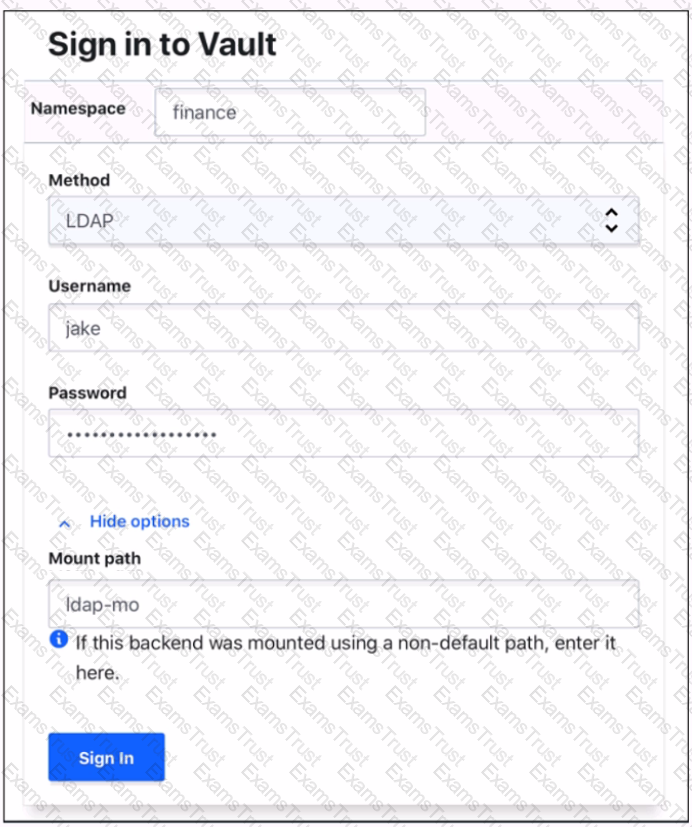
Where do you define the Namespace to log into using the Vault Ul?
To answer this question
Use your mouse to click on the screenshot in the location described above. An arrow indicator will mark where you have clicked. Click the "Answer" button once you have positioned the arrow to answer the question. You may need to scroll down to see the entire screenshot.
Running the second command in the GUI CLI will succeed.
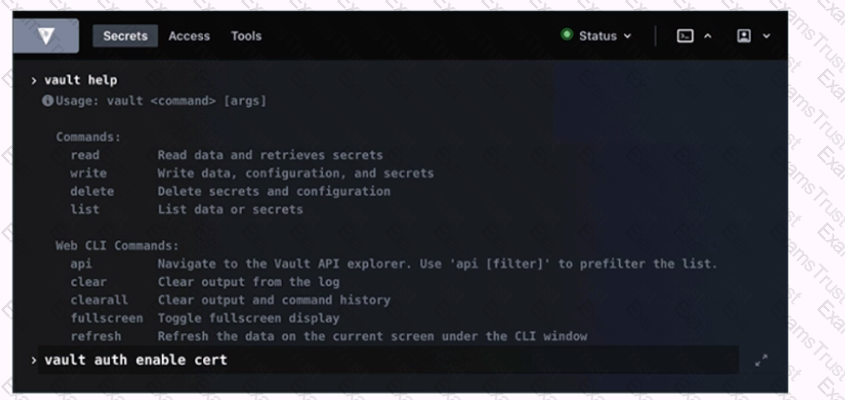
Which of the following is a machine-oriented Vault authentication backend?
When looking at Vault token details, which key helps you find the paths the token is able to access?
The following three policies exist in Vault. What do these policies allow an organization to do?
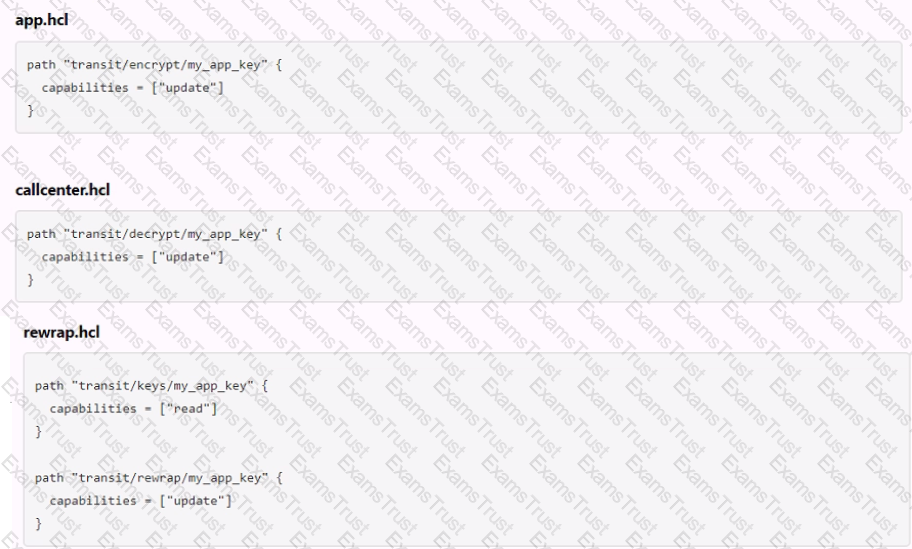
A web application uses Vault's transit secrets engine to encrypt data in-transit. If an attacker intercepts the data in transit which of the following statements are true? Choose two correct answers.