What are two reasons that an OSPF router does not have any type 5 tank-state advertisements (LSAs) In its link-stale database (LSD6)? (Choose two.)
Refer to the exhibit.
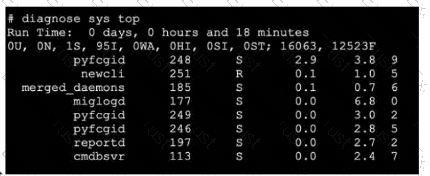
Which three pieces of information does the diagnose sys top command provide? (Choose three.)
Refer to the exhibit, which contains the output of diagnose vpn tunnel list.
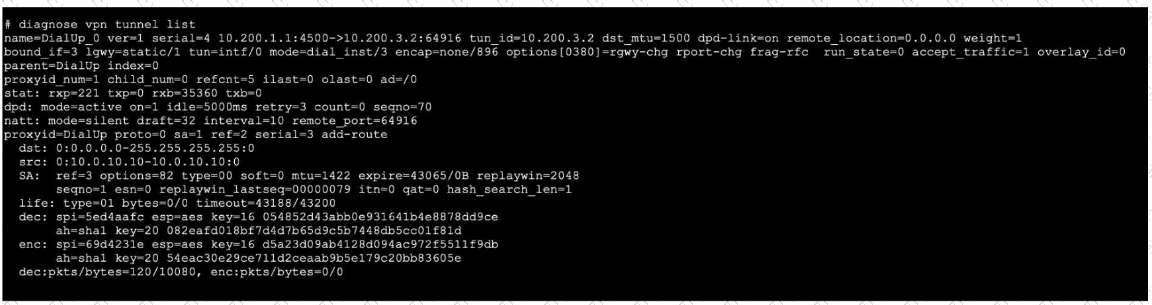
Which command will capture ESP traffic for the VPN named DialUp_0?
Exhibit.
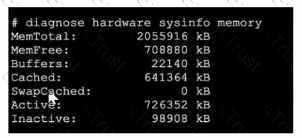
Refer to the exhibit, which shows a partial output of diagnose hardware aysinfo memory.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit, which shows the modified output of the routing kernel.
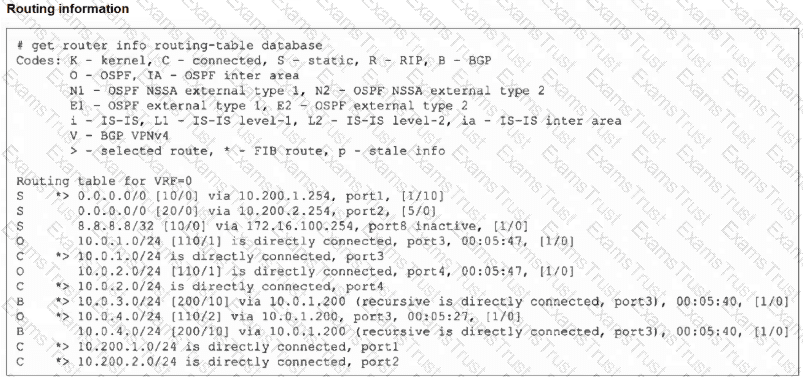
Which statement is true?
Refer to the exhibits.
