Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two.)
The administrator uses the FortiManager SD-WAN overlay template to prepare an SD-WAN deployment. With information provided through the SD-WAN overlay template wizard, FortiManager creates templates ready to install on spoke and hub devices.
Select three templates created by the SD-WAN overlay template for a spoke device. (Choose three.)
Refer to the exhibit.
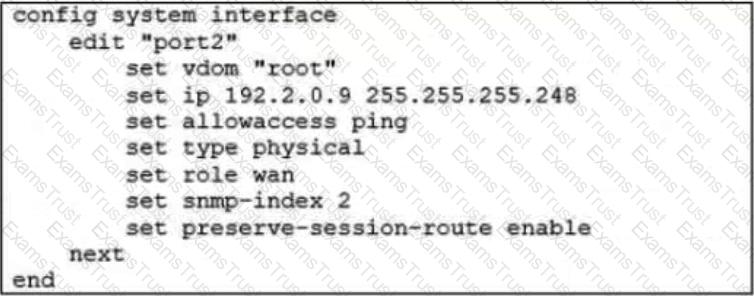
Based on the exhibit, which two actions does FortiGate perform on traffic passing through port2? (Choose two.)
Refer to the exhibits.
Exhibit A
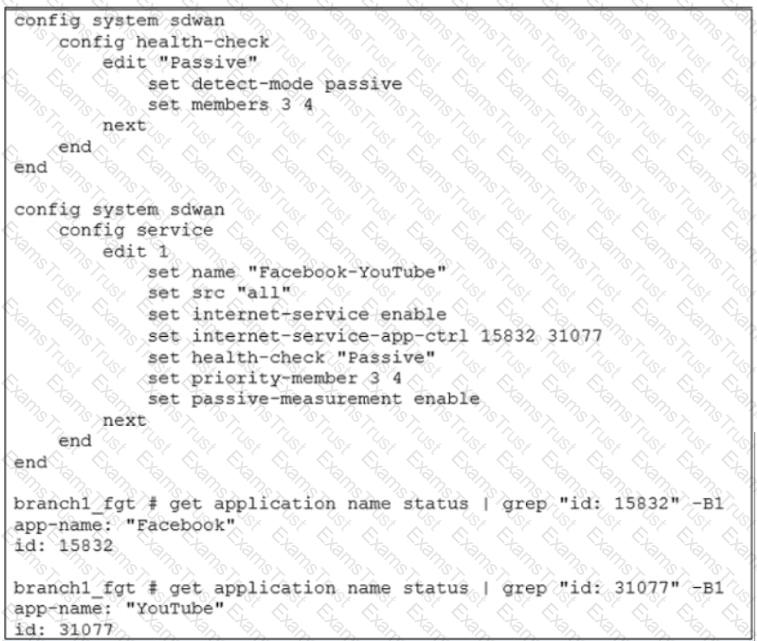
Exhibit B
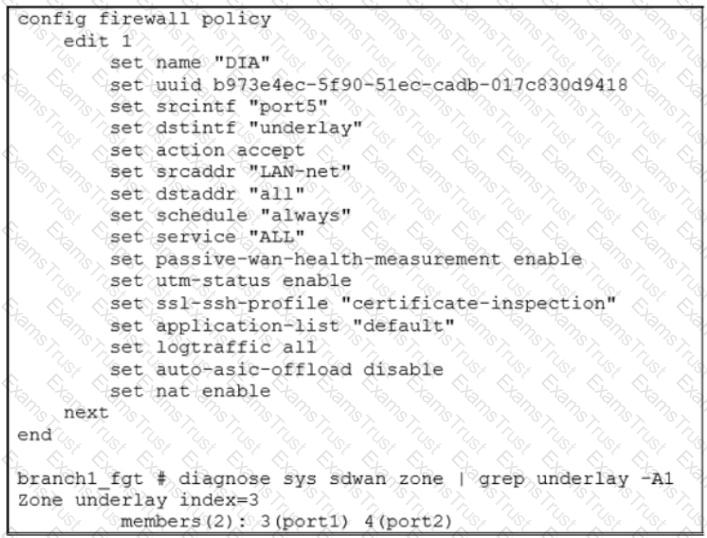
Exhibit A shows the SD-WAN performance SLA configuration, the SD-WAN rule configuration, and the application IDs of Facebook and YouTube. Exhibit B shows the firewall policy configuration and the underlay zone status.
