Refer to the CLI output:
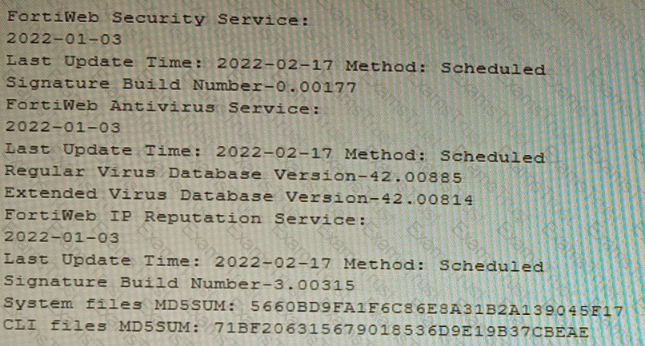
Given the information shown in the output, which two statements are correct? (Choose two.)
A remote worker requests access to an SSH server inside the network. You deployed a ZTNA Rule to their FortiClient. You need to follow the security requirements to inspect this traffic.
Which two statements are true regarding the requirements? (Choose two.)
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
Refer to the exhibit.
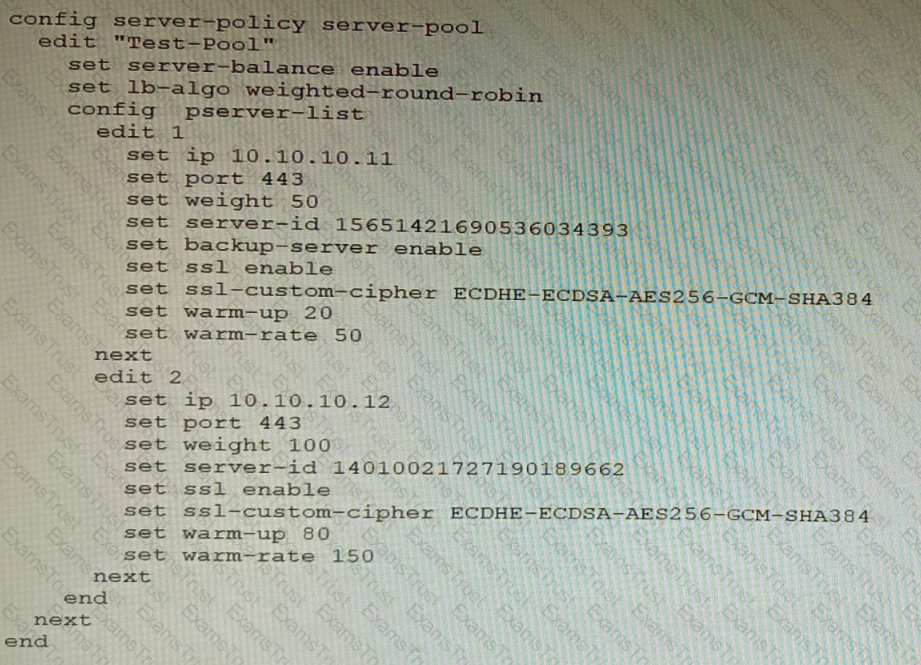
A FortiWeb appliance is configured for load balancing web sessions to internal web servers. The Server Pool is configured as shown in the exhibit.
How will the sessions be load balanced between server 1 and server 2 during normal operation?
You deployed a fully loaded FG-7121F in the data center and enabled sslvpn-load-balance. Based on the behavior of this feature which statement is correct?
A FortiGate deployment contains the following configuration:
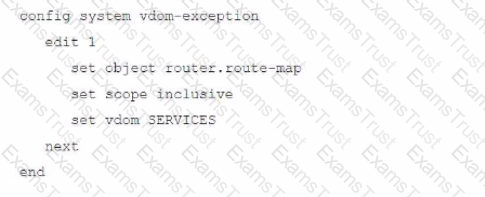
What is the result of this configuration?
Refer to the exhibit of a FortiNAC configuration.
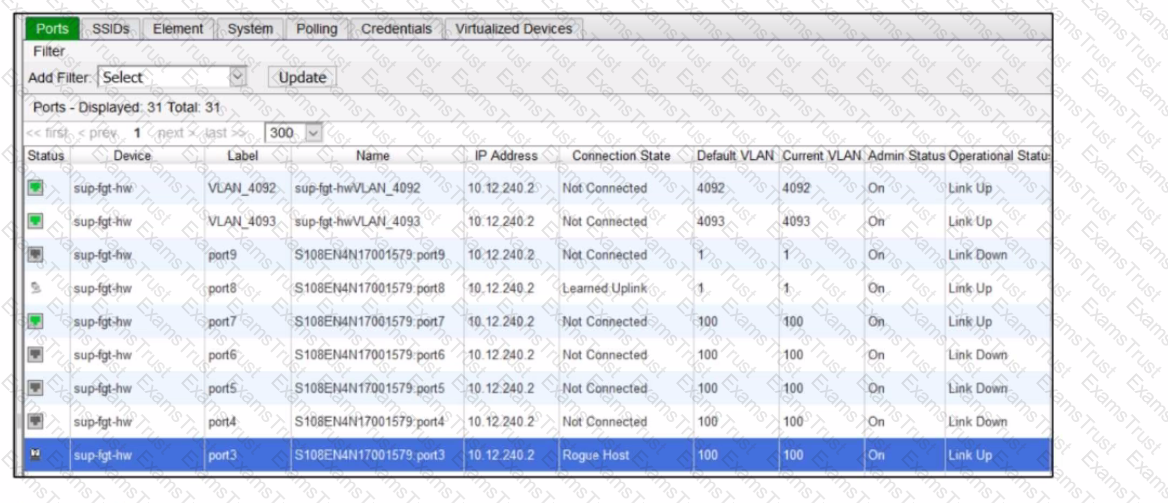
In this scenario, which two statements are correct? (Choose two.)
