A company that acquired multiple branches across different countries needs to install new FortiGate devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations on remote branches? (Choose three.)
An administrator needs to install an IPS profile without triggering false positives that can impact applications and cause problems with the user's normal traffic flow.
Which action can the administrator take to prevent false positives on IPS analysis?
What does the command set forward-domain
An administrator received a FortiAnalyzer alert that a 1 ТВ disk filled up in a day. Upon investigation, they found thousands of unusual DNS log requests, such as JHCMQK.website.com, with no answers. They later discovered that DNS exfiltration was occurring through both UDP and TLS.
How can the administrator prevent this data theft technique?
Refer to the exhibits.
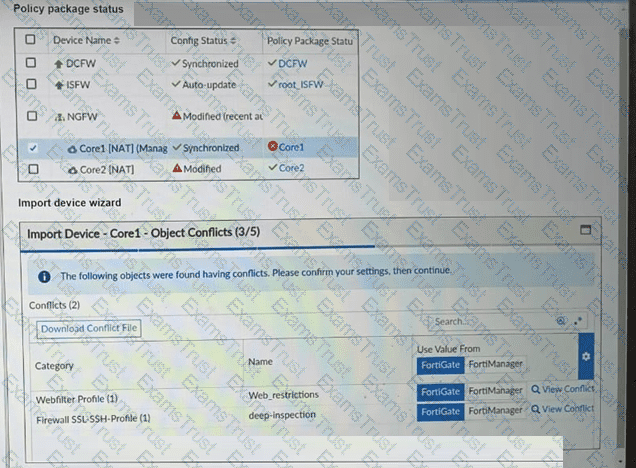
A policy package conflict status and information from the import device wizard in the Core1 VDOM are shown. When you import a policy package, the following message appears for the Web_restrictions web filter profile and the deep-inspection SSL-SSH profile: "The following objects were found having conflicts. Please confirm your settings, then continue." The Web_restrictions and deep-inspection profiles are used by other FortiGate devices within FortiManager. Which step must you take to resolve the issue? (Choose one answer)
An administrator is designing an ADVPN network for a large enterprise with spokes that have varying numbers of internet links. They want to avoid a high number of routes and peer connections at the hub.
Which method should be used to simplify routing and peer management?
Refer to the exhibit, which shows the ADVPN IPsec interface representing the VPN IPsec phase 1 from Hub A to Spoke 1 and Spoke 2, and from Hub В to Spoke 3 and Spoke 4.
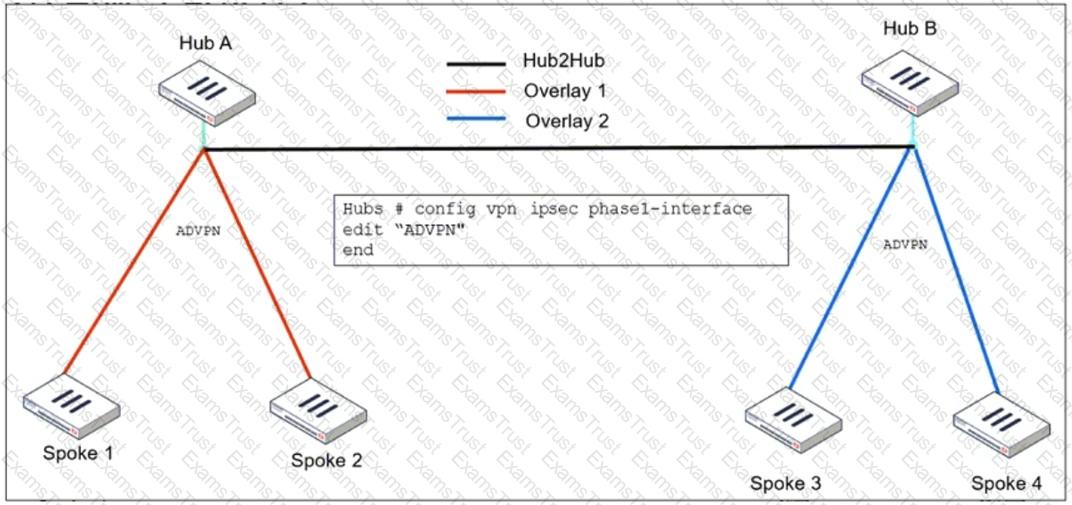
An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with 2.