Based on the exhibits, which two statements are correct about the health and performance of port1 and port2? (Choose two.)
Which type statements about the SD-WAN members are true? (Choose two.)
Which statement about using BGP routes in SD-WAN is true?
What is the route-tag setting in an SD-WAN rule used for?
What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in an hub-and-spoke topology? (Choose two.)
Which SD-WAN setting enables FortiGate to delay the recovery of ADVPN shortcuts?
Refer to the exhibit.
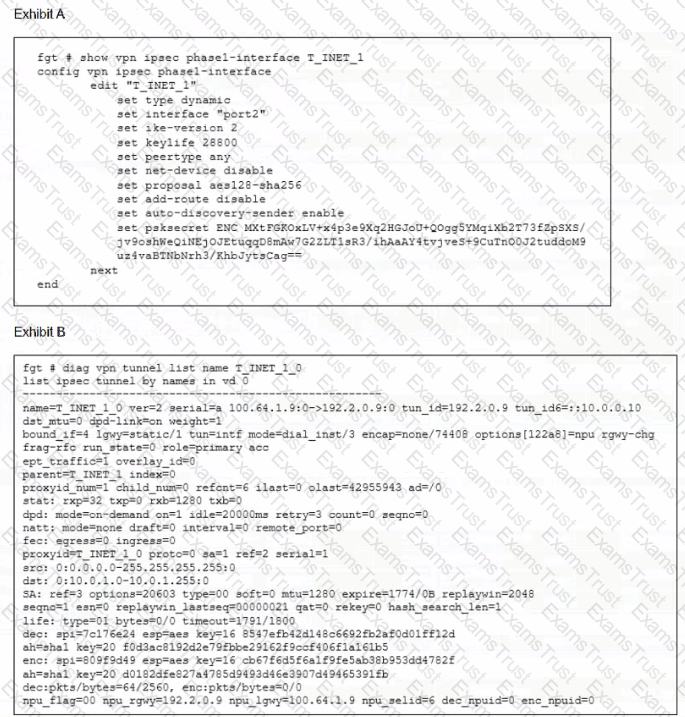
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
Refer to the exhibit.
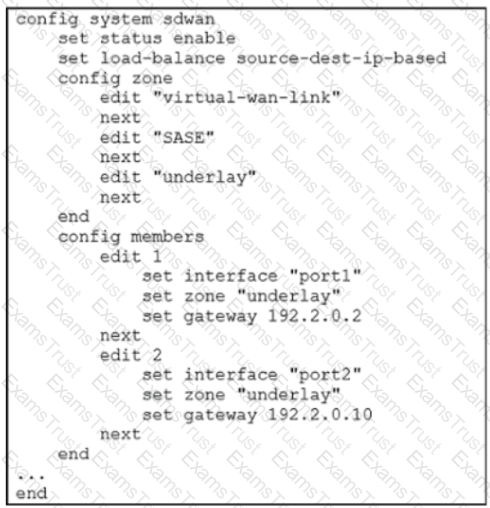
Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
Exhibit.
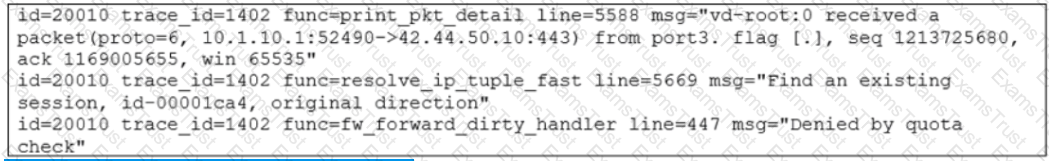
Which conclusion about the packet debug flow output is correct?
Refer to the exhibit.
