The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
in an operation technology (OT) network FortiAnalyzer is used to receive and process logs from responsible FortiGate devices
Which statement about why FortiAnalyzer is receiving and processing multiple tog messages from a given programmable logic controller (PLC) or remote terminal unit (RTU) is true'?
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
Refer to the exhibit.
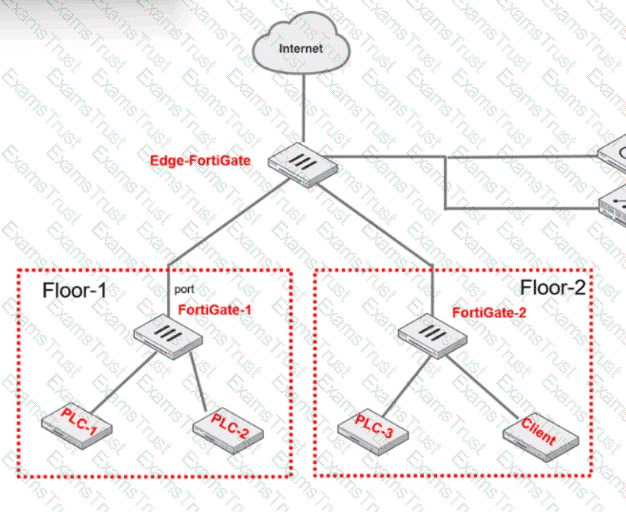
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2 level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
What can be assigned using network access control policies?
Refer to the exhibit.
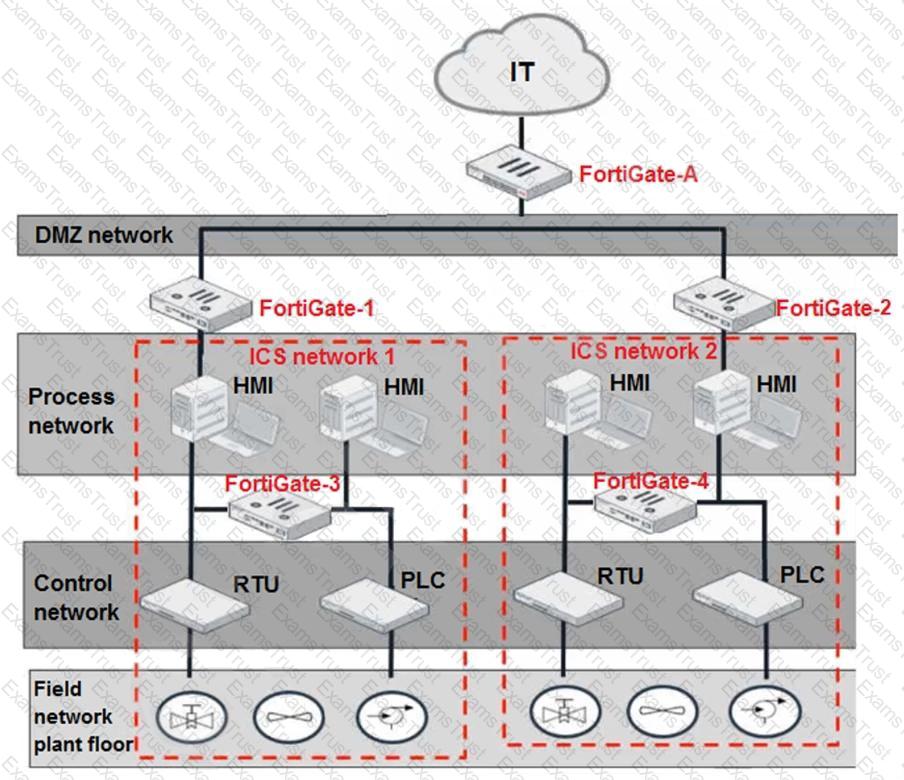
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
Refer to the exhibit.
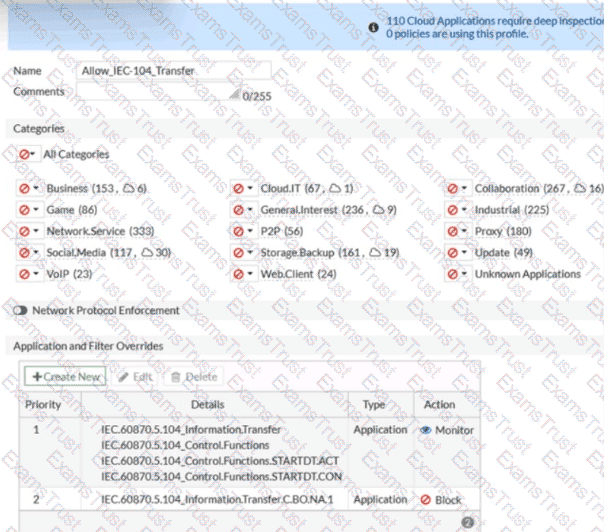
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
Refer to the exhibits.
