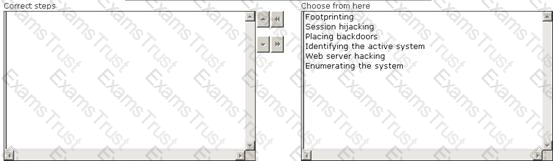
Maria works as a professional Ethical Hacker. She recently got a project to test the security of Arrange the three pre-test phases of the attack to test the security of weare-secure.
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer. She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with CHKDSK command to accomplish the task?
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to fix partitions on a hard drive. Which of the following Unix commands can you use to accomplish the task?
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP ports of his computer. Nathan uses the netstat command for this purpose but he is still unable to map open ports to the running process with PID, process name, and path. Which of the following commands will Nathan use to accomplish the task?
Which of the following is a file management tool?
Normally, RAM is used for temporary storage of data. But sometimes RAM data is stored in the hard disk, what is this method called?
Mark works as a security manager for SofTech Inc. He is using a technique for monitoring what the employees are doing with corporate resources. Which of the following techniques is being used by Mark to gather evidence of an ongoing computer crime if a member of the staff is e-mailing company's secrets to an opponent?
Which of the following type of file systems is not supported by Linux kernel?
An executive in your company reports odd behavior on her PDA. After investigation you discover that a trusted device is actually copying data off the PDA. The executive tells you that the behavior started shortly after accepting an e-business card from an unknown person. What type of attack is this?
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Which of the following is the correct order of digital investigations Standard Operating Procedure (SOP)?
Adam works as a Computer Hacking Forensic Investigator for a garment company in the United States. A project has been assigned to him to investigate a case of a disloyal employee who is suspected of stealing design of the garments, which belongs to the company and selling those garments of the same design under different brand name. Adam investigated that the company does not have any policy related to the copy of design of the garments. He also investigated that the trademark under which the employee is selling the garments is almost identical to the original trademark of the company. On the grounds of which of the following laws can the employee be prosecuted?
Which of the following tools can be used to perform tasks such as Windows password cracking, Windows enumeration, and VoIP session sniffing?
The MBR of a hard disk is a collection of boot records that contain disk information such as disk architecture, cluster size, and so on. The main work of the MBR is to locate and run necessary operating system files that are required to run a hard disk. In the context of the operating system, MBR is also known as the boot loader. Which of the following viruses can infect the MBR of a hard disk?
Each correct answer represents a complete solution. Choose two.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate the main server of SecureEnet Inc. The server runs on Debian Linux operating system. Adam wants to investigate and review the GRUB configuration file of the server system.
Which of the following files will Adam investigate to accomplish the task?
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
This type of virus infects programs that can execute and load into memory to perform predefined steps for infecting systems. It infects files with the extensions .EXE, .COM, .BIN, and .SYS. As it can replicate or destroy these types of files, the operating system becomes corrupted and needs reinstallation. This type of virus is known as __________.
Which of the following statements about the HKEY_LOCAL_MACHINE registry hive is true?
Which of the following wireless network standards operates on the 5 GHz band and transfers data at a rate of 54 Mbps?
Which of the following tools is an asterisk password revealer tool?
Which of the following representatives of incident response team takes forensic backups of the systems that are the focus of the incident?
Which of the following statements is true for a file in the UNIX operating system?
In 2001, the Council of Europe passed a convention on cybercrime. It was the first international treaty seeking to address computer crime and Internet crimes by harmonizing national laws, improving investigative techniques, and increasing cooperation among nations. On 1 March 2006, the Additional Protocol to the Convention on Cybercrime came into force. Which of the following statements clearly describes this protocol?
Which of the following graphical tools is used to navigate through directory structures?
Which of the following is the Windows feature on which the file management can be performed by a PC user?
Which of the following is used for remote file access by UNIX/Linux systems?
Which of the following tools is used to locate lost files and partitions to restore data from a formatted, damaged, or lost partition in Windows and Apple Macintosh computers?
Which of the following Incident handling process phases is responsible for defining rules, collaborating human workforce, creating a back-up plan, and testing the plans for an enterprise?
Which of the following registry hives stores configuration information specific to a particular user who is currently logged on to the computer?
Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned with a project to investigate a computer in the network of SecureEnet Inc. The compromised system runs on Windows operating system. Adam decides to use Helix Live for Windows to gather data and electronic evidences starting with retrieving volatile data and transferring it to server component via TCP/IP. Which of the following application software in Helix Windows Live will he use to retrieve volatile data and transfer it to the server component via TCP/IP?
Which of the following file systems supports disk quotas?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate an iphone, which is being seized from a criminal. The local police suspect that this iphone contains some sensitive information. Adam knows that the storage partition of the iphone is divided into two partitions. The first partition is used for the operating system. Other data of iphone is stored in the second partition. Which of the following is the name with which the second partition is mounted on the iphone?
What is the name of the Secondary IDE slave, fourth partition in Linux operating system according to the Linux naming convention?
You want to perform passive footprinting against we-are-secure Inc. Web server. Which of the following tools will you use?
A customer comes to you stating that his hard drive has crashed. He had backed up the hard drive, but some files on it were encrypted with Windows Encrypted File System (EFS). What do you need to do to be able to give him access to those restored encrypted files?
Which of the following commands can you use to create an ext3 file system?
Each correct answer represents a complete solution. Choose two.
Which of the following registry hives contains information about all users who have logged on to the system?
Which of the following types of attacks cannot be prevented by technical measures only?
Which of the following components are usually found in an Intrusion detection system (IDS)?
Each correct answer represents a complete solution. Choose two.
You want to change the attribute of a file named ACE.TXT to Hidden. Which command line will enable you to set the attribute?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of He enters the following command on the Linux terminal:
chmod 741 secure.c
Considering the above scenario, which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for NetTech Inc. The company's network is connected to the Internet. For security, you want to restrict unauthorized access to the network with minimum administrative effort. You want to implement a hardware-based solution. What will you do to accomplish this?
Which of the following articles defines illegal access to the computer or network in Chapter 2 of Section 1, i.e., Substantive criminal law of the Convention on Cybercrime passed by the Council of Europe?
Joseph works as a Software Developer for WebTech Inc. He wants to protect the algorithms and the techniques of programming that he uses in developing an application. Which of the following laws are used to protect a part of software?
You use the FAT16 file system on your Windows 98 computer. You want to upgrade to the FAT32 file system. What is the advantage of the FAT32 file system over FAT16 file system?
Each correct answer represents a complete solution. Choose two.
John works as a Technical Support Executive in ABC Inc. The company's network consists of ten computers with Windows XP professional installed on all of them. John is working with a computer on which he has enabled hibernation. He shuts down his computer using hibernation mode. Which of the following will happen to the data after powering off the system using hibernation?