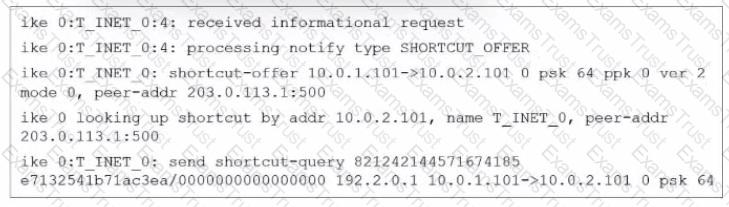
Which statement about the role of the ADVPN device in handling traffic is true?
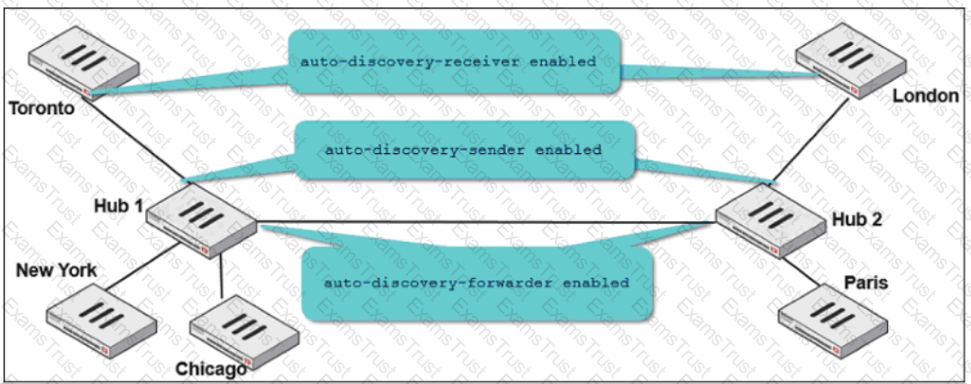
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2. The administrator configured ADVPN on both hub-and-spoke groups.
Which two outcomes are expected if a user in Toronto sends traffic to London? (Choose two.)
Refer to the exhibits.
Exhibit A -
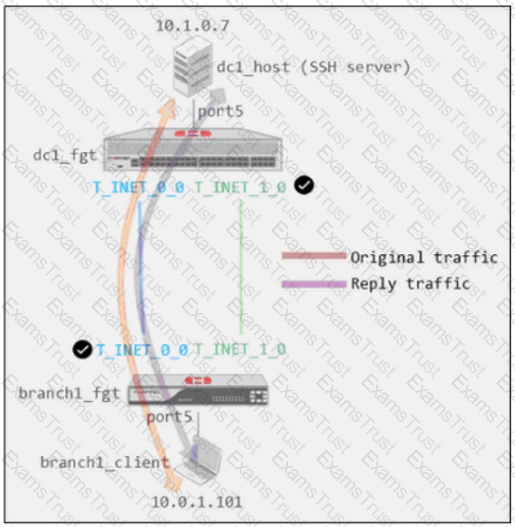
Exhibit B -

Exhibit A shows a site-to-site topology between two FortiGate devices: branch1_fgt and dc1_fgt. Exhibit B shows the system global and system settings configuration on dc1_fgt.
When branch1_client establishes a connection to dc1_host, the administrator observes that, on dc1_fgt, the reply traffic is routed over T_INET_0_0, even though T_INET_1_0 is the preferred member in the matching SD-WAN rule.
Based on the information shown in the exhibits, what configuration change must be made on dc1_fgt so dc1_fgt routes the reply traffic over T_INET_1_0?
Refer to the exhibit.
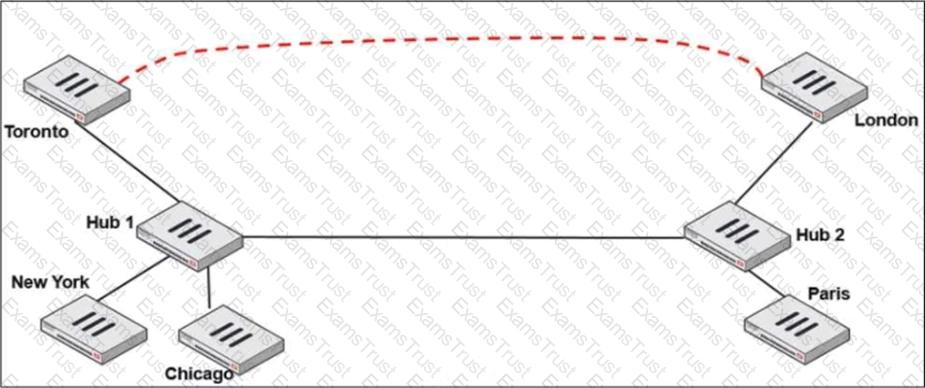
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2.
