Which of the following tools can be used to find a username from a SID?
Which of the following tools allows you to download World Wide Web sites from the Internet to a local computer?
If a password is seven characters or less, the second half of the LM hash is always
___________________.
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about SSID is NOT true?
You want to search Microsoft Outlook Web Access Default Portal using Google search on the
Internet so that you can perform the brute force attack and get unauthorized access. What search string will you use to accomplish the task?
You want that some of your Web pages should not be crawled. Which one of the following options will you use to accomplish the task?
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
Which of the following enables an inventor to legally enforce his right to exclude others from using his invention?
Which of the following TCSEC classes defines verified protection?
Which of the following tasks is NOT performed into the enumeration phase?
Which of the following statements about Fport is true?
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
Which of the following is an open source Web scanner?
Which of the following methods can be used to detect session hijacking attack?
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
Fill in the blank with the appropriate word.
____is a port scanner that can also be used for the OS detection.
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
You enter the following URL on your Web browser:
af../windows/system32/cmd.exe?/c+dir+c:\
What task do you want to perform?
Which of the following tools can be used by a user to hide his identity?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools can be used to enumerate networks that have blocked ICMP Echo packets, however, failed to block timestamp or information packet or not performing sniffing of trusted addresses, and it also supports spoofing and promiscuous listening for reply packets?
Every network device contains a unique built in Media Access Control (MAC) address, which is used to identify the authentic device to limit the network access. Which of the following addresses is a valid MAC address?
John works as a Penetration Tester in a security service providing firm named you-are-secure Inc.
Recently, John's company has got a project to test the security of a promotional Website
and assigned the pen-testing work to John. When John is performing penetration testing, he inserts the following script in the search box at the company home page:
After pressing the search button, a pop-up box appears on his screen with the text - "Hi, John."
Which of the following attacks can be performed on the Web site tested by john while considering the above scenario?
LM hash is one of the password schemes that Microsoft LAN Manager and Microsoft Windows versions prior to the Windows Vista use to store user passwords that are less than 15 characters long. If you provide a password seven characters or less, the second half of the LM hash is always
__________.
You want to retrieve the default security report of nessus. Which of the following google search queries will you use?
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which of the following cryptographic attacks can be used to break both ciphers?
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.
You work as an IT Technician for uCertify Inc. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
How can web server logs be leveraged to perform Cross-Site Scripting (XSSI?
While reviewing traffic from a tcpdump capture, you notice the following commands being sent from a remote system to one of your web servers:
C:\>sc winternet.host.com create ncservicebinpath- "c:\tools\ncexe -I -p 2222 -e cmd.exe"
C:\>sc vJnternet.host.com query ncservice.
What is the intent of the commands?
Which of the following is the feature that separates the use of Rainbow Tables from other applications such as Cain or John the Ripper?
A penetration tester wishes to stop the Windows Firewall process on a remote host running Windows Vista She issues the following commands:
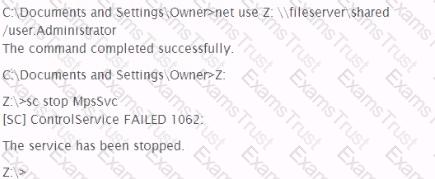
A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?
All of the following are advantages of using the Metasploitpriv module for dumping hashes from a local Windows machine EXCEPT:
You have compromised a Windows workstation using Metasploit and have injected the Meterpreter payload into the smss process. You want to dump the SAM database of the remote system so you can crack it offline. Which Meterpreter module would you need to load in addition to the defaults so that you can accomplish this?
Which of the following TCP packet sequences are common during a SYN (or half-open) scan?
What is the main difference between LAN MAN and NTLMv1 challenge/responses?
Which of the following is the JavaScript variable used to store a cookie?
Analyze the excerpt from a packet capture between the hosts 192.168.116.9 and 192.168.116.101. What factual conclusion can the tester draw from this output?
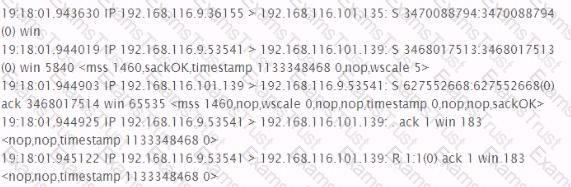
Identify the network activity shown below;
While performing a code audit, you discover a SQL injection vulnerability assuming the following vulnerable query, what user input could be injected to make the query true and return data?
select * from widgets where name = '[user-input]';
You are pen testing a Linux target from your windows-based attack platform. You just moved a script file from the windows system to the Linux target, but it will not execute properly. What is the most likely problem?
You have been contracted to perform a black box pen test against the Internet facing servers for a company. They want to know, with a high level of confidence, if their servers are vulnerable to external attacks. Your contract states that you can use all tools available to you to pen test the systems. What course of action would you use to generate a report with the lowest false positive rate?
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
Which of the following tools connects to and executes files on remote systems?
Which of the following tools is an automated tool that is used to implement SQL injections and to retrieve data from Web server databases?
Which of the following statements are true about firewalking?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator in the Secure Inc. You often need to send PDF documents that contain secret information, such as, client password, their credit card details, email passwords, etc. through email to your customers. However, you are making PDFs password protected you are getting complaints from customers that their secret information is being misused. When you analyze this complaint you get that however you are applying the passwords on PDFs, they are not providing the maximum protection. What may be the cause of this security hole?
Which of the following United States laws protects stored electronic information?
Which of the following tools allow you to perform HTTP tunneling?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards and also detects wireless networks marking their relative position with a GPS?
You want to scan your network quickly to detect live hosts by using ICMP ECHO Requests. What type of scanning will you perform to accomplish the task?
Analyze the output of the two commands below:
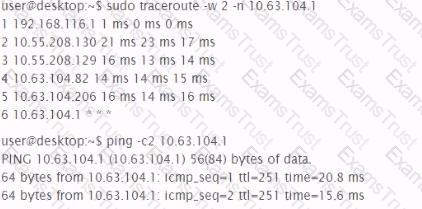
Which of the following can be factually inferred from the results of these commands?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 Active Directory domain-based network. The domain consists of a domain controller, two Windows 2003 member servers, and one hundred client computers. The company employees use laptops with Windows XP Professional. These laptops are equipped with wireless network cards that are used to connect to access points located in the Marketing department of the company. The company employees log on to the domain by using a user name and password combination. The wireless network has been configured with WEP in addition to 802.1x. Mark wants to provide the best level of security for the kind of authentication used by the company. What will Mark do to accomplish the task?