Refer to the exhibits.

Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the internet through FortiSASE, while Windows-AD can no longer access the internet.
Based on the information in the exhibits, which reason explains the outage on Windows-AD?
Which two advantages does FortiSASE bring to businesses with microbranch offices that have FortiAP deployed for unmanaged devices? (Choose two.)
Refer to the exhibits.
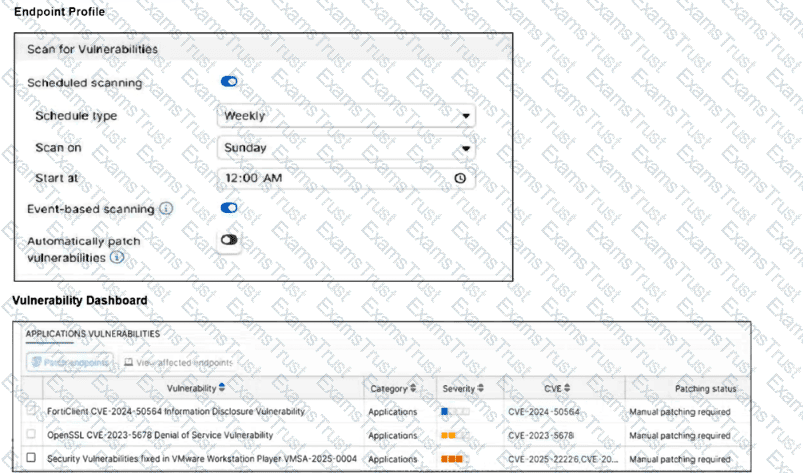
How will the application vulnerabilities be patched, based on the exhibits provided?
Which description of the FortiSASE inline-CASB component is true?
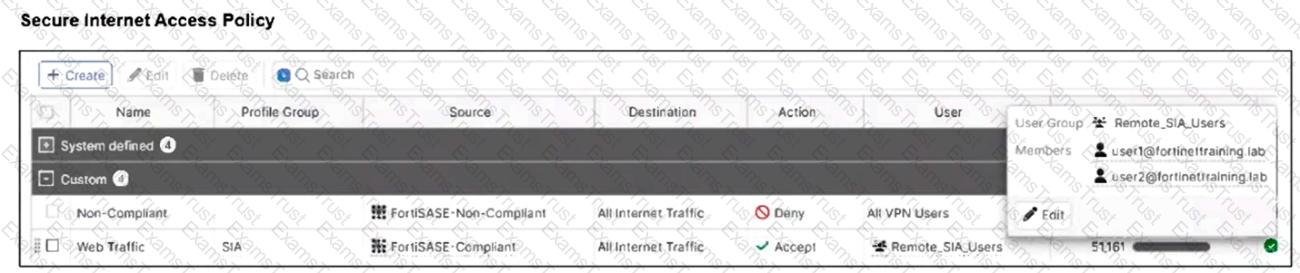
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?
Refer to the exhibit.
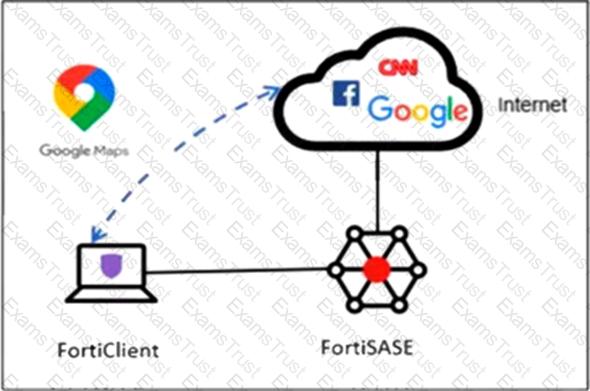
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
Refer to the exhibits.
