What can be configured on FortiSASE as an additional layer of security for FortiClient registration? (Choose one answer)
Which authentication method overrides any other previously configured user authentication on FortiSASE?
Refer to the exhibit.
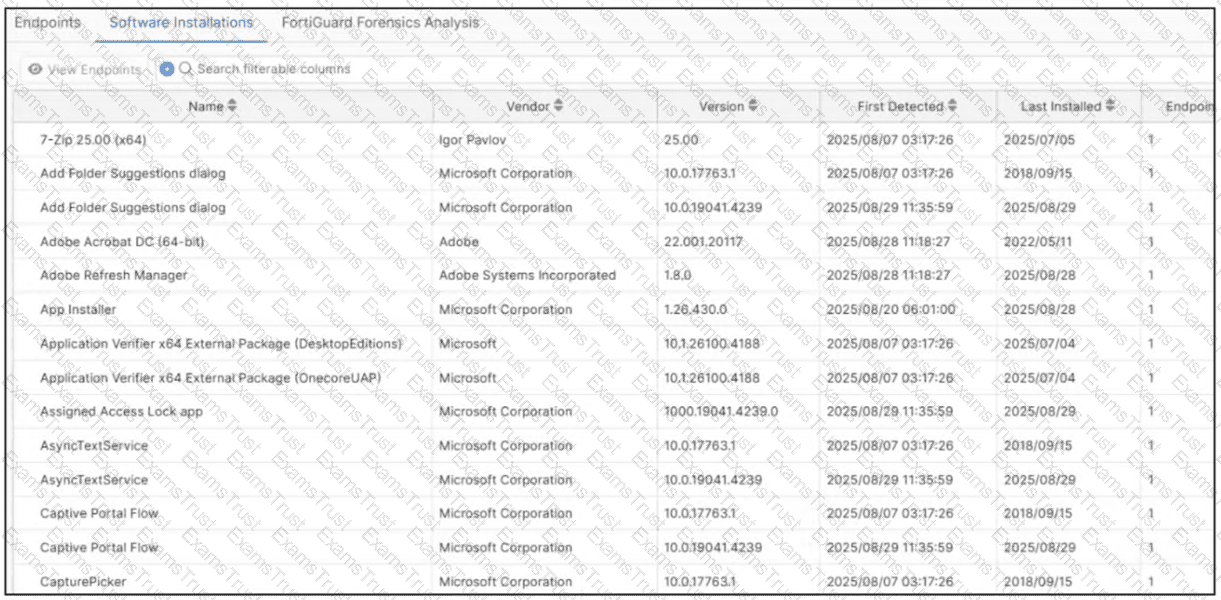
Which type of information or actions are available to a FortiSASE administrator from the following output? (Choose one answer)
An organization needs to resolve internal hostnames using its internal rather than public DNS servers for remotely connected endpoints. Which two components must be configured on FortiSASE to achieve this? (Choose two.)
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system. How can you provide secure internet access to the contractor using FortiSASE? (Choose one answer)
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)

How does FortiSASE Secure Private Access (SPA) facilitate connectivity to private resources in a hub-and-spoke network? (Choose one answer)
Which service is included in a secure access service edge (SASE) solution, but not in a security service edge (SSE) solution? (Choose one answer)
Which FortiSASE feature ensures least-privileged user access to all applications?
What action must a FortiSASE customer take to restrict organization SaaS access to only FortiSASE-connected users? (Choose one answer)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE. Which configuration can achieve this? (Choose one answer)
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
How does FortiSASE address the market trends of multicloud and Software-as-a-Service (SaaS) adoption, hybrid workforce, and zero trust? (Choose one answer)
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
What is the maximum number of Secure Private Access (SPA) service connections (SPA hubs) supported in the SPA use case? (Choose one answer)
What is the purpose of security posture tagging in ZTNA? (Choose one answer)
Refer to the exhibit.
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Refer to the exhibit.
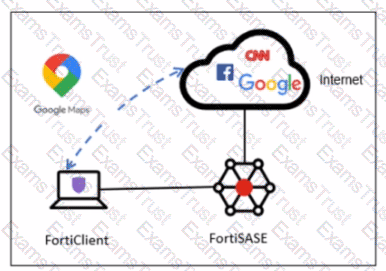
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement? (Choose one answer)
Refer to the exhibits.
WiMO-Pro and Win7-Pro are endpoints from the same remote location. WiMO-Pro can access the internet though FortiSASE, while Wm7-Pro can no longer access the internet
Given the exhibits, which reason explains the outage on Wm7-Pro?
