An organization has implemented a control for Controlled Use of Administrative Privileges. They are collecting audit data for each login, logout, and location for the root account of their MySQL server, but they are unable to attribute each of these logins to a specific user. What action can they take to rectify this?
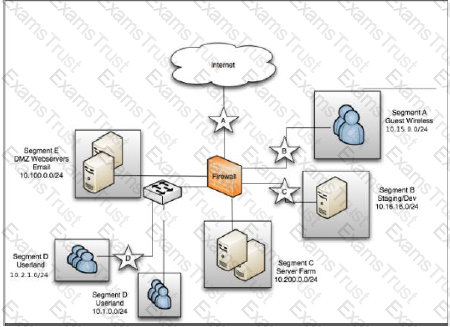
An organization has installed a firewall for Boundary Defense. It allows only outbound traffic from internal workstations for web and SSH, allows connections from the internet to the DMZ, and allows guest wireless access to the internet only. How can an auditor validate these rules?
Which of the following actions would best mitigate against phishing attempts such as the example below?

What is the first step suggested before implementing any single CIS Control?
IDS alerts at Service Industries are received by email. A typical day process over 300 emails with fewer than 50 requiring action. A recent attack was successful and went unnoticed due to the number of generated alerts. What should be done to prevent this from recurring?
John is implementing a commercial backup solution for his organization. Which of the following steps should be on the configuration checklist?
What tool creates visual network topology output and results that can be analyzed by Ndiff to determine if a service or network asset has changed?
Which of the following archiving methods would maximize log integrity?
Which of the following is a reliable way to test backed up data?
Which of the following should be used to test antivirus software?
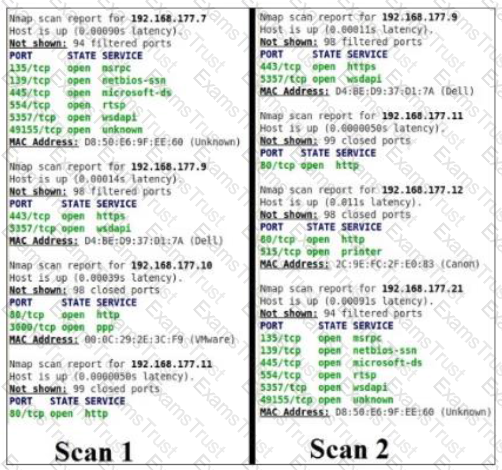
Scan 1 was taken on Monday. Scan 2 was taken of the same network on Wednesday. Which of the following findings is accurate based on the information contained in the scans?
John a network administrator at Northeast High School. Faculty have been complaining that although they can detect and authenticate to the faculty wireless network, they are unable to connect. While troubleshooting, John discovers that the wireless network server is out of DHCP addresses due to a large number of unauthorized student devices connecting to the network. Which course of action would be an effective temporary stopgap to secure the network until a permanent solution can be found?
A breach was discovered after several customers reported fraudulent charges on their accounts. The attacker had exported customer logins and cracked passwords that were hashed but not salted. Customers were made to reset their passwords.
Shortly after the systems were cleaned and restored to service, it was discovered that a compromised system administrator’s account was being used to give the attacker continued access to the network. Which CIS Control failed in the continued access to the network?