What must the administrator configure in the phase 1 VPN IPsec configuration of the ADVPN tunnels?
Refer to the exhibit, which shows the VDOM section of a FortiGate device.
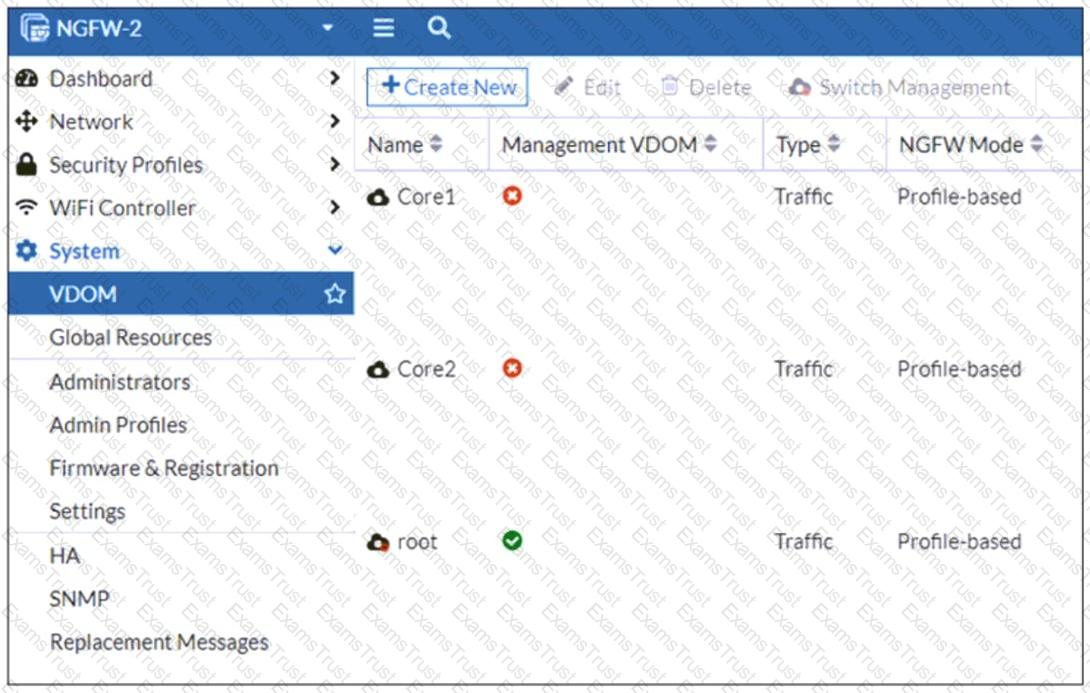
An administrator discovers that webfilter stopped working in Core1 and Core2 after a maintenance window.
Which two reasons could explain why webfilter stopped working? (Choose two.)