Refer to the exhibits.
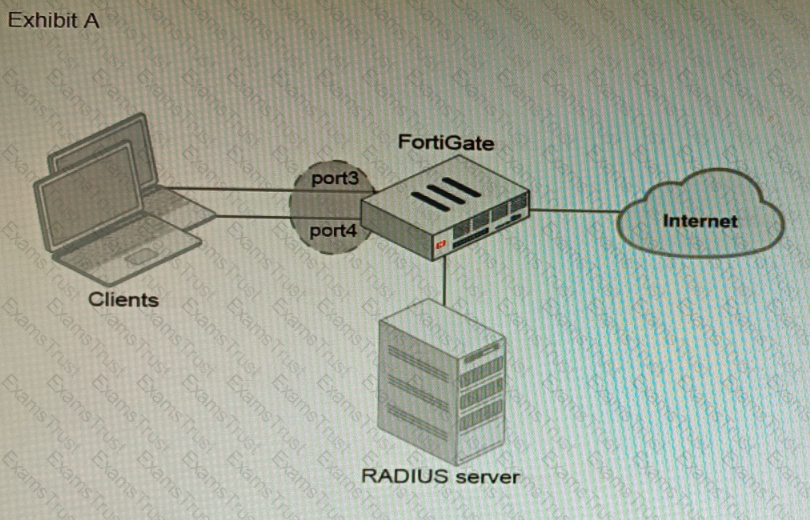
A customer is looking for a solution to authenticate the clients connected to a hardware switch interface of a FortiGate 400E.
Referring to the exhibits, which two conditions allow authentication to the client devices before assigning an IP address? (Choose two.)
A Hub FortiGate is connecting multiple branch FortiGate devices separating the traffic centrally in unique VRFs. Routing information is exchanged using BGP between the Hub and the Branch FortiGate devices.
You want to efficiently enable route leaking of specific routes between the VRFs.
Which two steps are required to achieve this requirement? (Choose two.)
Refer to the exhibit.
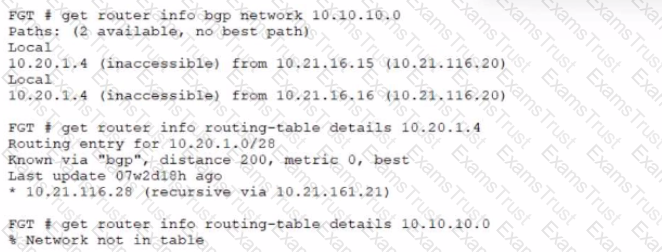
A customer reports that they are not able to reach subnet 10.10.10.0/24 from their FortiGate device.
Based on the exhibit, what should you do to correct the situation?
Refer to the exhibit.
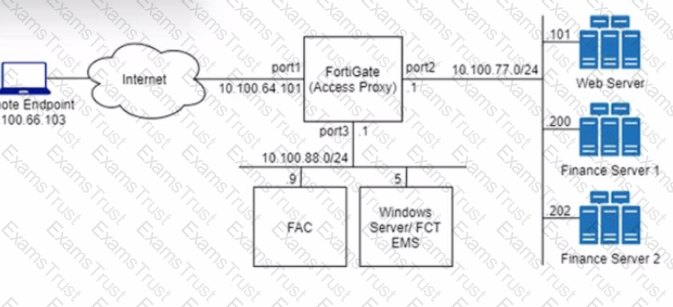
An HTTPS access proxy is configured to demonstrate its function as a reverse proxy on behalf of the web server it is protecting. It verifies user identity, device identity, and trust context, before granting access to the protected source. It is assumed that the FortiGate EMS fabric connector has already been successfully connected.
You need to ensure that ZTNA access through the FortiGate will redirect users to the FortiAuthenticator to perform username/password and multifactor authentication to validate access prior to accessing resources behind the FortiGate.
In this scenario, which two further steps need to be taken on the FortiGate? (Choose two.)
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
Refer to the exhibit.
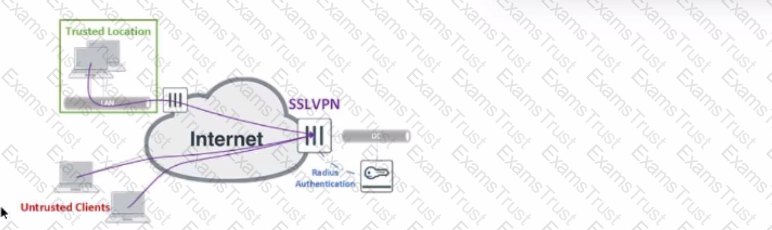
The exhibit shows the topology a customer wants to implement using a flexible authentication scheme. Users connecting from trusted remote locations are authenticated using only their username/password when connecting to the SSLVPN FortiGate in the data center.