Refer to the exhibits.
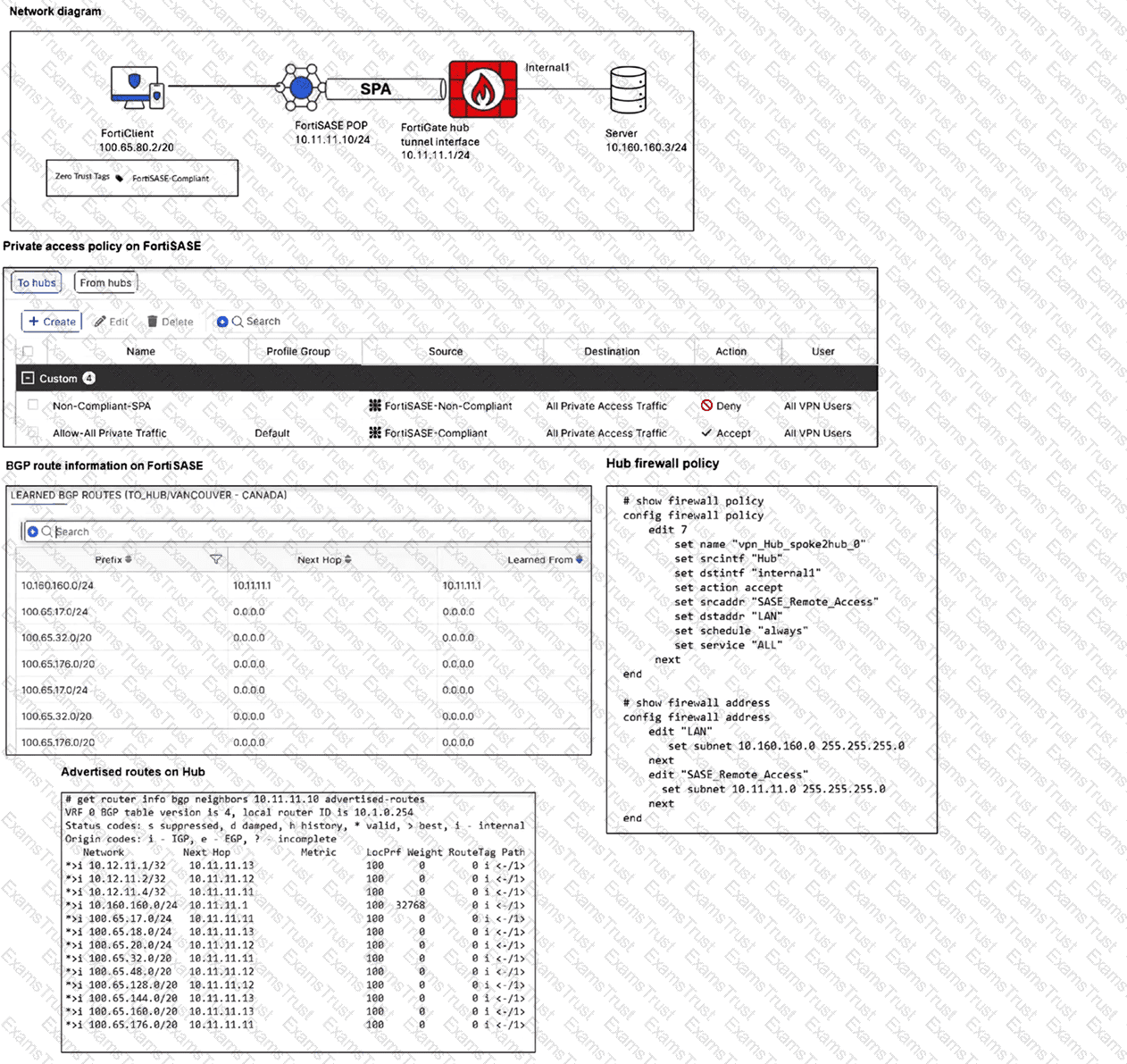
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub. What is the reason for the access failure? (Choose one answer)
Refer to the exhibit.
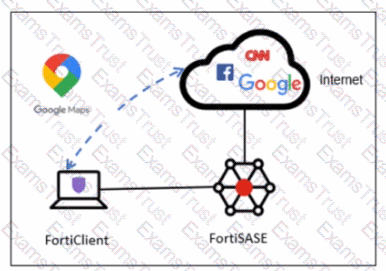
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
What is the purpose of the grace period for off-net endpoints in the FortiSASE Network Lockdown feature? (Choose one answer)
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?