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
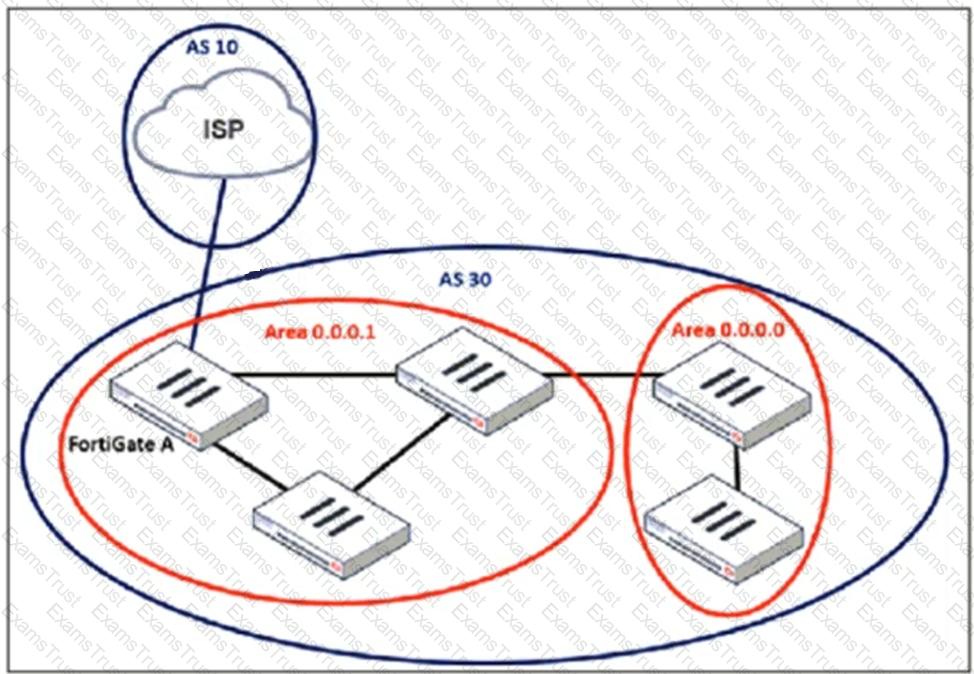
An administrator must configure a loopback as a BGP source to connect to the ISP.
Which two commands are required to establish the connection? (Choose two.)
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Refer to the exhibit, which shows a network diagram showing the addition of site 2 with an overlapping network segment to the existing VPN IPsec connection between the hub and site 1.
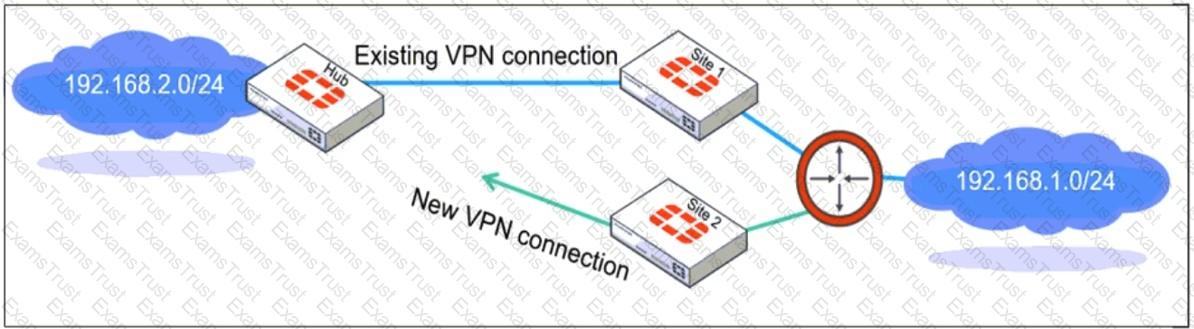
Which IPsec phase 2 configuration must an administrator make on the FortiGate hub to enable equal-cost multi-path (ECMP) routing when multiple remote sites connect with overlapping subnets?
Refer to the exhibit, which shows the HA status of an active-passive cluster.

An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?
Refer to the exhibit, which shows an ADVPN network.