When connecting from the Untrusted Clients, users must authenticate using 2-factor authentication.
In this scenario, which RADIUS attribute can be used as a RADIUS policy selector on the FortiAuthenticator to accomplish this goal?
Refer to the exhibit showing a FortiView monitor screen.
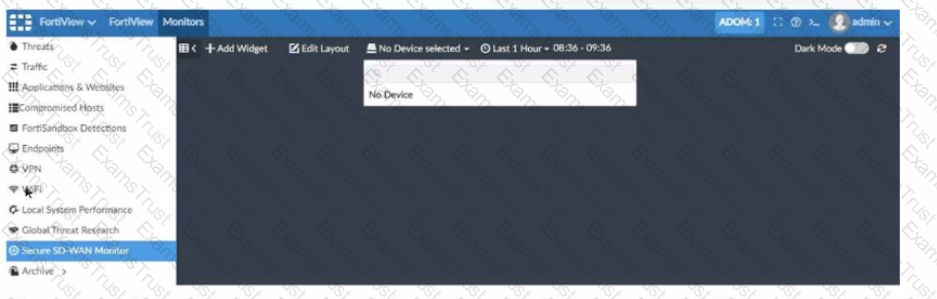
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
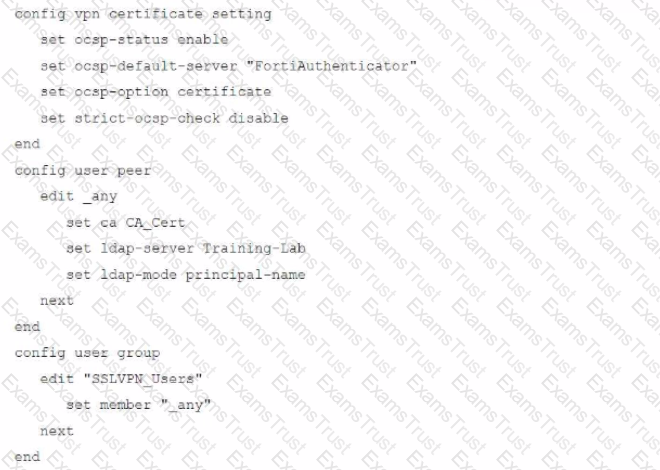
Based on this configuration, which authentication scenario will FortiGate deny?
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:
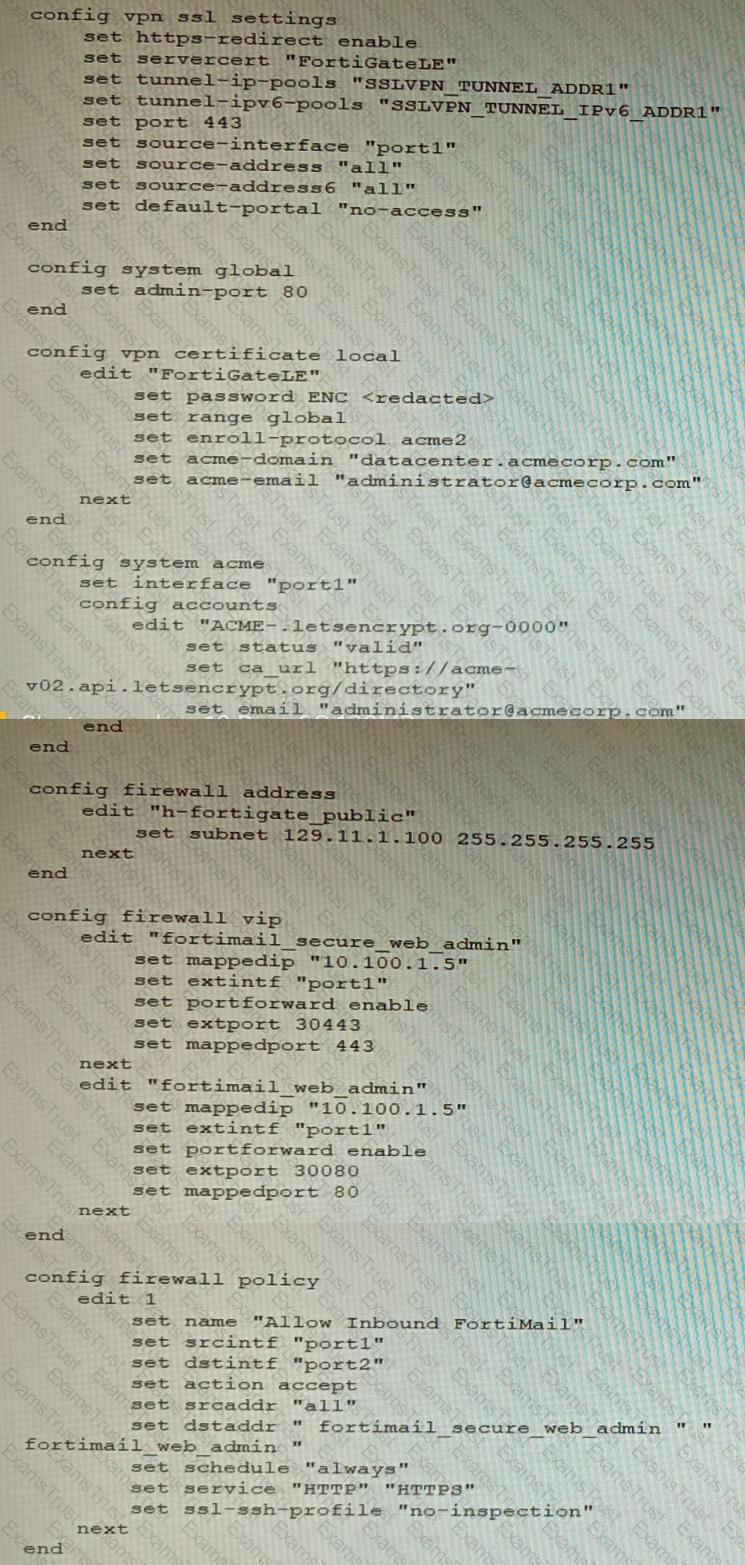
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
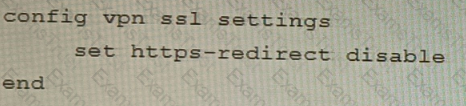
B)

C)
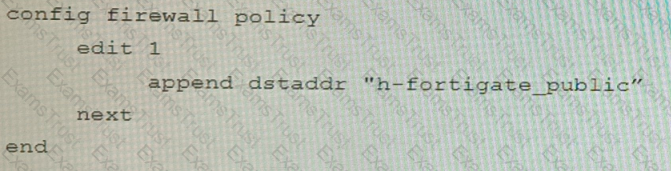
D)

Refer to the exhibits.
