Refer to the exhibit.
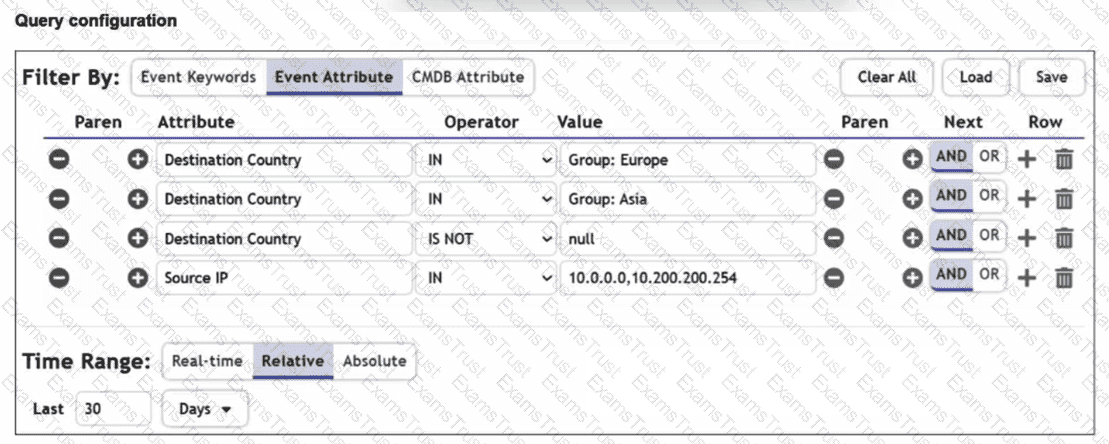
You are trying to find traffic flows to destinations that are in Europe or Asia, for hosts in the local LAN segment. However, the query returns no results. Assume these logs exist on FortiSIEM.
Which three mistakes can you see in the query shown in the exhibit? (Choose three answers)
Refer to the exhibits.
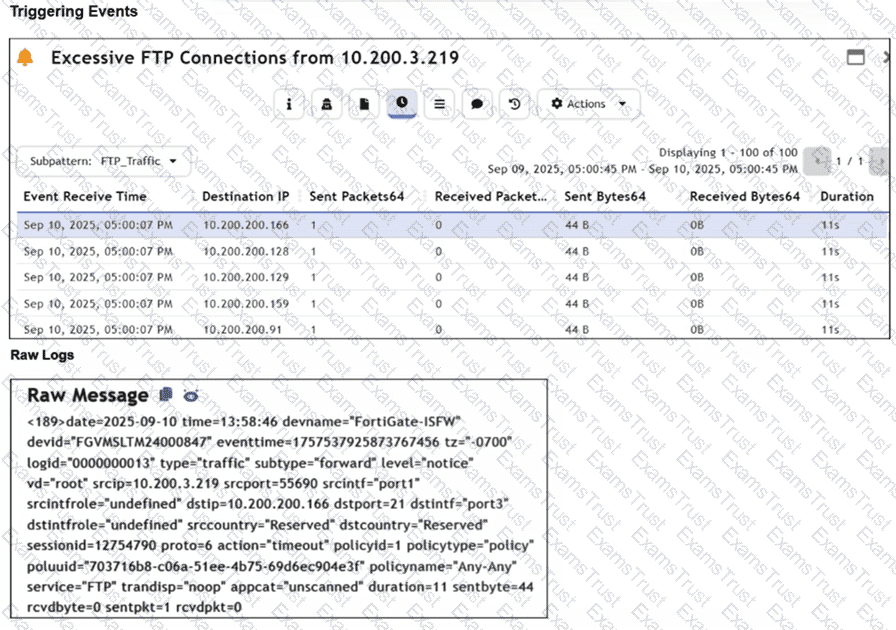
Assume that the traffic flows are identical, except for the destination IP address. There is only one FortiGate in network address translation (NAT) mode in this environment.
Based on the exhibits, which two conclusions can you make about this FortiSIEM incident? (Choose two answers)
Review the incident report:
An attacker identified employee names, roles, and email patterns from public press releases, which were then used to craft tailored emails.
The emails were directed to recipients to review an attached agenda using a link hosted off the corporate domain.
Which two MITRE ATT&CK tactics best fit this report? (Choose two answers)
Refer to the exhibits.
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three answers)
Which FortiAnalyzer feature uses the SIEM database for advance log analytics and monitoring?
When does FortiAnalyzer generate an event?
