Which of the following classes will you use to specify that a string must be centered when drawn?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to attach the Visual Studio Debugger to Internet Explorer when the application is running. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
In .NET Framework 3.5, you can create and access values that persist from one application session to another. What are these values called?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You create a Web service using .NET Framework 2.0. You want the Web service to utilize a two step process to map XML generated by Web methods to .NET objects. What will you do to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
Henry works as a Software Developer for SoftTech Inc. He creates a Windows form named
MyForm1. The form contains detailed information about a student. The form uses a ListBox control named ListBox1 that concatenates two strings displayed in two TextBox controls. Henry wants a method to return a value for the control. Which of the following options will he consider while creating a method for the control?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You have recently finished the development of an ASP.NET Web application using .NET Framework 3.5. The application must be deployed by using the URL. The application has several Web forms.
You need to implement Really Simple Syndication (RSS) feeds functionality. The RSS feeds will be used by the URL. You must ensure that the application displays the RSS-formatted information when accessing the given URL. What will you do to accomplish this?
Each correct answer represents a part of the solution. Choose two.
Patrick works as a Software Developer for GenTech Inc. He develops an application, named App1, using Visual C# .NET. He implements security using the security classes of the .NET Framework. He defines the following statements in the application:
PrincipalPermission Principal_Perm1 = new PrincipalPermission("Nick", "General
Manager");
PrincipalPermission Principal_Perm2 = new PrincipalPermission("Jack", "Accountant");
Patrick wants to check whether all demands that succeed for Principal_Perm1 also succeed for Principal_Perm2. Which of the following methods of the PrincipalPermission class will he use to accomplish this?
Which of the following is not a type of Remote object?
Andrew works as a Software Developer for Mansoft Inc. The company's network has a Web server that hosts the company's Web site. Andrew wants to enhance the security of the Web site by implementing Secure Sockets Layer (SSL). Which of the following types of encryption does SSL use?
Each correct answer represents a complete solution. Choose two.
John works as a Web Developer for ABC Inc. He develops an ASP.NET application, named MyApp1, using Visual Studio .NET. The application will be used in the Sales department to generate monthly reports. John wants to deploy the application on the company's intranet. The company uses Microsoft Windows authentication. John wants to deny access to all the members of the Guest1 role. Which of the following attributes will he use in the <authorization> element of the application's Web.config file to accomplish the task?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to redirect users to a default error page if an unhandled error occurs within your site. Which of the following actions will you perform to accomplish the task?
You work as a Software Developer for InfoTech Inc. You create a Windows form in a Windows-based application named MyWinApp1. You use graphics in the form. You write the following code in your form:
private void MyMouseEvent1(object sender1, MouseEventArgs event)
{
// Code to handle mouse events
}
You want to implement a property of the MouseEventArgs object. This property will return a Point structure that contains the x-coordinate and y-coordinate of the mouse. Which of the following properties of the MouseEventArgs object will you use to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a class library using the .NET Framework. The library will be used to open the NSCs of computers. Later, you will set up the class library to the GAC and provide it Full Trust permission. You write down the following code segments for the socket connections:
SocketPermission permission = new SocketPermission(PermissionState.Unrestricted);
permission.Assert(); A number of the applications that use the class library may not have the necessary permissions to open the network socket connections. Therefore, you are required to withdraw the assertion. Which of the following code segments will you use to accomplish the task?
Which of the following attributes of the customErrors element is used to specify whether custom errors are enabled, disabled, or shown only to remote clients?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You are creating an ASP.NET Web application using the .NET Framework 3.5. The application stores sensitive profile data in a MS SQL Server 2008 database. You are required to make sure that the profile data never stored in clear text. What will you do?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be deployed on an intranet server of the company. You require that the application meets the following requirements:
l Users can log on to the application by using their Active Directory credentials.
l Each Web page in the application must display user name and password controls for an unauthenticated user.
What will you do to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be used to share any type of photos on Internet. All the photos should be accessible in various sizes and formats. You need to add a download feature that can be easily maintained. You also need to make sure that only a single version of all photos is stored on a SQL server database. What will you do?
Ross works as a Software Developer for GenTech Inc. He develops a Windows-based application using Visual Studio .NET. He uses the Write method of the Debug and Trace classes to record information about the execution of the application in Windows 2000 event log. Ross performs integration testing on the application. He wants to ensure that only one entry is made to the event log, each time a call is made to the Write method of either class. Which of the following code will he use to accomplish this?
Each correct answer represents a complete solution. Choose two.