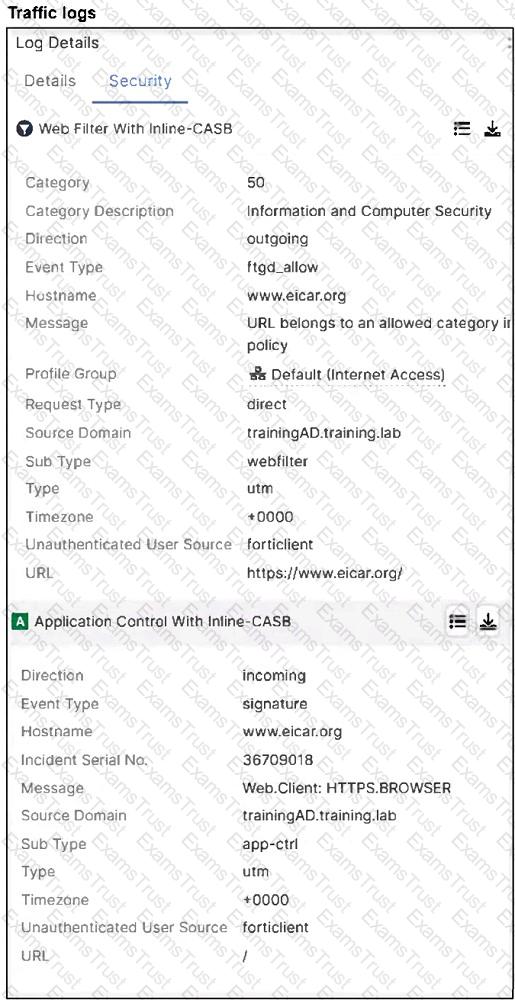
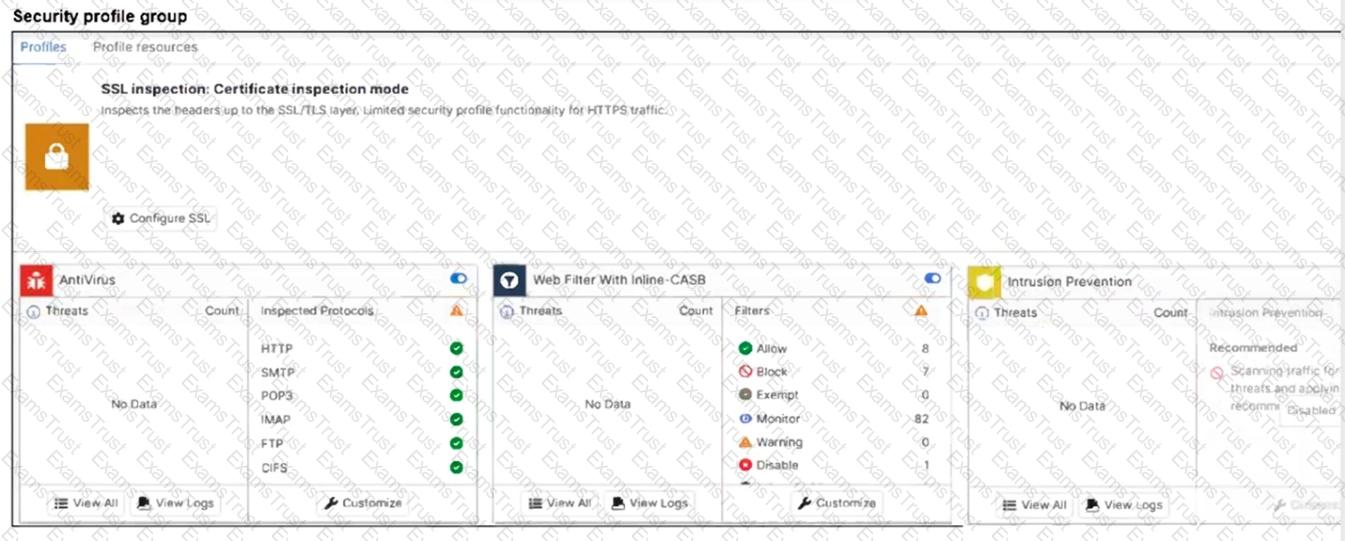
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from
Which configuration on FortiSASE is allowing users to perform the download?
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Refer to the exhibit.
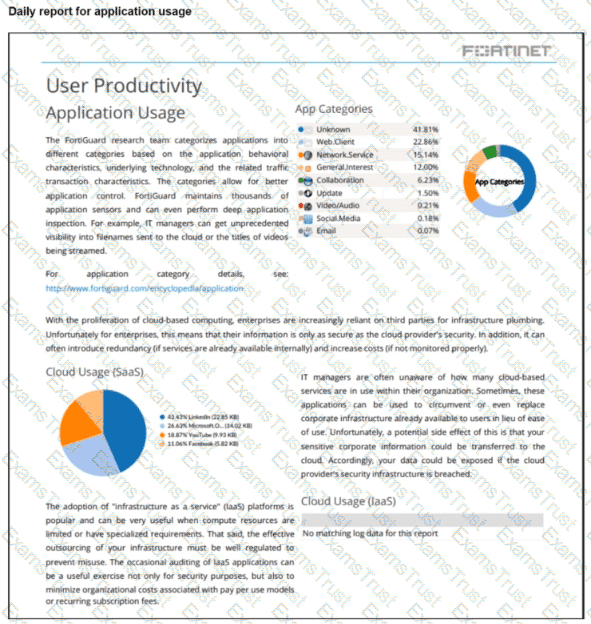
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
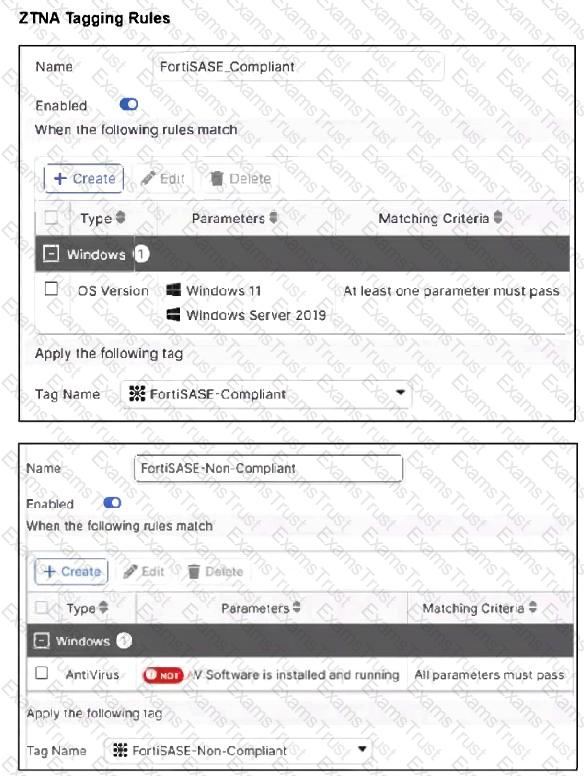
Refer to the exhibits.
