How can Vault be used to programmatically obtain a generated code for MFA, somewhat similar to Google Authenticator?
The following is a snippet from a Terraform configuration file:
1. provider "aws" {
2. region = "us-east-1"
3. }
4. provider "aws" {
5. region = "us-west-1"
6. }
which, when validated, results in the following error:-
1. Error: Duplicate provider configuration
2.
3. on main.tf line 5:
4. 5: provider "aws" {
5.
6. A default provider configuration for "aws" was already given at
7. main.tf:1,1-15. If multiple configurations are required, set the "______"
8. argument for alternative configurations.
Fill in the blank in the error message with the correct string from the list below.
Which of the following best describes the default local backend?
What is the result of the following terraform function call?
zipmap(["a", "b"], [1, 2])
Which of the following actions are performed during a terraform init? (select three)
When writing the Terraform code, HashiCorp recommends that you use how many spaces between each nesting level?
Which flag would be used within a Terraform configuration block to identify the specific version of a provider required?
In regards to Terraform state file, select all the statements below which are correct: (select four)
You are deploying Vault in a local data center, but want to be sure you have a secondary cluster in the event the primary cluster goes offline. In the secondary data center, you have applications that are running, as they are architected to run active/active. Which type of replication would be best in this scenario?
You've set up multiple Vault clusters, one on-premises which is intended to be the primary cluster, and the second cluster in AWS, which was deployed to be used for performance replication. After enabling replication, developers complain that all the data they've stored in the AWS Vault cluster is missing. What happened?
True or False? By default, Terraform destroy will prompt for confirmation before proceeding.
While Terraform is generally written using the HashiCorp Configuration Language (HCL), what another syntax can Terraform be expressed in?
True or False:
Once you create a KV v1 secrets engine and place data in it, there is no way to modify the mount to include the features of a KV v2 secrets engine.
After a client has authenticated, what security feature is used to make subsequent calls?
What Terraform feature is shown in the example below?
1. resource "aws_security_group" "example" {
2. name = "sg-app-web-01"
3. dynamic "ingress" {
4. for_each = var.service_ports
5. content {
6. from_port = ingress.value
7. to_port = ingress.value
8. protocol = "tcp"
9. }
10. }
11. }
When Vault is sealed, which are the only two options available to a Vault administrator? (select two)
What could you do with the feature found in the screenshot below? (select two)
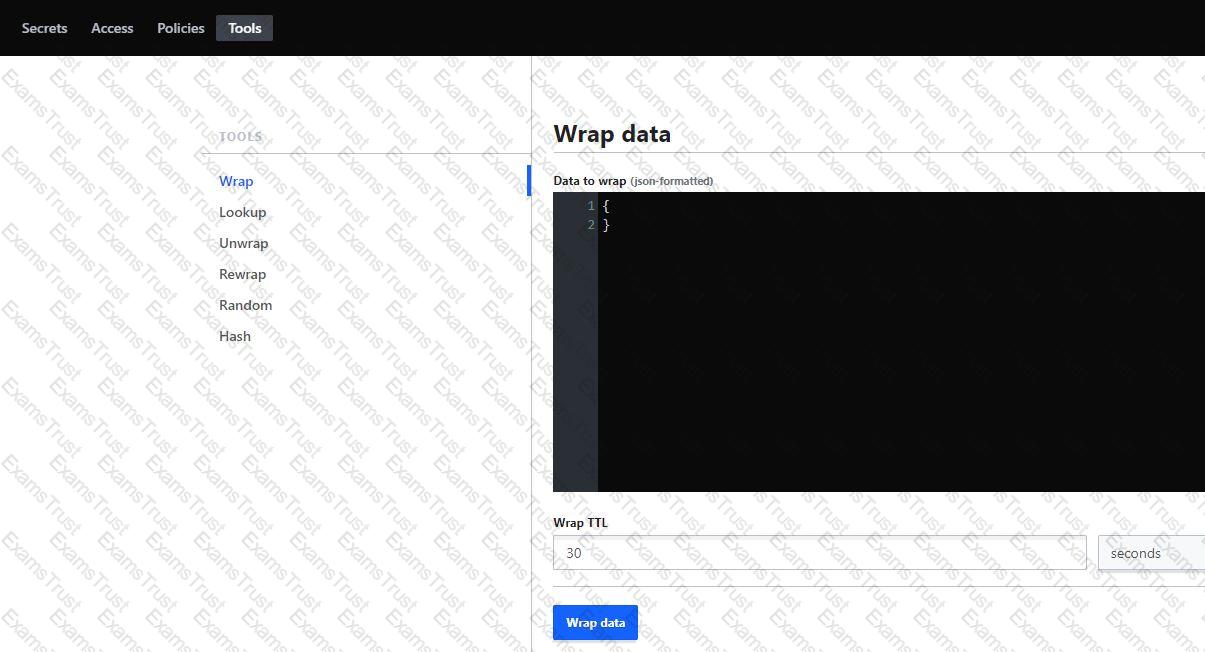
Why might a user opt to include the following snippet in their configuration file?
1. terraform {
2. required_version = ">= 0.12"
3. }
True or False:
The terraform refresh command is used to reconcile the state Terraform knows about (via its state file) with the real-world infrastructure. If the drift is detected between the real-world infrastructure and the last known-state, it will modify the infrastructure to correct the drift.
Which type of Vault replication copies all data from Vault, including K/V data, policies, and client tokens?
What happens when a terraform plan is executed?
Terraform has detailed logs which can be enabled by setting the _________ environmental variable.
After encrypting data using the transit secrets engine, you've received the following output. Which of the following is true based upon the output?
1. Key Value
2. --- -----
3. ciphertext vault:v2:45f9zW6cglbrzCjI0yCyC6DBYtSBSxnMgUn9B5aHcGEit71xefPEmmjMbrk3
An application is trying to use a secret in which the lease has expired. What can be done in order for the application to successfully request data from Vault?
Environment variables can be used to set variables. The environment variables must be in the format "____"_
An application requires a specific key/value to be updated in order to process a batch job. The value should be either "true" or "false". However, when developers have been updating the value, sometimes they mistype the value or capitalize on the value, causing the batch job not to run. What feature of a Vault policy can be used in order to restrict the entry to the required values?
Which of the following connection types are supported by the remote-exec provisioner? (select two)
What feature of Terraform Cloud and/or Terraform Enterprise can you publish and maintain a set of custom modules which can be used within your organization?
Select all features which are exclusive to Terraform Enterprise. (select three)
In the example below, the depends_on argument creates what type of dependency?
1. esource "aws_instance" "example" {
2. ami = "ami-2757f631"
3. instance_type = "t2.micro"
4. depends_on = [aws_s3_bucket.company_data]
5. }