Which platform provides a converged infrastructure solution?
Identify the bare-metal hypervisors?
What is true of a cloud service design best practice?
What does a service attribute specify?
Which is a lightweight, stand-alone, executable package that consists of whole runtime environment to execute the application?
What is a characteristic of an object-based storage system?
What is the effect of a denial-of-service attack?
A cloud provider installs a virtual firewall on a hypervisor to reduce the scope of a security breach when there is already a network-based firewall deployed in the cloud environment.
Which strategy did the cloud provider use to mitigate the risk of security threats?
Identify a threat caused, when an attacker sends massive quantities of data to the target with the intention of consuming bandwidth.
What term refers to the entry points from which an attack can be launched?
Which backup service deployment is utilized when a backup is performed in a consumer location and then the backup data is sent to the cloud for DR purpose?
Which activity is associated with Process Transformation?
What workflow software enables automation of complex IT tasks?
What term refers to businesses that do not have a digital plan, and have limited initiatives or investments related to digital transformation?
Which network feature enables dynamic distribution of applications I/O traffic across VMs?
Which key service management function modifies and aligns services according to consumer needs in the cloud environment?
Which is a characteristic of the chargeback model?
Which cloud role has the responsibility to perform independent cloud service assessments?
What is true about change management?
A cloud service provider must improve the utilization of resources by sharing them with multiple customers.
What mechanism should the cloud provider deploy to prevent one consumer from accessing the virtual machines of another consumer?
Which data storage type uses a non-hierarchical address space to store data?
Which cloud service management option defines the suite of service offerings and aligns it to the service provider's strategic business goals?
Which cloud security objective provides the required secrecy of information to ensure that only authorized users have access to data held within the cloud?
What does the management interface in a cloud portal enable consumers to do?
Which phase of the cloud service lifecycle involves ongoing management activities to maintain cloud infrastructure and deployed services?
An administrator must design a fault-tolerant IT environment for applications.
Which techniques meet this requirement?
Which condition triggers a warning level alert?
What is used to update information in a configuration management database?
Which concept ensures accountability for security breaches or misuse of resources?
An organization deployed a storage system that is configured with erasure coding. The erasure coding technique divides data into nine data segments and three coding segments.
What is the maximum number of drive failures supported in the storage system?
What refers to an agreement between provider and consumer that states the terms of service usage?
Which key service management function takes orders from customers, processes bills, and collects payments in the cloud environment?
When implementing an initial IT service center using ITILframework. In service strategy state which process needs to be considered for automation?
What are the key focus areas for IT transformation?
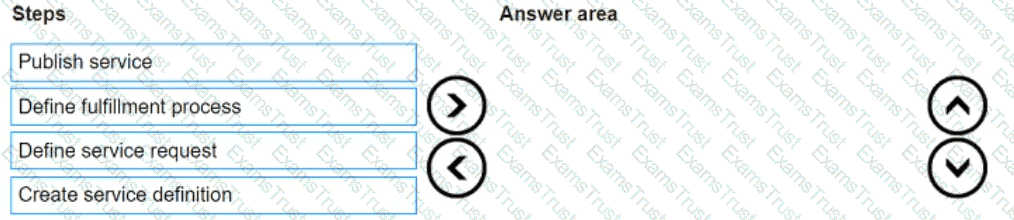
What is the correct sequence of steps in the service catalog design and implementation process?
An organization wants to deliver applications quickly and effectively. They believe that it is the only way to stay competitive in this ever-changing digital world. The organization wants to adopt practices that promote collaboration across teams during various phases of the software development lifecycle.
Which practice will meet the organization’s requirements?