Examine the Suspicious Indicators section of the scan job shown in the exhibit, then answer the following question:

Which FortiSandbox component identified the vulnerability exploits?
Which of the following actions are performed by FortiSandbox at the static analysis stage?
Which of the following are FortiWeb’s roles when integrated with FortiSandbox? (Choose two.)
Which FortiSandbox diagnostic command should you use to diagnose Internet connectivity issues on port3?
FortiSandbox generates structured threat information exchange (STIX) packages for which of the following threats? (Choose two.)
What information does a scan job report include? (Choose two.)
Examine the CLI configuration, than answer the following question:
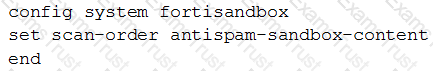
Which of the following statements is true regarding this FortiMail’s inspection behavior?
Which of the advanced threat protection solutions should you use to protect against an attacker may take during the lateral movement stage of the kill chain? (Choose two.)
Examine the virtual Simulator section of the scan job report shown in the exhibit, then answer the following question:
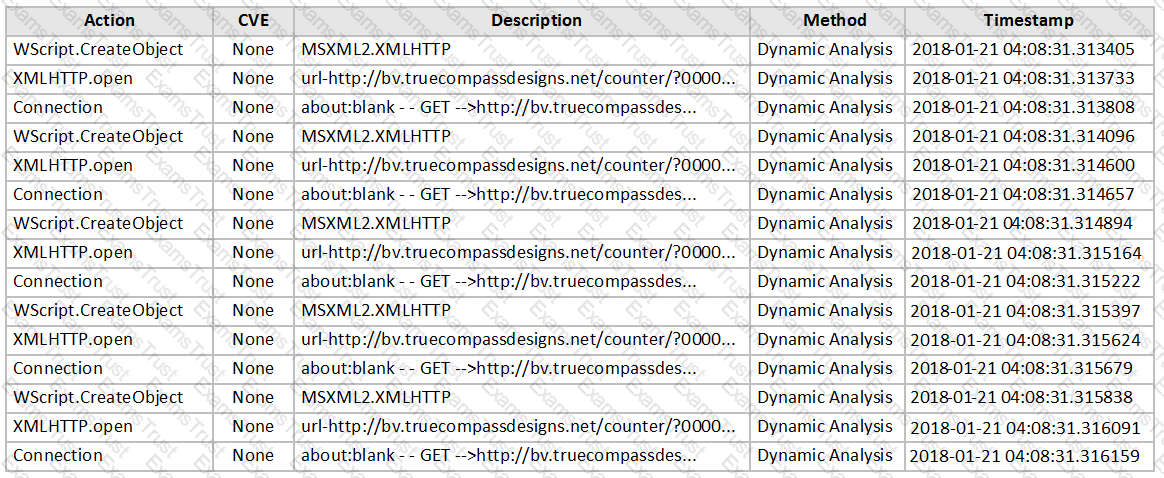
Based on the behavior observed by the virtual simulator, which of the following statements is the most likely scenario?