Cellebrite’s Physical Analyzer will conduct a Quick Scan for images, which goes through and carves files that may have been deleted from the device. When carving for image files, which of the following methods is most effectively used to recover data?
Which of the following is one potential risk of using the ALWAYS OFF rule for handling cell phones?
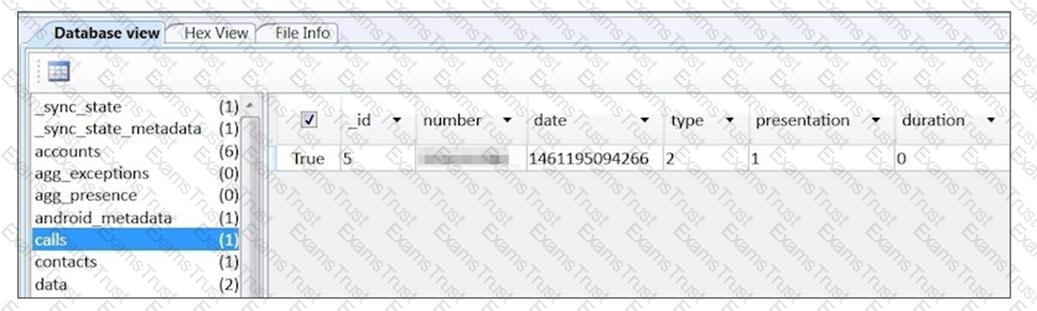
What is being shown in the image below?
Which of the following is a unique 56 bit number assigned to a CDMA handset?
Which of the following can most forensics tools crack on an iOS device?
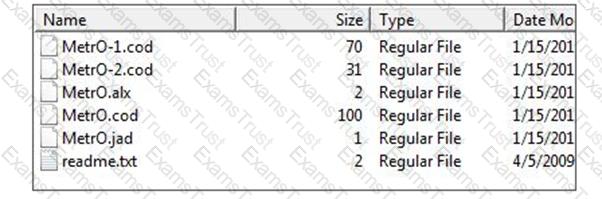
An analyst is reviewing the contents of a media card that was found without an associated device. Based on the image below, with which mobile device is it most likely that this device was once paired?
Which artifact(s) can be extracted from a logical image only if the device the image was acquired from was jailbroken?
Property list (Plist) files are used by iOS devices to store datA. Which of the file formats below is common to
plist files?
As part of your analysis of a legacy BlackBerry device, you examine the installed applications list and it
appears that no third-party applications were installed on the device. Which other file may provide you with additional information on applications that were accessed with the handset?
What will happen when a user creates an encrypted backup of their personal iPhone on their work computer then later performs a backup to their personal computer at home?
When examining a file system acquisition of an Android device Which artifact must be carved out manually?