Which three statements accurately describe step utilities in a playbook step? (Choose three answers)
Refer to the exhibits.
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
Refer to the exhibits.
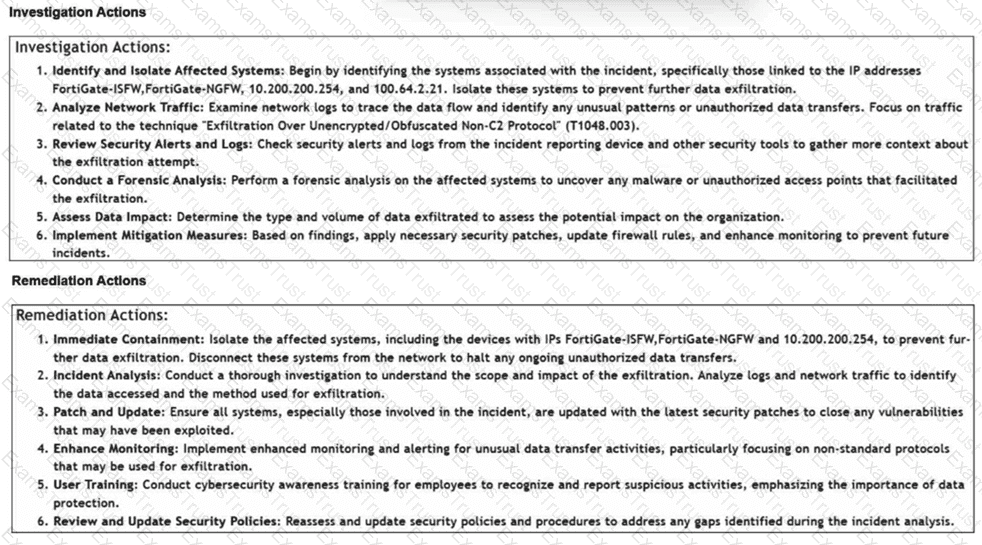
How is the investigation and remediation output generated on FortiSIEM? (Choose one answer)
While monitoring your network, you discover that one FortiGate device is sending significantly more logs to FortiAnalyzer than all of the other FortiGate devices in the topology.
Additionally, the ADOM that the FortiGate devices are registered to consistently exceeds its quota.
What are two possible solutions? (Choose two.)
Which role does a threat hunter play within a SOC?
Refer to the exhibit,
which shows the partial output of the MITRE ATT&CK Enterprise matrix on FortiAnalyzer.
Which two statements are true? (Choose two.)
Which two best practices should be followed when exporting playbooks in FortiAnalyzer? (Choose two answers)
Refer to the exhibit.
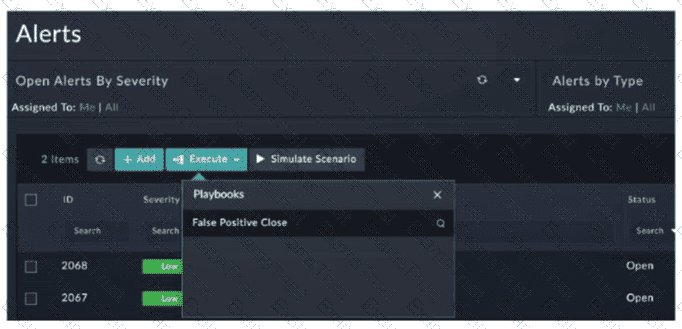
You configured a playbook namedFalse Positive Close, and want to run it to verify if it works. However, when you clickExecuteand search for the playbook, you do not see it listed. Which two reasons could be the cause of the problem? (Choose two answers)
Refer to the exhibit.
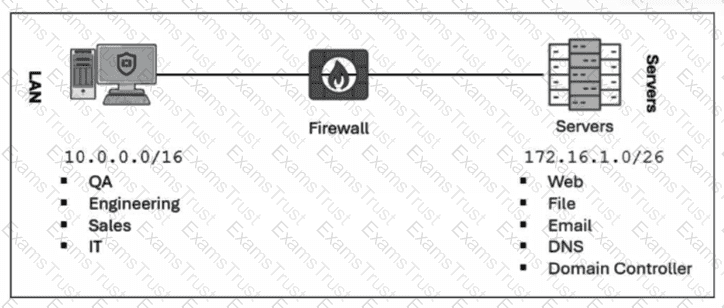
Which method most effectively reduces the attack surface of this organization? (Choose one answer)
Refer to the exhibit.
Assume that all devices in the FortiAnalyzer Fabric are shown in the image.
Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)