Which of the following options is an approach to restricting system access to authorized users?
Which of the following is the rating for gasoline or oil fires?
Which networking protocol is used to authenticate users or devices before granting them access to a network?
A user has opened a Web site that automatically starts downloading malicious code onto his computer.
What should he do to prevent this?
Each correct answer represents a complete solution. Choose two.
Which of the following protocols uses a combination of public key and symmetric encryption to provide communication privacy, authentication, and message integrity for secure browsing on the Internet?
Which of the following viruses replaces the boot sector data with its own malicious code?
Which of the following is a software testing method that uses an internal perspective of the system to design test cases based on the internal structure?
You are concerned about attackers simply passing by your office, discovering your wireless network, and getting into your network via the wireless connection. Which of the following are NOT steps in securing your wireless connection?
Each correct answer represents a complete solution. Choose two.
Which of the following records is the first entry in a DNS database file?
Which of the following is the default security level for the Internet zone?
Which type of repudiation states that the creator of the message denies ever creating the message even after creating it?
Which of the following is NOT a principle and practice of the 'Minimize the number of highconsequence targets' principle?
What does noise in a power line indicate?
Which of the following is a popular replacement for halon gas?
Which of the following is used for high-level or comprehensive analysis, as well as for root cause analysis?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
• HTTP
• SSL
• SSH
• IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
Which of the following is a structured review of the procurement process originated at the Plan Procurements process?
Which of the following encrypts its code differently with each infection or generation of infections?
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
Which of the following programs collects email addresses of users and creates a mailing list?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 Active Directory domain-based network. The domain consists of four domain controllers, six Windows 2003 member servers, and 500 Windows XP Professional client computers. The PKI infrastructure is already configured on the network. The current configuration of the network allows only managers to use EFS on local computers. Sometimes Mark faces problems when managers lose their private keys due to the user profile becoming corrupt or being lost. Due to this, the files that were persistently encrypted by using the corresponding public key are inaccessible. He wants to restore access to the encrypted files as quickly as possible. What will he do to accomplish the task?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. Rick, your assistant, is configuring some laptops for wireless access. For security, WEP needs to be configured for wireless communication. By mistake, Rick configures different WEP keys in a laptop than that is configured on the Wireless Access Point (WAP). Which of the following statements is true in such situation?
Which of the following statements are true about SSIDs?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following malware spread through the Internet and caused a large DoS attack in 1988?
You work as a Software Developer for PassGuide Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. You use the application to create an assembly. Now you need to encrypt assembly data. The company has not provided encryption requirements to you. Which of the following symmetric cryptography classes will you use to accomplish this task?
Which of the following attributes is a tool that does not aid the project manager in quality planning?
Which of the following functions can you use to mitigate a command injection attack?
Each correct answer represents a complete solution. Choose all that apply.
Maria works as the Chief Security Officer for PassGuide Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The company's network is connected to the Internet through a T1 line. The firewall is configured on the network for securing the internal network from the intruders on the Internet. The functional level of the forest is Windows Server 2008. You are designing a public key infrastructure (PKI) for the network. The network will use a root enterprise certificate authority (CA) and a subordinate CA. The root CA will be used to issue certificates to the subordinate CA, and the subordinate CA will be used to issue certificates to the clients.
The management of the company wants to ensure that the security of high-level CAs is not compromised. Which of the following steps will you take to accomplish the task?
Which of the following tools can be used to read NetStumbler's collected data files and present street maps showing the logged WAPs as icons, whose color and shape indicates WEP mode and signal strength?
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
A project team member has just identified a new project risk. The risk event is determined to have significant impact but a low probability in the project. Should the risk event happen it'll cause the project to be delayed by three weeks, which will cause new risk in the project. What should the project manager do with the risk event?
You discover that all available network bandwidth is being used by some unknown service. You discover that UDP packets are being used to connect the echo service on one machine to the chargen service on another machine. What kind of attack is this?
John is a malicious attacker. He illegally accesses the server of We-are-secure Inc. He then places a backdoor in the We-are-secure server and alters its log files. Which of the following steps of malicious hacking includes altering the server log files?
Which of the following security protocols can be used to support MS-CHAPv2 for wireless client authentication?
Each correct answer represents a complete solution. Choose two.
Adam works as a Penetration Tester for Umbrella Inc. He is assigned a project of testing the security of the company's network. He is using the Metasploit Framework for developing and executing exploit code against a remote target machine. The Metasploit Framework is the important sub-project of the Metasploit Project. Which of the following are the other sub-projects under the Metasploit projet?