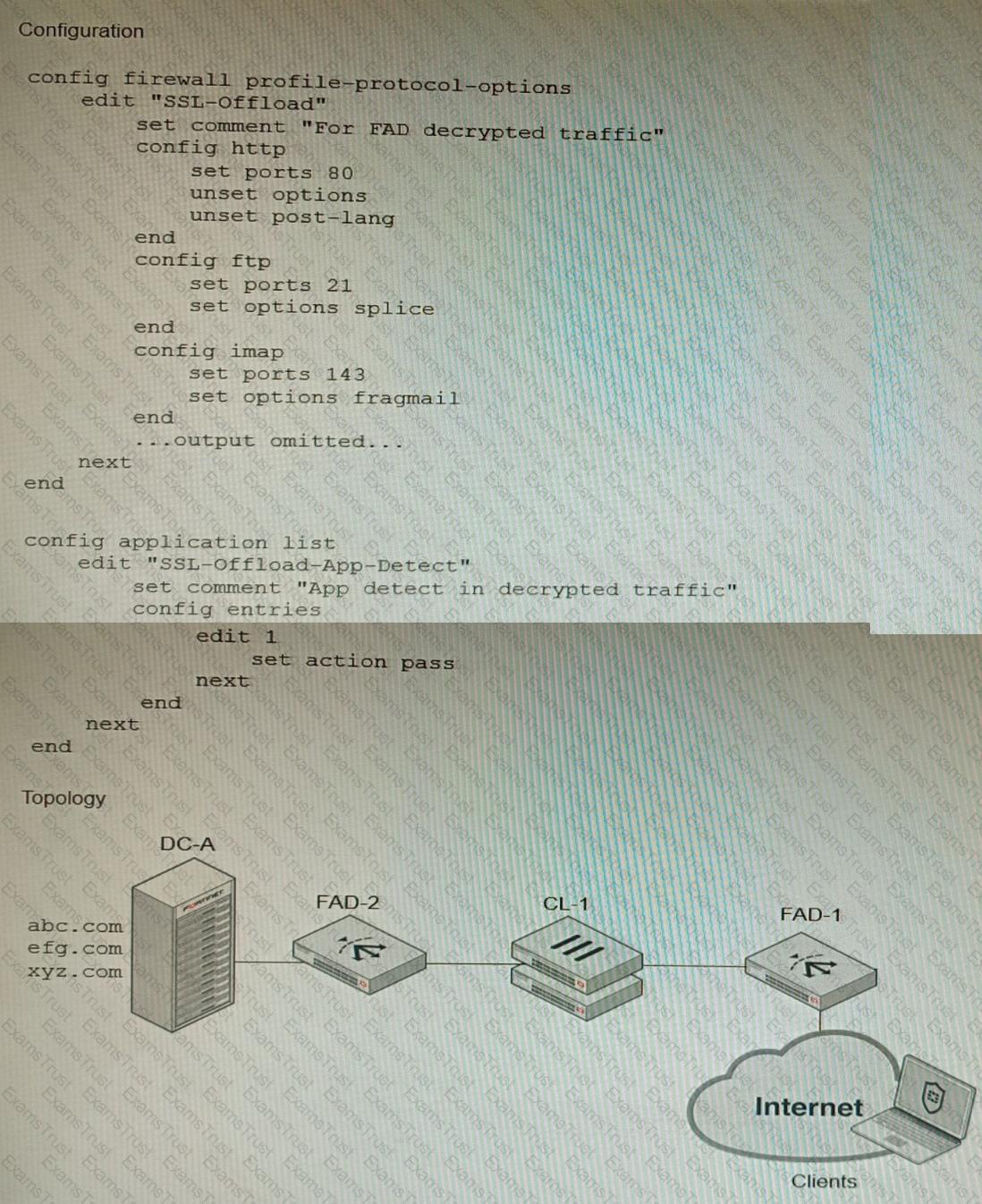
A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
A)
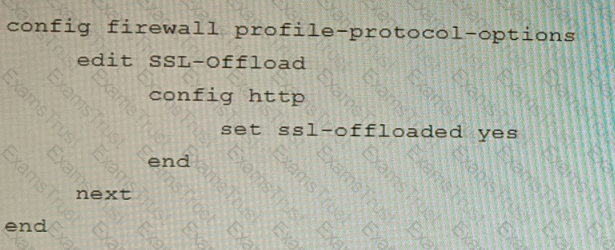
B)
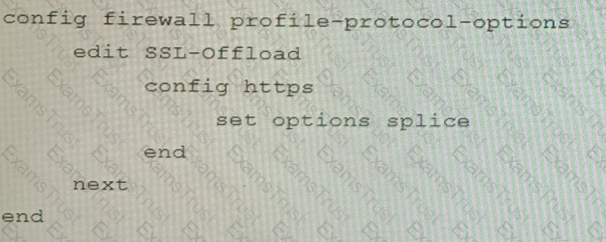
C)
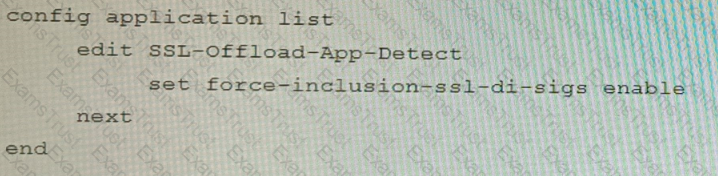
D)
Refer to the exhibit, which shows an SD-WAN configuration.