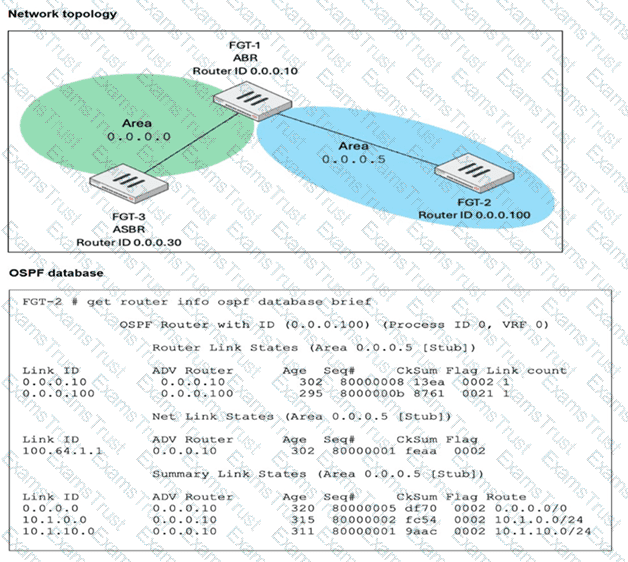
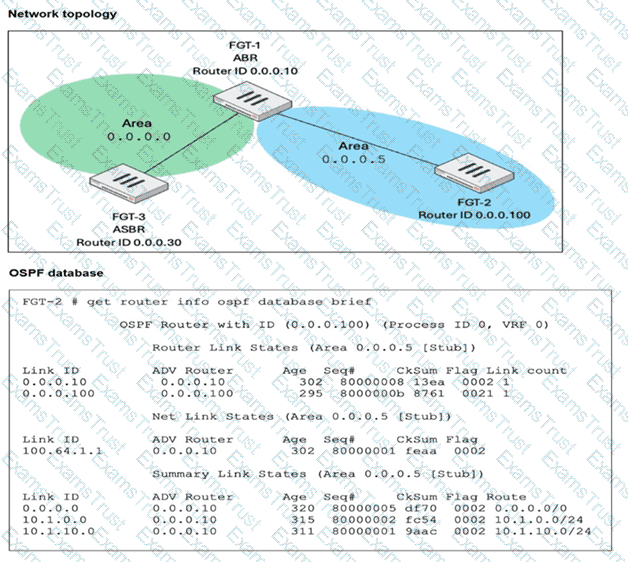
FGT-1 is an area border router (ABR) that has interfaces in OSPF areas 0.0.0.0 and 0.0.0.5. FGT-3 acts as an autonomous system border router (ASBR), importing static routes into OSPF. FGT-2 is an internal router with all its interfaces belonging to area 0.0.0.5. FGT-1 is receiving all advertised routes from FGT-2, however, FGT-3 is not receiving any of the advertised routes from FGT-1. What is the most likely reason for this? (Choose one answer)
Refer to the exhibit.
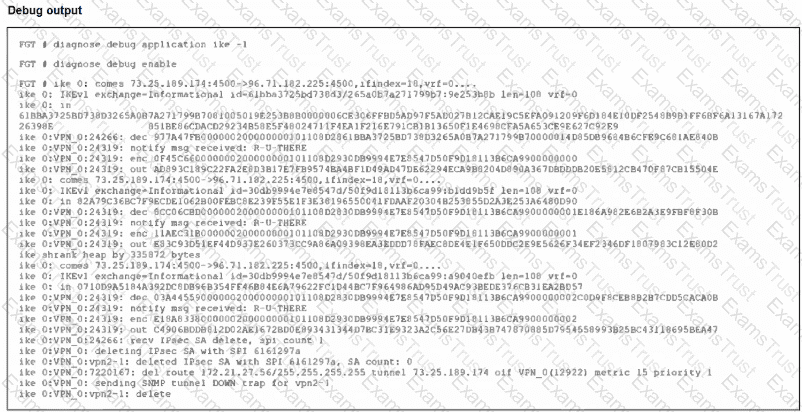
An IPsec VPN tunnel is dropping, as shown by the debug output.
Analyzing the debug output, what could be causing the tunnel to go down?
A FortiGate administrator is troubleshooting a VPN that is failing to establish.
As a first step, the administrator is attempting to sniff the traffic using the command:
# diagnose sniffer packet any ‘’udp port 500 or udp port 4500 or esp’’ 4
After several minutes there is still no output. What is the most Likely reason for this?
Which two statements about an auxiliary session ate true? (Choose two.)
Exhibit.
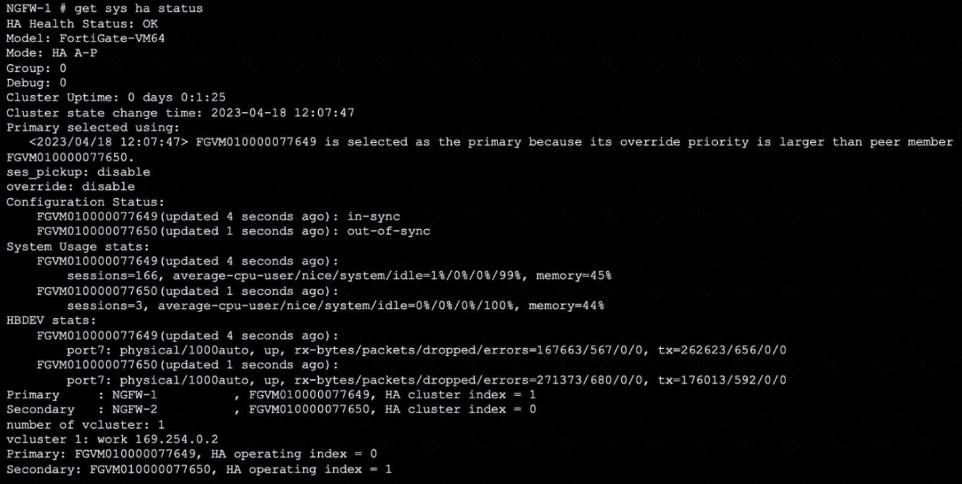
Refer to the exhibit, which shows the output of get system ha status.