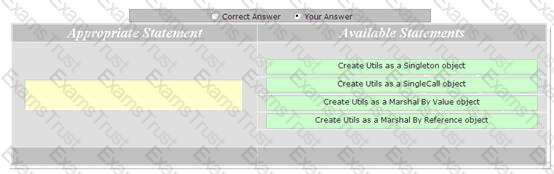
You work as a Software Developer for ABC Inc. You create an application, and you want to define a component for your application. In some deployments, the component will be deployed on the same computer as the application. In other deployments the component will be deployed on a separate computer. You create a Web service. You want a new object of the Web service to be created whenever a customer makes a call to the Web service. Drag and drop the appropriate statement to accomplish the task.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows application using .NET Framework 3.5. The application will process one million records in a production environment. Therefore, you need to test the application by using 7,500 records in a limited test environment to identify potential problems that might arise when the application is moved to the production environment. What will you do?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are in the process of creating an application that will handle unmanaged code using the .NET Framework 2.0. Which of the following services will you use to provide interoperability with the unmanaged code?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is used to place an assembly on the intranet. Which of the following classes will you use to test whether or not an assembly was located on the intranet?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. You are using regular expression in the application to validate email, phone number, etc. You are required to match a Unicode character using hexadecimal numbers. Which of the following character escapes will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company has several branches Worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an applications using .NET Framework 2.0. You want to allow users to view various details of a given unmanaged code. What will you do to accomplish the task?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using the .NET Framework.. He writes the following code segment in the application:
01 class gClass
02 {
03 public gClass(int k)
04 {
05 //Write code here
06 }
07 }
08 public class gSub : gClass
09 {
10 public static void Main(String[] argv)
11 {
12 gSub gs=new gSub(20);
13 }
14 gSub(int j):base(j)
15 {
16 //Write Code here
17 }
18 gSub(string st, int j):this(j)
19 {
20 gClass ss=new gClass();
21 }
22 }
When you execute the above code segment, you get an error at line 20. Which of the following code segments will he place at line 20 to execute the code successfully?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You are creating an ASP.NET Web application using the .NET Framework 3.5. The application stores sensitive profile data in a MS SQL Server 2008 database. You are required to make sure that the profile data never stored in clear text. What will you do?
Mark works as a Software Developer for McRobert Inc. He develops an ASP.NET application, named App1, using Visual Studio .NET. App1 retrieves purchase orders data from a SQL Server database and displays it in a DataGrid control, named DataGrid1. Mark wants to enable users to sort data in ascending or descending order, whenever they click a column. He writes code to sort the data in DataGrid1 using the SortOrder property. The SortOrder property stores a value "ASC" for ascending order and "DESC" for descending order. Mark wants to preserve the value during postbacks. Which of the following properties of the Control class will Mark use to accomplish this?
Allen works as a Software Developer for ManSoft Inc. He uses Microsoft Visual Studio 2005 to create a Web service named MyWebService. He wants to create a policy file with the help of WSE 3.0, which makes creating policy assertions files fairly straightforward. A policy assertion is a combination of the capabilities and requirements of the Web service. Allen initially writes the following steps to create and implement a policy file:
l He creates a stud to hold the policy elements. This task is accomplished by creating a config file known as a policy file or a policy cache file.
l He creates a set of policy assertions. There exists a set of assertions that can be used.
l He references the policy file from the application configuration file.
After completing these steps, the structure of the policy file is created. Now, he wants to use the structure of the policy file to inject input filters, output filters, or both, into the processing pipeline.
Which of the following policy file structures will Allen use to accomplish the task?
You work as an ADO.NET Application Developer for ABC Inc. The company uses Microsoft Visual Studio .NET 2008 as its application development platform. You create an ADO.NET application by using .NET Framework 3.5. You are using the System.Linq.Expressions namespace. You need to specify an expression that applies a delegate or lambda expression to a list of argument expressions. Which of the following classes will you use to accomplish the task?
You work as a Software Developer for ABC Inc. You develop a Windows application named
MyApp1. MyApp1 contains a Windows form named MyWinForm1. The form uses several controls such as Button, TextBox, and Label. You want mouse click events to be raised in the form. You want to use the mouse events that pass an instance of EventArgs in the signature of the event handler of a Button control. Which of the following events will you use in the application to accomplish the task?
Each correct answer represents a complete solution. Choose three.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an assembly. The assembly contains a public method. The Global Assembly Cache contains a second assembly. You require that the public method is only called from the second assembly. Which of the following permission classes will you use to accomplish this task?