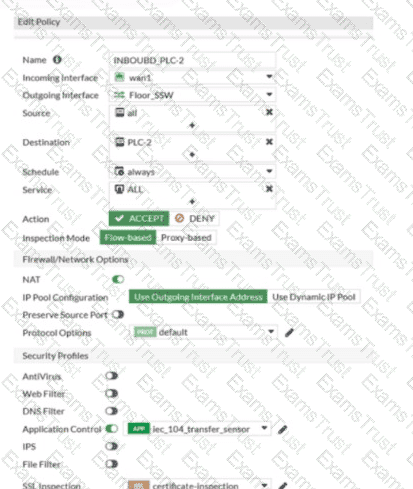
Which statement is true about the traffic passing through to PLC-2?
The OT network analyst run different level of reports to quickly explore failures that could put the network at risk. Such reports can be about device performance. Which FortiSIEM reporting method helps to identify device failures?
When you create a user or host profile, which three criteria can you use? (Choose three.)
Refer to the exhibits.
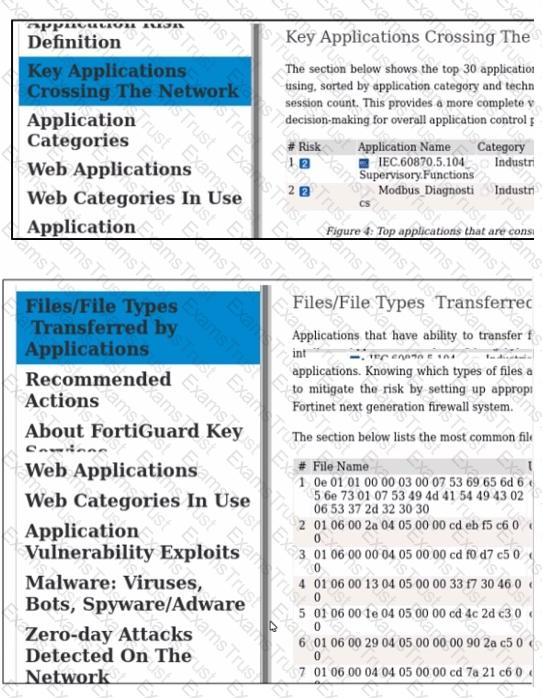
Which statement about some of the generated report elements from FortiAnalyzer is true?
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
FortiAnalyzer is implemented in the OT network to receive logs from responsible FortiGate devices. The logs must be processed by FortiAnalyzer.
In this scenario, which statement is correct about the purpose of FortiAnalyzer receiving and processing multiple log messages from a given PLC or RTU?
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
Refer to the exhibit.
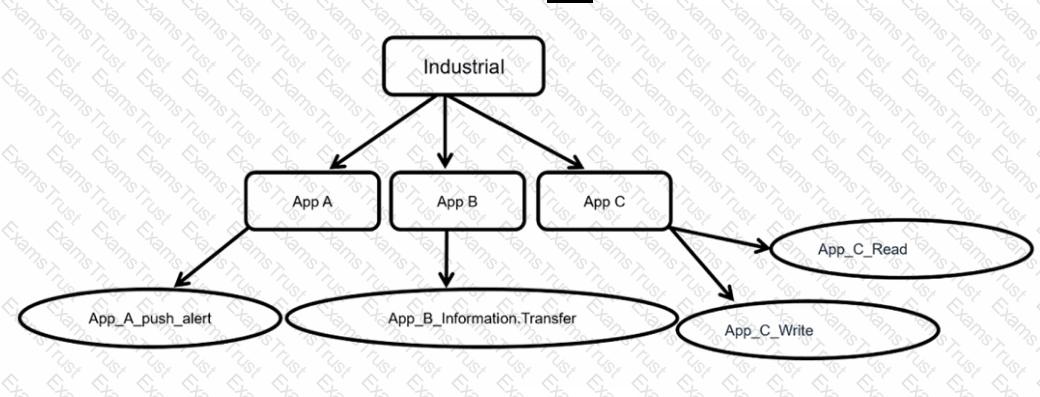
Which statement is true about application control inspection?
An OT network architect must deploy a solution to protect fuel pumps in an industrial remote network. All the fuel pumps must be closely monitored from the corporate network for any temperature fluctuations.
How can the OT network architect achieve this goal?
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)