NGFW-1 and NGFW-2 have been up for a week.
Which two statements about the output are true? (Choose two.)
While troubleshooting a FortiGate web filter issue, users report that they cannot access any websites, even though those sites are not explicitly blocked by any web filter profiles that are applied to firewall policies.
What are the three most likely reasons for this behavior? (Choose three answers)
Refer to the exhibit, which shows the output of a policy route table entry.
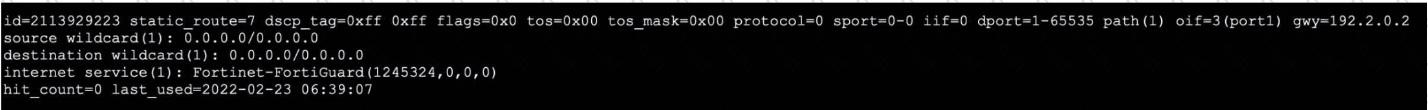
Which type of policy route does the output show?
Exhibit.
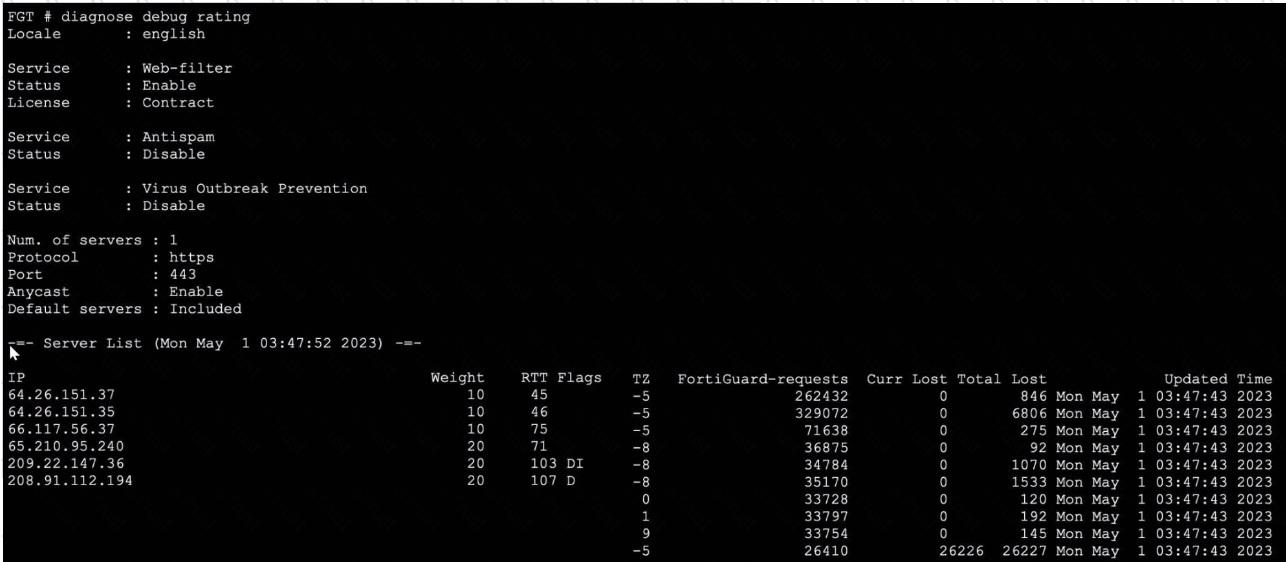
Refer to the exhibit, which shows the output of a diagnose command.
What can you conclude about the debug output in this scenario?