Mark works as a Software Developer for ABC Inc. He is participating in designing a .NET remoting component for an application that will be hosted on a load-balanced farm. For this, he creates a .NET remote object using Visual Studio .NET 2005. The .NET remote object is used to modify properties of a class. The class contains twenty properties. The .NET remote object is frequently used by client applications. He wants to minimize the network traffic. Which of the following actions will he take to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application can be run only by a specific set of user credentials. Therefore, other applications are not permitted to employ these user credentials. The ASP.NET application uses asymmetric encryption to encrypt and decrypt messages to other servers. You are required to shield the private key that is used to encrypt and decrypt messages that are accessed by other users or applications on the same server. What will you do to accomplish the task?
You work as a Software Developer for SunSoft Inc. The company uses Visual Studio .NET 2005 as its application development platform. You use .NET Framework 2.0 to create several Windows applications. All applications use a common class library assembly named Customers. You deploy the application to the client computers on your company's intranet. Later, you modify the assembly. Any application that uses version 1.0.0.0 must now use version 2.0.0.0. Which of the following options will you use to accomplish the task?
You work as an Enterprise Application Developer for Mansoft Inc. You are participating in the
design for a Web-based Order Management System. There are a few configuration options, such as applicable tax percentage, repeat customer discount percentage, etc., which are applicable to all the users of the Order Management System. However, these configuration options might be changed in the future. Which of the following techniques will you use to maintain this information from the performance and maintenance point of view?
You work as a Software Developer for ABC Inc. The company has several branches worldwide.
The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
You work as a Software Developer for InfoTech Inc. You create a Windows form in a Windows-based application named MyWinApp1. You use graphics in the form. You write the following code in your form:
private void MyMouseEvent1(object sender1, MouseEventArgs event)
{
// Code to handle mouse events
}
You want to implement a property of the MouseEventArgs object. This property will return a Point structure that contains the x-coordinate and y-coordinate of the mouse. Which of the following properties of the MouseEventArgs object will you use to accomplish this?
Robert works as a Software Developer for InfoTech Inc. He develops an application named MyApp that uses SQL Server database and three database components. He wants to ensure that other developed applications cannot use these database components. Users should be authorized before they can access these components. Robert configures the database component assemblies to accomplish this task. Choose the correct actions that Robert should take after the configuration.
Sam works as a Software Developer for BlueWell Inc. He creates a .NET Remoting object named MyObj using Visual Studio .NET. He wants to configure MyObj to send and receive confidential information from an XML file stored in an encrypted hard drive. What will he do to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
Charles works as a Web Developer for TechNet Inc. He develops an application named AdAgentsApp for advertising agents by using Visual Studio .NET. AdAgentsApp uses several Web services provided by the company. The employees in the IT department use only the existing port numbers 80 (HTTP protocol) and 443 (HTTPS protocol) for firewall security. However, they are forbidden to open any other new ports. These ports have been used to ensure the highest security level of authentication.
Which of the following actions should Charles take to maintain the highest security?
Each correct answer represents a part of the solution. Choose two.
Andrew works as a Software Developer for BlueWell Inc. He develops a Windows-based application, named App1, using Visual Studio .NET. The application uses Microsoft SQL Server as a backend database. Andrew wants to perform security checks on App1. Which of the following statements regarding security checks are true?
Each correct answer represents a complete solution. Choose two.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application needs a thread that accepts an integer parameter. You write the following code segment in the application:
Thread myThread = new Thread(new ParameterizedThreadStart(doWork));
myThread.Start(125);
You are required to declare the signature of the doWork method. Which of the following method signatures will you use?
You work as a Software Developer for Mansoft Inc. You create an application and use it to create users as members of the local Users group. Which of the following code snippets imperatively demands that the current user is a member of the local Users group?
Each correct answer represents a complete solution. Choose all that apply.
Sam works as a Software Developer for SamTech Inc. He develops a Windows-based application, named App1, using Visual Studio .NET. He wants to set a security policy for the application. To accomplish the task he uses the PolicyLevel class. He wants to set the current policy level to the default state. Which of the following methods will he use to accomplish the task?
Samantha works as a Software Developer for InfoWorld Inc. She develops a Web page named SalesReport.aspx for the employees of the company. However, she wants to ensure that all the requests for a particular employee are not stored on the server's memory. She also wants to ensure that no data is lost even after each user session has expired. Which of the following actions will Samantha take to accomplish the task?