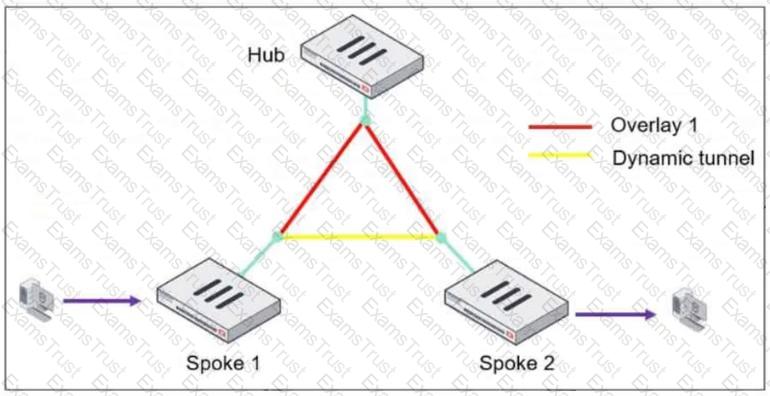
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
An administrator must standardize the deployment of FortiGate devices across branches with consistent interface roles and policy packages using FortiManager.
What is the recommended best practice for interface assignment in this scenario?
Refer to the exhibit, which shows the packet capture output of a three-way handshake between FortiGate and FortiManager Cloud.
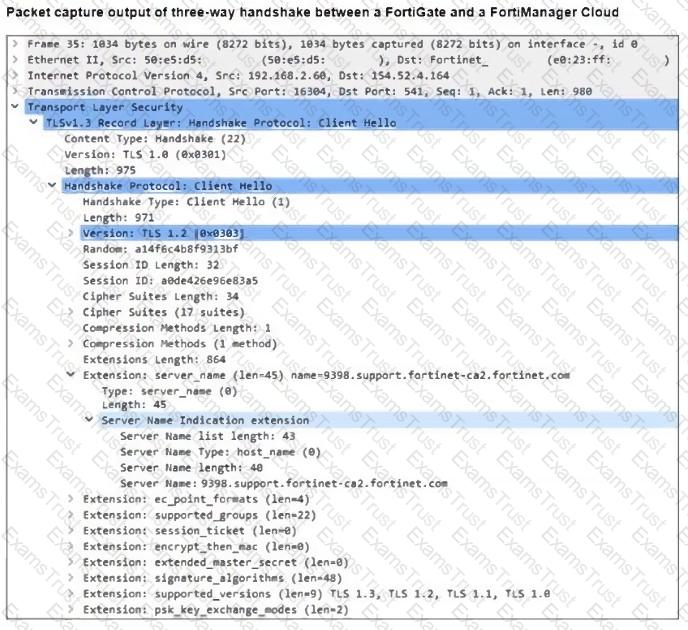
What two conclusions can you draw from the exhibit? (Choose two.)
An administrator applied a block-all IPS profile for client and server targets to secure the server, but the database team reported the application stopped working immediately after.
How can an administrator apply IPS in a way that ensures it does not disrupt existing applications in the network?
Refer to the exhibit, which shows an OSPF network.
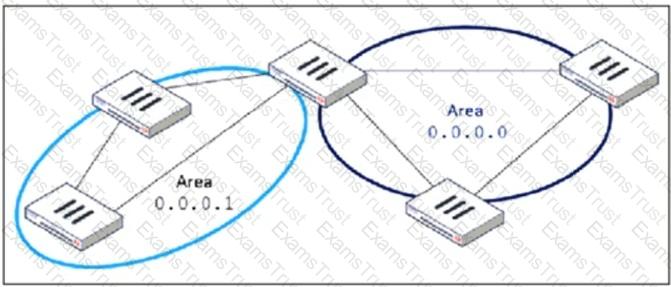
Which configuration must the administrator apply to optimize the OSPF database?
Refer to the exhibit.
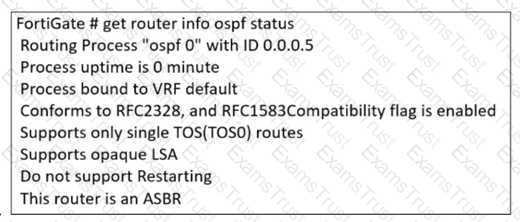
The partial output of an OSPF command is shown. You are checking the OSPF status of a FortiGate device when you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)