Which two configuration settings are required for Toronto and London spokes to establish an ADVPN shortcut? (Choose two.)
Refer to the exhibit.
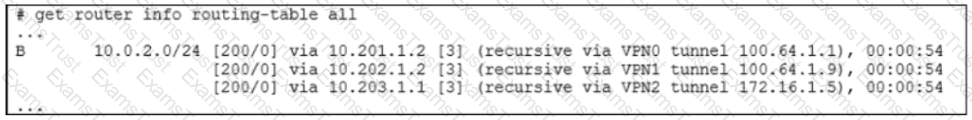
The device exchanges routes using IBGP.
Which two statements are correct about the IBGP configuration and routing information on the device? (Choose two.)
Which diagnostic command can you use to show the SD-WAN rules, interface information, and state?
diagnose sys sdwan service
diagnose sys sdwan route-tag-list
diagnose sys sdwan member
Which CLI command do you use to perform real-time troubleshooting for ADVPN negotiation?
Refer to the exhibits.
Exhibit A -
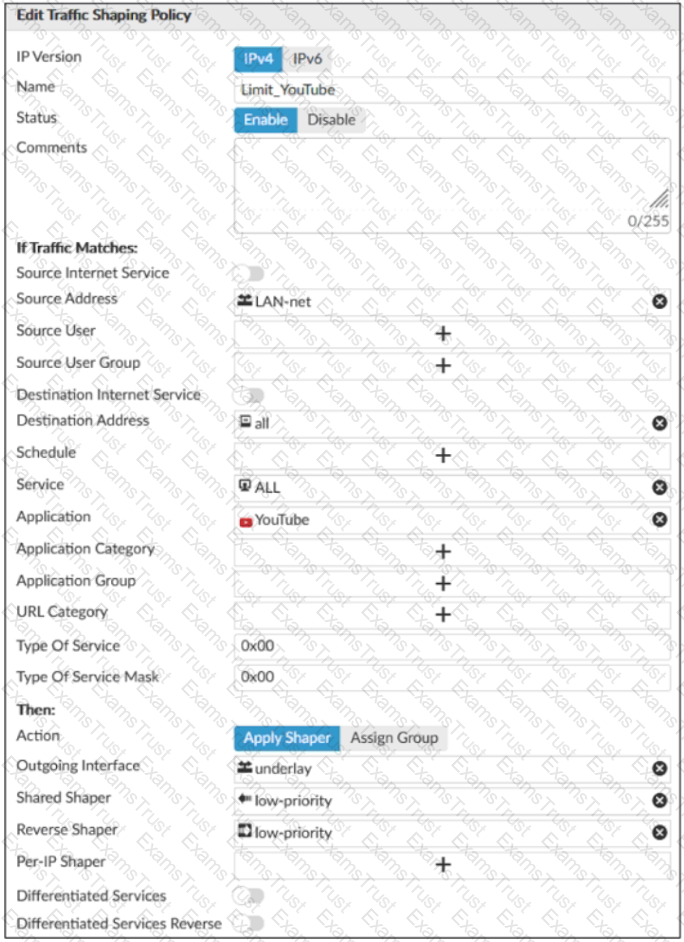
Exhibit B -
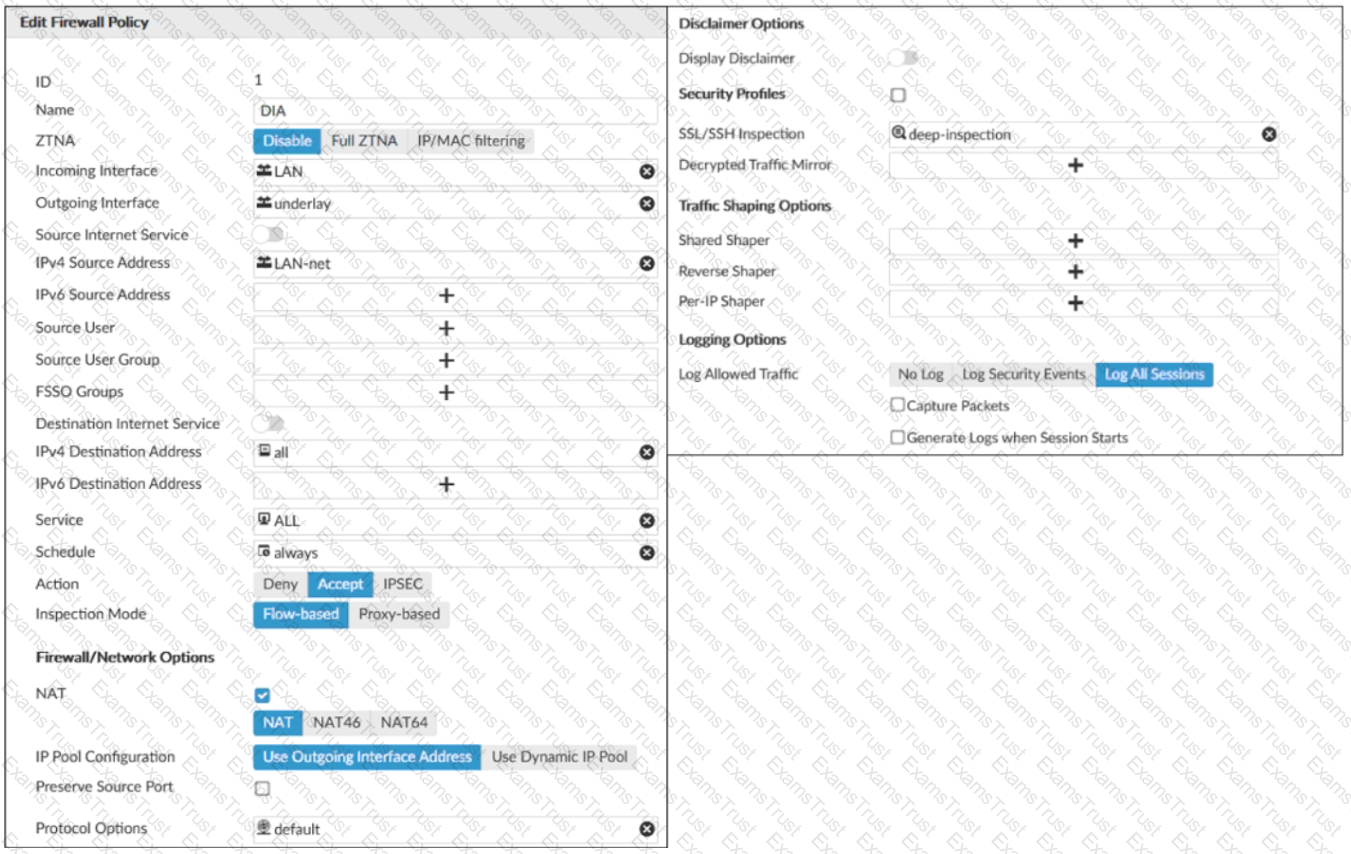
Exhibit A shows the traffic shaping policy and exhibit B shows the firewall policy.
The administrator wants FortiGate to limit the bandwidth used by YouTube. When testing, the administrator determines that FortiGate does not apply traffic shaping on YouTube traffic.
Based on the policies shown in the exhibits, what configuration change must be made so FortiGate performs traffic shaping on YouTube traffic?
Refer to the exhibit.