Refer to the exhibit, which a network topology and a partial routing table.
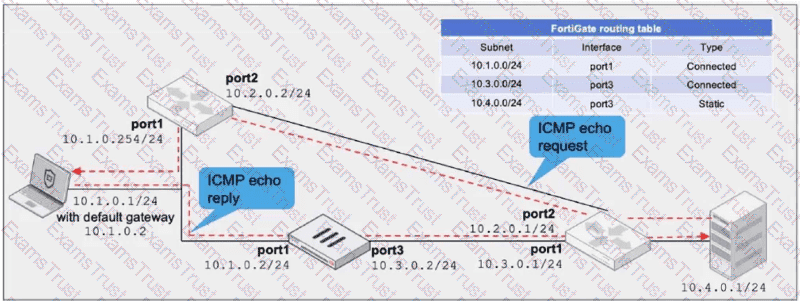
FortiGate has already been configured with a firewall policy that allows all ICMP traffic to flow from port1 to port3.
Which changes must the administrator perform to ensure the server at 10.4.0.1/24 receives the echo reply from the laptop at 10.1.0.1/24?
What are two reasons you might see iprope_in_check() check failed, drop when using the debug flow? (Choose two.)
Refer to the exhibit, which shows the output of diagnose sys session list.
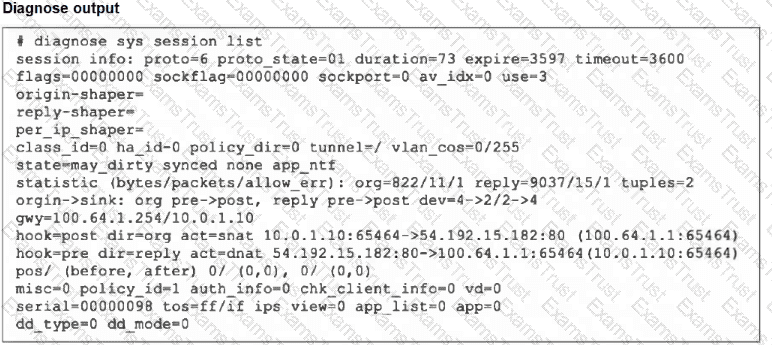
If the HA ID for the primary device is 0, what happens if the primary fails and the secondary becomes the primary?
What are two functions of automation stitches? (Choose two.)
In a Security Fabric environment which three actions must you take to ensure successful communication among the nodes? (Choose three.)
Refer to the exhibit, which shows a partial web filter profile configuration.
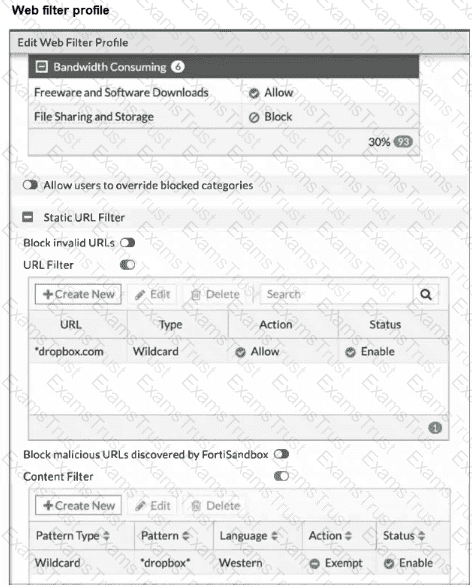
The URL is categorized as File Sharing and Storage.
Which action does FortiGate take if a user attempts to access
Consider the scenario where the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate. Which two actions will FortiGate take when using the default settings for SSL certificate inspection? (Choose two answers)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
Exhibit.
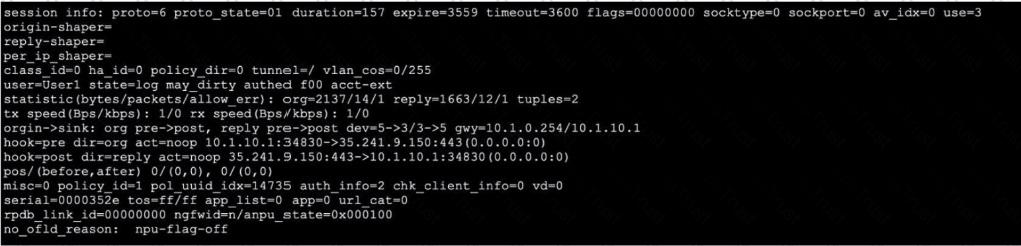
Refer to the exhibit, which shows the output of a session. Which two statements are true? (Choose Iwo.)