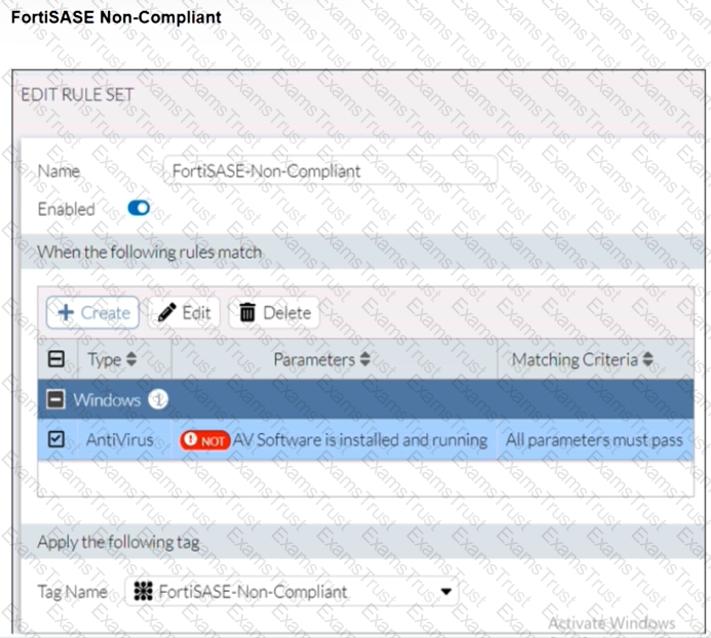
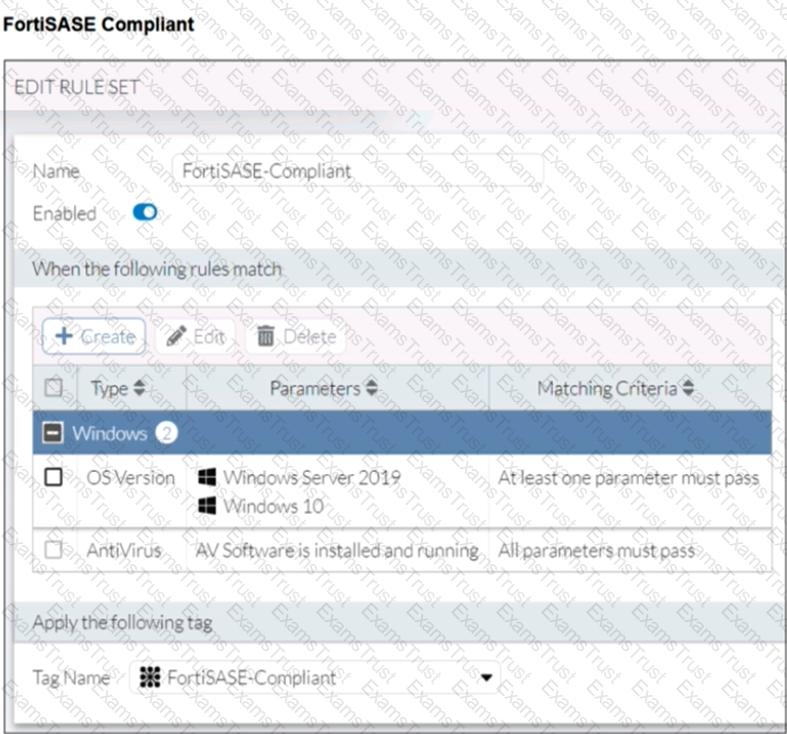
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?
Refer to the exhibit.
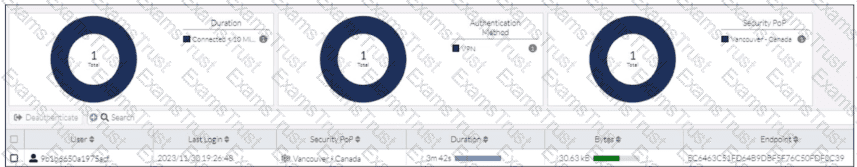
While reviewing the traffic logs, the FortiSASE administrator notices that the usernames are showing random characters.
Why are the usernames showing random characters?
Which information can an administrator monitor using reports generated on FortiSASE?
How does FortiSASE hide user information when viewing and analyzing logs?
Which statement applies to a single sign-on (SSO) deployment on FortiSASE?