Which is the primary purpose of exclusive accounts?
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens.
Which piece of the platform is missing?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
Which item is an option for PSM recording customization?
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
The System safe allows access to the Vault configuration files.
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
What is the chief benefit of PSM?
A Simple Mail Transfer Protocol (SMTP) integration is critical for monitoring Vault activity and facilitating workflow processes, such as Dual Control.
When managing SSH keys, the CPM stores the Public Key
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
What is a requirement for setting fault tolerance for PSMs?
What is the purpose of the password change process?
Which command configures email alerts within PTA if settings need to be changed post install?
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1.
What do you need to recover and decrypt the object? (Choose three.)
You have been asked to limit a platform called "Wmdows_Servers" to safes called "WindowsDCT and "WindowsDC2" The platform must not be assigned to any other safe What is the correct way to accomplish this?
You have been asked to configure SNMP remote monitoring for your organization's Vault servers. In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP Traps?
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
What is the purpose of the PrivateArk Server service?
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
PSM captures a record of each command that was executed in Unix.
Which report could show all accounts that are past their expiration dates?
Secure Connect provides the following. Choose all that apply.
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
Which of the following PTA detections are included in the Core PAS offering?
Your organization requires all passwords be rotated every 90 days.
Where can you set this regulatory requirement?
What is the easiest way to duplicate an existing platform?
You are installing PSM for SSH with AD-Bridge in CyberArkSSHD mode for your customer. ACME Corp What do you need to install to meet your customer's needs? (Choose 2)
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
You are creating a new Rest API user that utilizes CyberArk Authentication.
What is a correct process to provision this user?
SAFE Authorizations may be granted to____________.
Select all that apply.
In accordance with best practice, SSH access is denied for root accounts on UNIX/LINUX system. What is the BEST way to allow CPM to manage root accounts.
Which report provides a list of account stored in the vault.
Match each permission to where it can be found.
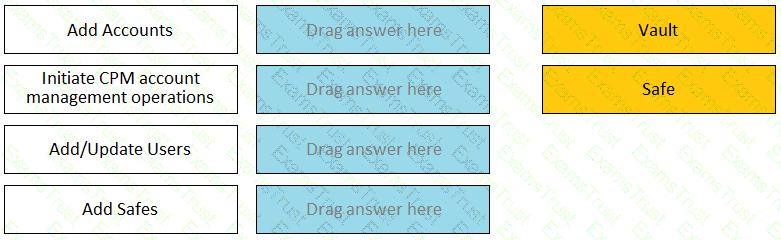
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?
Match each PTA alert category with the PTA sensors that collect the data for it.

What is the purpose of the Immediate Interval setting in a CPM policy?
You are helping a customer prepare a Windows server for PSM installation. What is required for a successful installation?
Which Master Policy Setting must be active in order to have an account checked-out by one user for a pre-determined amount of time?
VAULT authorizations may be granted to_____.
Which of the following options is not set in the Master Policy?
Which components can connect to a satellite Vault in distributed Vault architecture?
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
Which of these accounts onboarding methods is considered proactive?
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
Which components support fault tolerance.
A customer installed multiple PVWAs in the production environment behind a load balancer VIP. They subsequently observed that all incoming traffic from the load balancer VIP goes to only one PVWA, even though all the PVWAs are up and running. What could be the likely cause of this situation?
Which browser is supported for PSM Web Connectors developed using the CyberArk Plugin Generator Utility (PGUP
Which one the following reports is NOT generated by using the PVWA?
The vault supports Subnet Based Access Control.
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
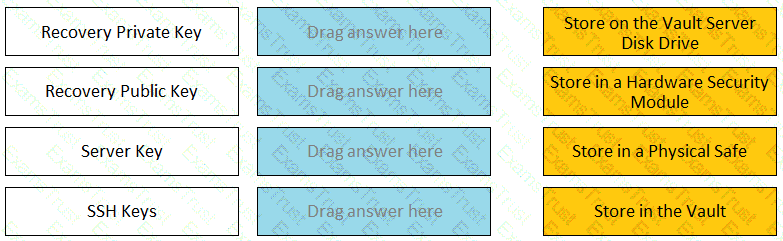
Match each key to its recommended storage location.
It is possible to control the hours of the day during which a user may log into the vault.
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
Match the connection component to the corresponding OS/Function.

You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
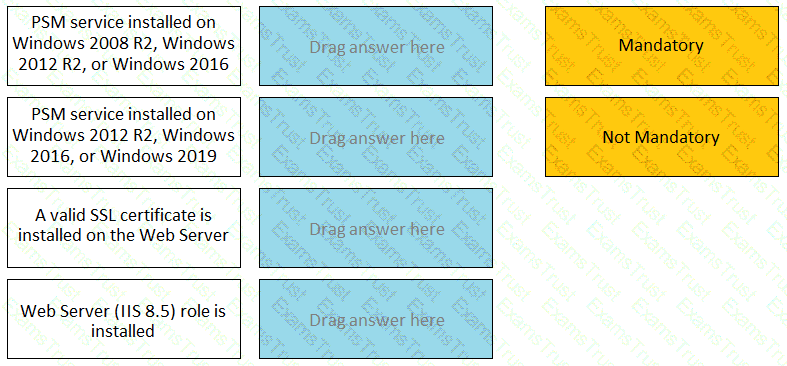
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access (PVWA) and receive approval before being able to launch a secure connection via PSM for Windows (previously known as RDP Proxy).
What is the purpose of the CyberArk Event Notification Engine service?
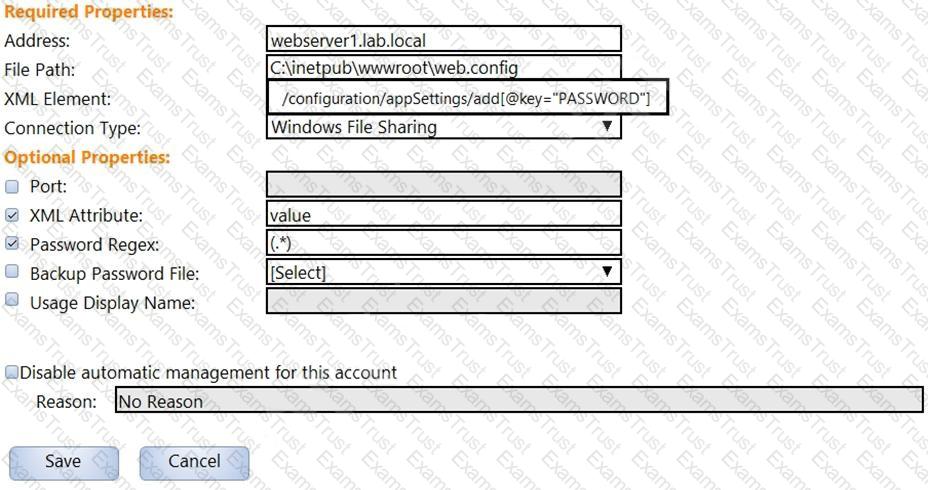
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
Which report shows the accounts that are accessible to each user?
Which configuration file and Vault utility are used to migrate the server key to an HSM?