A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?
Which statement is true regarding virtual provisioning?
Which block storage volume allocates all of the physical storage specified at the time it is created?
A host sends one write /O to the RAID 1 array.
How many writes does it take for the array to store the data?
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
What occurs when a company’s IT infrastructure security is breached by a passive attack?
Refer to the Exhibit:
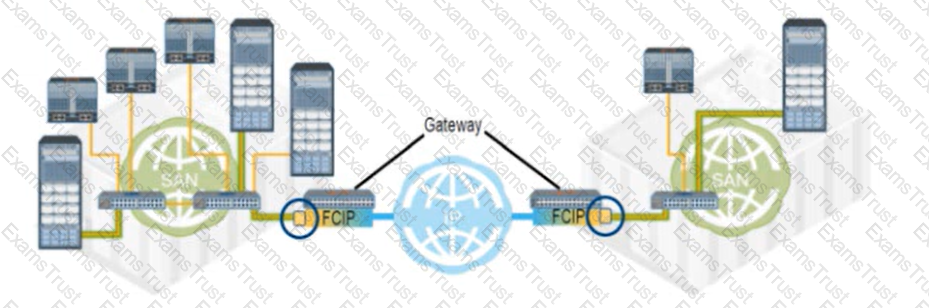
What type of FC port connects each FCIP gateway to each FC SAN?
What is an accurate statement regarding virtual LANs?
What is a goal of cyber recovery?
Which interface does an SCM device use to connect to intelligent storage system controllers?
Which plane of the SDDC architecture provides a CLI and GUI for IT to administrator the infrastructure and to configure policies? (Choose Correct Answer from Associate - Information Storage and Management version 5 Manual from dellemc.com and give explanation)
An organization is planning to secure the connection between the data center and cloud while performing data backup and replication.
Which security control mechanism will help organization to achieve the desired security?
What is a function of VM hardening?
Why is it important for organizations to store protect and manage their data?
The Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port 4 occurs as follows:
Monday = 8 PM to 11 PM -
Wednesday = 7 PM to 10 PM -
Thursday = 6 AM to 12 PM -
What is the MTTR of Port 4?
An IT organization wants to deploy four FC switches for compute and storage system connectivity. To meet performance requirements, a maximum of one active ISL and redundant ISLs for their compute to storage traffic.
Which FC SAN topology should be recommended?
Which backup component maintains the catalog containing details about the backups that have occurred?
An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday.
However, a failure of Port 7 occurs as follows:
● Monday=4 PM to 11 PM
● Wednesday= 2 PM to 10 PM
● Friday= 5 AM to11 AM
What is the MTTR of Port 7?
Which backup component sends metadata and tracking information about each backup to the system that maintains this information?
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
What is a key benefit for deploying a remote data protection and recovery solution in a data center environment?