You configured the SD-WAN from Branch1 to the HUB and enabled packet duplication. You later notice that the traffic is not being duplicated. In this scenario, what is causing this problem?
Refer to the exhibit, which shows diagnostic output.
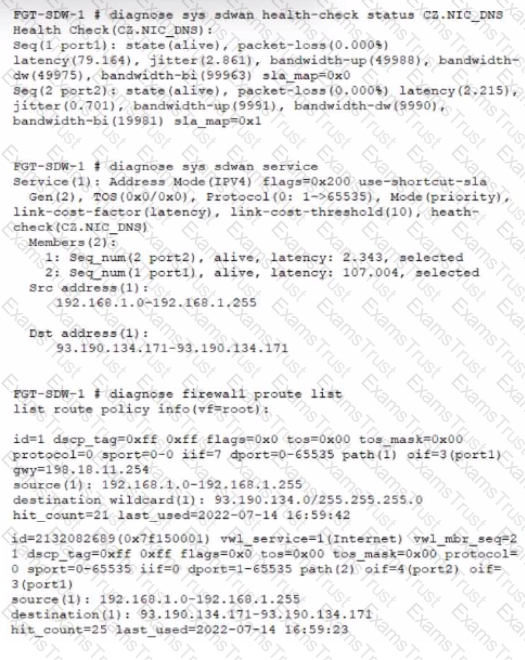
A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
Refer to the exhibit.
What is happening in this scenario?
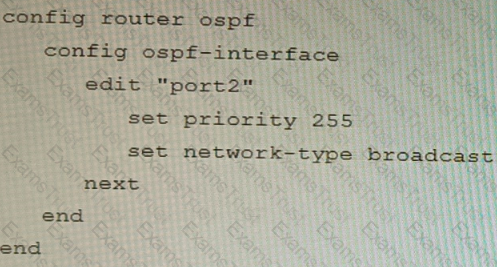
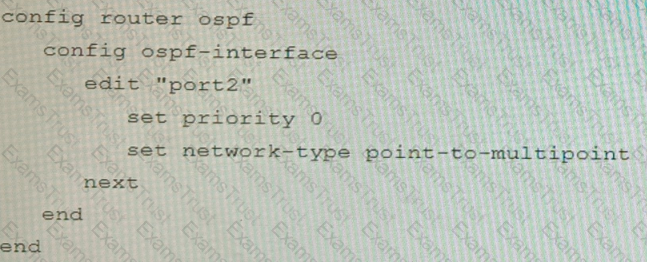
Refer to the exhibit.
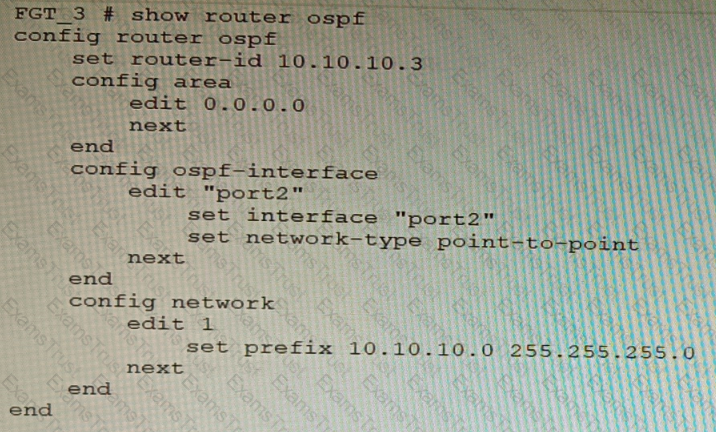
You are operating an internal network with multiple OSPF routers on the same LAN segment. FGT_3 needs to be added to the OSPF network and has the configuration shown in the exhibit. FGT_3 is not establishing any OSPF connection.
