Which item is a supported one-time secure token for IBE authentication?
Refer to the exhibit, which shows a topology diagram of two separate email domains.
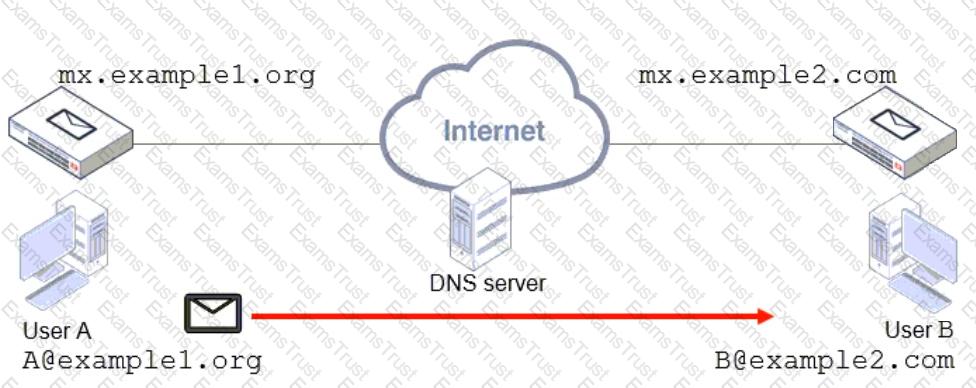
Which two statements correctly describe how an email message is delivered from User A to User B? (Choose two.)
Refer to the exhibit which displays a list of IBE users on a FortiMail device.
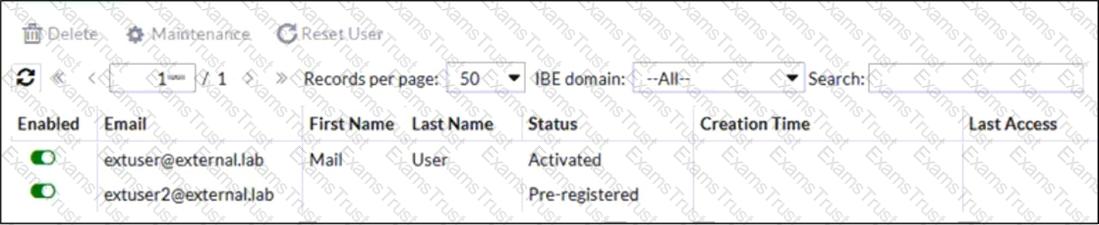
Which statement describes the pre-registered status of the IBE user extuser2@external.lab?
Refer to the exhibit which shows an nslookup output of MX records of the example.com domain.
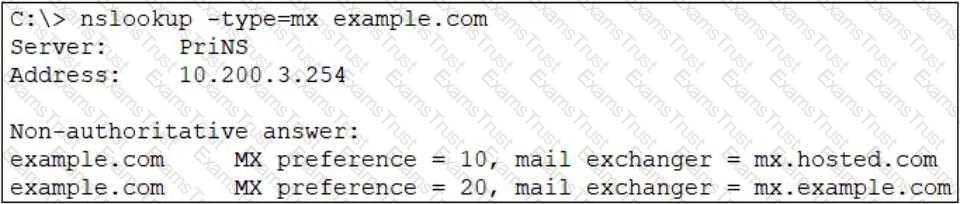
Which two MTA selection behaviors for the example.com domain are correct? (Choose two.)
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
In which FortiMail configuration object can you assign an outbound session profile?
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Refer to the exhibits which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
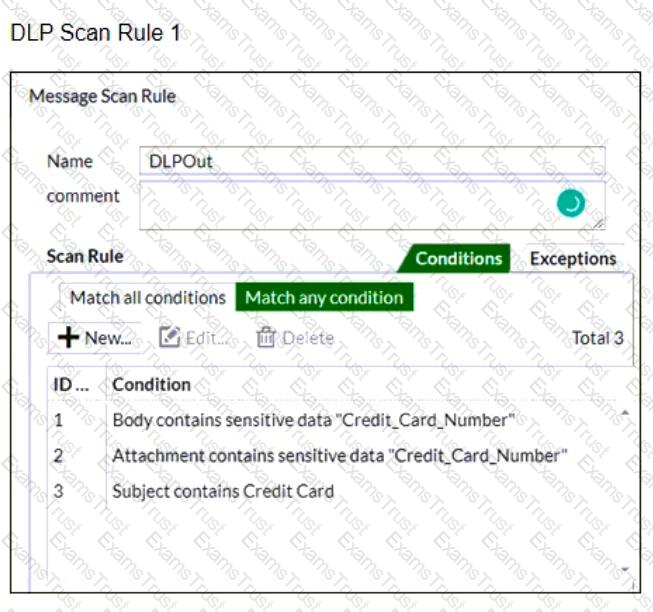
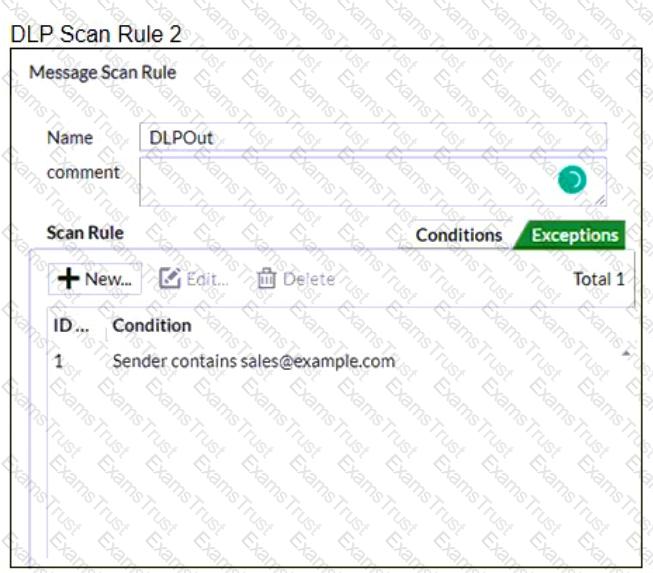
Which two message types will trigger this DLP scan rule? (Choose two.)