Each correct answer represents a complete solution. Choose all that apply.
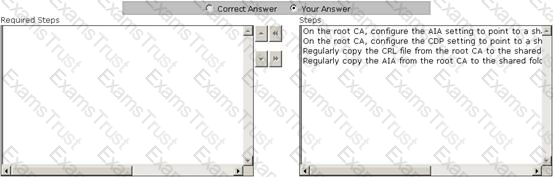
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. All client computers on the network run Windows XP Professional. You configure a public key infrastructure (PKI) on the network. You configure a root CA and a subordinate CA on the network. For security reasons, you want to take the root CA offline. You are required to configure the CA servers to support for certificate revocation. Choose the steps you will require to accomplish the task.
Which of the following types of virus is capable of changing its signature to avoid detection?
Which of the following types of firewall ensures that the packets are part of the established session?
Which of the following attacks can be mitigated by providing proper training to the employees in an organization?
Which of the following statements correctly defines a script kiddie?
Rick is the project manager for TTM project. He is in the process of procuring services from vendors. He makes a contract with a vendor in which he precisely specify the services to be procured, and any changes to the procurement specification will increase the costs to the buyer. Which type of contract is this?
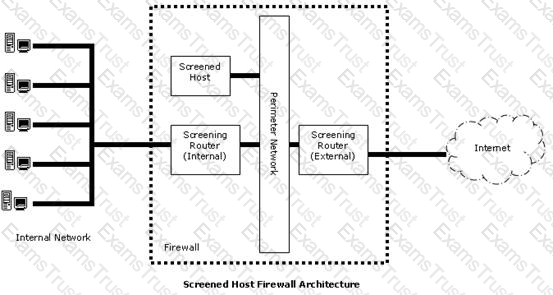
In the image of the Screened Host Firewall Architecture given below, select the element that is commonly known as the access router.
You work as Network and Security Manager for PassGuide Inc. The management of the company is quite concerned about the security of the network. The management has assigned this task to you to improve the security. Which of the following access methods will you use if the method is to be primarily based on pre-established access, and users cannot change it?
IDS systems can be classified in many different ways. Which of the following is not a way that IDS systems are commonly classified?
One of the sales people in your company complains that sometimes he gets a lot of unsolicited messages on his PDA. After asking a few questions, you determine that the issue only occurs in crowded areas like airports. What is the most likely problem?
You work as an Administrator for Bluesky Inc. The company has 145 Windows XP Professional client computers and eighty Windows 2003 Server computers. You want to install a security layer of WAP specifically designed for a wireless environment. You also want to ensure that the security layer provides privacy, data integrity, and authentication for client-server communications over a wireless network. Moreover, you want a client and server to be authenticated so that wireless transactions remain secure and the connection is encrypted. Which of the following options will you use to accomplish the task?
John works as a Website Administrator in ABC Inc. The company has to set a privacy policy on all the computers. The policy requires John to restrict only third party cookies that do not have a compact private policy or that use personally identifiable information without a user's implicit consent. He reports to the Technical Support Executive that he wants to set the policy. The Technical Support Executive asks him to configure the settings in the Privacy tab page. Which of the following privacy settings will John use to accomplish the task?
You are responsible for security at a company that uses a lot of Web applications. You are most concerned about flaws in those applications allowing some attacker to get into your network. What method would be best for finding such flaws?
Wired Equivalent Privacy (WEP) is a security protocol for wireless local area networks (WLANs). It has two components, authentication and encryption. It provides security equivalent to wired networks for wireless networks. WEP encrypts data on a wireless network by using a fixed secret key. Which of the following statements are true about WEP?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the practice of a domain name registrant using the five-day "grace period" (the Add Grace Period or AGP) at the beginning of the registration of an ICANN-regulated second-level domain to test the marketability of the domain?
Which of the following statements is true about the difference between worms and Trojan horses?
You work as an Incident handling manager for Orangesect Inc. You detect a virus attack incident in the network of your company. You develop a signature based on the characteristics of the detected virus. Which of the following phases in the Incident handling process will utilize the signature to resolve this incident?
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
What is the term used to describe the cost of the solution after the solution has been implemented in production by a vendor?
Which of the following statements are true about MS-CHAPv2?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. The domain functional level is set to Windows Server 2003. You have configured an Active Directory-integrated DNS zone on the network. A new security policy dictates that each incoming DNS query should be recorded. Which of the following steps will you take to implement the new security policy?