Daniel works as a Software Developer for GenTech Inc. He develops an ASP.NET application, named
App1, using Visual Studio .NET. He creates an interface in App1, named Employees. The Employees interface contains declaration for a method, named Method1. Daniel creates another interface, named HeadOfDept. HeadOfDept inherits from the Employees interface and contains the declaration for a method, named Method2. He then creates a class named Manager as follows:
public class Manager : HeadOfDept
Which of the following statements about the application are true?
Each correct answer represents a complete solution. Choose all that apply.
Allen works as a Software Developer for Mansoft Inc. He develops an application using Visual Studio .NET 2005. The application connects to a SQL Server database using a SqlConnection object named NewConnection. Allen creates a few stored procedures in the database. Sometimes an error occurs, when a user executes stored procedures. Allen wants to add an error-handling code to the application to handle errors that occur on executing stored procedures. Which of the following code segments will he use to accomplish this task?
Allen works as a Software Developer for ABC Inc. He develops an application using Visual Studio .NET
2005. The application will be used for the registration of employees by filling a form provided in the application. The form contains the following fields:
l First Name
l Last Name
l Date of Birth
l E-mail
He provides a TextBox control for each field. He wants an employee to be able to receive a user-defined error message when he makes a wrong entry. Which of the following properties is mandatory if a
CustomValidator control is used to validate an entry?
Dennis works as a Software Developer for BlueWell Inc. He develops an application, named App1, using Visual C# .NET. App1 contains a class, named Class1, which is stored in a namespace, named BlueWell.Namespace1. Dennis wants to create another class, named Class2, and use Class1 from Class2. For this, he wants to define an alias, named Alias1, and use it in Class2.
Which of the following statements will Dennis use to define Alias1?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an application using the .NET Framework. The application contains a class named globalInfo. You need to serialize all public and nonpublic data of the globalInfo class to ensure that the class generates the minimum byte stream so that the minimum load is placed upon network resources. What will you do?
Mark works as a Software Developer for McRobert Inc. He develops an ASP.NET application using Visual Studio .NET. The application loads department name and employee data only once in each user's session. Mark creates two DataTable objects, named Employees and Departments. The
Departments object remains static, but the Employees object is modified whenever new employees join the company.
Mark wants to minimize the time it takes for the application to reload an ASP.NET page after each change. Which of the following statements will he use to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is using an assembly. You want to ensure that the application provides the best performance. Security is not a consideration. Which of the following permission sets will you use to accomplish the task?
Maria works as a Software Developer for BlueWell Inc. She develops an application, named App1, using Visual C# .NET. App1 contains a Form control, named Form1, for collecting users' contact information. Form1 contains a TextBox control, named TextBox1. App1 requires users to enter data in TextBox1. Maria writes a method, named Method1, to validate the entered data. She adds an ErrorProvider control, named Control1, to Form1. Maria wants to ensure that App1 notifies the users if they enter invalid data in TextBox1. Which of the following code will she use to accomplish this?
Maria works as a Software Developer for MarcLync Inc. She creates an XML Web service, named MyWebService, using Visual Studio .NET. Maria wants to debug MyWebService. Therefore, she attaches a debugger to the Web service process. However, Maria notices that whenever MyWebService is executed, it throws an exception System.Net.WebException after a certain time period. The exception displays the message "The current operation has timed-out." Maria wants to modify the code in MyWebService. Which of the following actions will Maria take in order to resolve this issue?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are presently busy implementing a custom trace that logs errors and warnings in a MS SQL Server database. The implementation should allow different applications to decide whether errors or warnings should be logged at a specified time. You install the assembly that contains the trace listener in the GAC on an application server. You want to enable all Web services on the application server to utilize the trace listener by default. You need to ensure that the implementation does not force Microsoft Windows Forms applications that run on the server to utilize the trace listener. What will you do to accomplish this task?
Each correct answer represents a part of the solution. Choose two.
You work as an Application Developer for ABC. The company uses Visual Studio .NET Framework 3.5 as its application development platform. You are working on enhancements to an existing WPF application. One problem you have been encountering is that users of the current version routinely enter invalid data, and since the controls use data binding, that data either gets put in the database incorrectly, or in some cases generates a database error. You want to incorporate validation with your data bound controls. Which of the following choices is the best way to accomplish this goal?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using the .NET Framework. You create a database to maintain the record of the students. You create a table named Student. You want to retrieve names and roll number of those students whose age is less than ten years. An instance of the SqlCommand class named StudentCommand is already created. Which of the following code segments should you use to execute the query?
Sandra works as a Software Developer for ABC Inc. She develops an application named MyApp that contains a data-bound control named MyDataControl. She wants to use an Oracle database in order to bind data to MyDataControl. Which of the following GUI-based data sources will Sandra use to accomplish the task?