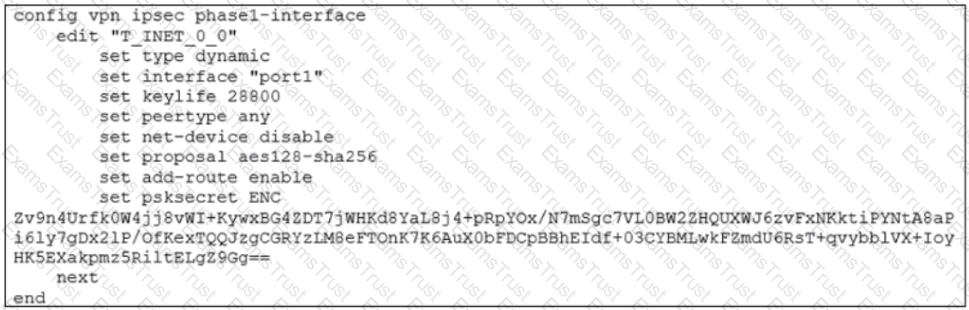
Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
Refer to the exhibits.
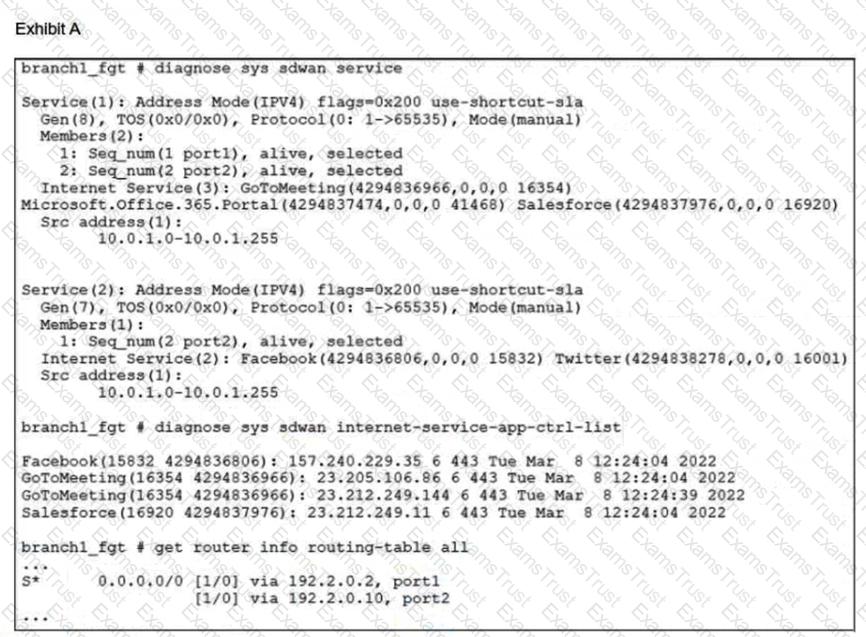
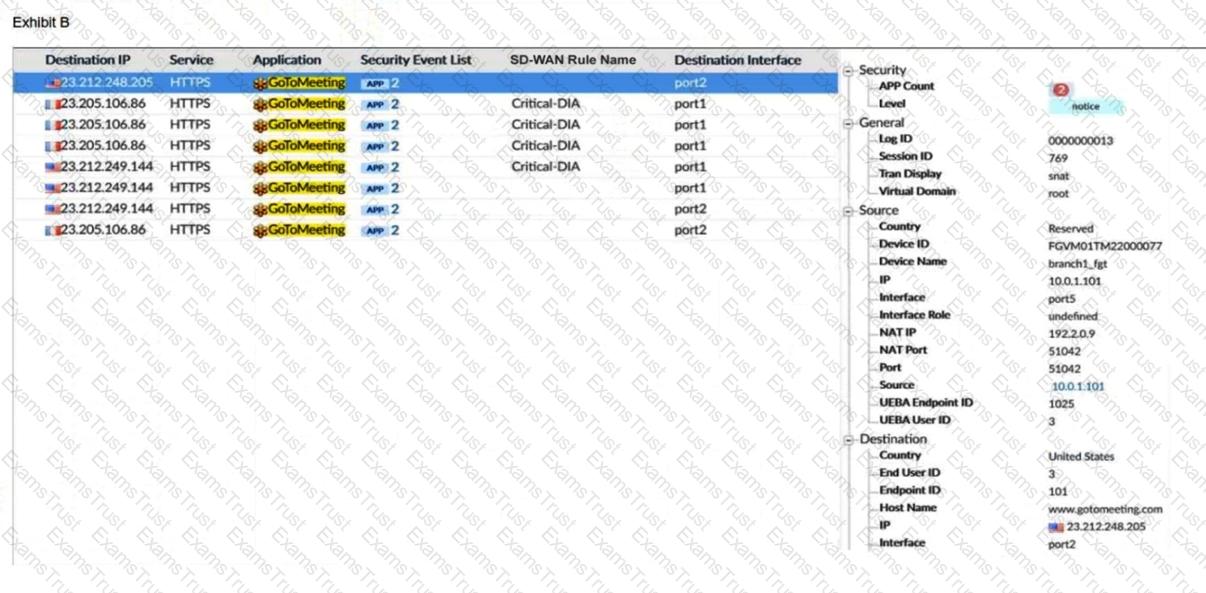
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in exhibit A.