Which of the following items are generally analyzed by Internet filters?
Each correct answer represents a complete solution. Choose three.
Which of the following are types of social engineering attacks?
Each correct answer represents a complete solution. Choose two.
Which of the following terms describes the statement given below?
"It refers to a range of skills, tools, and techniques used to manage time when accomplishing specific tasks, projects, and goals. This set encompasses a wide scope of activities, and these include planning, allocating, setting goals, delegation, analysis of time spent, monitoring, organizing, scheduling, and prioritizing."
Which of the following processes is NOT a part of the Project Procurement Management Knowledge Area?
John works as a Programmer for We-are-secure Inc. On one of his routine visits to the company, he noted down the passwords of the employees while they were typing them on their computer screens.
Which of the following social engineering attacks did he just perform?
Which of the following is used to describe the type of FTP access in which a user does not have permissions to list the contents of directories, but can access the contents if he knows the path and file name?
Fill in the blank with the appropriate term.
NOTE. Do not use abbreviation.
________ is a configurable client identification that allows a client to communicate with a particular base station.
Which of the following activities result in change requests?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following exists between the client and the server system to provide security and allows customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application layer protocols?
Which of the following protocols uses a combination of public key and symmetric encryption to provide communication privacy, authentication, and message integrity for secure browsing on the Internet?
You and your project team have identified the project risks and now are analyzing the probability and impact of the risks. What type of analysis of the risks provides a quick and high-level review of each identified risk event?
Which of the following tools can be used to detect the steganography?
You are the Network Administrator for a large corporate network. You want to monitor all network traffic on your local network for suspicious activities and receive a notification when a possible attack is in process. Which of the following actions will you take for this?
John works as an IT Technician for PassGuide Inc. One morning, John receives an e-mail from the company's Manager asking him to provide his logon ID and password, but the company policy restricts users from disclosing their logon IDs and passwords. Which type of possible attack is this?
You have configured a virtualized Internet browser on your Windows XP professional computer. Using the virtualized Internet browser, you can protect your operating system from which of the following?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of He receives the following e-mail:
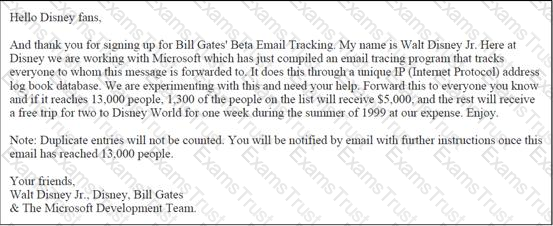
The e-mail that John has received is an example of __________.
You have been hired as a project manager for a project. The initial project planning predicts a benefitcost ratio (BCR) of the project as 3.5. What does this figure mean?
You are working on your computer system with Linux Operating system. After working for a few hours, the hard disk goes to the inactive state (sleep). You try to restart the system and check the power circuits. You later discover that the hard disk has crashed. Which of the following precaution methods should you apply to keep your computer safe from such issues?
Which of the following techniques is based on a set of criteria that has been acquired in a specific knowledge area or product area?
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest network. You have recently added three new SCSI hard disk drives to a domain controller that already has two physical disk drives. The new SCSI disk drives are configured in a RAID-5 array. You are required to enhance the performance of the Active Directory database on the domain controller. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
Which of the following are the benefits of information classification for an organization?
Each correct answer represents a complete solution. Choose two.
Which of the following statements are true about locating rogue access points using WLAN discovery software such as NetStumbler, Kismet, or MacStumbler if you are using a Laptop integrated with Wi-Fi compliant MiniPCI card?
Each correct answer represents a complete solution. Choose two.
You are the Network Administrator for a company that does a large amount of defense contract business.
A high level of security, particularly regarding sensitive documents, is required. Which of the following steps will you take to secure network printers?
Each correct answer represents a complete solution. Choose two.
Management has asked you to perform a risk audit and report back on the results. Bonny, a project team member asks you what a risk audit is. What do you tell Bonny?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You are working as a root user on the Linux operating system. Your company is facing an IP spoofing attack. Which of the following tools will you use to get an alert saying that an upcoming IP packet is being spoofed?
Which of the following files must be configured to enable hostname lookups to use the Domain Name Service (DNS)?
John works as a Security Administrator for Enet Inc. He uses a 4 digits personal identification number (PIN) to access the computer and a token is used to perform offline checking whether John has entered the correct PIN or not. Which of the following attacks is possible on John's computer?