Which statement applies to a single sign-on (SSO) deployment on FortiSASE?
Which event log subtype captures FortiSASE SSL VPN user creation?
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE component facilitates this always-on security measure?
Which FortiSASE feature ensures least-privileged user access to all applications?
Refer to the exhibits.
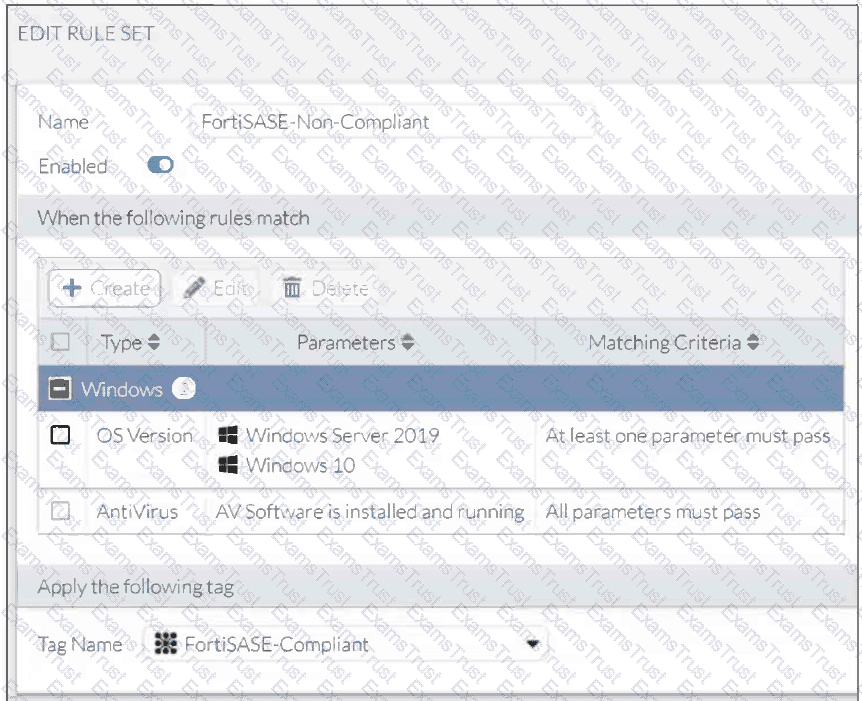
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?
What are two advantages of using zero-trust tags? (Choose two.)
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which three setups will achieve the above requirements? (Choose three.)
How does FortiSASE hide user information when viewing and analyzing logs?
Refer to the exhibit.
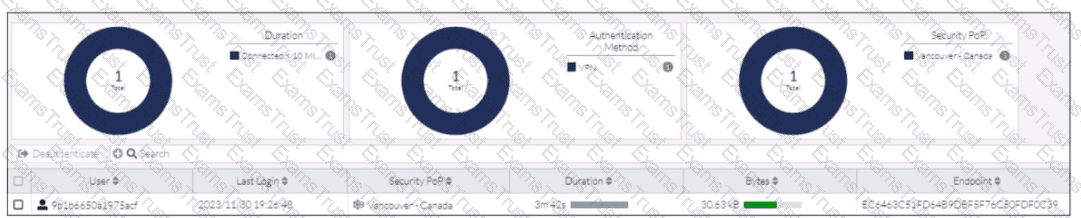
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Refer to the exhibit.
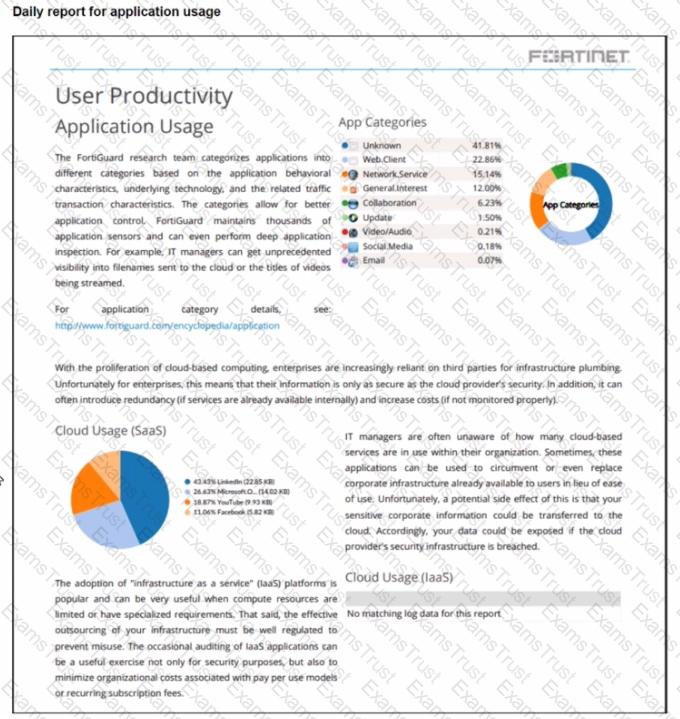
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)