What needs to be changed to the configuration to make sure FGT_3 will establish OSPF neighbors without affecting the DR/BDR election?
A)
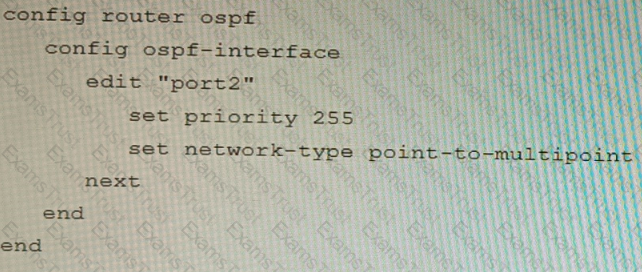
B)
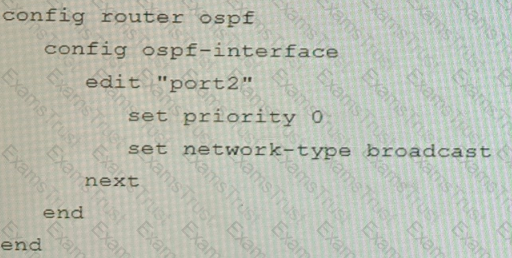
C)
D)
Review the Application Control log.
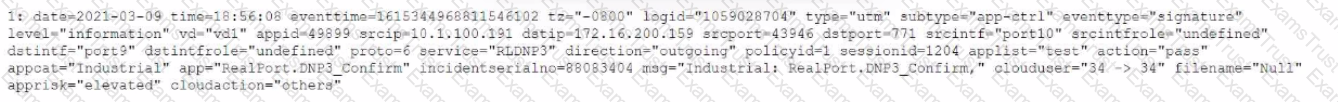
Which configuration caused the IPS engine to generate this log?
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
Which feature must you enable on the BGP neighbors to accomplish this goal?
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
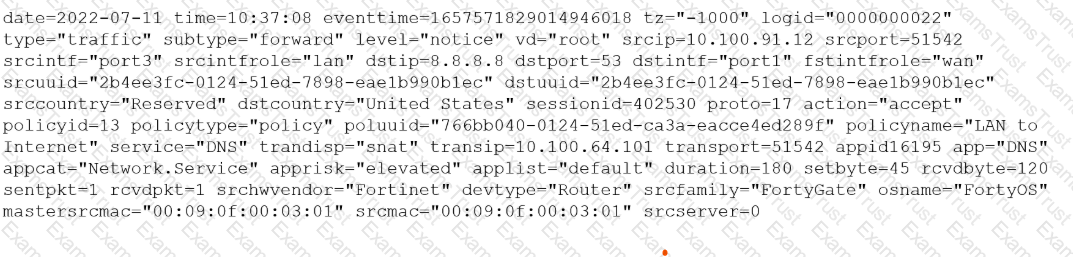
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
Refer to the exhibit that shows VPN debugging output.
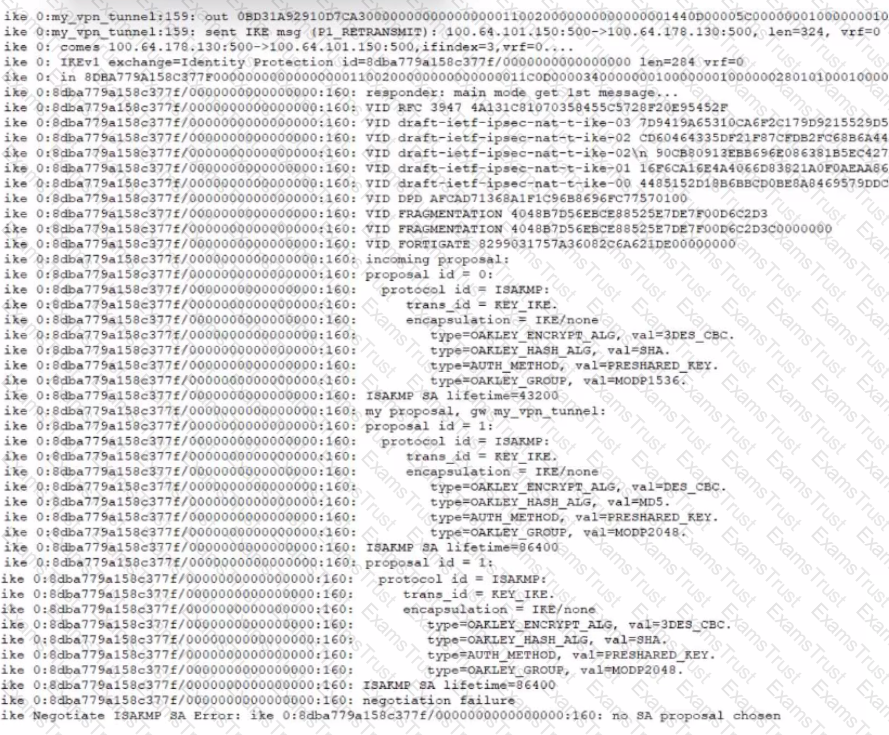
The VPN tunnel between headquarters and the branch office is not being established.
What is causing the problem?
Refer to The exhibit showing a FortiEDR configuration.