After generating GoToMeeting test traffic, the administrator examined the respective traffic log on FortiAnalyzer, which is shown in exhibit B. The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why the traffic matched the implicit SD-WAN rule? (Choose two.)
Refer to the exhibit.
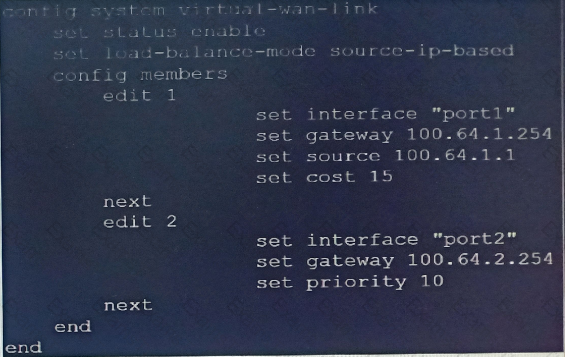
Based on the output shown in the exhibit, which two criteria on the SD-WAN member configuration can be used to select an outgoing interface in an SD-WAN rule? (Choose two.)
Refer to the exhibit.
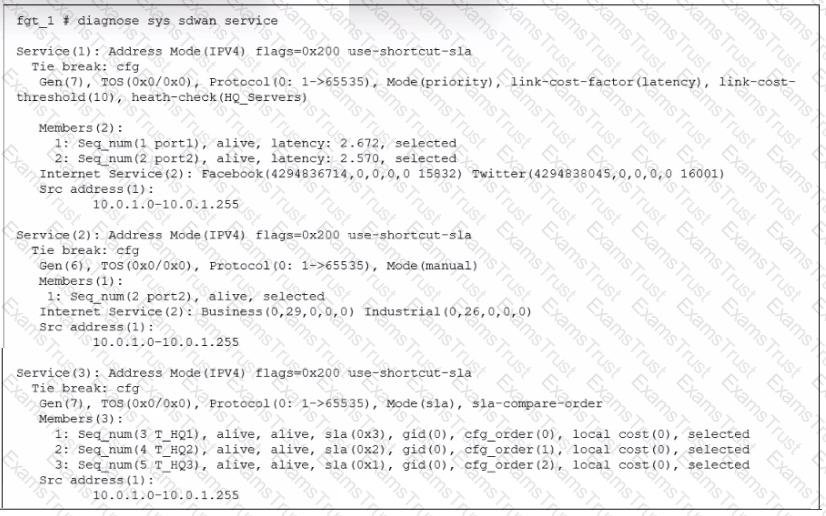
The exhibit shows output of the command diagnose 3vg sdwan service collected on a FortiGate device.
The administrator wants to know through which interface FortiGate will steer the traffic from local users on subnet 10.0.1.0/255.255.255.192 and with a destination of the business application Salesforce located on HO servers 10.0.0.1.
Based on the exhibits, which two statements are correct? (Choose two.)
In which SD-WAN template field can you use a metadata variable?
Which three matching traffic criteria are available in SD-WAN rules? (Choose three.)
Exhibit.
