An administrator security policy defines allowed URLs, file types and parameter values Which security model is the administrator using?
Ping and Traceroute outputs are provided for a connectivity issue.
What is the cause of these results?
A company deploys F5 load balancers to manage a large number of secure applications. The company manage certificates. Which F5 provides this functionality?
What advantage does an active-standby configuration have over an active-active configurations?

A BIG IP Administrator needs to create a virtual server for a new secure end-to-end web application After change in configuration the virtual server .3 still marked down. The configuration of the virtual server and the pool member are correct. A quick server shows the status.
To fix the issue, what should the BIG-IP Administrator inform the web server administrator to do?
Which protocol data unit (PDU) is associated with the OSI model’s Transport layer?
A VoIP application requires that data payloads will NOT be fragmented. Which protocol controls network behavior in this situation?
Tl SISSL prides which functionary when a web browser connects to web site using the HTTPS protocol?
In which scenario is a packet forwarding architecture required?
Which two destination pods should be used in a default active FTP Session? (Choose two)
Which high availability feature allows two different BIG-IP devices to use the MAC address for the same server IP?
10:20: 37 .00749:IP 199.16.255.254.36664>10.0.1.10 http : flags (s) seq 700424862, Win 29200
A website is fronted by a toad balancer that implements a full proxy architecture with SNAT enabled Behind the load balancer there are bro nodes Node 1 and node2
She administrator is debugging an issue on node 1 using icpdump and records the above out about a received packet o watch device does the IP address 192 168 265 254" belong?
Which type of certificate is pre-installed in a web browser’s trusted store?
What are the two primary functions of the OSI 7 layer model (Choose two)
ARP provides translation between which two address types?
The BIG IP device is connected to the same network as a server
Which communication protocol will the BIG IP device use to discover the link layer address of the server?
What describes the third ‘’A’’ in the common authentication acronym AAA?
ICMP is used by which command line tool?
A company is creating a new department for Security Engineering and needs to create a segregated network segment with only 24 IPS.
What should be configured?
Which support service is required to synchrony the time stamps in system logs from these devices?
In which FTP mode is the serve, responsible for initiating the data correction back to the client?
An administrator is currently designing the IP addressing scheme for a small company. They have been asked to use the 192. 168. 100 x block of addresses with a /27 network prefix. How many networks and hosts per network will be available when using the 27-bit network prefix.
HTTPs traffic is not working properly.
What is the likely reason for the issue?
In an administrator's environment, the administrator wants to inspect a high volume of SSL traffic
What should be used for this task?
A server is operating on the network 10.100/24. The BIG-IP device is operating on the 192.168.0.0/24 net. What is required to enable the several and BIG-IP device to communicate properly?
An administrator needs to lower .he amount of new TCP connections to help with network congest?
How should the administrator accomplish this?
Where is the MAC masquerade address configured?
An application has a mix of both and short and long lived connections. Which algorithm would provide and event distributionof all connections across the pool?
What does the HTTP status code 404 mean?
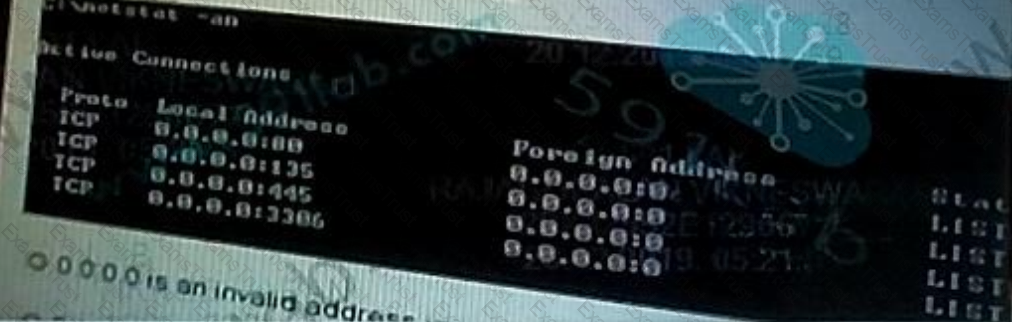
Given the service list of a server shown, the administrator needs to determine why users are unable to resolve the IP address .
What is the causing this issue?
A messaging system digitally signs messages to ensure non-repudiation of the sender. Which component should the receiver use to validate the message?
The 2001:db8: : IP6 address block is allocated to a load balancer for use as virtual server addresses. The address block is routed to a balancer self IP address using a static route. What is the correct representation for the last address in the address block that a virtual server can use?
Web application at 10.10.1.1.110, is unresponsive. A recent change migrated DNS to a new platform
in which scenario is a full proxy TCP connection required?
A BIG-IP administrator is interested in using some of the vCMP
What should impact the administrator's decision?
Which protocol data unit (PDU) is associated with the OSI model Network layer?