When you log into your Windows desktop what information does your Security Access Token (SAT) contain?
Which of the following Linux commands can change both the username and group name a file belongs to?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You are required to search for the error messages in the /var/log/messages log file. Which of the following commands will you use to accomplish this?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. He is working as a root user on the Linux operating system. He wants to delete his private.txt file from his operating system. He knows that the deleted file can be recovered easily. Hence, he wants to delete the file securely. He wants to hide the shredding, and so he desires to add a final overwrite of the file private.txt with zero. Which of the following commands will John use to accomplish his task?
What is the fundamental problem with managing computers in stand-alone Windows workgroups?
Which of the following attack vectors are addressed by Xinetd and TCP Wrappers?
One of your Linux systems was compromised last night. According to change management history and a recent vulnerability scan, the system's patches were up-to-date at the time of the attack. Which of the following statements is the Most Likely explanation?
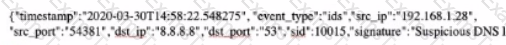
Which of the following is a benefit to utilizing Cygwin for Windows?
You have set up a local area network for your company. Your firewall separates your network into several sections: a DMZ with semi-public servers (web, dns, email) and an intranet with private servers. A penetration tester gains access to both sections and installs sniffers in each. He is able to capture network traffic for all the devices in the private section but only for one device (the device with the sniffer) in the DMZ. What can be inferred about the design of the system?
Which Defense-in-Depth principle starts with an awareness of the value of each section of information within an organization?
Use sudo to launch Snort with the, /etc /snort /snort.conf file In full mode to generate alerts based on incoming traffic to echo. What is the source IP address of the traffic triggering an alert with a destination port of 156?
Note: Snort Is configured to exit after It evaluates 50 packets.

Which of the following SIP methods is used to setup a new session and add a caller?
Which of the following Unix syslog message priorities is the MOST severe?
Which of the following defines the communication link between a Web server and Web applications?
The process of enumerating all hosts on a network defines which of the following activities?
Which logging capability is provided natively by syslog?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the modified date and time of the file private.txt to 11 Nov 2009 02:59:58 am. Which of the following commands will John use to accomplish his task?
Each correct answer represents a complete solution. Choose all that apply.
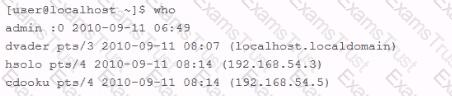
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back:
Which of the following are network connectivity devices?
Each correct answer represents a complete solution. Choose all that apply.
What is the command-line tool for Windows XP and later that allows administrators the ability to get or set configuration data for a very wide variety of computer and user account settings?
Which of the following utilities provides an efficient way to give specific users permission to use specific system commands at the root level of a Linux operating system?
Which of the following is a private, RFC 1918 compliant IP address that would be assigned to a DHCP scope on a private LAN?
Which of the following networking topologies uses a hub to connect computers?
A database is accessed through an application that users must authenticate with, on a host that only accepts connections from a subnet where the business unit that uses the data is located. What defense strategy is this?
Which of the following protocols allows an e-mail client to access and manipulate a remote e-mail file without downloading it to the local computer?
You work as a Network Administrator for Rick International. The company has a TCP/IP-based network. A user named Kevin wants to set an SSH terminal at home to connect to the company's network. You have to configure your company's router for it. By default, which of the following standard ports does the SSH protocol use for connection?
A US case involving malicious code is brought to trial. An employee had opened a helpdesk ticket to report specific instances of strange behavior on her system. The IT helpdesk representative collected information by interviewing the user and escalated the ticket to the system administrators. As the user had regulated and sensitive data on her computer, the system administrators had the hard drive sent to the company's forensic consultant for analysis and configured a new hard drive for the user. Based on the recommendations from the forensic consultant and the company's legal department, the CEO decided to prosecute the author of the malicious code. During the court case, which of the following would be able to provide direct evidence?
When no anomaly is present in an Intrusion Detection, but an alarm is generated, the response is known as.
There is not universal agreement on the names of the layers in the TCP/IP networking model. Which of the following is one of the functions of the bottom layer which is sometimes called the Network Access or Link Layer?
For most organizations, which of the following should be the highest priority when it comes to physical security concerns?
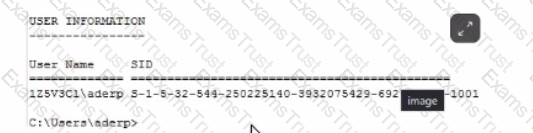
Analyze the following screenshot. What conclusion can be drawn about the user account shown?
What is the maximum number of connections a normal Bluetooth device can handle at one time?
Which asymmetric algorithm is used only for key exchange?