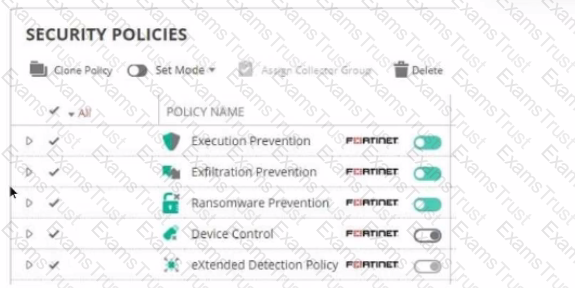
Based on the exhibit, which statement is correct?
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
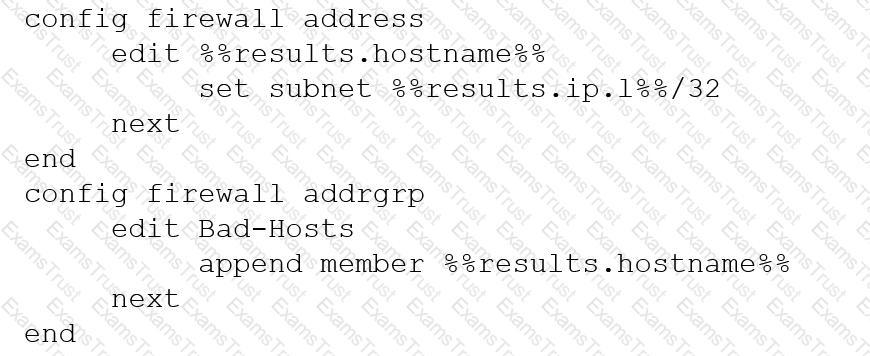
Refer to the exhibits.
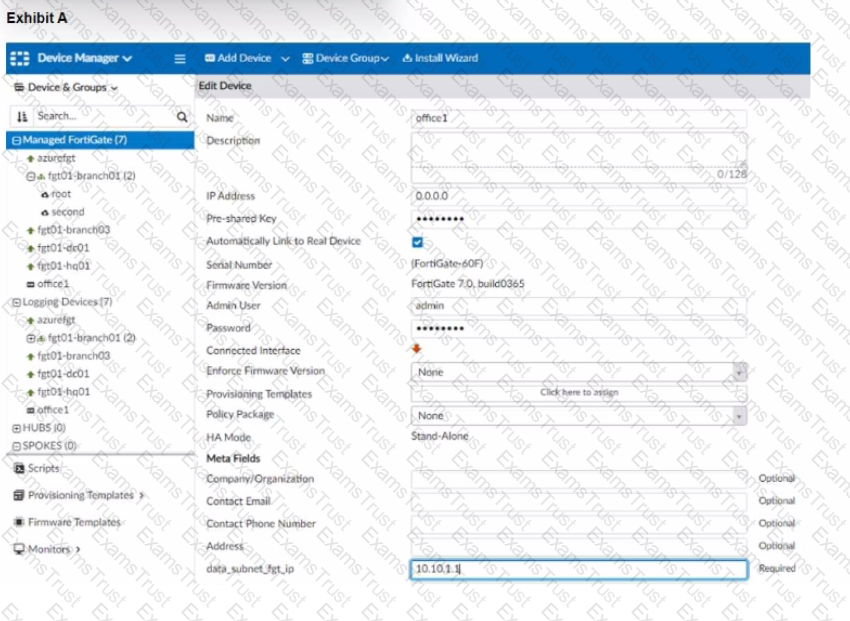
The exhibit shows a FortiGate model device that will be used for zero touch provisioning and a CLI Template.
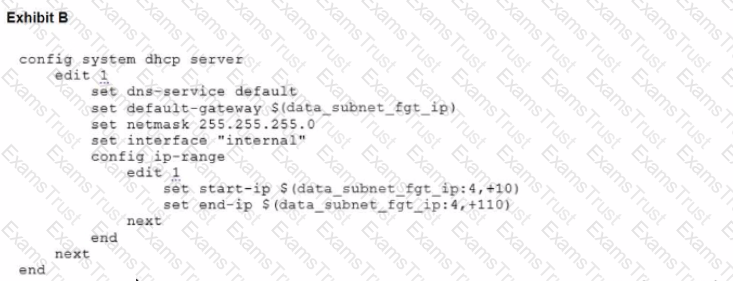
To facilitate a more efficient roll out of FortiGate devices, you are tasked with using meta fields with the CLI Template to configure the DHCP server on the "office1" FortiGate.
Given this scenario, what would be the output of the config ip-range section on the CLI Template?
Refer to the exhibits.