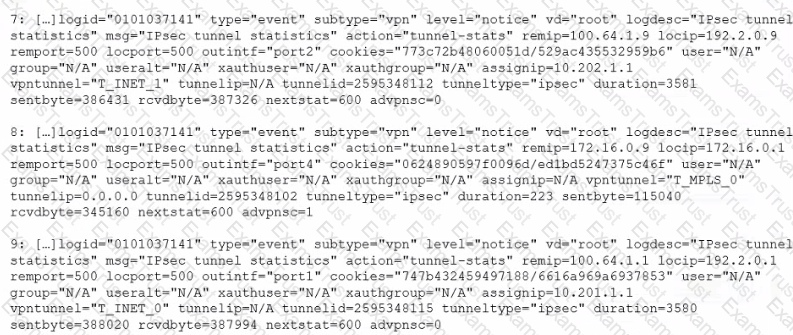
The exhibit shows VPN event logs on FortiGate. In the output shown in the exhibit, which statement is true?
Refer to the exhibits.
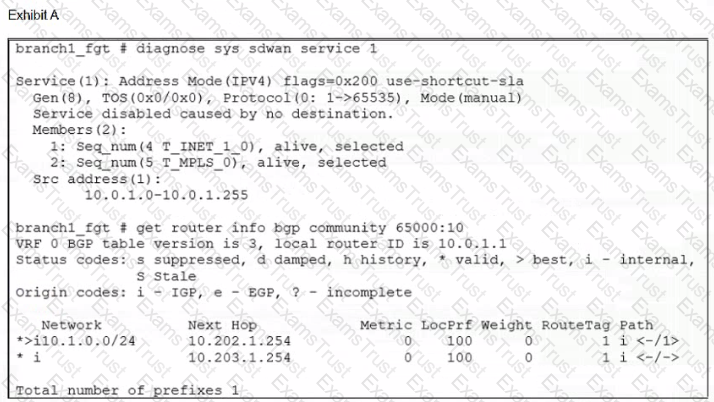
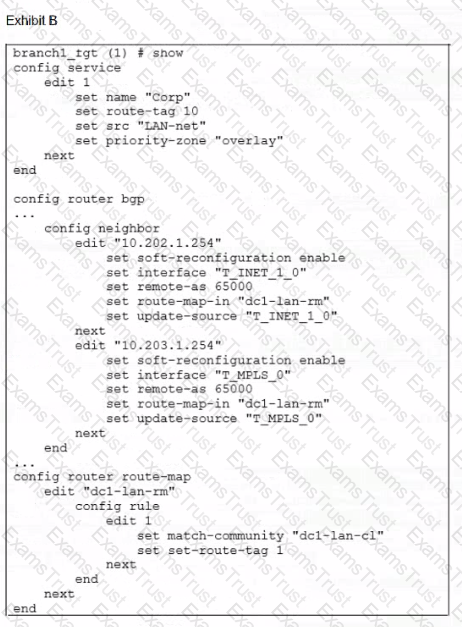
Exhibit A shows the SD-WAN rule status and the learned BGP routes with community 65000:10.
Exhibit B shows the SD-WAN rule configuration, the BGP neighbor configuration, and the route map configuration.
The administrator wants to steer corporate traffic using routes tags in the SD-WAN rule ID 1.
However, the administrator observes that the corporate traffic does not match the SD-WAN rule ID 1.
Based on the exhibits, which configuration change is required to fix issue?
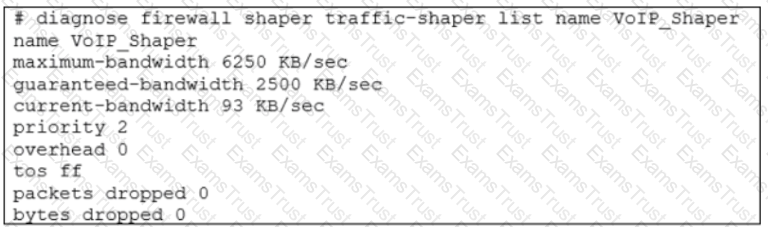
Which two conclusions for traffic that matches the traffic shaper are true? (Choose two.)