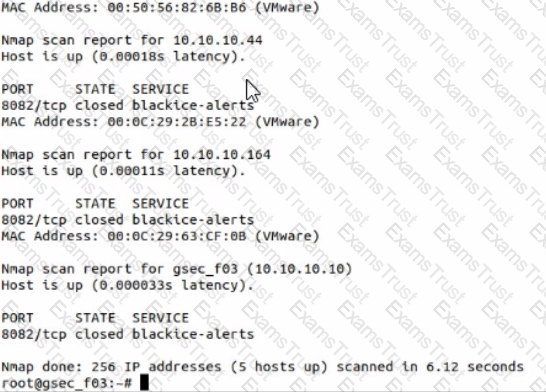
Use nmap to discover a host on the 10.10.10.0/24 network, scanning only port 8082 and using the SYN or Stealth scan approach. Which host has a service called -blackice-alerts"?
Which of the following statements about the integrity concept of information security management are true?
Each correct answer represents a complete solution. Choose three.
You are responsible for a Microsoft based network. Your servers are all clustered. Which of the following are the likely reasons for the clustering?
Each correct answer represents a complete solution. Choose two.
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
The following three steps belong to the chain of custody for federal rules of evidence. What additional step is recommended between steps 2 and 3?
STEP 1 - Take notes: who, what, where, when and record serial numbers of machine(s) in question.
STEP 2 - Do a binary backup if data is being collected.
STEP 3 - Deliver collected evidence to law enforcement officials.
What is the main reason that DES is faster than RSA?
The TTL can be found in which protocol header?
Why are false positives such a problem with IPS technology?
Your IT security team is responding to a denial of service attack against your server. They have taken measures to block offending IP addresses. Which type of threat control is this?
Users at the Marketing department are receiving their new Windows XP Professional workstations. They will need to maintain local work files in the first logical volume, and will use a second volume for the information shared between the area group. Which is the best file system design for these workstations?
Your CIO has found out that it is possible for an attacker to clone your company's RFID (Radio Frequency ID) based key cards. The CIO has tasked you with finding a way to ensure that anyone entering the building is an employee. Which of the following authentication types would be the appropriate solution to this problem?
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
Which of the following protocols provides maintenance and error reporting function?
An attacker is able to trick an IDS into ignoring malicious traffic through obfuscation of the packet payload. What type of IDS error has occurred?
Which of the following types of computers is used for attracting potential intruders?
What is SSL primarily used to protect you against?
What could be used to mitigate hash collisions?
Which of the following areas of a network contains DNS servers and Web servers for Internet users?
What does PowerShell remoting use to authenticate to another host in a domain environment?
To be considered a strong algorithm, an encryption algorithm must be which of the following?
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
If a Linux administrator wanted to quickly filter out extraneous data and find a running process named RootKit, which command could he use?
When discussing access controls, which of the following terms describes the process of determining the activities or functions that an Individual is permitted to perform?
IPS devices that are classified as "In-line NIDS" devices use a combination of anomaly analysis, signature-based rules, and what else to identify malicious events on the network?
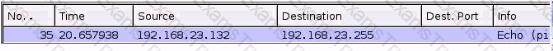
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
Which of the following is a Personal Area Network enabled device?
You are doing some analysis of malware on a Unix computer in a closed test network. The IP address of the computer is 192.168.1.120. From a packet capture, you see the malware is attempting to do a DNS query for a server called iamabadserver.com so that it can connect to it. There is no DNS server on the test network to do name resolution. You have another computer, whose IP is 192.168.1.115, available on the test network that you would like for the malware connect to it instead. How do you get the malware to connect to that computer on the test network?
In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
On which of the following OSI model layers does IPSec operate?
Who is responsible for deciding the appropriate classification level for data within an organization?
Which of the following TCP packet flags indicates that host should IMMEDIATELY terminate the connection containing the packet?
Which common firewall feature can be utilized to generate a forensic trail of evidence and to identify attack trends against your network?
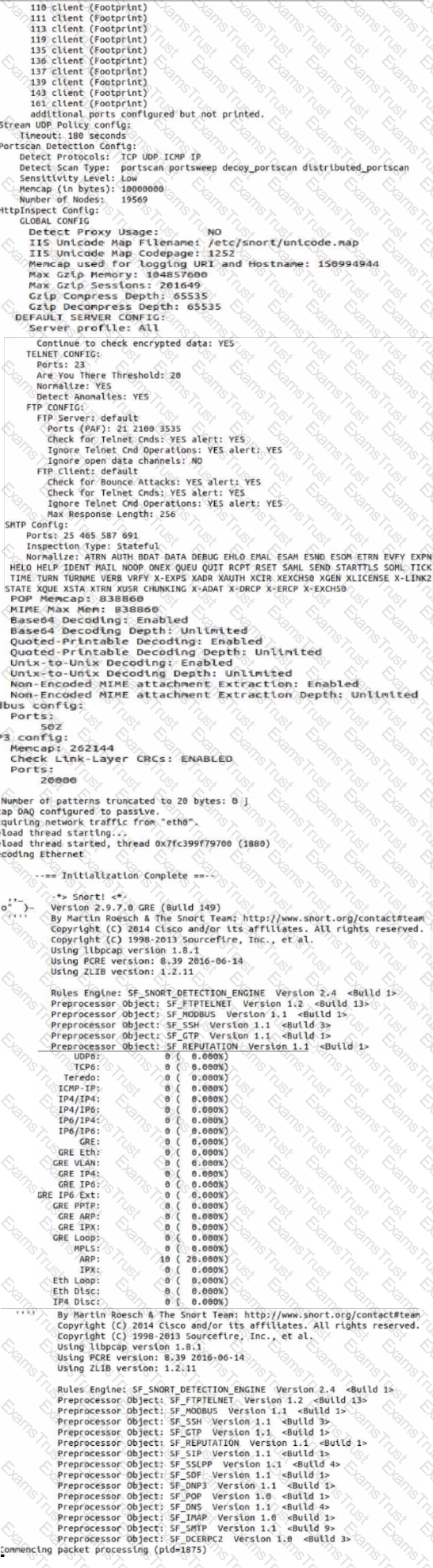
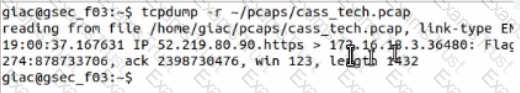
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
Which of the below choices should an organization start with when implementing an effective risk management process?