Refer to the exhibit.
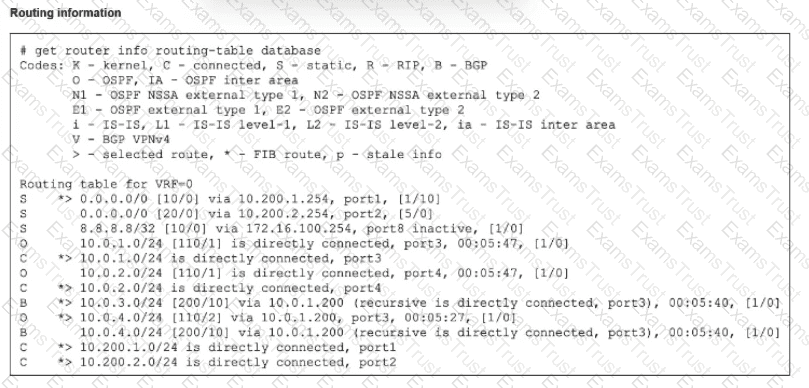
The modified output of live routing kemel is shown
Which two statements about the output are (rue? (Choose two.)
Refer to the exhibit, which shows the output of get router info bgp summary.
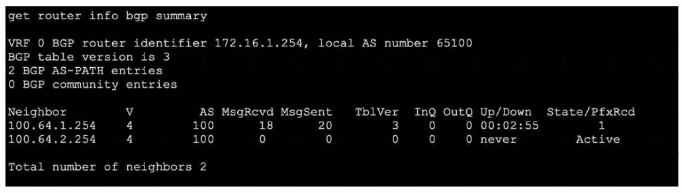
Which two statements are true? (Choose two.)
Refer to the exhibit.
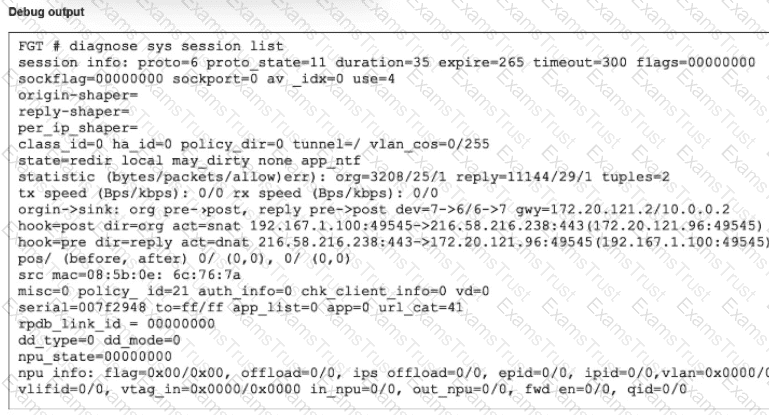
Which Iwo statements about FortiGate behavior relating to this session are correct? (Choose two.)
Refer to the exhibit.
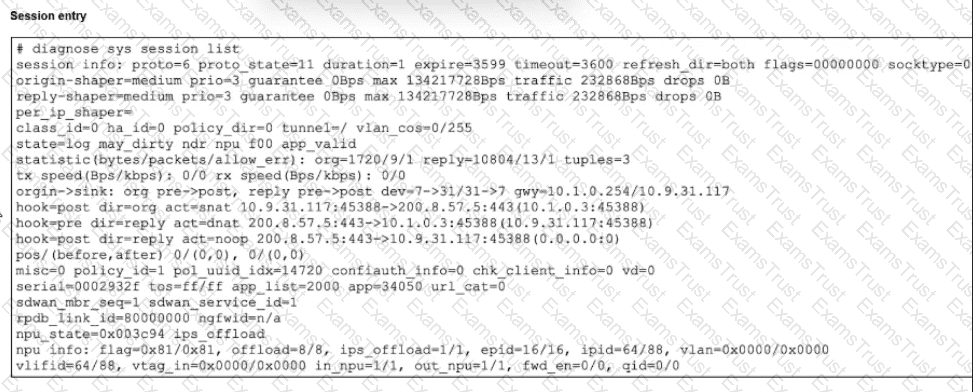
The exhibit shows a session entry.