You work as a Software Developer for ABC Inc. You use C# .NET to develop a windows application. The application will implement a role-based authorization scheme that is based on a Microsoft SQL Server database of user names. Users will enter their names in a text box named UserName. You must ensure that users are assigned the supervisor role and the PG role by default. Which of the following code segments will you use to accomplish this task?
Martha works as a Software Developer for NetCom Inc. She develops an application, named App1, using Visual Studio .NET. The application contains a form, named MyForm1. MyForm1 contains several controls including a TextBox, named txtDOB. The txtDOB control is used to accept the date of birth from a user. In order to ensure that a user enters a valid date in txtDOB, Martha adds validation logic to the Validating event of txtDOB. When she tests the form by using some invalid dates in txtDOB, the validation logic does not appear to be working as expected. What is the most likely cause of the issue?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. The application is used to map HTTP requests to HTTP handlers based on a file name extension. You need to ensure that each HTTP handler processes individual HTTP URLs or groups of URL extensions in the application.
Which of the following built-in HTTP handlers will you use to accomplish this task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You need to read the entire contents of a file named Msg.txt into a single string variable using .NET Framework. Which of the following code segments will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are developing an application that manages sports teams. When a user queries details about a particular team, the id and name of each member of the team must be stored as a single collection. You must create the collection of team members in the most efficient manner, in a manner that guarantees type safety, and in a manner that will require the least amount of code to retrieve and work with the data in the collection. Which code segment should you choose?
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You create an application that will be used by all the branches of the company. You use the Regex class in the application to validate some strings. You want to search an input string for an occurrence of a regular expression. Which of the following methods of the Regex class will you use to accomplish the task?
Maria works as a Software Developer for BlueWell Inc. She develops an application, named App1, using Visual C# .NET. The application displays employee details from a SQL Server database. Maria wants to use a string array, named MyArray, in the application code to store employee names. Which of the following statements will she use to declare MyArray?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application has multiple threads that execute one after another. You want to ensure that the application terminates only when all the threads complete their tasks. Which of the following methods will you use to accomplish the task?
Lewis works as a Web Developer for TechNet Inc. He develops an ASP.NET application named App1 by using Visual Studio .NET. Lewis wants to allow everyone access to the application. However, he does not want to implement any type of Windows authentication. Which of the following authentication methods will he use to accomplish this task?
Roger works as a Software Developer for BlackWell Inc. He develops an application, named MyApplication1, using Visual Studio .NET. The application contains a form, named MyForm1, which will be used to set a password for a user. A password allotted to a user will be case-sensitive. MyForm1 contains several controls including two TextBox controls, named txtPassword and txtConfirm, respectively. The txtMyPassword control is used to accept a string from a user. The string entered in txtPasword will be used as the password for the user. In txtConfirm, the user has to retype the string that he enters in txtPassword. This will ensure that there are no typing errors. MyForm1 also contains a Button control, named cmdSetPassword, which when clicked will set the password for the user.
Before setting the password for a user, Roger wants to ensure that the two text boxes contain the same string. In order to accomplish this, he decides to use the StrComp function. The password for a user can only be set if the StrComp function returns 0. He has not used an Option Compare statement in the code. Which of the following statements can Roger use to compare the two strings?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create the definition for a Car class by using the following code segment:
public class Car {
[XmlAttribute(AttributeName = "category")]
public string CarType;
public string model;
[XmlIgnore]
public int year;
[XmlElement(ElementName = "mileage")]
public int miles;
public ConditionType condition;
public Car() {
}
public enum ConditionType {
[XmlEnum("Poor")] BelowAverage,
[XmlEnum("Good")] Average,
[XmlEnum("Excellent")] AboveAverage
}}
You create an instance of the Car class. You fill the public fields of the Car class as shown in the table below:
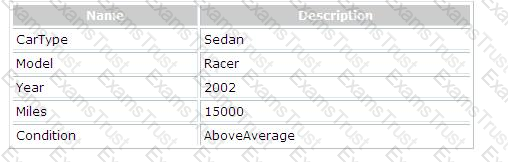
You are required to recognize the XML block that is produced by the Car class after serialization. Which of the following XML blocks represents the output of serializing the Car class?
You are working on an ASP.NET application that will handle shopping cart for online users. You wish to generate images of all your company's products dynamically on one of the application's Web pages. You need to modify your configuration settings file for this purpose. Which of the following sections of the configuration file will you use to accomplish the task?