How many clients Is a single WSUS server designed to support when the minimum system requirements are met?
Which of the following statements about Hypertext Transfer Protocol Secure (HTTPS) are true? Each correct answer represents a complete solution. Choose two.
Which of the following tasks is the responsibility of a Linux systems administrator who is deploying hardening scripts to his systems?
Regarding the UDP header below, what is the length in bytes of the UDP datagrarn?
04 1a 00 a1 00 55 db 51
What is the term for a game in which for every win there must be an equivalent loss?
The TTL can be found in which protocol header?
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
Which of the following is more commonly used for establishing high-speed backbones that interconnect smaller networks and can carry signals over significant distances?
What cryptographic technique does file Integrity monitoring employ?
In the AGULP model, who should be assigned permissions and privileges?
Which of the four basic transformations in the AES algorithm involves the leftward circular movement of state data?
Which access control mechanism requires a high amount of maintenance since all data must be classified, and all users granted appropriate clearance?
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. You want to mount an SMBFS share from a Linux workstation. Which of the following commands can you use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
Which of the following statements would describe the term "incident" when used in the branch of security known as Incident Handling?
What defensive measure could have been taken that would have protected the confidentiality of files that were divulged by systems that were compromised by malware?
An email system administrator deploys a configuration blocking all inbound and outbound executable files due to security concerns.
What Defense in Depth approach is being used?
Which of the following applications cannot proactively detect anomalies related to a computer?
Which of the following is a backup strategy?
Which of the following is TRUE regarding the ability of attackers to eavesdrop on wireless communications?
Which Windows event log would you look in if you wanted information about whether or not a specific diver was running at start up?
Which of the following should be implemented to protect an organization from spam?
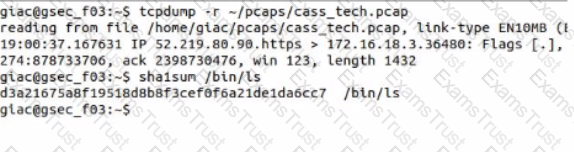
What is the SHA1 hash of the Ale /bin/Is?

What does Authentication Header (AH) add to the packet in order to prevent an attacker from lying about the source?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
A new data center is being built where customer credit information will be processed and stored. Which of the following actions will help maintain the confidentiality of the data?
A Windows administrator wants to automate local and remote management tasks in Active Directory. Which tool is most appropriate for this?
What is it called when an OSI layer adds a new header to a packet?
What protocol is a WAN technology?
Which of the following radio frequencies is used by the IEEE 802.11a wireless network?
Which Linux command could a systems administrator use to determine if an attacker had opened up a new listening port on her system?
What does it mean if a protocol such as HTTP is stateless?
Which of the following heights of fence deters only casual trespassers?
A Network Engineer is charged with maintaining and protecting a network with a high availability requirement. In addition to other defenses, they have chosen to implement a NIPS. How should the NIPS failure conditions be configured to ensure availability if the NIPS is installed in front of the Firewall that protects the DMZ?
Where could you go in Windows XP/2003 to configure Automatic Updates?
Which of the following is Azure's version of a superuser?
When are Group Policy Objects (GPOs) NOT applied automatically to workstations?
Which of the following is the reason of using Faraday cage?
What is the name of the Windows XP/2003 tool that you can use to schedule commands to be executed on remote systems during off-peak hours?
You are an Intrusion Detection Analyst and the system has alerted you to an Event of Interest (EOI) that appears to be activity generated by a worm. You investigate and find that the network traffic was normal. How would this type of alert be categorized?
SSL session keys are available in which of the following lengths?
Which of the following proxy servers provides administrative controls over the content?
Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a complete solution. Choose three.
What is the first thing that should be done during the containment step of incident handling?
Which of the following is an UDP based protocol?
Which of the following books deals with confidentiality?
What is a recommended defense against SQL injection, OS injection, and buffer overflows?