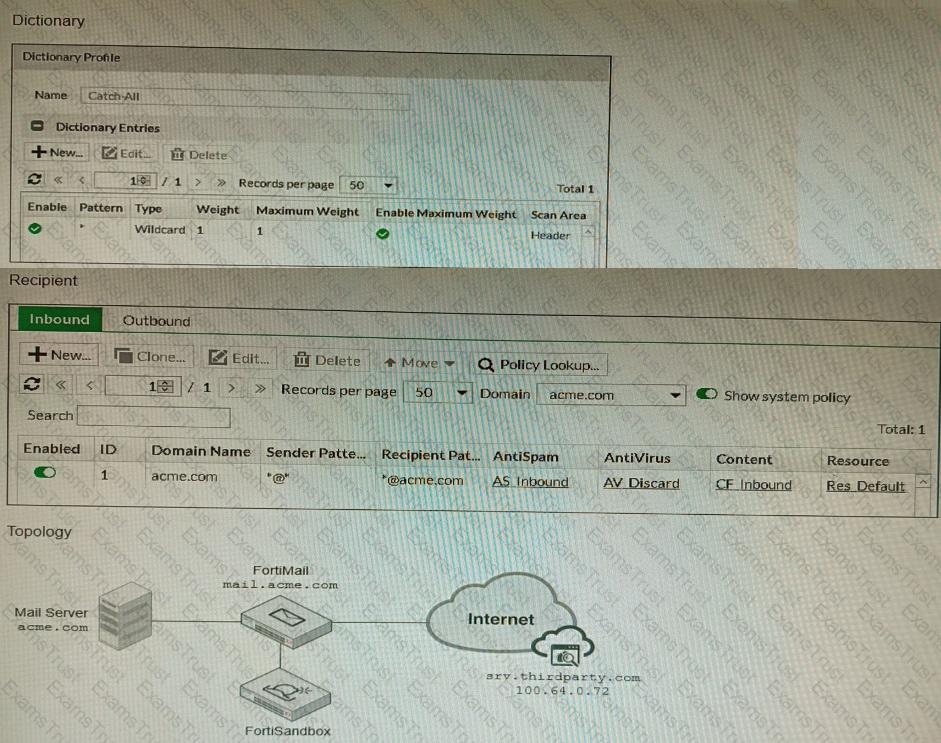
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
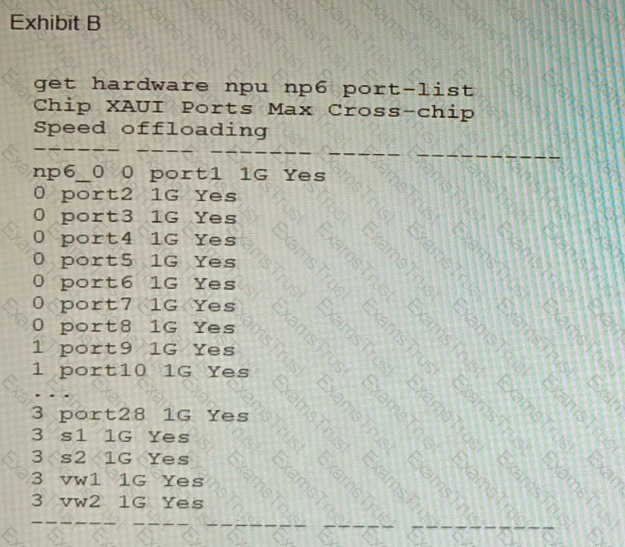
Refer to the exhibit.
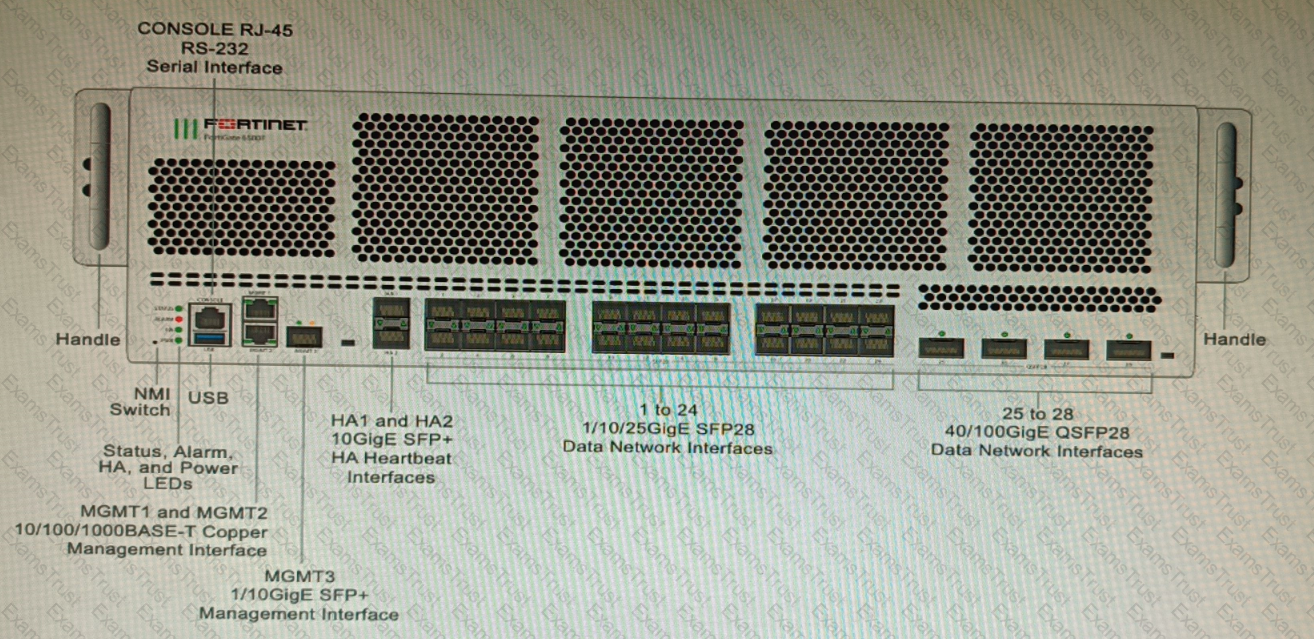
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?