Which statement about this TCP session is true?
Refer to the exhibit.
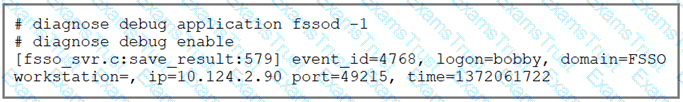
Partial output of the fssod daemon real-time debug command is shown. Which two conclusions can you draw from the output? (Choose two answers)
When FortiGate enters conserve mode because of memory pressure, which action can FortiGate perform to preserve memory?
Exhibit 1.
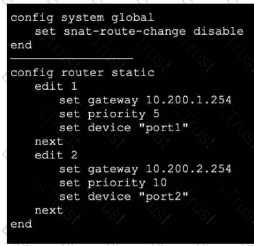
Exhibit 2.
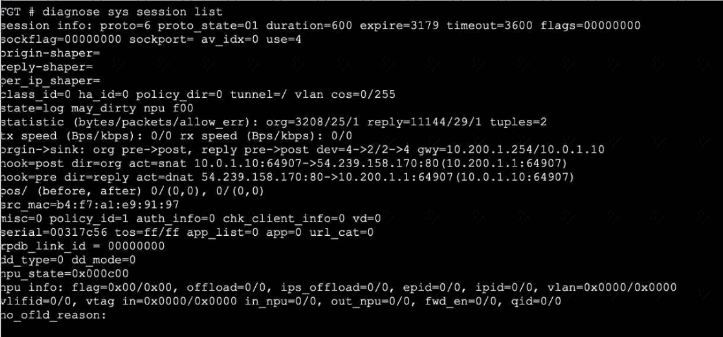
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
An administrator would like to lest session failover between the two service provider connections.
Which two changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
Refer to the exhibits,
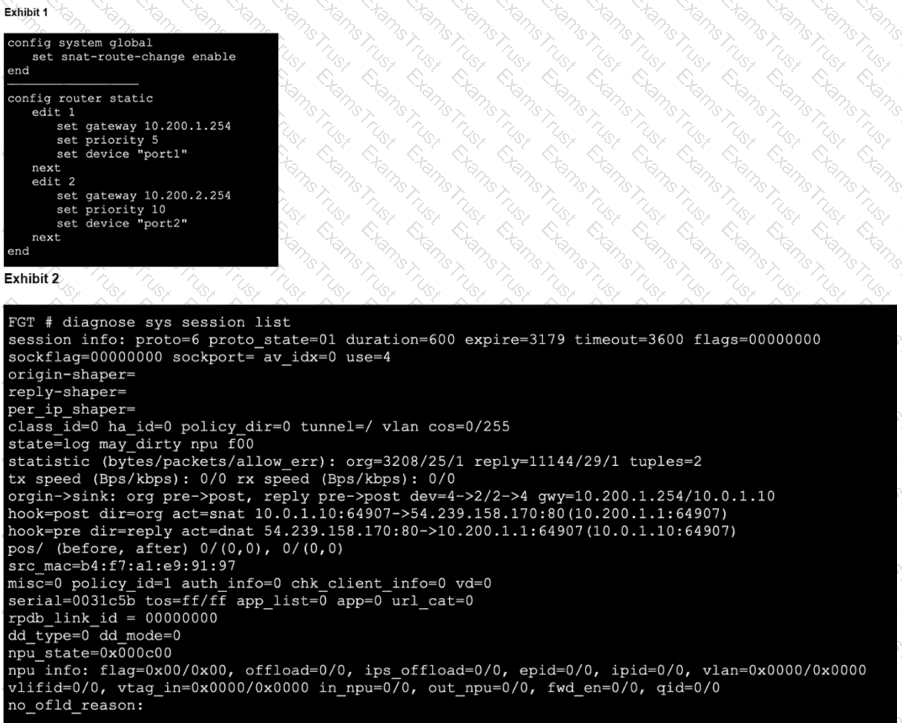
which show the configuration on FortiGate and partial session information for internet traffic from a user on the internal network. If the priority on route ID 2 were changed from 10 to 0, what would happen to traffic matching that user session? (Choose one answer)